The current ransomware landscape continues to evolve, with new and increasingly sophisticated ransomware emerging regularly.
Among the most recent players to hit the cybersecurity scene, Anubis stands out for a rather disturbing feature: Anubis is capable of permanently destroying data, even after encryption.
This new “double destruction” approach somewhat transforms the rules of the game in the world of ransomware.
Note that Anubis should not be confused with the Android malware of the same name, which features a ransomware module…
Table des matières
ToggleDisneyland Paris in the crosshairs: the rise of Anubis
Recent Anubis activity confirms the group’s expansion on the international cybercrime scene.
Indeed, on June 20, 2025, the operators claimed responsibility for a cyber attack on Disneyland Paris, setting a June 26 deadline for the disclosure of the allegedly stolen data.
The entertainment company has yet to officially confirm this incident, but this claim illustrates the group’s move towards larger-scale targets.
An in-depth data analysis approach
This claim stands out for the level of analysis of the information presented. Anubis operators have studied the documents in their possession, publishing screenshots of what appear to be attraction plans, technical specifications and internal visual content. This method of detailed investigation, less common among other criminal groups, is accompanied by monitoring of the victims’ public communications.
This surveillance enables the group to identify any contradictions between the official statements of the targeted companies and the reality of the incident as they present it. This lobbying tactic is also based on an understanding of the reputational challenges faced by organizations under attack.
An indicator of evolving threats
The alleged Disneyland Paris incident demonstrates Anubis’ ability to target high-profile companies. This move towards leading international organizations suggests that the group has moved beyond its initial emergence phase to establish itself as a significant player in the world of ransomware.
This further underlines the importance for organizations in all sectors to re-evaluate their security measures, regardless of their size or resources, in the face of the constantly evolving tactics employed by these criminal groups. See the Le Mag IT article for full coverage of this incident.
Anubis, the rising ransomware with destructive methods
Anubis is no ordinary ransomware. First appearing in December 2024, it operates on a Ransomware-as-a-Service (RaaS) model, but with a vicious innovation: the integration of a “wiper ” module that can permanently erase the contents of target files, if the ransom is not paid for example…
This destructive feature, activated by the /WIPEMODE parameter, doesn’t just encrypt data. It irretrievably deletes them, reducing the size of files to 0 Kb while preserving their names and structures. The result is catastrophic: even if the victim finally pays the ransom, recovery becomes virtually impossible.
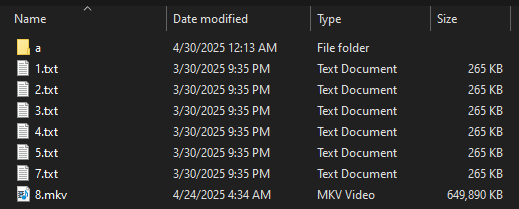
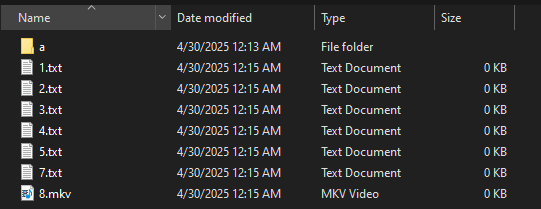
It is clear that the aim of this module is to reduce negotiation times prior to payment of the ransom, and to exert additional pressure on victim organizations.
This approach can be seen as a significant escalation in the cybercriminals’ arsenal, now crossing the red line between extortion and outright destruction.
A highly structured criminal organization
A diversified business model
Unlike traditional groups, Anubis innovates by offering several affiliate programs that maximize criminal revenues:
- Ransomware program (80/20): affiliates keep 80% of the ransom money collected.
- Data extortion program (60/40): Monetization of stolen data with 60% revenue for affiliates
- Access monetization program (50/50): Sale of access to compromised networks with equal sharing of profits
This diversification reflectsa sophisticated business approach that goes far beyond the traditional ransomware model.
A worrying marketing approach
The group demonstrates a disturbingly professional approach to its criminal activities. Their operators write detailed investigative articles on their victims, analyzing in depth the vulnerabilities of each targeted company.
This method enables them to identify the most effective pressure points during negotiations. They also maintain an active presence on social networks and underground forums, using pseudonyms such as “superSonic” on the RAMP forum and “Anubis__media” on XSS.
