Michelin, Mazda, Canon, Logitech, Harvard University… A hundred international organizations have just discovered that their most sensitive data has been exfiltrated for months. Behind this wave of attacks on an exceptional scale is the cybercriminal group Cl0p, which exploited a zero-day vulnerability in Oracle E-Business Suite long before Oracle was even aware of its existence.
This sixth major Cl0p campaign since 2020 confirms the formidable effectiveness of their strategy: identify a massively deployed enterprise platform, discover a critical vulnerability, silently exfiltrate terabytes of data, then launch a massive extortion campaign. After MOVEit Transfer, which affected over 2,700 organizations in 2023, Oracle E-Business Suite becomes the group’s new playground. On November 20, 2025, Cl0p announced a new series of victims, marking a spectacular acceleration in this campaign which began this summer.
Table des matières
ToggleMonths of invisible exploitation
It all began discreetly on July 10, 2025. Google Threat Intelligence Group and Mandiant detected suspicious activity targeting the UiServlet component of Oracle E-Business Suite. At this stage, no one is fully aware of the extent of what is afoot. The abnormal HTTP requests originating from the IP address 200.107.207.26 could be nothing more than classic exploitation attempts. Investigators cannot yet formally confirm a successful exploit, but the associated network infrastructure shows characteristics consistent with the callback servers used in subsequently disclosed exploits.
Between August 9 and 12, the attack shifted up a gear. Cl0p deployed its full exploitation chain, this time targeting the SyncServlet component, giving it direct access without authentication to the Oracle EBS environments of dozens of companies. For several weeks, the attackers methodically sucked in massive volumes of data: customer files, HR files, financial documents and confidential contracts. Victims never suspect a thing. System administrators went about their daily tasks, unaware that their Oracle servers were transmitting their secrets to the Cl0p infrastructure.
On September 29, 2025, hundreds of executives discovered the catastrophe by e-mail. The messages all began with the same formula: “Dearest Executive, We have recently breached your Oracle E-Business Suite application and copied a lot of documents.”

To prove the veracity of their claims, Cl0p attached listings of legitimate files extracted in mid-August. The message is clear: pay, or your data will be published. Two email addresses are used to initiate negotiations. The extortion machine is launched.
Two critical vulnerabilities, CVE-2025-61882 and CVE-2025-61884 exploited in chain
CVE-2025-61882: the flaw that changes everything
Oracle discovered the scale of the disaster in early October. The vulnerability exploited by Cl0p is now called CVE-2025-61882, and its CVSS score of 9.8 out of 10 ranks it among the most critical of the year. It affects the BI Publisher Integration component within Oracle EBS’s Concurrent Processing module, responsible for executing background tasks across the suite. What makes this flaw so devastating? It allows the execution of arbitrary code remotely via HTTP without any prior authentication. No password required, no prior login necessary: a simple network access to the EBS server is enough to take full control.
On October 3, 2025, a rival group called “Scattered Lapsus Hunters” published the complete exploit on Telegram. Technical analysis reveals the sophistication of the attack chain: the exploit combines a Server-Side Request Forgery (SSRF) injection, a Carriage-Return Line-Feed (CRLF) injection, an authentication bypass and an XSL template injection. In concrete terms, the attacker can inject malicious commands directly into XSL templates stored in the XDO_TEMPLATES_B and XDO_LOBS tables of the EBS database, then trigger execution of these templates via the TemplatePreviewPG endpoint to execute code on the server. This exploit chain makes it possible to deploy Bash reverse shells or execute arbitrary commands on compromised EBS servers.
From now on, it’s not just Cl0p that can exploit the CVE flaw: any cybercriminal with access to the code can strike. The disclosure of this exploit on public channels considerably aggravates the situation, making the vulnerability accessible to other malicious actors beyond Cl0p.
