A massive identity theft campaign is currently hitting over 100 leading companies worldwide. Behind this offensive is the cybercriminal alliance Scattered LAPSUS$ Hunters (SLSH), which includes ShinyHunters, one of the most prolific groups in English-speaking cybercrime. Unlike traditional automated attacks, these intrusions rely on advancedsocial engineering techniques, combining fraudulent phone calls and sophisticated phishing kits capable of bypassing even the most robust multi-factor authentication systems.
Table des matières
ToggleA real-time threat to SSO platforms
Threat intelligence firm Silent Push identified as early as January 26, 2026 a massive infrastructure deployed to target Okta Single Sign-On (SSO) accounts and other single sign-on platforms used by hundreds of global enterprises. This campaign does not rely on conventional automated attack tools: it uses a human, interactive approach known as vishing (voice phishing).
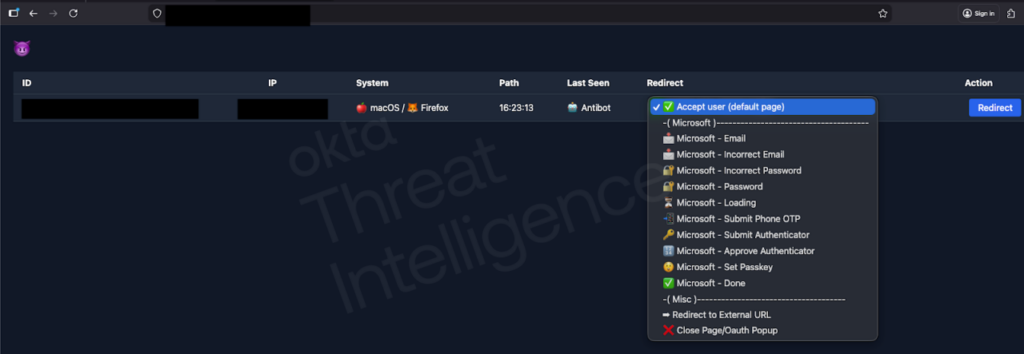
Attackers use a live phishing panel that enables them to interpose themselves in real time during an authentication session, posing as IT support while simultaneously manipulating the web pages displayed in the victim’s browser.
Mandiant, Google’s threat intelligence division, confirmed in a statement on January 28, 2026 that this is an active and ongoing campaign. Charles Carmakal, Chief Technology Officer at Mandiant Consulting, says: “Mandiant is tracking a new, ongoing campaign under the ShinyHunters brand, using advanced voice phishing techniques to successfully compromise victim organizations’ SSO credentials and enroll attacker-controlled devices in victims’ multi-factor authentication solutions.”
MFA bypass through social manipulation
The formidable effectiveness of these attacks lies in their ability to neutralize multi-factor authentication (MFA), despite it being considered a fundamental security measure. The phishing kits used by attackers feature several technical characteristics that make them particularly dangerous.
On January 22, 2026,Okta Threat Intelligence published a detailed analysis of these new phishing kits designed specifically for vishing operations. Brett Winterford, Vice President at Okta Threat Intelligence, explains, “These kits can be adapted on the fly by callers to control the pages presented in the user’s browser, in order to synchronize with the caller’s script and the real MFA challenges the caller faces when trying to log in.”
