Despite the historic dismantling carried out by Operation Cronos in February 2024, the LockBit cybercrime group has resurfaced with version 5.0, featuring significant technical improvements while retaining a scalable code base. This new iteration, analyzed in depth by Trend Micro researchers, confirms the extraordinary resilience of the world’s most prolific ransomware group.
In September 2025, on the occasion of their sixth anniversary, the LockBit operators officially unveiled this fifth version, which simultaneously targets Windows, Linux and VMware ESXi environments. This cross-platform approach, initiated since LockBit 2.0 in 2021, has now reached an unprecedented level of sophistication that is of particular concern to cybersecurity experts. Trend Research researchers have analyzed the source binaries of the latest activity of the notorious LockBit ransomware with their version 5.0, which features advanced obfuscation, anti-analysis techniques and transparent cross-platform capabilities for Windows, Linux and ESXi systems.
Table des matières
ToggleA strong comeback after Operation Cronos
Operation Cronos, carried out in February 2024 by an international coalition including the FBI, the UK National Crime Agency, Europol and law enforcement agencies from eleven countries, dealt a severe blow to LockBit’s infrastructure. This landmark initiative resulted in the seizure of LockBit’s main servers, the disclosure of decryption keys and the closure of the group’s trading sites.
This operation revealed the scale of their activities: more than 7,000 attacks built using their services between June 2022 and February 2024, according to Europol.However, as analysts had anticipated, the dismantling of such an organized group could only be a temporary victory. The emergence of LockBit 5.0 confirms the fears expressed by the security community: cutting off one head of the cybercriminal hydra can provoke the regrowth of new, sometimes stronger networks. This resurgence is a perfect illustration of the adaptability and resilience of modern ransomware groups.
Chronological evolution of LockBit versions
To better understand the scope of LockBit 5.0, we need to examine the evolution of the group since its inception. The following table illustrates the main innovations and their strategic impact:
| Version | Period | Code name | Key innovations | Strategic impact |
|---|---|---|---|---|
| LockBit 1.0 | 2019-2020 | “ABCD | – .abcd extension on encrypted files– C/C++ implementation – Basic fast encryption | Initial emergence of the |
| LockBit 2.0 | 2021 | “Red | – StealBit: dedicated exfiltration tool – Automated propagation (SMB, PsExec, WMI) – Linux and VMware ESXi support – Structured RaaS program | Transition to industrial model |
| LockBit 3.0 | 2022 | “Black | – Optimized intermittent encryption – First bug bounty program – Point-and-click tool for affiliates – Triple extortion (encryption + theft + publication) | Market domination (40% of incidents) |
| LockBit 4.0 | Late 2024 – Early 2025 | “Green | – Complete rewriting in .NET Core – Stealth-first architecture – Advanced anti-EDR API release – Decentralized Tor infrastructure – Multi-threaded encryption | Response to law enforcement pressure |
| LockBit 5.0 | September 2025 | N/A | – Complete modular architecture – Potential cartel coordination – Optimized speed/furtivity – Flexible Tor + Tox communications – Revamped affiliate program | Post-Cronos renaissance |
This progression reveals a strategy of incremental rather than revolutionary evolution, with major breakthrough points in 2021 (industrialization), 2022 (market domination) and 2024-2025 (post-dismantling resilience).
