Table des matières
ToggleRETEX: from the failure of the Akira decryptor to a tailor-made solution
Background to the attack
We were recently contacted on an urgent basis by an IT company in the south of the Netherlands, after being hit by an Akira ransomware attack.
This company, like so many others, found itself faced with a scenario that has unfortunately become classic: a massive encryption of files on their VMware ESXi infrastructure, followed bya sudden crash of the server in the middle of the encryption process…
The targeted infrastructure included several dozen business-critical virtual machines. In addition, the ESXi server, the cornerstone of their information system, hosted sensitive data and essential business applications.
When Akira struck, the company’s entire business came to a standstill.
A double-edged decision: pay the ransom?
Faced with the scale of the damage and the operational urgency, management made the difficult decision to pay the ransom.
This decision, largely understandable in the context of extreme pressure, illustrates the dilemma faced by many organizations: maintain activity at all costs, even at the cost of feeding the criminal economy with no guarantee of results?
The attackers did indeed provide an official decryptor along with a decryption key, in line with their “commitments”. The tool seemed relatively simple to use, with clear instructions:
unlocker.exe -p="path_to_unlock"
unlocker.exe -s="C:paths.txt"
where "paths.txt" is a list of paths for the decryptor, each path on a new line
ESXi commands:
1) chmod +x unlocker
2) ./unlocker -p="/vmfs/volumes"The unexpected failure of the decryptor…
It soon became clear that Akira’s official decrypter had major shortcomings. While the first file could be restored without difficulty, the situation became more complicated with the second file. Our technical analysis revealed several critical problems:
The absence of Akira footers: the files concerned lacked the characteristic signature added at the end of the file by the ransomware. This signature, which is essential for the decryptor to function correctly, was missing due to the server’s sudden crash during the encryption process.
Unmanaged partial encryption: the official decrypter was unable to handle partially encrypted files. When the ESXi server crashed, the encryption process stopped in the middle of certain zones, creating files in a hybrid state that the tool did not anticipate.
Deficient error handling: faced with these unanticipated situations, the decryptor generated fatal errors and abandoned processing, leaving victims in the lurch.
What to do when cybercriminals defect?
The situation was made even worse when the cybersecurity company in charge of the project tried to contact the Akira operators for technical assistance. This was a sign of the victims’ despair at the ineffectiveness of the “solution” they had paid for, and of the hackers’ indifference.
The results were disappointing: the Akira forums on the darkweb were closed, and there was no response from the group. As one analyst from the cyber cell involved bitterly put it: “Our ‘lazy bastards’ are already sunbathing by the pool, mission accomplished”.

This attitude reveals an often overlooked reality: once the ransom has been paid, cybercriminals have no interest in providing technical support. Their “customer service” stops at payment!
The problem of backups
Alongside the difficulties with the decryptor, the company was facing another challenge: the unavailability of its critical backups. The NAS containing the backups had itself broken down, and had been sent to a data recovery specialist, probably abroad according to the information gathered.
This situation illustrates a common vulnerability: organizations often believe that their backups protect them against ransomware, but neglect the availability and resilience aspects of these same backups.
Initial results from the analysis of .vbk files ( Veeam backups) recovered from the NAS were initially optimistic. A colleague had rated all the files as “good”. However, our own analysis using specialized tools revealed a very different picture.
In-depth technical analysis
Our precise diagnosis showed that only three files out of all the backups were really usable. These files, all very small (less than 10 MB), were Veeam password-protected incremental backups.
Although we were able to extract the list of virtual machines contained in one of them, recovery of usable data proved impossible. Beyond 5% of the file structure, only inconsistent and unusable blocks remained.
This situation highlights the importance of regular restoration tests. A backup that has never been tested is often no more than a security lure.
Developing a tailor-made solution
Faced with the failure of the official decryptor and the unavailability of backups, our team decided to develop a customized solution. This approach required in-depth forensic analysis of Akira’s encryption mechanism.
Reverse engineering of the decryptor: we analyzed the internal workings of the decryptor provided by the attackers. This analysis enabled us to understand the encryption mechanisms used and identify points of failure.
Identification of encryption patterns: each file had a different signature due to process interruption. We developed algorithms capable of dynamically identifying encrypted and non-encrypted zones.
Manual key extraction: the decryption process relied on keys that had to be extracted and injected manually for each file, adapting to the specificities of each corruption.
Development of an adaptive decryptor: our final solution was capable of dynamically adapting to the specificities of each file, reconstructing data blocks and managing encryption interruptions.
