Nitrogen ransomware trapped by its own bug
The cybercriminal group Nitrogen has just suffered an embarrassing mishap that turns their ransomware into a tool for outright destruction. A programming error in their

The cybercriminal group Nitrogen has just suffered an embarrassing mishap that turns their ransomware into a tool for outright destruction. A programming error in their
A massive identity theft campaign is currently hitting over 100 leading companies worldwide. Behind this offensive is the cybercriminal alliance Scattered LAPSUS$ Hunters (SLSH), which

Industry observers agree on one thing: the year 2026 marks a shift in the very nature of cyberattacks. Artificial intelligence no longer simply assists attackers,

On January 5, 2026, British carmaker Jaguar Land Rover released its preliminary figures for the third quarter of fiscal 2026. These results confirm the scale
Having emerged in mid-2025, the Sinobi group has rapidly established itself as a major player in the ransomware landscape, thanks to its disciplined approach and

First identified in February 2025, the Kraken group quickly distinguished itself in the cybercriminal ecosystem through its sophisticated technical approach. Stemming from the ashes of
Generative artificial intelligence is revolutionizing business productivity, with 71% of organizations now using it on a regular basis. But like all powerful technologies, large-scale language

Gone are the days when ransomware simply encrypted data for ransom. For several years now, cybercriminals have been transforming their business model by adding a

A major international alert On November 13, 2025, an unprecedented coalition of international cybersecurity agencies issued a joint alert update on the Akira ransomware. This
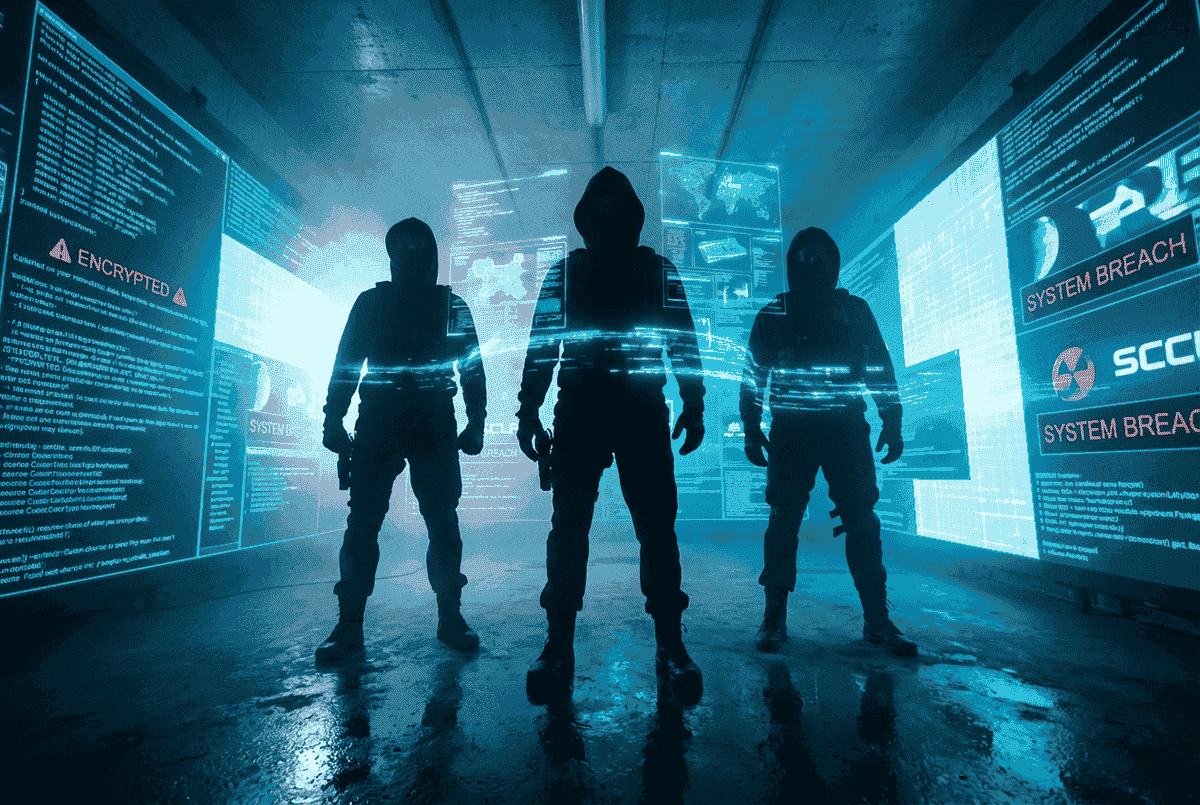
Launched in August 2025, the Scattered LAPSUS$ Hunters (SLSH) collective has rapidly established itself as one of the most formidable threats on today’s cybercriminal landscape.

Michelin, Mazda, Canon, Logitech, Harvard University… A hundred international organizations have just discovered that their most sensitive data has been exfiltrated for months. Behind this

First appearing in October 2025, Genesis has rapidly established itself as a formidable new player in the ransomware landscape. This emerging cybercriminal group has caught