In the second quarter of 2024, France continued to suffer the onslaught of cybercriminals. Ransomware attacks continued to grow in frequency and complexity, forcing businesses to constantly review their security measures. At a time when cybersecurity has become a priority for businesses of all sizes, these statistics provide vital information for better understanding the dynamics of attacks and the groups responsible. SOS Ransomware takes a look at the main statistics of recent months.
Table des matières
ToggleVolume of ransomware attacks in France (first and second quarter 2024)
Data on ransomware attacks for the first and second quarters of 2024 reveal some notable variations. After an apparent drop in attacks in March, as we had already observed in our previous gazette, April and May recorded a peak with 17 and 22 claimed attacks respectively, before falling back in June with 9 attacks. This fluctuation could reflect the emergence or disappearance of new groups of cybercriminals, potentially in response to corporate security measures or international police operations such as the recent Operation Cronos.
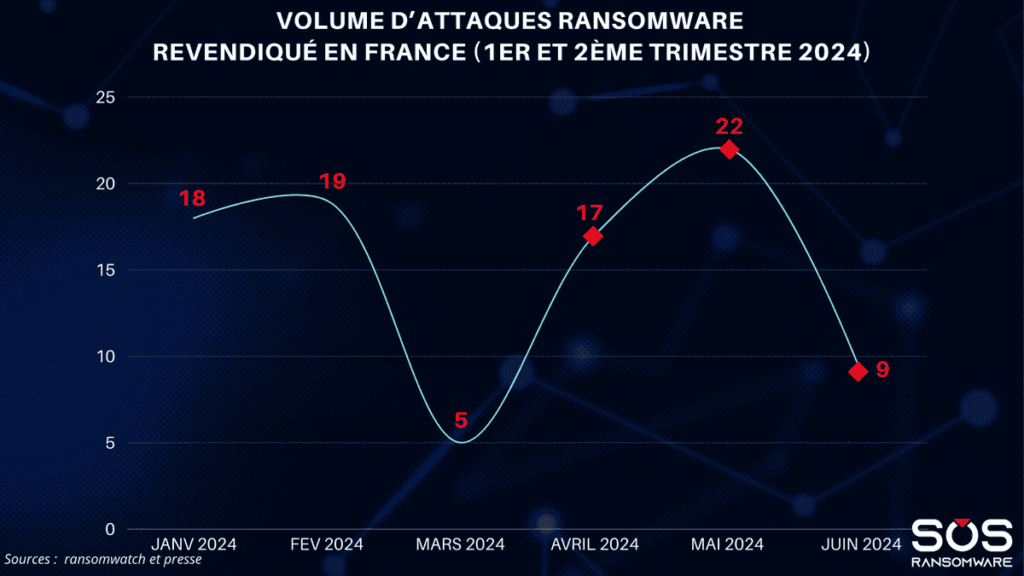
The significant drop observed in June (with just 9 attacks) might suggest a reduction in the threat, but recent history teaches us that this is often a temporary respite. Cybercriminals, particularly those behind ransomware like Lockbit, adapt their tactics and timing to maximize their effectiveness. As a result, businesses need to remain constantly on their guard, and not lower their level of protection during periods of relative calm.
Ransomware groups active in France in the second quarter of 2024
In the second quarter of 2024, one group clearly dominates the French ransomware landscape: Lockbit. This group claimed no fewer than 13 attacks in the second quarter alone, a clear lead over its competitors. Behind them, groups such as BlackCat and 8Base claimed just 3 attacks each. Lockbit’s dominance is part of a global trend observed in recent years, with this group remaining one of the most active and dangerous on the international scene.