Significant technical improvements
A redesigned user interface
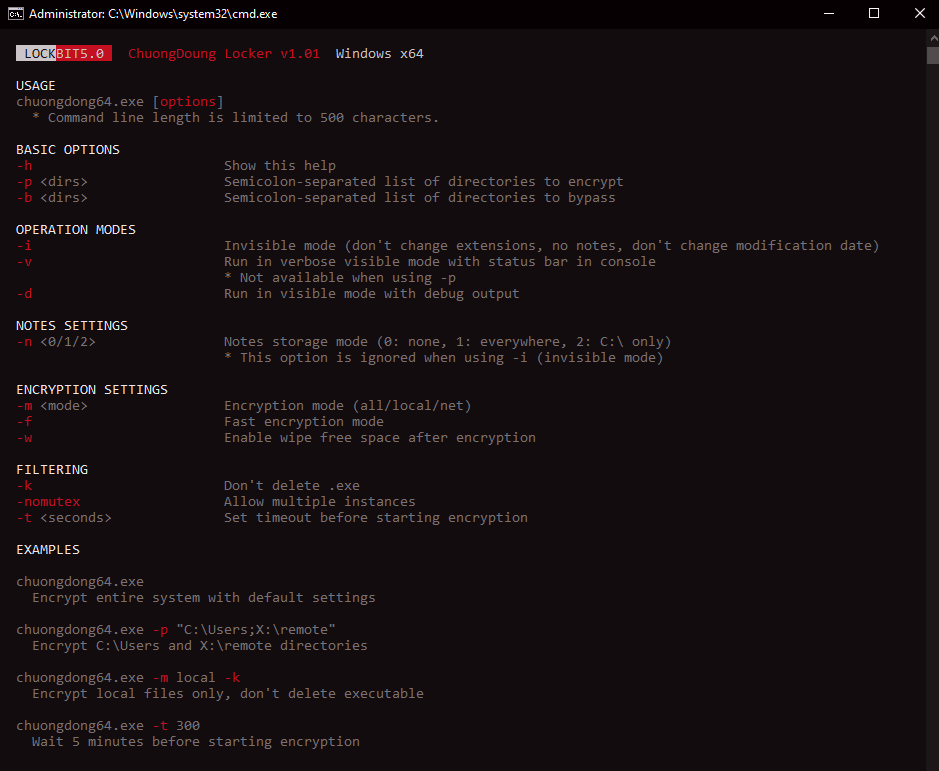
LockBit 5.0 boasts a significantly improved user interface, with clear, professional formatting that was not present in previous versions. This evolution, which makes it easier for affiliates to use, bears witness to the increasing professionalization of the RaaS (Ransomware-as-a-Service) model.
The interface details numerous runtime options and parameters, including the specification of directories to be encrypted or bypassed, invisible and verbose operating modes, ransom note parameters, encryption settings and advanced filtering options. This operational flexibility offers attackers unprecedented customization of their campaigns.
Advanced obfuscation techniques
The Windows variant of LockBit 5.0 uses massive obfuscation and packaging, loading its payload via DLL reflection, which considerably complicates static analysis. The researchers at Trend Research state: “The sample analyzed by Trend Research uses extensive obfuscation via packaging. During debugging, we discovered that it functions as a binary loader, decrypting a PE binary in memory and loading it via DLL reflection methods. This sophisticated loading mechanism considerably complicates static analysis”.
Alongside code obfuscation, the malware implements several advanced anti-analysis techniques, including patching the EtwEventWrite API by replacing it with a 0xC3 (return) instruction, thus disabling Windows Event Tracking (ETW) capabilities. This specific evasion technique directly targets modern detection solutions based on Event Tracing for Windows.
Neutralization of system defenses and forensic erasure
Once execution has been established, LockBit 5.0 eliminates security-related services by comparing hashed service names with a hard-coded list of 63 values, then deletes all event logs using the EvtClearLog API once encryption is complete. This systematic approach aims to neutralize traditional defenses and erase forensic traces of the attack.
The ransomware uses a hash system identical to LockBit 4.0 for service identification, confirming that it is an evolution of the original code rather than an imitation by other malicious actors.
A refined multiplatform strategy
Extended Linux capabilities
The Linux variant of LockBit 5.0 features similar functionality to its Windows counterpart, demonstrating the group’s commitment to cross-platform capabilities. The command-line interface mirrors the formatting and functionality of the Windows version, offering attackers the same operational flexibility on both platforms.
During execution, the Linux variant provides detailed logging of its activities, displaying files targeted for encryption and folders designated for exclusion. This transparency in operation logs suggests that the variant can be used in test environments or by affiliates requiring detailed execution feedback.
Critical threat to virtualized environments
The ESXi variant represents a critical escalation in LockBit’s capabilities, as it specifically targets VMware virtualization infrastructure. As Trend Micro explains: ” this ESXi variant represents a critical escalation in LockBit’s capabilities, as ESXi servers typically host multiple virtual machines, enabling attackers to encrypt entire virtualized environments with the execution of a single payload “.
This capability turns a single attack into an organizational disaster, where dozens or hundreds of virtual machines can be compromised simultaneously. The impact on business continuity then becomes exponential compared with traditional attacks targeting individual workstations.