Technical analysis of the Anubis ransomware: a formidable arsenal
Multiple infection methods
Anubis attacks usually start with carefully crafted phishing emails, containing malicious attachments or links that appear to come from trusted sources. The group also exploits vulnerabilities in RDP protocols through brute-force attacks, and distributes its malware via Trojan software and fake system updates.
Advanced technical capabilities
The ransomware features advanced technical characteristics. It uses ECIES (Elliptic Curve Integrated Encryption Scheme) encryption similar to that seen in the EvilByte and Prince ransomwares, leading to speculation that existing code may have been reused. The ransomware can automatically elevate its privileges to NT AUTHORITYSYSTEM and spread across corporate domains. Its multi-platform compatibility covers Windows, Linux, NAS and ESXi, considerably broadening the potential attack surface.
Once installed, Anubis methodically deletes Volume Shadow Copies to prevent any attempt at system restoration, and terminates processes likely to interfere with encryption.
The ransomware also modifies the icons of encrypted files to affix its distinctive logo, creating an immediate visual impact on victims.
Victims and geographical impact
Since its emergence, Anubis has already claimed several strategically chosen victims around the world. The group primarily targets the healthcare, engineering and construction sectors, with a geographic approach that stretches from Australia to Canada, via Peru and the USA.
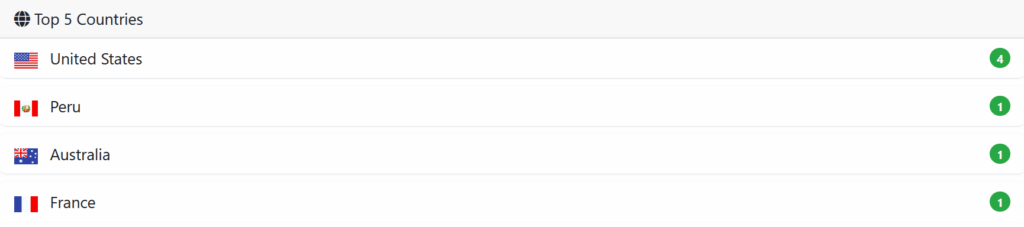
In addition to Dyneyland, confirmed victims include Australia’s Pound Road Medical Centre, which issued a statement detailing the incident on November 13, 2024, and Summit Home Health in Canada. These cases perfectly illustrate the group’s appetite for sensitive data in the medical sector, which is particularly vulnerable to blackmail due to the critical nature of patient information.
A worrying change in the threat landscape
The emergence of Anubis illustrates a worrying escalation in the tactics of modern cybercriminals.
The addition of definitive data destruction capabilities represents a major turning point in the history of ransomware: victims now lose all hope of recovery, even if they pay the ransom.
This development breaks the tacit contract that existed between criminals and victims, where payment theoretically guaranteed data recovery.
This transformation is part of a wider trend observed in 2025, with a dramatic 87% increase in ransomware incidents between January and February according to industry data. The arrival of new players like Anubis is contributing to this explosion, bringing technical innovations that constantly push back the boundaries of digital destruction.
Conclusion: prepare for a new reality
Anubis ransomware marks the definitive entry into a new era of cybercriminal threats, where destruction is gradually replacing simple reversible encryption. This fundamental change is forcing organizations to completely rethink their approach to cybersecurity, moving from a post-incident recovery logic to a strategy of absolute prevention.
To respond to this new situation, companies and institutions can no longer be content with traditional defensive strategies. Prevention becomes absolutely critical, because once Anubis penetrates a system and activates its destruction mode, even the best negotiation strategies become obsolete. Affected files are lost forever, with no turning back.
Massive investment in prevention and immutable backups is no longer a strategic option, but a vital necessity to survive this new generation of destructive threats. Organizations that fail to adapt quickly to this reality risk discovering, too late, that their most valuable data has been wiped out by criminals who play by no rules.
If you are a victim of ransomware, contact our teams as soon as possible. Our emergency response team is at your disposal 24/7.
Consult the main sources of the article :
- Trend Micro: Anubis: A Closer Look at an Emerging Ransomware with Built-in Wiper
- BleepingComputer: Anubis ransomware adds wiper to destroy files beyond recovery
- The Hacker News: Anubis Ransomware Encrypts and Wipes Files, Making Recovery Impossible
- KELA Cyber: Anubis: A New Ransomware Threat
- Foresiet: Inside Anubis Ransomware: Tactics, Impact & Protection
