Cybercriminals are seizing on a new AI tool originally designed to strengthen cybersecurity to rapidly exploit zero-day vulnerabilities. This development marks another turning point in the digital arms race and is transforming the economics of cybercrime.
Artificial intelligence continues to radically change what we knew about cybersecurity until now – and, as you might expect, not necessarily for the better. HexStrike AI, an open source offensive framework developed by security researcher Muhammad Osama, initially designed to help security teams, was quickly hijacked by cybercriminals to automate their attacks. This malicious appropriation perfectly illustrates the dual nature of AI in cybersecurity: a tool that can strengthen defenses just as it can amplify threats exponentially.
Table des matières
ToggleA legitimate tool hijacked for malicious purposes
HexStrike AI bills itself as “a revolutionary AI-powered offensive security framework that combines professional security tools with autonomous AI agents”. The tool, available for free on GitHub since July 2025 where it has already collected over 1,800 stars and 400 forks, enables the integration of AI agents capable of automatically using over 150 cybersecurity tools for automated penetration testing and vulnerability discovery.
A revolutionary operating principle: HexStrike-AI acts as a “brain” orchestrating dozens of specialized AI agents. These agents can use recognized tools such as Nmap, Metasploit, Burp Suite, or John the Ripper, all in an autonomous and coordinated way. Users need only give general instructions such as “Perform a full security assessment of …” or “Find vulnerabilities in this application” for the system to automatically deploy a suitable tool chain.
Technical architecture: when AI orchestrates the attack
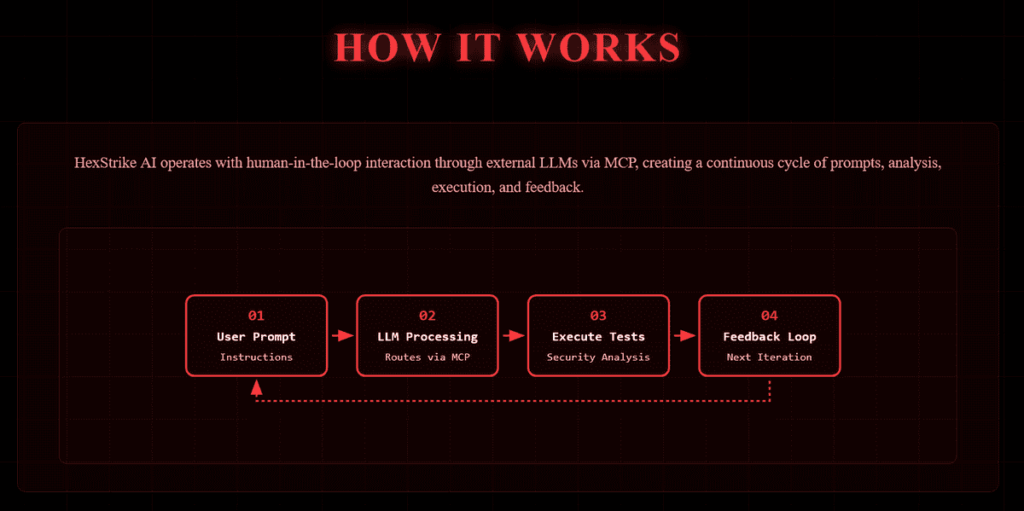
HexStrike AI’s architecture is based on Anthropic’s Model Context Protocol (MCP), which establishes a FastMCP server acting as a communication hub between the large language models (LLMs) – Claude, GPT, Copilot – and the tool functions. This approach enables fluid orchestration where commands can be issued programmatically without constant human intervention.
Here, LLMs act as reasoning and planning engines, breaking down attack objectives into logical steps, selecting appropriate tools according to context, interpreting intermediate results and dynamically adjusting the operating strategy. This contextual reasoning capability fundamentally distinguishes HexStrike AI from traditional fixed-sequence attack scripts.
The system integrates over 12 specialized autonomous AI agents, driven by these LLMs, with precise roles: IntelligentDecisionEngine for strategic planning, CVEIntelligenceManager for real-time vulnerability intelligence, and AIExploitGenerator for automated exploit creation. Each tool is abstracted into a standardized function, making orchestration transparent and automatic.
A particularly worrying feature is the client-integrated retry logic and recovery management. This ensures that operations continue reliably even in the event of failure, a critical feature when chaining together scans, exploits and persistence attempts. The system also includes security features such as Safe Mode and scope validation, ironically designed to limit abuse but easily bypassed by malicious actors.
This LLM-centric architecture transforms cyber attacks from rigid technical operations into adaptive processes driven by conversational artificial intelligence. In concrete terms, it is deployed through an automated workflow structured into four critical phases.