Features common to all three variants
Random file extensions
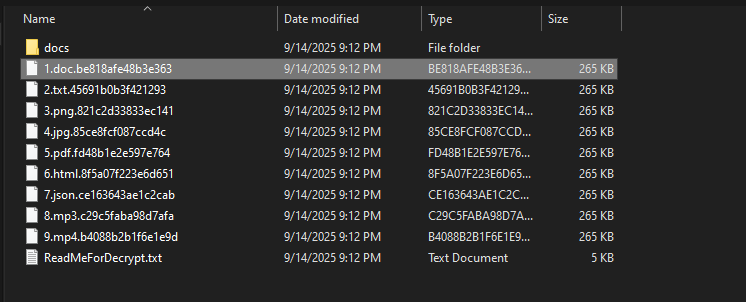
All LockBit 5.0 variants use 16-character random file extensions, significantly complicating recovery efforts. Unlike some ransomware variants that use common infection markers, LockBit 5.0 omits traditional markers at the end of files.
This approach makes the identification and analysis of encrypted files more complex for incident response teams. However, Trend Micro’s analysis revealed consistent patterns including the original file size embedded in the footer of the encrypted file.
Geolocation mechanisms
In line with previous versions, LockBit 5.0 includes geopolitical protections, terminating execution upon detection of Russian language settings or Russian geolocation. This common practice among Eastern European ransomware groups reflects strategic geopolitical considerations in the development of the malware.
These geographic protection mechanisms suggest a specific geographic origin of the group and constitute a significant technical attribution element for investigators.
Modular architecture and code evolution
Continuity with LockBit 4.0
Comparative analysis between LockBit 4.0 and 5.0 reveals significant code reuse and evolutionary development rather than complete rewriting. Both versions share identical hashing algorithms for string operations, a critical component for API resolution and service identification.
The code structure for dynamic API resolution remains remarkably similar between versions, suggesting that the developers have built on the existing LockBit 4.0 code base. This technical continuity confirms that LockBit 5.0 represents a continuation of the LockBit ransomware family and not an imitation by different threat actors. As Trend Research puts it: ” These similarities are a clear indication that LockBit 5.0 represents a continuation of the LockBit ransomware family and is not an imitation or rebranding by different threat actors “.
Advanced modular approach
LockBit 5.0 introduces a modular architecture allowing affiliates to switch components per campaign. This modularity optimizes speed and enhances anti-detection analysis, while offering flexible communications during negotiations through Tor portals and Tox channels as required.
The system includes revised incentives for affiliates to rebuild the network after the dismantling of Operation Cronos, with signals of cooperation with peer groups and potential cartel-like coordination. The aim is to reduce impact time while reducing the detection surface.
A strategic dimension: towards a ransomware cartel
Beyond its technical improvements, LockBit 5.0 is part of a broader strategy to consolidate the criminal market. On the RAMP forum, DragonForce publicly proposed that LockBit and Qilin form a cartel to “create a level playing field, without conflict or public insults“. This initiative reflects the growing professionalization of the cybercriminal ecosystem, and a desire to stabilize illicit revenues through cooperation rather than destructive competition.

This collaborative approach could enable participating groups to pool their technical resources, share intelligence on targets and coordinate their campaigns to avoid interference. The formation of such a cartel would represent a major evolution in the organization of cybercrime, transforming individual players into a structured consortium capable of exerting increased systemic pressure on companies and institutions.
Cartel-like consolidation would also facilitate the standardization of practices and optimization of criminal processes, enabling even greater industrialization of ransomware operations. This development is of particular concern to analysts, as it could lead to a significant increase in the volume and sophistication of attacks.
Impact on the threat ecosystem
Democratization of advanced techniques
The reduction in affiliate program barriers (automatic enrolment, broader recruitment) means that intrusion techniques are more varied from one campaign to the next. This evolution lowers the technical threshold required to carry out sophisticated attacks, potentially broadening the pool of malicious actors capable of exploiting the platform.
Payloads are often launched filelessly via PowerShell or hijacked legitimate binaries (Living off the Land Binaries – LOLBins), and constructs can include expiring validity periods, hampering post-incident analysis. This fileless approach significantly complicates detection by traditional security solutions.
Evasion tactics evolve
LockBit 5.0 introduces expanded process termination lists, advanced API stall and built-in obfuscation in the modular architecture. These technical enhancements are specifically targeted at modern security solutions, including Endpoint Detection and Response (EDR) tools and SIEM platforms.