CVE-2025-61884: the secondary flaw
On October 11, 2025, Oracle released a second emergency patch for CVE-2025-61884, a high-severity vulnerability with a CVSS score of 7.5. It affects the Oracle Configurator Runtime UI and allows remote attackers toaccess sensitive configuration data and trigger internal requests via the UiServlet endpoint, again without authentication. The US Cybersecurity and Infrastructure Security Agency (CISA) immediately adds CVE-2025-61884 to its catalog of Known Exploited Vulnerabilities, confirming its active exploitation in the wild and imposing a mandatory patching deadline of November 10, 2025 on US federal agencies.
Both vulnerabilities affect Oracle EBS versions from 12.2.3 to 12.2.14, exposing a considerable base of enterprise installations worldwide.
The timeline reveals a major problem in Oracle’s response. On October 2, 2025, Oracle published a first security advisory suggesting that the attackers were exploiting vulnerabilities already patched in the Critical Patch Update of July 2025. Faced with mounting evidence of the exploitation of an unknown zero-day vulnerability, Oracle published an emergency patch on October 4, addressing CVE-2025-61882. However, this first patch failed, forcing Oracle to publish a second patch on October 11 to address CVE-2025-61884. Customers thus remain exposed for a further six days, after having already been vulnerable for several months.
A campaign that intensifies in November
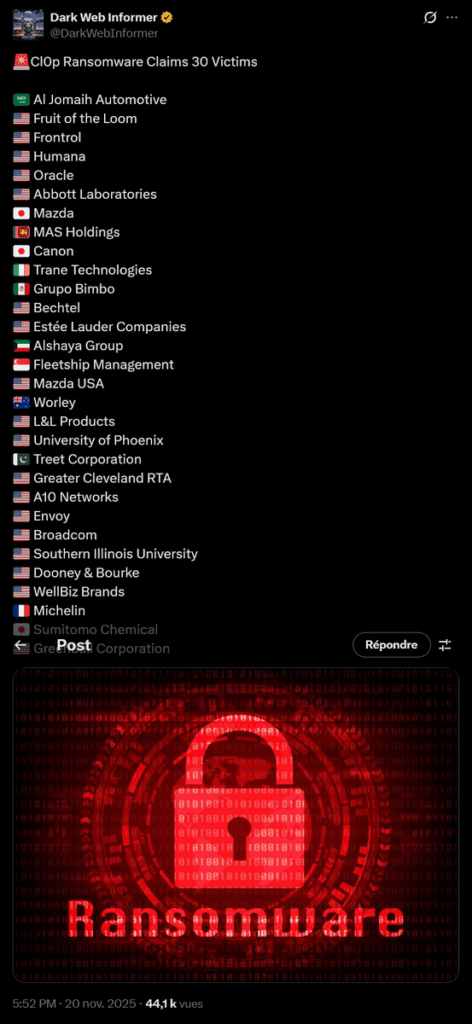
The extortion campaign initiated at the end of September 2025 saw several waves of publications on the Cl0p leak site during November. The first victims had been named in mid-October, including Harvard University and Envoy Air, a subsidiary of American Airlines, which quickly confirmed that they had been compromised. In early November, SecurityWeek reported that nearly 30 organizations were now listed on the group’s site. These victims included companies from a wide range of sectors: technology, automotive, healthcare, industrial manufacturing and education.
The pace quickened again in the second half of the month, with new victims confirming the compromises: The Washington Post revealed the exposure of employee data, and British insurer Allianz UK also appeared on the list. The British National Health Service NHS was also listed by Cl0p , but the organization has not confirmed any compromise and no data has been published to date. The NHS is currently conducting an investigation with the National Cyber Security Centre.
November 20 marked the peak of the campaign when Cl0p added a new wave of high-profile victims to its site. These included industrial giants such as Mazda, the Japanese car manufacturer, and its American subsidiary Mazda USA, as well as Canon, a specialist in optics and imaging. However, Mazda confirms that it was targeted, and claims to have detected and repelled the attack without any data leakage, while Canon has also confirmed a security incident, specifying however that it appeared to be limited to a subsidiary of Canon U.S.A. Inc., affecting only a web server.