Automation and attack workflow: from reconnaissance to exfiltration
According to Check Point research, HexStrike AI automates the entire attack process, from initial reconnaissance to final data exfiltration. The framework orchestrates a complete workflow in four critical phases:
Phase 1 – reconnaissance and scanning: AI agents automatically perform sub-domain enumeration, service discovery and vulnerability identification on thousands of targets simultaneously.
Phase 2 – exploitation: the system automatically generates and adapts exploits according to the vulnerabilities discovered, testing different variants until success is achieved.
Phase 3 – persistence: once access has been gained, HexStrike AI automatically deploys webshells and establishes persistence mechanisms to maintain access to the compromised system.
Phase 4 – exfiltration: the framework structures the extraction of sensitive data into optimized AI workflows, considerably reducing the time needed to transfer information en masse off the target network.
Industrial performance and scalability
The LLM architecture described above radically transforms offensive capabilities on two complementary levels. On the one hand, it dramatically accelerates each individual stage of the attack process, reducing operations from days to minutes. On the other, it enables unprecedented industrialization through massive parallelization and dynamic adaptation, transforming artisanal cybercrime into a truly industrial process.
Quantified performance: when AI accelerates cybercrime
The performance of HexStrike AI v6.0 demonstrates an unprecedented acceleration in offensive capabilities according to the technical data available:
| Evaluation type | Manual time | HexStrike AI | Acceleration factor |
|---|---|---|---|
| Sub-domain enumeration | 24 hours | 5-10 minutes | x24 |
| Vulnerability scanning | 4-8 hours | 15-30 minutes | x16 |
| Web security tests | 6-12 hours | 20-45 minutes | x18 |
| Exploit development | 2-10 days | 30-120 minutes | x96 |
These figures, calculated by GBhackers, reveal a qualitative transformation in cybercrime: what used to require specialized teams for weeks on end can now be accomplished by a single operator in a matter of hours. The most impressive acceleration factor concerns exploit development, where HexStrike AI compresses a traditionally long and complex process into an automated procedure of less than two hours.
Industrial scalability and dynamic adaptation
HexStrike AI’s real strength lies in its ability to adapt and parallelize. Unlike traditional attacks limited by human resources, the framework can launch simultaneous attacks against thousands of targets, with each AI agent working independently while sharing information discovered.
Dynamic adaptation is a major advantage: if an exploitation or exfiltration technique fails, HexStrike AI automatically modulates its strategy in real time, testing alternative methods until success is achieved. This ability to learn and adapt considerably increases the success rate of attacks, transforming attempted intrusions into truly industrial campaigns.
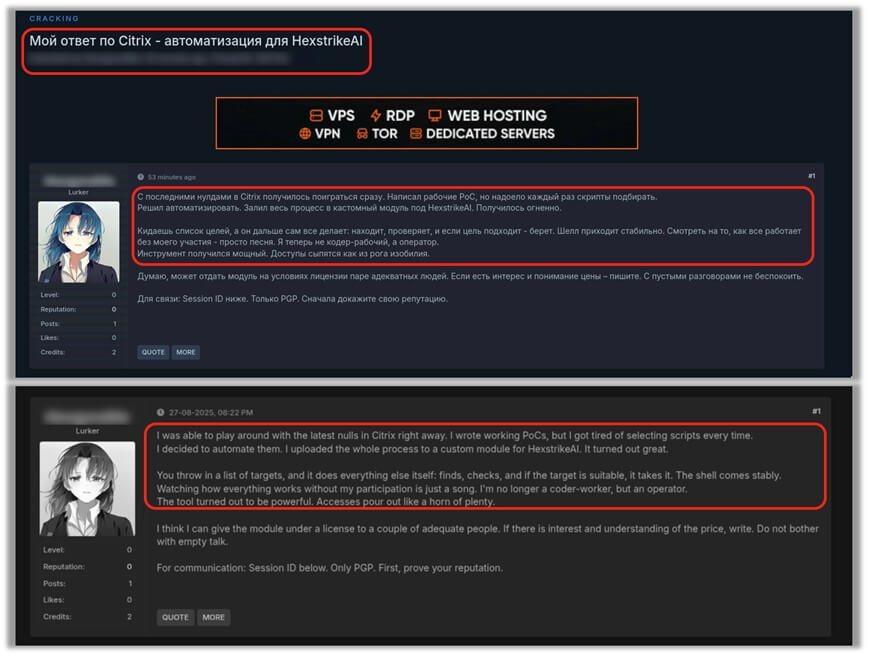
A cybercriminal describes this transformation on an underground forum: “I’m no longer a worker-coder, but an operator“, illustrating how AI raises the level of abstraction and democratizes access to advanced attack techniques. This evolution marks the shift from artisanal cybercrime requiring specialized technical skills to an industrialized model where technical expertise is encapsulated in AI orchestration.
