A new strain of ransomware dubbed HybridPetya was revealed by ESET Research researchers in September 2025. This sophisticated malware represents a worrying fusion between the destructive techniques of 2017’s infamous NotPetya and the recovery capabilities of the original Petya, while adding modern UEFI Secure Boot bypass features that make it particularly formidable.
Samples of this ransomware were initially uploaded to VirusTotal in February 2025 from Poland under various evocative file names such as “notpetyanew.exe”, immediately suggesting a filiation with the malware that caused over $10 billion in damage in the 2017 attack.
Table des matières
ToggleA sophisticated technical legacy: from Petya to NotPetya
To understand the threat posed by HybridPetya, it’s worth recalling the evolution of its predecessors. Petya, discovered in March 2016, was an innovative ransomware that, unlike traditional strains, did not encrypt individual files but attacked the Master File Table (MFT) of NTFS partitions directly. This approach rendered the entire file system inaccessible while preserving data, theoretically enabling recovery after payment of the ransom.
NotPetya, which appeared in June 2017, marked a dramatic turning point in the history of cyberattacks. Although it shared many characteristics with Petya, NotPetya was actually a destructivewiper (malware designed to permanently destroy data without the possibility of recovery) disguised as ransomware. Recovery of decryption keys from victims’ personal installation keys was impossible, making data restoration impractical. This cyberattack, considered the most destructive in history, initially targeted the Ukraine via a booby-trapped update to the M.E.Doc accounting software, before spreading worldwide. According to ESET Research analysts “unlike the original NotPetya (and the Petya ransomware too), HybridPetya is also capable of compromising modern UEFI-based systems by installing a malicious EFI application on the EFI system partition.”
HybridPetya’s technical innovations
Malware architecture and components
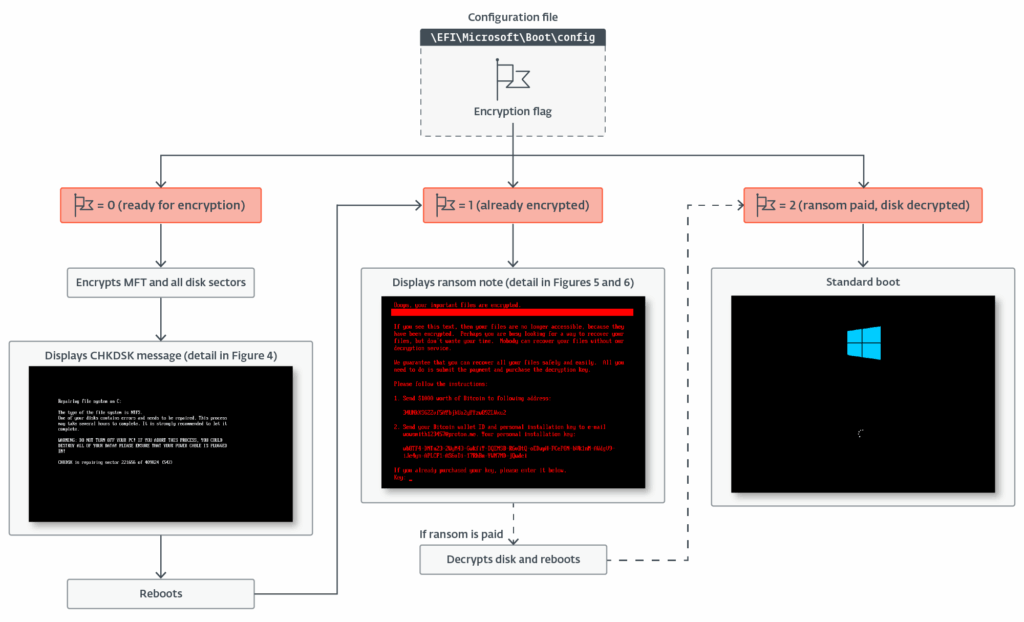
HybridPetya features a sophisticated architecture consisting of two main components: a bootkit and an installer. The system uses an encryption flags mechanism to manage the state of infection:
- 0: system ready for encryption
- 1: disk already encrypted
- 2: ransom paid, disk decrypted
This structured approach enables the malware to efficiently manage the different phases of the attack and maintain a consistent state even after a system reboot.
Exploiting CVE-2024-7344: bypassing Secure Boot
HybridPetya’s most worrying capability lies in its exploitation of CVE-2024-7344, a critical UEFI Secure Boot bypass vulnerability discovered by ESET in July 2024. This flaw affects the “reloader.efi” UEFI application developed by Howyar Technologies, signed by the Microsoft Corporation UEFI CA 2011 third-party certificate.
The vulnerability stems from the use of a custom PE loader instead of the standard UEFI LoadImage and StartImage functions. This flawed implementation allows the application to load any UEFI binary, even unsigned ones, from a specially crafted file named “cloak.dat”, during system boot, regardless of the Secure Boot UEFI state.