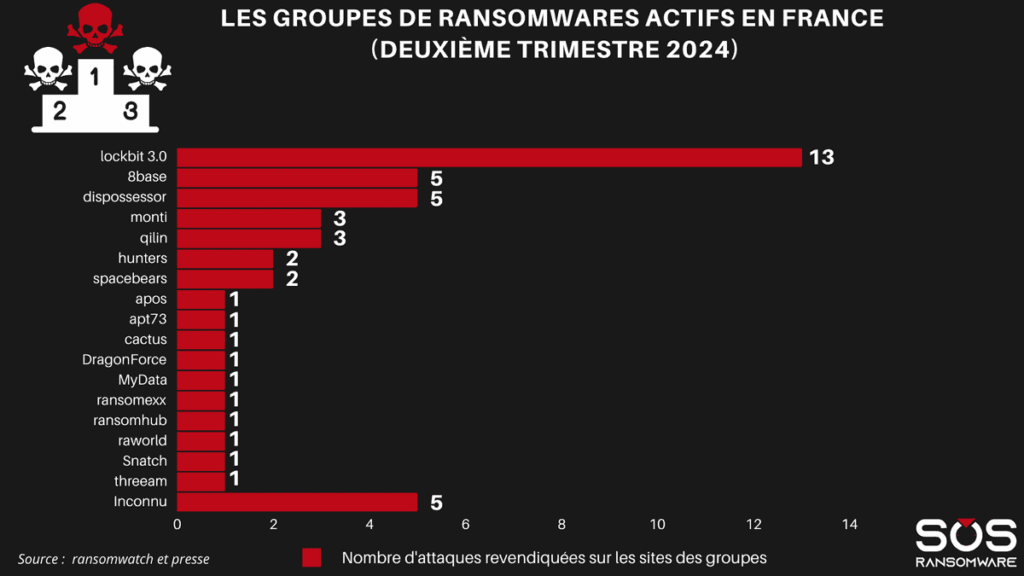
However, Lockbit’s apparent monopoly should not obscure the threats posed by other, often more discreet but equally dangerousgroups. The evolution of Lockbit, which continues to perfect its attack tools and distribution methods despitethe blow dealt to the organization by Operation Cronos, makes this group a persistent threat to French businesses. The fact that it still so largely dominates the ransomware scene in France calls for increased surveillance and closer cooperation between law enforcement and businesses to effectively counter this threat. A newcomer, RansomHub, is starting to make waves in Europe and France.
Countries most affected by ransomware (January to August 2024)
Between January and August 2024, France ranked as the sixth country most affected by ransomware worldwide, with 3.9% of global attacks. This percentage places France far behind the United States, which suffers 70.6% of attacks, but close to nations such as Italy (4.4%) and Germany (4.2%). In the top 3, behind the USA, we find the UK with 8.3% of attacks, followed by Canada with 7.9%.
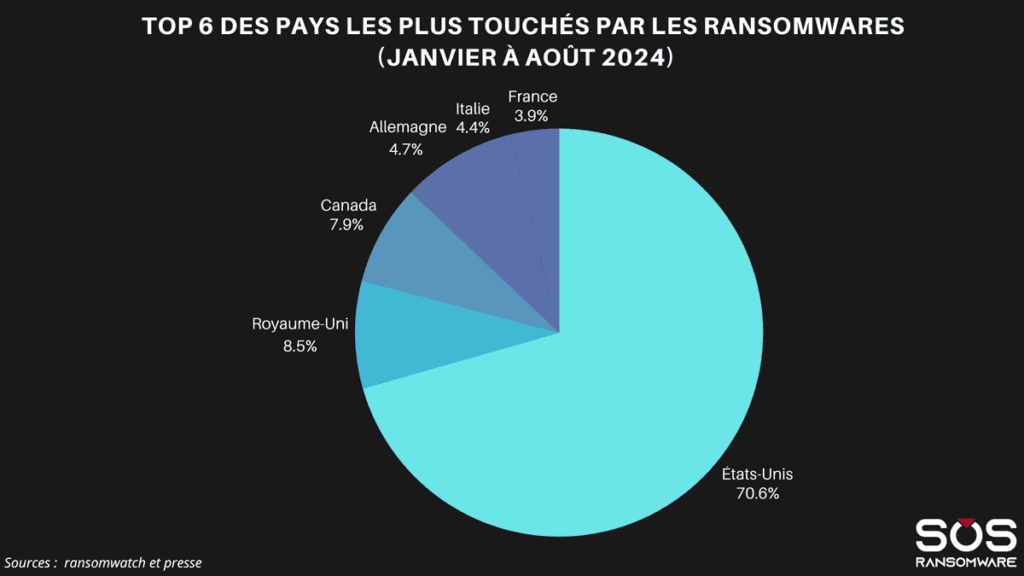
These figures show that, although attacks are mainly concentrated in the USA, cybercriminals are not neglecting other major economies. France, as a European economic powerhouse, remains a prime target for ransomware groups. It is therefore vital that all French companies, large and small, are aware of this risk and invest in robust security infrastructures.
