More than 40,000 new computer vulnerabilities were discovered in 2024, a spectacular 38% increase on the previous year.
Behind every CVE lies a potential entry point for cybercriminals, particularly ransomware groups, who methodically exploit these flaws to cripple entire companies.
But what exactly is a CVE, and why has this referencing system become the backbone of global cybersecurity?
CVE stands for Common Vulnerabilities and Exposures, and refers to a public list of discovered computer security flaws. When someone mentions a CVE, they are referring to a specific vulnerability that has been assigned a unique CVE identifier (ID).
This system enables IT teams to coordinate their efforts to prioritize and address vulnerabilities, with the aim of making IT systems as secure as possible.
The concrete impact of this referencing system became particularly apparent in December 2021 with the publication of CVE-2021-44228. This vulnerability, actually known since 2013 under the name “Log4Shell“, affects an Apache Log4j Java library.
The exposure of the flaw caused quite a stir at the time, prompting a rapid response from software vendors around the world. The Washington Post even called it the most serious vulnerability ever encountered…
Table des matières
ToggleThe CVE system, an indispensable standard for communication
The CVE system was created in 1999 by the MITRE Corporation in response to a growing problem: the lack of a common nomenclature for identifying security flaws.
Before this standardization, each publisher, researcher or organization used its own references, making it difficult to track and communicate vulnerabilities.
Today, each CVE follows a precise format: CVE-YYYY-NNNNN, where the year generally corresponds to the year in which the identifier was assigned, not necessarily the year the flaw was discovered.
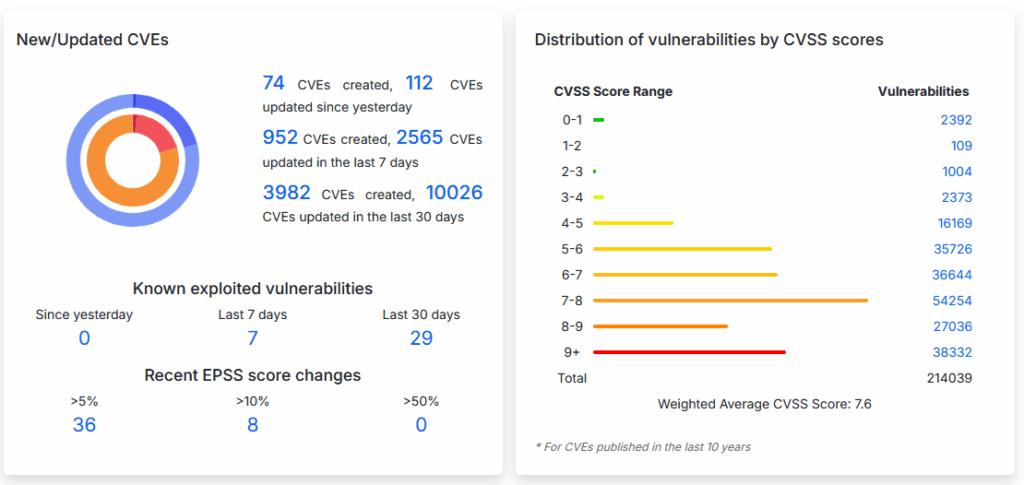
This sequential numbering also makes it possible to estimate the annual volume of vulnerabilities listed, which regularly exceeds 20,000 new entries per year. The year 2024 saw a peak of 40,000 new registrations.
The process of assigning CVE identifiers
Assigning a CVE number is not a random process. Specialized organizations, called CVE Numbering Authorities(CNAs), are empowered to review and validate reported vulnerabilities.
These CNAs include major software publishers such as Microsoft or Adobe, research institutes and security organizations.
When a vulnerability is discovered, it can remain confidential until the software publisher concerned develops and distributes a patch. This is the principle of “coordinated disclosure”, designed to prevent malicious exploitation of unpatched vulnerabilities. The CVE identifier is generally only made public once this stage has been completed.
Vulnerability assessment
Obtaining a CVE identifier is only the first step. The vulnerability must then be assessed to determine its criticality. This is the role of the U.S. National Institute of Standards andTechnology (NIST), which maintains the National Vulnerability Database (NVD) of CVE vulnerabilities as a worldwide frame of reference.
NIST assigns each CVE a CVSS (Common Vulnerability Scoring System) score, ranging from 0 to 10. This score takes into account several factors: ease of exploitation, impact on data confidentiality, integrity and availability, and the complexity of a potential attack.
Vulnerabilities rated between 9 and 10 are considered critical.
System limitations
Despite its acknowledged usefulness, the CVE system has certain limitations:
The time between the discovery of a vulnerability and the assignment of its identifier can sometimes extend over several months, creating grey areas in security communication.
What’s more, not all vulnerabilities are automatically assigned a CVE identifier. Some vulnerabilities, deemed minor or too specific, may be excluded from the repository.
This selection, while necessary to maintain the relevance of the database, can sometimes leave out vulnerabilities that can be exploited in certain contexts.
An indispensable tool for modern security
Despite its imperfections, the CVE system remains the backbone of cybersecurity communication. It enables professionals around the world to share a common language, and automated security tools to correlate information from a variety of sources.
For organizations, mastering this repository is very important in a context where cyber-attacks are multiplying and becoming more sophisticated. The ability to quickly identify vulnerabilities affecting their infrastructure and prioritize patches is now as much a competitive advantage as an operational necessity.

CVE and ransomware: when vulnerability becomes a weapon
The year 2025 perfectly illustrates how ransomware groups methodically exploit CVEs to carry out their attacks.
A recent case in point highlights this reality: CVE-2025-29824, a zero-day vulnerability in the Windows Common Log File System (CLFS) with a CVSS score of 7.8, was actively exploited by a group linked to Play even before it was publicly disclosed.