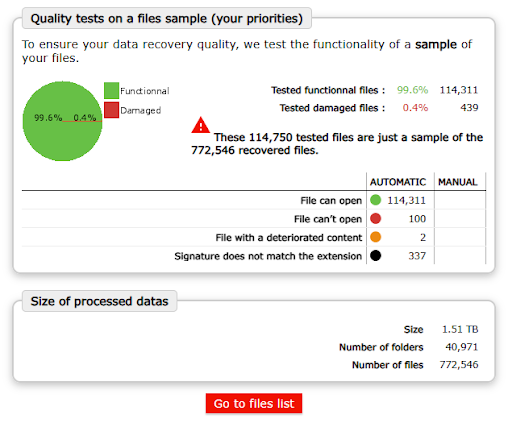
Results and delivery
Less than 48 hours after the start of our intervention, we were able to deliver all the decrypted files to our customer. This performance demonstrates several important points:
Advantage to specialized expertise: our customized solution proved more effective than the tool provided by the cybercriminals themselves.
Importance of technical analysis: a thorough understanding of encryption mechanisms can overcome the shortcomings of automated tools.
Value of reactivity: our rapid intervention limited the impact of the attack on the company’s business.
Lessons learned from this intervention
This experience illustrates several important realities:
- Paying the ransom does not guarantee recovery: even if they give in to the cybercriminals’ demands, organizations are not guaranteed to recover their data.
- The reliability of decryptors is questionable: the tools provided by attackers are often basic and do not handle complex use cases.
- Technical expertise makes the difference: in critical situations, the intervention of experienced specialists can make the difference between recovery and definitive data loss.
- The importance of backup testing: a backup strategy that is not regularly tested may prove useless at the critical moment.
Akira ransomware: background and in-depth technical analysis
Emergence and positioning in the ecosystem
Akira emerged in March 2023 against a backdrop of profound change in the ransomware landscape. Its appearance coincides with the gradual disappearance of certain established groups, and illustrates the constant dynamic of renewal in this criminal ecosystem.
The group has rapidly established itself as a major threat, adopting a sophisticated RaaS (Ransomware-as-a-Service) model from the outset. This approach enables developers to make their malware available to affiliates in exchange for a share of the profits, thereby multiplying the impact and reach of attacks.
Suspected conti connections
Many cybersecurity experts are drawing disturbing links between Akira and the defunct Conti ransomware, which officially ceased operations in May 2022. These connections are based on several elements:
Similarities in attack techniques: infiltration, lateral propagation and encryption methods bear many similarities to those used by Conti.
Tool reuse: some of the tools and scripts used by Akira show striking similarities to those developed by the Conti ecosystem.
Immediate technical expertise: unlike new groups that require a learning curve, Akira demonstrated remarkable technical sophistication from the outset.
This presumed parentage would partly explain the speed with which Akira established itself as a major threat, potentially benefiting from the expertise accumulated by former Conti operators.
Technical evolution: from Windows to multi-platform
One of Akira’s most remarkable features is its rapid technical evolution. Initially designed to target Windows environments, the group rapidly extended its capabilities to Linux systems, notably VMware ESXi servers.
This transition, which took place in April 2023, demonstrates a strategic understanding of modern infrastructures. ESXi servers are particularly attractive targets, as they often represent a single point of failure: the compromise of a single virtualization server can affect dozens of virtual machines.
Sophisticated cryptographic architecture
Akira uses a hybrid encryption architecture combining efficiency and security:
ChaCha20 for symmetrical encryption: this choice is not accidental. ChaCha20 offers excellent performance on modern processors while maintaining a high level of security. This combination enables fast encryption of large volumes of data.
RSA for key protection: ChaCha20 keys are themselves encrypted with RSA, creating a two-tier architecture that makes any recovery attempt without the attackers’ private key considerably more difficult.
Signature management: Akira adds specific signatures (footers) to encrypted files, enabling the decryptor to validate the integrity and completeness of the encryption process.
Evolution of extensions and markers
The evolution of the extensions used by Akira bears witness to continuous adaptation:
- Initial phase (.akira): early versions used the .akira extension, easily identifiable by security solutions.
- Diversification (.powerranges): the adoption of new extensions such as .powerranges aims to evade detection signatures and complicate automatic identification.
This diversification strategy is part of a continuous adaptation to countermeasures deployed by security teams.
A sophisticated attack methodology
Initial access and recognition
Akira’s initial access methods reveal a methodical and opportunistic approach:
Exploitation of vulnerable VPNs: VPN systems without multi-factor authentication are the preferred target. In particular, Akira exploits known vulnerabilities in Cisco VPN solutions.