Observed techniques include shutting down antivirus and backup agents, deleting shadow copies via the vssadmin delete shadows command, deleting logs and detection checks on sandbox and virtual machine environments. This holistic approach to evasion demonstrates a deep understanding of contemporary organizational defenses.
Defensive recommendations
Multi-layered detection approach
Experts recommend that organizations adopt an urgent multi-layered detection approach, recognizing that static signatures and traditional rules are no longer sufficient. Detection systems need to incorporate up-to-date threat intelligence data, learn from ongoing attacks and dynamically adapt to new evasion techniques.
Behavioral detection becomes crucial to identify anomalous login activity, repeated authentication failures and suspicious scripting activity, particularly PowerShell-generated child processes. SOC teams also need to monitor registry access outside normal baselines.
Enhanced protection for virtualized environments
The ESXi variant of LockBit 5.0 requires specific protection measures for virtualization infrastructures:
- strict network segmentation of virtualization infrastructures to isolate hypervisors from production networks
- enhanced monitoring of ESXi administrator access, with mandatory multi-factor authentication and real-time monitoring
- isolated backups of VM configurations and datastores maintained offline, with regular restore tests
- monitoring of critical commands and snapshots to detect suspicious manipulations
- hardening of management interfaces with deactivation of non-essential services
Faster patch cycles
When uptime is measured in hours, patching can no longer be a process lasting several weeks. Automated patch validation and deployment pipelines become essential in the face of LockBit 5.0’s speed of operation.
Organizations also need to monitor dark web discussions and underground forums as a critical defensive input. These early signals provide vital preparation time before new attack techniques are deployed.
Future challenges and strategic implications
Industrialization of cybercrime
LockBit 5.0 represents the embodiment of the industrialization of cybercrime, where once artisanal processes become large-scale operations optimized for efficiency and profitability. This evolution is transforming the digital underground economy, creating new business models based on automation and scalability.
The ability to launch simultaneous attacks against thousands of targets with a single operator is revolutionizing the attack economy. This industrial scalability favors mass ransomware and enables cybercriminals to enrich themselves rapidly, while dramatically compressing the defensive reaction window.
Continuous evolution expected
The existence of Windows, Linux and ESXi versions confirms LockBit’s ongoing cross-platform strategy, enabling simultaneous attacks across entire corporate networks, from workstations to critical servers hosting databases and virtualization platforms. As Trend Micro points out: “the existence of Windows, Linux and ESXi variants confirms LockBit’s ongoing multiplatform strategy, enabling simultaneous attacks across entire corporate networks, including virtualized environments*”.
LockBit 5.0’s architectural modularity also facilitates the rapid integration of new features and adaptation to emerging defensive countermeasures, suggesting a capacity for continuous and accelerated evolution.
Conclusion
LockBit 5.0 marks a turning point in the evolution of ransomware, confirming that the temporary dismantling of a cybercriminal group is only a fleeting victory against such resilient and adaptive criminal organizations. The technical sophistication of this new version, combined with its multiplatform approach and advanced evasion capabilities, makes it significantly more dangerous than its predecessors.
Theheavy obfuscation and technical enhancements of all variants make LockBit 5.0 significantly more dangerous than its predecessors, considerably delaying the development of detection signatures. This evolution is forcing organizations to rethink their traditional defense strategies in favor of adaptive approaches driven by artificial intelligence.
For defenders, the urgency is threefold: address current vulnerabilities with unprecedented speed, prepare for a future where AI-driven orchestration will be the norm, and develop countermeasures capable of rivaling the growing sophistication of offensive tools. The sooner the security community adapts – by patching faster, detecting smarter and responding at machine speed – the greater our ability to keep pace in this new era of industrialized cyber conflict.
Main article sources:
- Trend Micro: New LockBit 5.0 Targets Windows, Linux, ESXi
- Vectra AI: LockBit is Back: What’s New in Version 5.0
- Infosecurity Magazine: New LockBit Ransomware Variant Emerges as Most Dangerous Yet
- Europol: New measures issued against LockBit
- SocRadar: LockBit 5.0 & Ransomware Cartel: What You Need To Know?
- Trellix: Inside the LockBit’s Admin Panel Leak: Affiliates, Victims and Millions in Crypto
