The cybercriminal group Nitrogen has just suffered an embarrassing mishap that turns their ransomware into a tool for outright destruction. A programming error in their malware targeting VMware ESXi environments makes decrypting files technically impossible, even for the hackers themselves. This discovery, revealed by Coveware researchers on February 2, 2026, vividly illustrates why paying ransoms never guarantees data recovery.
Table des matières
ToggleAn irreversible cryptographic flaw
The technical analysis carried out by Coveware’s teams reveals a fundamental malfunction in the encryption process of the Nitrogen ransomware. Derived from the publicly disclosed Conti 2 source code, the malware contains a memory management error that systematically corrupts the public key used to encrypt victims’ files. This corruption is not insignificant: it makes any subsequent decryption mathematically impossible, even if the victim agrees to pay the requested ransom.

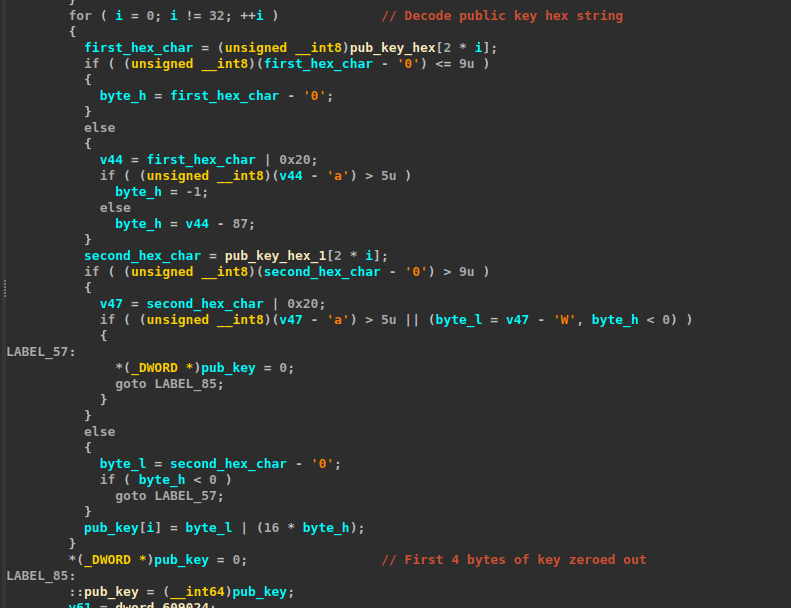
The problem lies precisely in the manipulation of variables in memory. During the encryption process, the malware stores the public key at offset rsp+0x20 on the memory stack. Immediately afterwards, however, the program writes another QWORD variable (8 bytes) at offset rsp+0x1c. This operation causes a memory overlap that overwrites the first four bytes of the public key, replacing them with zeros.
The Coveware researchers explain that “the resulting corrupted public key was not generated from a private key, it was generated by mistakenly overwriting a few bytes of another public key. The end result is that nobody really knows the private key that corresponds to the corrupted public key.” This cryptographic corruption transforms what should be a reversible process into definitive destruction.
Understanding the encryption mechanism and its failure
To fully grasp the seriousness of this error, we need to understand the expected operation of ransomware using Curve25519 asymmetric encryption coupled with the ChaCha8 algorithm. In a correct implementation, the malware generates for each targeted file a unique cryptographic key pair based on the Curve25519 algorithm: a private key and its corresponding public key. This key pair is then used to create a “shared secret” that serves as a lock on the data. This shared secret becomes the encryption key for the symmetrical ChaCha8 algorithm, which effectively locks the contents of the file. Finally, only the public key generated for this specific file is stored in the footer of the encrypted document.
Decryption relies on the reverse operation: the tool supplied by the criminals contains their master private key, which, when exchanged with the public key stored in each file, enables the same shared secret to be recreated and the data unlocked.