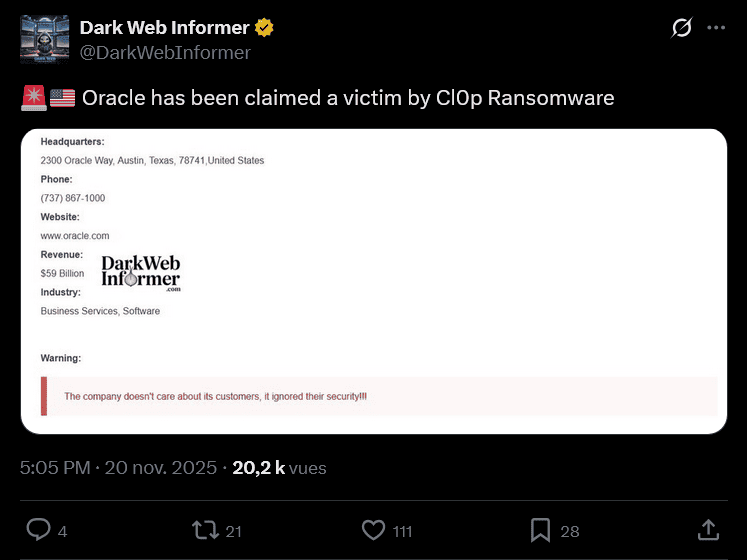
Oracle itself briefly appeared on the Cl0p leak site on November 20, 2025, before the entry was quickly removed. This appearance was accompanied by a message incriminating Oracle: “The company doesn’t care about its customers. It ignored their security!!!”
Victims from all walks of life
Several organizations have publicly confirmed that they have been compromised as part of this campaign, providing details of the extent of the breaches, while other posted victims have yet to confirm the attack.
Logitech was among the first major brands to make the compromise official. On November 14, the Swiss manufacturer confirmed that an attacker had exploited the CVE-2025-61882 vulnerability in Oracle E-Business Suite to copy internal data. Cl0p claims possession of 1.8 terabytes of information, including financial documents, spreadsheets and HR data. Other institutions followed suit: Dartmouth College revealed a compromise in August, GlobalLogic notified thousands of employees.
In the private sector, one big name follows another: semiconductor giant Broadcom appears alongside French tire manufacturer Michelin, Mexican conglomerate Grupo Bimbo, and Middle Eastern groups such as Aljomaih Automotive (Saudi Arabia) and Alshaya Group (Kuwait). No sector was spared, from consumer brands like Estée Lauder (cosmetics) to healthcare companies like Humana (health insurance). The geographic and sectoral diversity confirms the opportunistic nature of the campaign: with Oracle EBS massively deployed, Cl0p was able to compromise Japanese automakers, American universities, French manufacturers and software publishers alike.
Cl0p’s proven playbook: mass industrial exploitation
This Oracle campaign is not an improvisation. It’s part of a perfectly honed strategy that has made Cl0p one of the world’s most formidable extortion groups. Active since 2020, Cl0p has built its reputation on the systematic exploitation of zero-day vulnerabilities in widely deployed enterprise software.
Where other ransomware groups multiply targeted attacks one by one, Cl0p has chosen a radically different approach: the massive exploitation of widely deployed enterprise platforms. The group identifies critical platforms used by hundreds of companies, discovers undocumented security flaws, massively exfiltrates data, then launches coordinated extortion campaigns several weeks after the initial intrusion. This industrial approach transforms a single vulnerability into a lever for extortion on an international scale.
