A critical vulnerability allows any domain user to remotely execute code on Veeam Backup & Replication servers attached to the domain – a nightmare for the security of backup infrastructures.
Table des matières
ToggleA worrying vulnerability that facilitates attacks
Veeam has just released a critical security update to correct several vulnerabilities in Veeam Backup & Replication (VBR), including a particularly worrying remote code execution (RCE) vulnerability. Identified as CVE-2025-23121, this flaw has been awarded the maximum CVSS score of 9.9/10, underlining its extreme criticality.
The vulnerability was discovered and reported by security researchers at watchTowr and CodeWhite, two teams renowned for their research into deserialization vulnerabilities.
The problem: too wide an entry point
The troubling feature of CVE-2025-23121 lies in its ease of exploitation: any authenticated domain user can exploit this vulnerability to obtain remote code execution on the backup server. Unlike many vulnerabilities requiring elevated privileges, this one only requires basic access to the Active Directory domain (source:BleepingComputer).
This flaw only affects VBR installations attached to a domain, but in many organizations this configuration is unfortunately common despite Veeam’s security recommendations.
Affected versions and patch
The vulnerability affects Veeam Backup & Replication 12.3.1.1139 and all earlier versions of branch 12. The patch has been integrated into version 12.3.2.3617, released on June 17, 2025 Veeam KB4743.
Two other vulnerabilities have also been patched in this update:
- CVE-2025-24286 (CVSS Score: 7.2) – Allowing a user with the “Backup Operator” role to modify backup tasks to execute arbitrary code
- CVE-2025-24287 (CVSS score: 6.1) – Local privilege escalation vulnerability in Veeam Agent for Windows
The technical expertise behind the discovery
watchTowr researchers have published a detailed technical analysis revealing that this vulnerability exploits weaknesses in blacklist-based security mechanisms. The problem lies in the uncontrolled deserialization of data via Veeam’s .NET Remoting channel.
As the researchers explain: “Blacklists are based on a very optimistic (and obviously flawed) idea that we can simply make a list of all malicious classes”. This approach proved insufficient in the face of the researchers’ creativity, who identified new exploitable classes in Veeam’s own code.
A particularly vulnerable ecosystem
The potential impact of this vulnerability is considerable, given Veeam’s popularity. According to official data, Veeam products are used by over 550,000 customers worldwide, including 82% of Fortune 500 companies and 74% of Global 2000 companies.
This widespread adoption makes Veeam servers particularly attractive targets for cybercriminals, especially ransomware groups who know that compromising backup infrastructure cripples victims’ ability to recover.
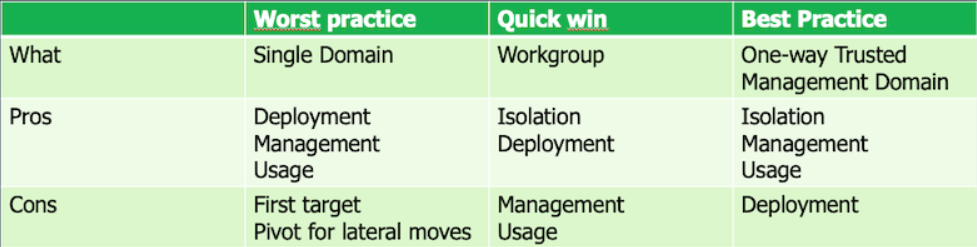
Good security practices ignored
Ironically, Veeam has long recommended in its best practice guides that backup servers should not be attached to the main domain. The official recommendation is to use a separate Active Directory forest or dedicated workgroup for the backup infrastructure.
Unfortunately, many organizations conveniently ignore these recommendations, creating exactly the conditions for the exploitation of CVE-2025-23121.
Worrying history of ransomware exploitation
This new vulnerability is part of a disturbing history of repeated exploitation of Veeam vulnerabilities by ransomware groups:
Recent documented attacks:
- CVE-2024-40711: Exploited by the Frag ransomware since November 2024(see related article)
- Akira and Fog: These groups used the same vulnerability as early as October 2024(see related article)
- Cuba ransomware: Historically targeted Veeam servers to steal credentials.
- FIN7: This APT group has been observed exploiting VBR vulnerabilities against critical infrastructures.
As ransomware operators have confided to BleepingComputer, they always target VBR servers as this simplifies data theft and blocks recovery efforts by deleting backups before deploying their payloads.
Immediate recommendations
Priority actions:
- Upgradeimmediately to Veeam Backup & Replication 12.3.2.3617
- Audit configuration: Check if your Veeam servers are attached to the domain
- Implement segmentation: Isolate backup infrastructure in a separate AD forest
- Monitor access: set up reinforced monitoring of connections to Veeam servers
- Multi-factor authentication: Enable 2FA for all Veeam administrative accounts
Recommended secure architecture:
- Use a dedicated Active Directory forest for Veeam
- Limit network access to backup servers
- Implement continuous monitoring for suspicious activity
- Maintain offline and air-gapped backups
A lesson in the limitations of blacklists
This vulnerability perfectly illustrates why blacklist-based security mechanisms are fundamentally flawed. As the researchers at watchTowr point out: “No matter how perfect your list is, someone will eventually find a way to exploit it”.
This reactive approach – adding entries to a blacklist after each discovery – proves insufficient in the face of the creativity of researchers and attackers who can identify new exploitation vectors in existing code.
Conclusion: A critical update not to be postponed
CVE-2025-23121 represents a major risk for any organization using Veeam Backup & Replication in a domain-attached configuration. The combination of a CVSS score of 9.9, ease of exploitation by any domain user, and a history of ransomware exploitation of Veeam vulnerabilities makes this a top priority.
Upgrading to version 12.3.2.3617 should be considered a security emergency. At the same time, it’s time to review the architecture of your backup infrastructure to bring it into line with Veeam’s recommended security best practices.
Experience shows that Veeam vulnerabilities are quickly exploited en masse. Don’t let your backup servers become the weak link in your security chain.
Sources :