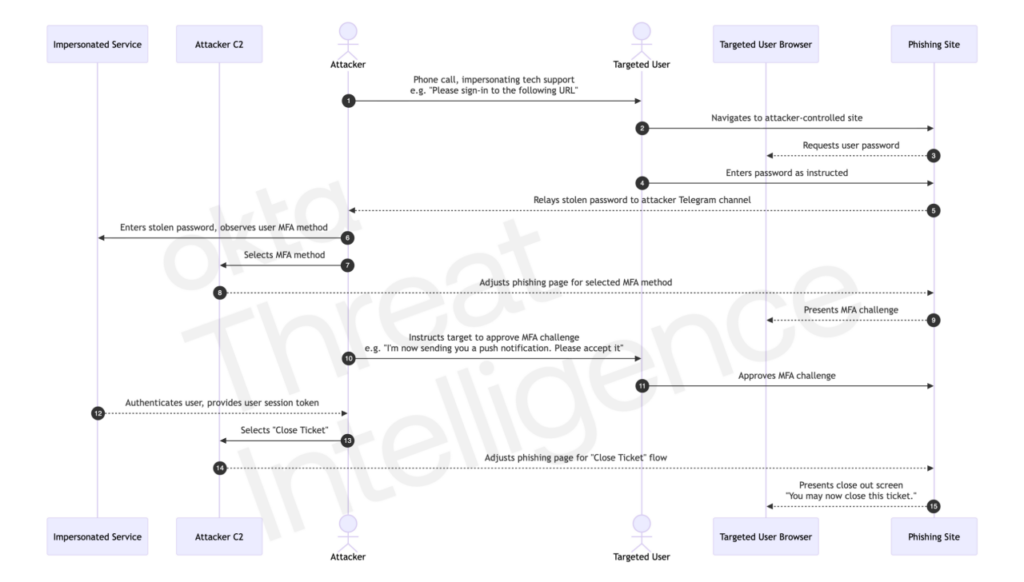
The attack process typically proceeds according to this scenario:
- the attacker contacts his target posing as the IT helpdesk, claiming an urgent technical problem requiring identity verification ;
- the victim is directed to a phishing site that perfectly reproduces the legitimate login interface (Okta, Microsoft Entra, Google Workspace);
- when the victim enters his/her credentials, they are immediately passed on to the attackers, who attempt a real connection to the legitimate service;
- the system triggers an MFA request (SMS code, push notification or temporary code);
- the attackers then synchronize the fake site to display exactly the same type of challenge, giving the impression of a normal procedure;
- the victim approves the challenge or enters the code, thinking they are acting on a legitimate platform, when in fact they are allowing the cybercriminals access.
Moussa Diallo, threat researcher at Okta, explains: “Using these kits, an attacker on the phone with a targeted user can control the authentication flow while that user interacts with credential phishing pages. They can control the pages the target sees in their browser in perfect sync with the instructions they provide during the call. The threat actor can use this synchronization to defeat any form of MFA that is not phishing-resistant.”
Over 100 global companies in the firing line
Silent Push published a list of organizations specifically targeted by this campaign over the past 30 days on January 26, 2026. The list, which includes over 100 companies, covers virtually every economic sector: technology, finance, healthcare, energy, real estate, telecommunications, and even legal services.
Among the targets identified are major names: Atlassian, Canva, Epic Games, HubSpot, RingCentral, ZoomInfo in the technology sector; Moderna, Biogen, Gilead Sciences, Amgen in biotech and pharmaceuticals; Apollo Global Management, Blackstone, State Street, RBC in financial services; Halliburton, Sempra Energy, American Water in energy and critical infrastructure; and Telstra in telecommunications.
This sectoral diversification demonstrates that attackers are not targeting a specific industry, but rather organizations using SSO platforms such as Okta. Once compromised, an SSO account becomes a veritable digital master key, giving access to a company’s entire application ecosystem: messaging, cloud storage, collaboration tools, customer databases, management systems and much more.
First victims confirmed and data exposed
Several organizations have already publicly confirmed that they have fallen victim to the campaign. Hudson Rock security researcher Alon Gal revealed on January 23, 2026 that he had been contacted directly by ShinyHunters, who claimed responsibility for the attacks and confirmed the use of vishing kit services to compromise numerous organizations using Okta.
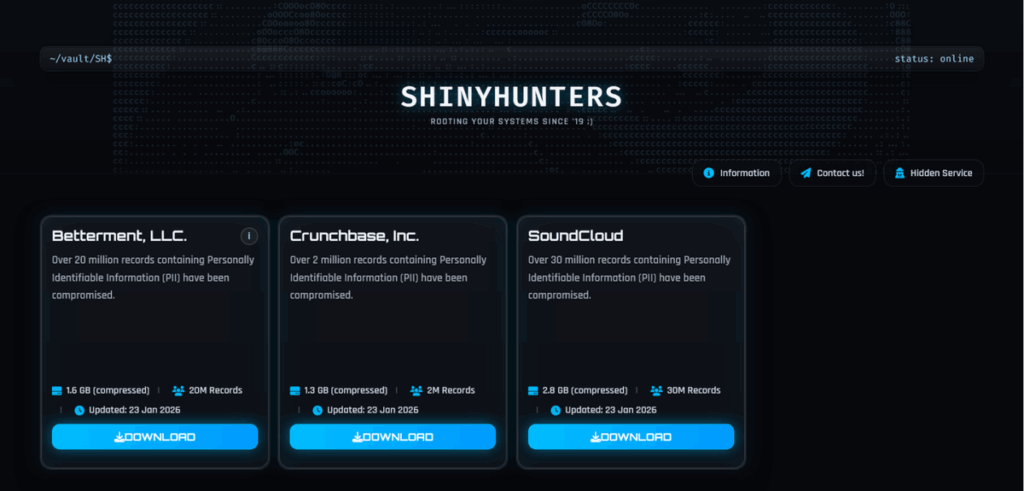
Following the failure of their extortion attempts, the group published the information stolen from three organizations on their Data Leak Site:
- Betterment: over 20 million records concerning this automated financial services and investment platform. The company confirmed on January 9, 2026 that an attacker had gained access to some of its systems via a social engineering attack and that customer data had been stolen, although no accounts had been directly compromised;
- Crunchbase: over 2 million records including personally identifiable information and various corporate data, including signed contracts;
- SoundCloud: more than 30 million recordings, affecting around 20% of the audio streaming platform’s user base, i.e. some 36 million people. The company discovered the intrusion in mid-December 2025 and confirmed that personally identifiable data had been compromised.