The Group’s track record bears witness to the effectiveness of this strategy. In 2020, the exploitation of CVE-2021-27104 in the Accellion File Transfer Appliance affected around a hundred organizations. In 2021, a zero-day flaw in SolarWinds Serv-U FTP (CVE-2021-35211) served as a springboard for further compromises. In 2023, the GoAnywhere MFT campaign exploiting CVE-2023-0669 impacted over 100 companies, before the MOVEit Transfer exploit (CVE-2023-34362) became one of the most massive data theft campaigns ever documented, affecting 2,773 organizations worldwide and exposing almost 96 million individuals. At the end of 2024, Cl0p exploited vulnerabilities CVE-2024-50623 and CVE-2024-55956 in Cleo products, claiming over 400 victims in the first three months of 2025.
Historically known for its ransomware discovered in early 2019 and originally attributed to the TA505 group, Cl0p has distanced itself from encrypting its victims’ data since 2023, favoring simple extortion based solely on data theft and the threat of disclosure. This strategic evolution reflects an adaptation to increasingly sophisticated defenses against traditional ransomware, while maintaining effective extortion capability. The US State Department is now offering a $10 million reward for any information linking Cl0p activities to a foreign government.
How to defend against this threat
In the face of this campaign, organizations using Oracle E-Business Suite need to adopt a multi-layered defensive posture. Immediate application of the Oracle emergency patches released on October 4 and 11, 2025 is the top priority. Analysts at Google Threat Intelligence Group estimate that Oracle EBS servers updated with the October 11 patch are probably no longer vulnerable to known exploit chains.
However, patching is not enough to eradicate an existing compromise. If your Oracle EBS systems were exposed between July and October without patching, attackers may already have established footholds in your infrastructure.
Hunting down malicious templates in the EBS database is a critical detection measure. Attackers store their payloads directly in the XDO_TEMPLATES_B and XDO_LOBS tables of the EBS database. Administrators should immediately query these tables to identify malicious templates, particularly those whose TEMPLATE_CODE begins with the prefixes TMP or DEF.
Security teams should also restrict outbound Internet access from EBS servers to disrupt the attack chain, monitor abnormal HTTP requests to /OA_HTML/configurator/UiServlet, /OA_HTML/SyncServlet and TemplatePreviewPG endpoints, immediately block source IP addresses identified in the campaign, including 200.107.207.26 and 161.97.99.49, and forensically analyze the memory of Java processes associated with the EBS application to detect compromises.
Beyond the immediate response, this campaign calls for a strategic rethink. Organizations need to segment EBS environments to limit the blast radius in the event of a compromise, and accelerate patch deployment cycles via automated pipelines. The time between the discovery of a vulnerability and its exploitation is now counted in days, not weeks.
A wake-up call for ERP users
The Cl0p campaign against Oracle EBS underlines the importance for companies of keeping a close eye on software updates. ERP platforms, the backbone of modern organizations, are becoming prime targets for mass extortion operations. Their compromise simultaneously exposes customer, HR, financial and operational data.
This attack reminds us of an uncomfortable truth: zero-days in massively deployed enterprise software turn every organization using the product into a potential victim, regardless of its own security posture. Faced with attackers who discover and exploit vulnerabilities before the vendor is even aware of them, traditional defenses are showing their limits.
The response requires an in-depth approach combining continuous monitoring, accelerated patch cycles, rigorous network segmentation and advanced detection capabilities. The 103 organizations identified on November 21 probably represent a fraction of the actual victims. According to Google Threat Intelligence, thousands of Oracle EBS environments were potentially exposed during the exploitation period.
Sources
Google Cloud: Oracle E-Business Suite Zero-Day Exploited in Widespread Extortion Campaign
Oracle: Security Alert CVE-2025-61882
Oracle: Security Alert CVE-2025-61884
SOCRadar: Cl0p’s Oracle EBS Zero-Day Campaign: What We Know So Far
Cybernews: Cl0p gang hacks Oracle, exploiting Oracle’s own EBS zero-day
BleepingComputer: Clop extortion emails claim theft of Oracle E-Business Suite data
BleepingComputer: Logitech confirms data breach after Clop extortion attack
The Record: At least 35,000 impacted by Dartmouth College breach through Oracle EBS campaign
Ransomware.live : Clop Group