The operating process follows a precise pattern:
- Replacement of the legitimate Windows bootloader by the vulnerable “reloader.efi
- Deployment of the “cloak.dat” file containing the malicious UEFI application encoded via XOR
- Exploit vulnerability during reboot to bypass Secure Boot
- Execution of malicious code with elevated privileges before operating system startup
Infection and encryption process
The HybridPetya infection process follows a sophisticated sequence that begins with the identification of the system type. The installer checks whether the system uses UEFI with GPT partitioning by retrieving disk information and looking for the EFI system partition identified by PARTITION_SYSTEM_GUID.
Once the EFI partition has been identified, the malware proceeds with the following steps:
- Remove the rescue bootloader: delete “EFIBootBootx64.efi”.
- Deployment of the encryption configuration: installation of the “EFIMicrosoftBootconfig” file containing the Salsa20 key, the 8-byte nonce and the victim’s personal installation key.
- Creation of the verification file: deployment of “EFIMicrosoftBootverify” containing an array of 0x200 bytes with the value 0x07
- Legitimate bootloader backup: copy “EFIMicrosoftBootbootmgfw.efi” to “EFIMicrosoftBootbootmgfw.efi.old”.
The encryption process specifically targets NTFS-formatted partitions by identifying all connected storage devices, then checking the NTFS signature “NTFS” in the first bytes of each partition. The bootkit then encrypts the Master File Table (MFT) using the Salsa20 algorithm, rendering the entire file system inaccessible.
User interface and ransomware
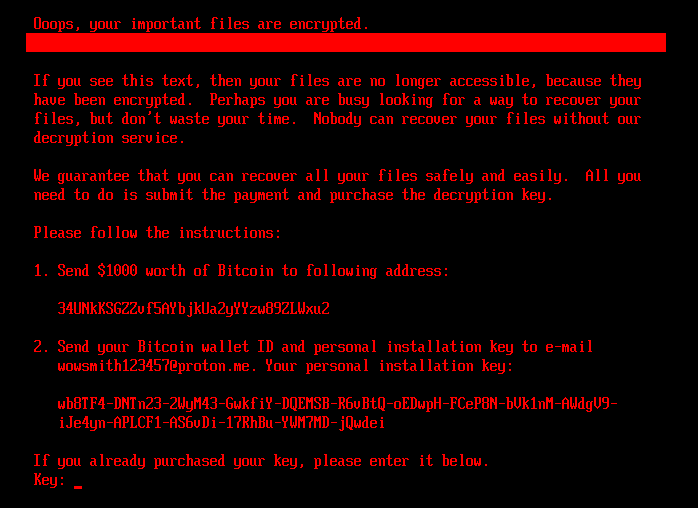
When the system detects that the disk is encrypted (flag = 1), HybridPetya displays a ransom note demanding $1,000 in Bitcoin to be sent to the specified wallet address (34UNkKSGZZvf5AYbjkUa2yYYzw89ZLWxu2). This Bitcoin address was empty at the time of ESET’s analysis, although it had received $183.32 between February and May 2025 according to The Hacker News.
The ransom note retains the visual format of the original NotPetya, but shows significant variations depending on the version. The variant deployed with Secure Boot bypass uses the email address “wowsmith999999@proton[.]me”, while the one deployed by standard installers uses “wowsmith1234567@proton[.]me”. This differentiation suggests either distinct groups or deliberate segmentation of campaigns.
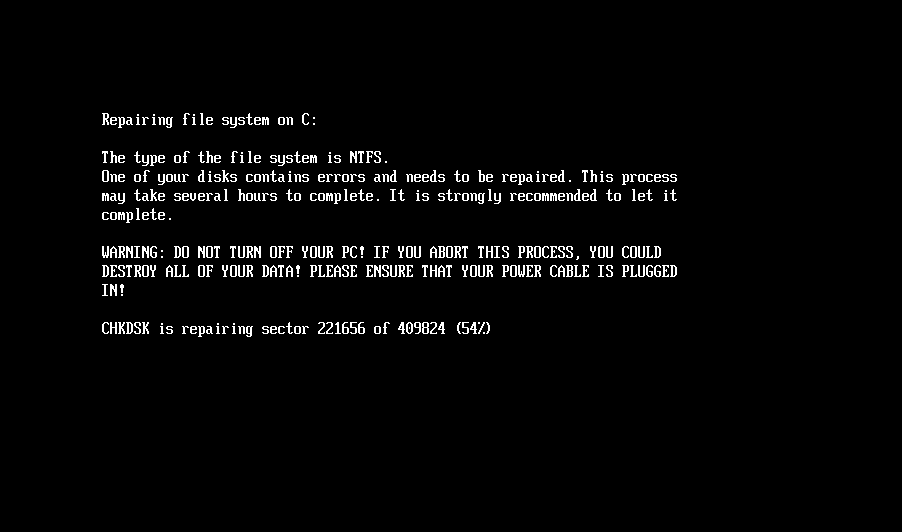
During the encryption process, HybridPetya displays fake CHKDSK messages identical to those of NotPetya, fooling victims into believing that the system is performing routine maintenance rather than malicious encryption. This misinformation technique enables the malware to operate without arousing suspicion for extended periods.