Interviewed by Cybersecurity Dive, Rafe Pilling, Director of Threat Intelligence at Sophos Counter Threat Unit, said his team was tracking around 150 malicious domains created in December 2025 and used in vishing campaigns that led to data theft and extortion requests. “We can’t confirm that they’ve all been used, but threat actors are creating target-specific domains designed to mimic single sign-on services and impersonate providers like Okta,” he said.
Scattered LAPSUS$ Hunters: a formidable criminal alliance
This campaign is a continuation of the operations carried out by Scattered LAPSUS$ Hunters, a cybercriminal alliance that federates three of the most notorious groups in the English-speaking ecosystem: Scattered Spider, LAPSUS$ and ShinyHunters. This coalition, which appeared publicly in August 2025, combines Scattered Spider’s expertise in social manipulation, LAPSUS$’s extortion capabilities and ShinyHunters’ specialization in massive data exfiltration.
The FBI and Google Threat Intelligence Group are tracking this threat under the identifiers UNC6040 and UNC6395. In an advisory published in September 2025, the FBI already warned of the intensive use of vishing and manipulation techniques to compromise cloud and SaaS platforms.
This decentralized structure enables the group to run several large-scale campaigns simultaneously. In 2025, Scattered LAPSUS$ Hunters orchestrated a massive campaign against the Salesforce ecosystem, compromising over 760 companies and claiming to have stolen over 1.5 billion registrations from giants such as Toyota, FedEx, Disney, Cisco, Marriott and McDonald’s. This offensive was based on the compromise of third-party applications connected to Salesforce, notably Salesloft Drift, whose stolen OAuth tokens enabled access to hundreds of customer instances.
An intensifying attack strategy
Cyberthreat experts note the increasing professionalization of these techniques. Cynthia Kaiser, Senior Vice President of Halcyon’s Ransomware Research Center, points out: “Although these campaigns occur frequently, the difference here lies in the slightly higher success rate of the recent campaign. This is probably due to the credible content and the use of vishing rather than simple phishing. When you get a call, it’s personalized and it changes in real time, it sounds credible, it’s a different element that people don’t necessarily have their guard up for.”
This evolution in attack tactics illustrates the trends identified in our article on cybersecurity experts’ predictions for 2026. Social engineering is taking on a new level thanks to the integration of artificial intelligence, which can generate perfectly worded and contextually appropriate communications, making it increasingly difficult to distinguish between a legitimate message and an attempted scam.
The combination of highly personalized voice attacks with sophisticated technical tools creates a particularly difficult attack vector for organizations to counter, even those with robust perimeter defenses.
Consequences for victims: far beyond data theft
Once initial access has been gained by compromising SSO accounts, attackers deploy a methodical strategy to maximize their gains. They immediately proceed with the systematic exfiltration of sensitive data: customer information, employee personal data, industrial secrets, internal communications and contractual documents. At the same time, they register their own devices in the victims’ MFA systems, ensuring persistent access even after the intrusion has been discovered. This massive collection is accompanied by a methodical advance into the victim’s cloud environment, where cybercriminals access collaboration applications such as Slack or Microsoft Teams to manipulate other employees and gain even higher privileges.

The final phase follows the now-standard double extortion model: the group threatens to publish the stolen data if victims refuse to pay. In some cases, as confirmed by Mandiant, the attackers also encrypt the data after exfiltration. Silent Push sums up the severity of the threat:“Once an Okta or other SSO provider session is hacked, the attacker has a master key to every application in your environment.“
Recommendations for protection against this threat
Given the intensity and sophistication of this campaign, security experts recommend a multi-dimensional defensive approach combining technical and organizational measures.
Phishing-resistant authentication
Okta places particular emphasis on one critical point: not all forms of MFA are created equal. Methods based on SMS codes, conventional push notifications or temporary codes (TOTP) remain vulnerable to real-time attacks such as those deployed by ShinyHunters.