Express exploitation of Citrix vulnerabilities
The formidable effectiveness of HexStrike AI was demonstrated in the recent disclosure of three critical vulnerabilities affecting Citrix NetScaler ADC and Gateway appliances. Vulnerabilities CVE-2025-7775, CVE-2025-7776 and CVE-2025-8424 were rapidly exploited by cybercriminals using this framework, according to Check Point researchers who observed significant discussion on the dark web.
Accelerated exploitation timeline
The CVE-2025-7775 vulnerability, considered the most critical with a CVSS score of 9.2, allows remote code execution without authentication. Traditionally, exploiting such vulnerabilities requires “highly skilled operators and weeks of development“ to understand memory operations, authentication bypasses and the peculiarities of the NetScaler architecture.
With HexStrike AI, this timeline collapses dramatically. Check Point researchers report that within 12 hours of the vulnerabilities being disclosed, malicious actors were already claiming to be using HexStrike AI to scan and exploit vulnerable NetScaler instances, reducing exploitation time “from days to less than 10 minutes“.
Extent of the threat and commercialization of access
According to Bleeping Computer, data from the ShadowServer Foundation reveals the scale of the threat: almost 8,000 endpoints remained vulnerable to CVE-2025-7775 as of September 2, 2025, down from 28,000 the previous week. This decrease, while encouraging, still leaves thousands of systems exposed to automated attacks.
Cybercriminals are not content to simply exploit these vulnerabilities: they are now offering compromised NetScaler instances for sale on underground forums, creating a veritable market for illegal access to critical infrastructures. This immediate commercialization of compromised access illustrates the transformation of vulnerability exploitation into an industrial process.
Impact on the ransomware economy
HexStrike AI is fundamentally transforming the criminal economy, democratizing access to advanced attack techniques and creating new business models based on automation. This evolution is redefining the rules of the ransomware market and accelerating the professionalization of cybercrime.
Lowering the technical threshold
AI orchestration enables less skilled players to execute complex campaigns, considerably expanding the ransomware-as-a-service (RaaS) market. This democratization increases competition between criminal groups, driving prices down while exponentially multiplying the number of attacks. Script kiddies could now orchestrate expert-level attacks simply by giving natural language instructions to the AI.
New criminal business models
Attacks that used to take weeks and mobilize entire teams can now be launched in parallel on thousands of targets with a single operator. This industrial scalability favors mass ransomware and enables cybercriminals to enrich themselves rapidly. Criminal groups can now adopt automated mass-attack strategies, targeting freshly disclosed vulnerabilities on a massive scale.
Increased profitability
From a financial point of view, HexStrike AI revolutionizes the economics of attack: drastically reducing the duration and costs of a campaign, multiplying opportunities for “successful runs” (successful exfiltration, ransom obtained), and facilitating the resale of access and data on criminal marketplaces. The return on investment of malicious campaigns improves exponentially.
Compression of attack cycles
Compromised accesses are immediately resold, triggering chain ransomware operations in sensitive sectors, with virtually zero intervention and mitigation time for victims. This speed of execution dramatically compresses the defensive reaction window, transforming the cybersecurity ecosystem into a permanent race against the clock.
The creator’s position, systemic risks and countermeasures
The malicious appropriation of HexStrike AI raises fundamental questions about the responsible development of AI tools in cybersecurity. Between the creator’s defensive intentions, the inherent risks of misappropriation and the new vulnerabilities of AI agents, this situation perfectly illustrates the challenges of security innovation in the age of conversational artificial intelligence.
The creator’s position: defend before you attack
When asked by The Register about the abuse potential of his framework, Muhammad Osama, the creator of HexStrike AI, maintains that his tool was “built as a defender-oriented framework to speed up penetration testing”. He stresses that the aim is to help defenders discover vulnerabilities before attackers, using AI to simulate various attack paths at machine speed.
Nevertheless, he acknowledges that:“Like other security frameworks, it can be misused, but it doesn’t include pre-built zero-day exploits. It automates workflows, and others can insert their own logic.” He also reveals that he has “held back the release of the RAG (Retrieval-Augmented Generation)-based version, which can dynamically integrate CVE intelligence and adjust tests in real time“, to carefully balance empowering defenders and limiting abuse.