Sophisticated real-time exploitation
This flaw, discovered by Microsoft and patched on April 8, 2025, represents a perfect example of the race against time between discovery and exploitation. The Play ransomware, exploited by the Balloonfly group active since June 2022 (also known as PlayCrypt), used this elevation-of-privilege vulnerability as a zero-day – i.e. before a patch was available – to infiltrate organizations in the USA, Venezuela, Spain and Saudi Arabia.
The modus operandi was particularly elaborate:
- Initial access via a publicly exposed Cisco ASA firewall
- Deployment of the Grixba infostealer, a tool specific to the Play group
- Exploitation of CVE-2025-29824 to escalate privileges
- Preparing the environment for ransomware deployment
A revealing attack chain
Technical analysis reveals that the attackers created files in C:ProgramDataSkyPDF, including a PDUDrv.blf file – an exploit artifact – and a clssrv.inf DLL injected into the winlogon.exe process. This DLL then deployed two batch files:
servtask.bat: to elevate privileges and create a hidden administrator usercmdpostfix.bat: to erase all traces of the exploit.
This methodology demonstrates the growing sophistication of ransomware groups, who develop or acquire zero-day exploits to bypass traditional defenses.
A growing phenomenon
CVE-2025-29824 is not an isolated case. In 2024, incident analysis shows that ransomware groups are increasingly exploiting newly discovered vulnerabilities:
- Black Basta also exploited a Windows vulnerability (CVE-2024-26169) as a zero-day in 2024.
- 78% of cyberattacks now target domain controllers, according to Microsoft, and 35% of ransomware attacks use the domain controller as their main propagation point (see Alon Rosental’s latest post on this subject).
Practical impact for organizations
This evolution is fundamentally transforming cyber risk management. When a group like Play exploits a CVE before it is published, it means that :
- No antivirus signature can detect the attack
- Traditionaldetection systems are blind
- The window of vulnerability can last for months before being discovered.
For enterprises, this reality calls for an in-depth approach to security, where behavioral monitoring and anomaly detection become as critical as patching.
CVE-2025-29824 is a reminder that, in the age of modern ransomware, every new vulnerability can quickly become an attack vector. This dynamic reinforces the crucial importance of the CVE system, not only to catalog vulnerabilities, but also to enable a coordinated response to threats that are evolving faster than ever.

How do you monitor CVEs in your organization?
Monitoring CVE vulnerabilities within an organization is a complex challenge, requiring a structured approach tailored to the resources available. While methods vary considerably according to the size and resources of each structure, certain fundamental principles emerge.
First and foremost, know your environment
The first step is invariably to draw up an exhaustive inventory of your IT assets. Without this prior mapping, it is impossible to determine which CVEs are really relevant to the organization. This involves not only taking stock of operating systems and applications, but also identifying critical elements whose compromise would have a major impact on the business.
Strategies adapted to scale
Approaches naturally differ according to the resources available. Larger organizations tend towards complete automation: mass deployment of scanners, integration with ticket management systems, and automated notification processes for the relevant teams.
This industrialization makes it possible to manage fleets of tens of thousands of devices with proportionately smaller teams.
On the other hand, smaller organizations often prefer a pragmatic approach focused on the systematic application of available patches, addressing only the most critical vulnerabilities without immediate patching. This method, less sophisticated on the surface, can prove more effective than complex monitoring processes that are difficult to maintain with a small workforce.
The monitoring technology ecosystem
The market today offers a wide range of tools, from vulnerability scanners to unified management platforms, detection and response solutions and threat intelligence services. The choice largely depends on budget, in-house expertise and the complexity of the infrastructure to be protected.
Beyond the CVSS score
Mature organizations no longer content themselves with a simple CVSS criticality score to prioritize their actions. They integrate contextual elements: actual exposure of the systems concerned, business criticality, existence of active exploits, or even targeting by specific threat groups. This contextualization makes it possible to distinguish alerts requiring an immediate response from the daily volume of less urgent notifications.
An integrated approach
CVE monitoring cannot be considered in isolation. It forms part of a more global security strategy that includes behavioral monitoring, network segmentation, user training and business continuity plans. This multi-layered defensive approach recognizes thata single vulnerability rarely leads to a major compromise.
Processes and governance
Beyond the technical aspects, the success of a CVE monitoring program depends on clear processes: definition of roles and responsibilities, establishment of remediation deadlines according to criticality, escalation procedures, and exception management when certain patches cannot be applied immediately.
The ultimate goal remains to transform the continuous flow of new vulnerabilities into concrete, proportionate action, without paralyzing technical teams or compromising the overall security of the information system. It’s a delicate balance that requires constant adaptation to technological developments and new threats.
When prevention is no longer enough
Proactive CVE management is an essential bulwark against cyberattacks, but even the best-prepared organizations can fall victim to an attack. We have seen that between the publication of a CVE and the actual deployment of patches, a critical window of time opens up – one that cybercriminals exploit with formidable effectiveness.
Despite increasingly sophisticated vulnerability management programs, incidents are multiplying. Zero-day attacks, which exploit flaws before they are referenced in the CVE, are a reminder that no security is absolute, especially as the durability of the system itself has recently been called into question…
This reality calls for a balanced approach: while CVE monitoring remains essential to reduce the attack surface, organizations must also be prepared for the scenario of a successful attack.
When, despite all precautions, an attack succeeds, the ability to rapidly restore systems and data often makes the difference between a controlled incident and a corporate catastrophe. In this context, having an expert partner in post-attack recovery is no longer an option, but a strategic necessity.
In the event of an incident, contact our 24/7 emergency teams for rapid recovery of your data and systems after a ransomware attack.