A crucial difference with NotPetya: recoverability
Unlike NotPetya, HybridPetya actually enables data recovery. ESET researchers point out: ” Interestingly, despite the file names on VirusTotal and the format of the ransom note in the current samples suggesting that they could be related to NotPetya, the algorithm used to generate the victim’s personal installation key, unlike the original NotPetya, allows the malware operator to reconstruct the decryption key from the victims’ personal installation keys “. This fundamental feature, inspired by the RedPetyaOpenSSL PoC, makes HybridPetya a true commercial ransomware rather than a purely destructive tool like NotPetya.
The decryption process follows a sophisticated reverse logic: after verifying the key provided by the victim by decrypting the “verify” file, the bootkit reads the number of encrypted clusters from the “counter” file and proceeds to decrypt precisely the same number of clusters. This approach guarantees complete and consistent restoration of the file system.
UEFI bootkit context and threat escalation
HybridPetya represents the fourth publicly known example of a real or proof-of-concept UEFI bootkit with Secure Boot bypass functionality. It joins a worrying list including BlackLotus (exploiting CVE-2022-21894), BootKitty (exploiting LogoFail), and the PoC Hyper-V Backdoor (exploiting CVE-2020-26200).
This proliferation demonstrates that Secure Boot bypasses are no longer theoretical threats, but are becoming increasingly common and attractive techniques for researchers and attackers alike. BlackLotus, for example, was sold for $5,000 on the dark web and could run on fully-updated Windows 11 systems with Secure Boot enabled.
Firmware-level attacks represent a significant escalation in malware sophistication, as they operate at such a low level that they survive formatting, complete system reinstallations, and even hard disk changes. This maximum persistence makes detection and removal extremely difficult for traditional security solutions.
Implications for organizational security
The emergence of HybridPetya underlines a fundamental transformation of the threat landscape. As Eclypsium’s analysis highlights, this malware perfectly illustrates why traditional detection approaches fail when faced with firmware-level threats. When malware operates at UEFI level, it resides in the “dusty corners” of the IT infrastructure, where most security tools offer no visibility.
Traditional antivirus solutions, EDR platforms and threat hunting tools typically operate at or above the operating system level. They look for malicious processes, suspicious network connections and abnormal file system activity. But HybridPetya establishes itself before these monitoring systems even begin to operate.
Current status and threat assessment
According to ESET’s telemetry, no active use of HybridPetya in the wild has been detected. Researchers suspect that this could be a proof of concept developed by an unknown security researcher or threat actor. This hypothesis is reinforced by the recent discovery of a Petya UEFI PoC by researcher Aleksandra “Hasherezade” Doniec, suggesting a possible relationship between the two projects.
Unlike NotPetya, HybridPetya does not appear to have the aggressive network propagation capabilities that enabled its predecessor to cause massive damage in 2017. NotPetya used the EternalBlue exploit to spread from machine to machine, transforming the attack into a veritable digital epidemic. HybridPetya apparently favors persistence over propagation, a tactical choice that favors stealth over immediate impact.
Protection measures and recommendations
The CVE-2024-7344 vulnerability has been patched by Microsoft in the Patch Tuesday update of January 14, 2025. Windows systems that have applied this update or later versions are protected against HybridPetya. Microsoft has also revoked the vulnerable binaries in its revocation database (dbx).
Organizations can check their exposure to this vulnerability by using specific PowerShell commands to check the status of Secure Boot databases. On Linux systems, the dbxtool tool can be used to check that the necessary revocations are installed.
Experts recommend a multi-layered security approach including :
- Bootloader integrity monitoring: establishing baselines for the contents of the EFI system partition and monitoring for unauthorized changes
- Boot chain analysis: continuous monitoring of the complete boot sequence, from firmware to OS
- Secure Boot status check: regular validation of Secure Boot activation and operation
- Privilege management: limit the administrator rights required to access the EFI system partition
Conclusion: the continuing evolution of UEFI threats
HybridPetya represents a significant milestone in the evolution of ransomware, marking the entry of bootkit techniques into the modern ransomware ecosystem. Although not actively deployed, its technical capabilities – MFT encryption, UEFI compatibility and Secure Boot bypass – make it a worrying model for future threats.
This discovery confirms that firmware security can no longer be a secondary consideration. The cybersecurity industry must adapt its strategies to include firmware-level monitoring and protection, fundamentally transforming the approach to endpoint security in a context where attackers increasingly operate “under the operating system”.
Main article sources :
- ESET Research: Introducing HybridPetya: Petya/NotPetya copycat with UEFI Secure Boot bypass
- ESET Research : Under the cloak of UEFI Secure Boot: Introducing CVE-2024-7344
- ESET Research : BlackLotus UEFI bootkit: Myth confirmed
- ESET Research : Bootkitty: Analyzing the first UEFI bootkit for Linux
- The Hacker News: New HybridPetya Ransomware Bypasses UEFI Secure Boot With CVE-2024-7344
- Eclypsium: HybridPetya Shows Why Firmware Security Can’t Be an Afterthought
- G Data Software: Ransomware Petya: A Technical Review
- Wired: NotPetya cyberattack Ukraine Russia code crashed the world