In statements reported by Cybernews, its defensive vision remains resolutely optimistic:“Defenders have a unique opportunity to tip the balance in their favor. Attackers often move opportunistically and chaotically, whereas defenders, if they embrace automation and AI-driven orchestration, can build systematic, adaptive and resilient defenses that exceed what manual processes allow.“
The dual-use dilemma: when defense tools become weapons
HexStrike AI perfectly illustrates the dual-use dilemma of AI technologies in cybersecurity. This problem goes beyond the scope of this specific tool, and raises fundamental questions about the development of AI tools for security.
Recent research by Alias Robotics and Oracle Corporation reveals that cybersecurity AI agents like PentestGPT carry high risks of prompt injection, effectively turning security tools into cyber weapons via hidden instructions. This intrinsic vulnerability of AI systems directly threatens the penetration testers and security teams who deploy these tools, creating a paradox where defenders expose themselves to new risks as they attempt to strengthen their defensive capabilities.
A paradigm shift in cybersecurity
The emergence of HexStrike AI marks a pivotal moment in the evolution of cyber threats. Amit Weigman, Director of Solutions Engineering at Check Point, points out that “the window between disclosure and mass exploitation is shrinking dramatically“. This time compression transforms the cybersecurity ecosystem into a permanent race against time.
This paradigm shift is forcing organizations to rethink their defense strategies: traditional patch cycles, measured in weeks, are becoming obsolete when exploitation time is now measured in hours. Check Point research confirms that “HexStrike AI represents a broader paradigm shift, where AI orchestration will increasingly be used to weaponize vulnerabilities quickly and at scale“.
Recommendations for security teams
In the face of this new threat, Check Point research recommends that defenders adopt an urgent, multi-layered approach:
- adaptive detection: static signatures and rules will no longer suffice. Detection systems must ingest fresh intelligence, learn from ongoing attacks and adapt dynamically
- AI-driven defense: just as attackers build orchestration layers, defenders must deploy AI systems capable of correlating telemetry, detecting anomalies and responding autonomously at machine speed
- drastically shorten patch cycles: when uptime is measured in hours, patching can no longer be a process lasting several weeks. Automated patch validation and deployment pipelines become essential
- merging threat intelligence: monitoring dark web discussions and underground forums is becoming a critical defensive input. Early signals provide vital preparation time
- resilience engineering: assume compromise and architect systems with segmentation, least privilege and robust recovery capabilities, so that successful exploitation does not mean catastrophic impact.
The future: an even more powerful version in the pipeline
The developer plans to release a major update in the near future, HexStrike AI v7.0, which will extend capabilities to over 250 AI agents and tools, with one-command configuration, Docker support, a native desktop client and a fully integrated RAG system enabling real-time adaptation to zero-days and dynamic exploit search. This evolution promises next-generation defensive automation, but also risks amplifying offensive capabilities.
Conclusion: when AI redefines cyber warfare
HexStrike AI represents the concrete embodiment of a conceptual architecture that Check Point Research had anticipated: a central orchestration brain directing specialized AI agents. What was once theoretical is now operational, and attackers waste no time in exploiting it.
This evolution transcends the mere technical problem to become a fundamental change in the very nature of cyberattacks. Intelligent automation now enables less skilled actors to execute sophisticated attacks, democratizing advanced cybercrime and transforming the digital underground economy.
The industrialization of cybercrime through AI is creating an ecosystem where attacks are being deployed at an unprecedented scale and speed, forcing defenders to abandon their traditional approaches and embrace intelligent automation too.
For defenders, the urgency is threefold: address current vulnerabilities with unprecedented speed, prepare for a future where AI-driven orchestration will be the norm, and develop AI countermeasures capable of rivaling the growing sophistication of offensive tools. The sooner the security community adapts – by patching faster, detecting smarter and responding at machine speed – the greater will be our ability to keep pace in this new era of industrialized cyber conflict.
The advent of HexStrike-AI definitively confirms what the security community feared: the convergence between AI orchestration and offensive tooling was not theoretical. What seemed like an emerging possibility is now an operational reality, redefining the rules of the cybersecurity game for years to come.
Main article sources :
- Check Point Research: HexStrike AI: When LLMs Meet Zero-Day Exploitation
- The Register: HexStrike AI Citrix exploits
- Cybernews: AI brain HexStrike runs cyberattacks on its own
- FedNinjas: HexStrike-AI tool exploits n-day flaws
- BleepingComputer: Hackers use new HexStrike-AI tool to rapidly exploit n-day flaws
- GBHackers: HexStrike AI Links Security Tools
- Vulert: HexStrike-AI weaponized: threat actors exploit
- Artificial Intelligence News : AI hacking tool exploits zero-day security vulnerabilities in minutes
- Security Affairs: Crooks turn HexStrike AI into a weapon for fresh vulnerabilities