But in the case of Nitrogen, the corruption of the first four bytes of the public key breaks this cryptographic chain. Since the recorded public key was never mathematically derived from a legitimate private key, but is the result of an accidental memory overwrite, no existing private key can be used to generate the shared secret required for decryption: ChaCha8 has locked the files with a key that nobody knows, not even the cybercriminals. The cryptographic link has been broken once and for all.
Organizations in a total bind
This discovery places the victims of the Nitrogen ransomware in a particularly tragic situation. Organizations whose ESXi servers have been encrypted by this flawed variant, and who have no viable backups, find themselves facing definitive data loss. Coveware is categorical: “Even the threat actor itself is unable to decrypt them, and victims without viable backups have no way of recovering their encrypted ESXi servers. Paying a ransom won’t help these victims, as the decryption key/tool won’t work.”
Coveware’s incident response team recommends that organizations impacted by Nitrogen exercise extreme caution when analyzing their recovery options. Any file encrypted by the ESXi variant without an available backup should be analyzed in conjunction with the corresponding malware sample to determine with certainty whether it is affected by this cryptographic bug. This technical verification becomes essential before considering any negotiation with the attackers.
An established cybercriminal group since 2023
The Nitrogen group is no newcomer to the cybercriminal landscape. First identified in 2023, the group started out as a malware developer and operator facilitating initial access for other cybercriminals. Originally, Nitrogen created and sold a sophisticated progressive loader, a small piece of code embedded in the installation programs of legitimate applications such as WinSCP, Advanced IP Scanner, AnyDesk or PuTTY. These applications were specifically chosen because they are frequently downloaded by IT teams and technical users.
The infection strategy was based on malvertising distributed via Google and Bing, a technique also used in ClickFix campaigns, redirecting victims to fake download sites. Once the compromised application was installed, the malware performed a DLL sideloading, loading a malicious dynamic link library instead of the legitimate system file.
The Nitrogen loader operated according to a progressive multi-stage architecture: after installation of the booby-trapped application and sideloading of the malicious DLL, an intermediate component (stager) took over to decompress or download the next phase of the attack. This phase generally deployed Python scripts accompanied by command and control (C2) beacons such as Cobalt Strike or Sliver, establishing permanent communication with the attackers’ infrastructure. This modular architecture made it possible to establish robust persistence on compromised systems, while facilitating subsequent lateral movements in the victim’s environment.
The evolution towards double extortion
Nitrogen’s business underwent a significant transformation around September 2024, when the group stopped selling its malware to third parties to become a fully-fledged ransomware operator. This transition was marked by the appearance of their first public victims on their disclosure site dubbed “NitroBlog”. The group developed its own strain of ransomware, derived from the Conti 2 source code that had been publicly disclosed in 2022 in the context of the war in Ukraine.
Nitrogen has adopted the double extortion model, exfiltrating victims’ sensitive data to their infrastructure before proceeding to encrypt systems. The ransomware adds the “.nba” extension to encrypted files and drops a ransom note named “readme.txt” on the desktop and in each affected folder. Victims who refuse to negotiate have their data published on the leaks site, where the group publicly exposes stolen information to put pressure on compromised organizations.

A striking illustration of the ineffectiveness of ransom payments
This discovery is a further and particularly powerful argument against ransom payments. Authorities and cybersecurity experts tirelessly repeat this message: there is no guarantee that cybercriminals actually possess the technical means to decrypt your systems, even if they intend to do so. In the case of Nitrogen, it’s no longer a question of the attackers’ good faith or competence, but of sheer mathematical impossibility.
This technical failure turns the economic logic of ransomware on its head. Where there should be a criminal but rational exchange (data for payment), there is only a total impasse. Files are irretrievably lost, and cybercriminals can’t honor their share of the “black market”, even if they wanted to. This situation profoundly erodes the group’s credibility with potential future victims. Ransomware that cannot deliver on its fundamental promise of decryption undermines the very viability of the criminal business model, as targeted organizations lose any rational incentive to negotiate if they discover that decryption is technically impossible.