Compromised remote access services: the poorly secured RDP protocol is another favorite attack vector, exploited via brute force techniques or compromised credentials.
Targeted phishing: Akira’s spear phishing campaigns are distinguished by their sophistication, with customized lures tailored to the specificities of each target organization.
Establishing persistence
Once initial access has been gained, Akira deploys a multi-layered persistence strategy:
Creating dummy accounts: attackers create administrator accounts or compromise existing ones, ensuring access is maintained even after initial discovery.
Use of legitimate tools: tools such as AnyDesk, WinSCP, FileZilla and Rclone are hijacked to maintain access and facilitate exfiltration.
Active directory exploitation: in corporate environments, Akira aims to obtain domain administrator privileges for efficient lateral propagation.
Reconnaissance and mapping
Akira’s reconnaissance phase can last several weeks. Attackers use tools such as SoftPerfect Network Scanner and Advanced IP Scanner to thoroughly map :
- critical servers and their interdependencies
- Backup systems and their location
- Sensitive data and their location
- Security measures and any loopholes
The double extortion strategy
Akira has perfected the double extortion technique, combining destructive encryption with the threat of disclosure:
Pre-exfiltration phase: prior to encryption, the attackers identify and extract the most sensitive data, a process that can represent several terabytes.
Selective encryption: unlike primitive ransomware, Akira applies selective encryption, targeting critical files while preserving minimal functionality.
Customized negotiation: the group engages in negotiation tailored to each victim, modulating its demands according to the size and financial capacity of the organization.
Alarming impact and statistics
Data from CISA (Cybersecurity and Infrastructure Security Agency) paints a disturbing picture of Akira’s impact. Since March 2023, the group has affected over 250 organizations, generating approximately $42 million in illicit revenues.
Statistics for 2025 confirm this worrying trend:
- January 2025: 72 claimed attacks
- February 2025: 77 claimed attacks
These figures position Akira as the most active ransomware group worldwide, outstripping its competitors in terms of volume and impact.
Targeted sectors and specific vulnerabilities
Healthcare sector
The medical sector represents a priority target for Akira, so much so that the Health Sector Cybersecurity Coordination Center (HC3) issued a formal warning in February 2024. Healthcare establishments present several attractive vulnerabilities:
- System criticality: disruption of hospital systems directly endangers human lives
- Ability to pay: healthcare establishments generally have substantial budgets at their disposal
- Sensitive data: medical information has a high value on the black market
Critical infrastructures
Utilities, transport networks and communication systems are under particular scrutiny, creating significant systemic risks for society.
Manufacturing sector
Manufacturing industries, often dependent on SCADA and automation systems, suffer particularly costly production interruptions.
Evolving countermeasures and adaptations
In the face of the cybersecurity industry’s efforts, Akira has demonstrated a remarkable ability to adapt:
Migration of attack vectors: the group is gradually abandoning methods that have become less effective to explore new vectors.
Increasing sophistication: integration of advanced techniques to automate recognition and improve attack effectiveness.
Geographic diversification: expansion into new markets, notably Asia-Pacific and South America.
Challenges for security teams
Akira’s sophistication poses particular challenges for security teams:
Complex detection: the use of legitimate tools and the sophistication of techniques complicate automatic detection.
Time-critical response: Akira’s speed of execution requires near-instantaneous response capabilities.
Technical expertise: understanding attack mechanisms requires in-depth technical expertise.
Conclusion:
Our experience with the Dutch company perfectly illustrates the realities of Akira ransomware. Despite payment of the ransom, full data recovery was not guaranteed. It was only through in-depth technical expertise and the development of a customized solution that we were able to overcome the shortcomings of the official decryptor.
This experience underlines several crucial points:
- Payment is never a guarantee: even by giving in to the demands of cybercriminals, organizations are not guaranteed to recover their data in full.
- Technical expertise makes the difference: in critical situations, the intervention of experienced specialists can accomplish what automated tools cannot.
- Preventive preparation is essential: a comprehensive defense strategy, including tested backups, advanced detection and a response plan, remains the best investment.
- Adaptability is crucial: in the face of sophisticated threats like Akira, organizations need to develop the capacity for continuous adaptation and innovation.
Akira represents the evolution of ransomware towards more sophisticated and adaptive forms. Its ability to evolve, innovate and circumvent traditional countermeasures makes it a formidable adversary. The organizations that survive this threat will be those that have invested in resilience rather than mere protection.
In the event of an incident involving Akira or any other ransomware, don’t hesitate to seek the assistance of experienced specialists. As our intervention demonstrated, an innovative technical approach can sometimes succeed where conventional solutions fail.