Organizations need to migrate to phishing-resistant authentication methods:
- FIDO2 security keys (such as YubiKey) that use public key cryptography and link authentication to the legitimate domain;
- cryptographicpasskeys that transmit no secrets over the network;
- proprietary solutions such as Okta FastPass, which implement similar cryptographic binding mechanisms.
These technologies make Adversary-in-the-Middle attacks technically impossible, as no identifiers or tokens are transmitted over the network, and authentication is cryptographically linked to the legitimate domain.
Reinforced access controls
Organizations must also implement strict contextual controls that analyze every access attempt according to multiple criteria. Active monitoring of new device registration events, particularly when immediately followed by connections from unusual IP addresses, enables early detection of compromise. Continuous behavioral analysis identifies deviations from normal usage patterns: atypical connection times, inconsistent geolocation, or unusual access types for a given user. These detection mechanisms must be accompanied by geographical and network restrictions appropriate to the context of each organization, limiting exposure to the attack vectors commonly used by cybercriminals.
Staff awareness and training
The human dimension remains the most critical element. Organizations need to implement specific vishing awareness programs that go far beyond conventional anti-phishing training. When an organization is identified as the target of an active campaign, information must be communicated immediately to all employees, with concrete examples of the techniques used. It is essential to establish protocols requiring verification of the identity of any caller claiming to represent IT support, via an independent communication channel such as a callback on a known and validated official number.
Employees must feel encouraged and legitimate to immediately report any suspicious call to the security department, without fear of appearing paranoid. Dedicated reporting channels, quick and easy to access, facilitate this critical feedback. Finally, the regular organization of vishing simulation exercises enables staff to test their real resilience in the face of such attacks, to identify behavioral vulnerabilities specific to each team, and to adjust training according to the results observed.
Silent Push also recommends the use of predictive intelligence systems capable of detecting DNS-level attack infrastructures even before vishing campaigns begin. Their Indicators of Future Attack™ (IOFA™) technology can block malicious domains imitating authentication platforms before they become operational.
A persistent threat that is constantly evolving
The formal attribution of this campaign remains complex. While the group publicly uses the ShinyHunters brand, Ian Gray, Vice President of Intelligence at Flashpoint, reminds us that “a cybercriminal or group can use any username they choose and apply it to a data leak site, but that doesn’t prove a direct link.”
Nevertheless, the tactics, techniques and procedures (TTPs) observed correspond precisely to the documented methods of Scattered LAPSUS$ Hunters. What particularly worries experts is the scalability of these attacks. Unlike intrusions requiring the exploitation of complex technical vulnerabilities, vishing assisted by sophisticated kits can be deployed on a massive scale with relatively limited human resources. The professionalization of tools makes these capabilities accessible even to technically unskilled affiliates, democratizing access to frighteningly effective attack techniques.
Digital identity: the new security perimeter to defend
The vishing campaign orchestrated by ShinyHunters and the Scattered LAPSUS$ Hunters alliance illustrates a fundamental shift in the cyberthreat landscape. Attackers now target the identity layer directly, rather than network infrastructures or endpoints, rendering traditional perimeter defenses largely obsolete.
This evolution requires organizations to radically rethink their security posture. Traditional multi-factor authentication, long considered a sufficient bulwark, is no longer sufficient in the face of adversaries capable of simultaneously manipulating the technical and human dimensions of an attack.
Effective response requires a holistic approach combining phishing-resistant technologies, rigorous contextual access controls, advanced behavioral surveillance, and above all an organizational culture of vigilance where every employee understands his or her role in the collective defense.
As cybercriminals continue to refine their techniques and artificial intelligence amplifies their capabilities, the race between attackers and defenders intensifies. The organizations that survive will be those that have anticipated this new reality and built their resilience on solid foundations, both technical and human.
Sources :
Silent Push: Special Alert: SLSH Malicious “Supergroup” Targeting 100+ Organizations via Live Phishing Panels
Okta Blog: Phishing kits adapt to the script of callers
BleepingComputer: Okta SSO accounts targeted in vishing-based data theft attacks
Hackread: Scattered Lapsu$ Hunters Target 100+ Global Organisations in New Identity Theft Campaign
SOCRadar: Okta Vishing Campaign Allegedly Linked to ShinyHunters
CyberScoop: Real-Time phishing kits target Okta, Microsoft, Google
Cybersecurity Dive: Cybercrime group claims credit for voice phishing attacks
BleepingComputer: ShinyHunters launches Salesforce data leak site to extort 39 victims