Repercussions on the criminal ecosystem
Beyond the direct victims, this programming error could have significant repercussions on Nitrogen’s position in the cybercriminal ecosystem. Reputation is a central element in the operation of ransomware groups, particularly those operating under the RaaS (Ransomware-as-a-Service) model or collaborating with affiliates. A group unable to guarantee effective decryption of compromised systems risks seeing potential affiliates turn to more reliable operations.
This situation also raises questions about development and quality control processes within cybercriminal groups. Researchers describe this anomaly as an obvious coding error that should have been detected during basic testing of the malware on laboratory environments. The fact that it escaped any verification process suggests either haste in deploying this ESXi variant, or a lack of rigor in the group’s internal procedures. This negligence contrasts with the sophistication generally observed in modern ransomware operations.
Recommendations for organizations
In the face of this threat, organizations need to reinforce their security posture, particularly with regard to their VMware ESXi virtualization environments, which are prime targets for many ransomware groups. Essential preventive measures include :
- implementing a robust backup strategy following the 3-2-1 rule as a minimum (three copies of data, on two different media, with one copy off-site), with backups regularly tested and isolated from the main network ;
- strict monitoring of software downloads, systematically favoring official publisher sites over sponsored search results that can be compromised by malvertising;
- network segmentation to limit lateral movements in the event of initial compromise;
- regularly updating ESXi hypervisors and applying VMware security patches as soon as they are released;
- ongoing training of IT teams in the social engineering and malvertising techniques used by Nitrogen and similar groups;
- the deployment of EDR (Endpoint Detection and Response) solutions capable of detecting suspicious behavior linked to DLL parachuting and C2 beacons such as Cobalt Strike or Sliver.
For organizations that have already fallen victim to Nitrogen, forensic analysis becomes crucial. It is imperative to retain the malware samples that have encrypted systems and have them analyzed by incident response experts to determine with certainty whether they are affected by the cryptographic bug. This analysis will avoid unnecessary negotiations and payments that lead to no data recovery.
A textbook case for the future
The Nitrogen case is just one in a series of technical malfunctions in the ransomware ecosystem. In December 2025, another group of cybercriminals had inadvertently left their decryption key publicly accessible, enabling victims to recover their data free of charge. These incidents are a reminder that cybercriminal groups, despite their growing technical sophistication and apparent professionalization, are not immune to human error and negligence, which can totally compromise the effectiveness of their operations.
For cybersecurity professionals and decision-makers alike, the Nitrogen case will serve as a concrete, documented example when discussing incident response policies. It demonstrates irrefutably that paying a ransom is never a guarantee of recovery, even when attackers would theoretically intend to cooperate. Tools can be faulty, keys can be lost, and as this case spectacularly demonstrates, the malware itself may contain bugs making decryption technically impossible.
Security through prevention rather than ransomware
Coveware’s discovery reinforces a fundamental principle of cybersecurity: the only truly reliable defense remains prevention and preparation, with solid backups regularly tested and a proven business continuity plan. Organizations that invest in resilient architectures, team training and robust backup processes are the ones that survive ransomware attacks, regardless of the attackers’ capabilities or intentions.
The Nitrogen bug perfectly illustrates why the recommendations of government agencies and cybersecurity experts consistently converge on the same conclusion: never pay ransoms. Not only does payment directly fund criminal activities and encourage new attacks, it also offers absolutely no guarantee of data recovery. In the case of Nitrogen, this lack of guarantee reaches its paroxysm: even with the best will in the world, cybercriminals can’t decipher what their own malware has corrupted.
Sources :
Coveware: Nitrogen Ransomware: ESXi malware has a bug!
The Register : Nitrogen can’t unlock its own ransomware after coding error
Barracuda: Nitrogen ransomware: From staged loader to full-scale extortion
Sophos: Into the tank with Nitrogen
Ransomware live: Nitrogen