Types of companies targeted in France: special attention to SMEs and ETIs
Small and medium-sized businesses (SMBs) and mid-sized companies (MSEs) continue to be on the front line when it comes to cyber attacks. Together with VSEs, they accounted for more than 61.7% of attacks recorded in the second quarter of 2024, with 36.2% for SMEs, 19.1% for ETIs and 6.4% for VSEs. This proportion is worrying, as these structures often have fewer resources to invest in advanced cybersecurity technologies and recover from an attack. These figures show that cybercriminals are increasingly targeting smaller structures, perhaps due to their less robust defenses and limited ability to react quickly to an attack.
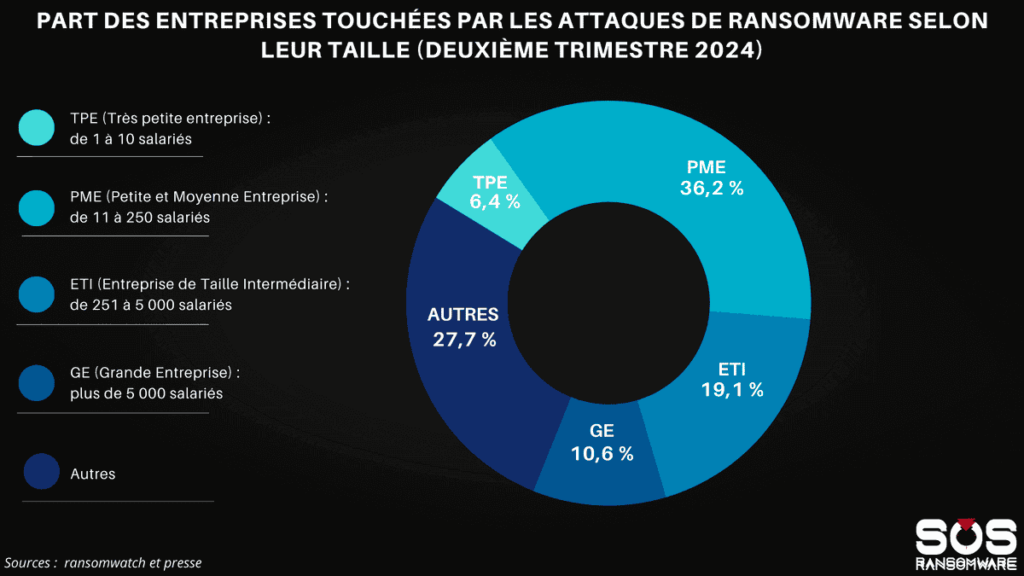
Large enterprises (LE) are also targeted, but to a lesser extent, with “only” 10.6% of attacks. These larger organizations generally have better defensive capabilities, but they are not free from vulnerabilities, and although they invest more in cybersecurity, they are never totally immune to these threats. It is essential that all businesses, whatever their size, adopt proactive strategies to protect their critical data and systems. This focus by cybercriminals on small businesses underlines the need for better education and easier access to affordable cybersecurity tools for these businesses, which are an essential part of the French economic fabric.
Average recovery time after a ransomware attack: a cost difficult to estimate.
Finally, a particularly alarming piece of data is the average time it takes for a business to resume operations after a ransomware attack. According to statistics from the second quarter of 2024, it takes an average of 3 to 4 weeks to restore systems and data after an attack. This may seem like a long time to recover, but it reflects the complexity of recovery procedures and the massive disruption caused by these cyberattacks. In line with global trends, this timeframeremains extremely long for small businesses, for whom every day of inactivity can result in significant financial losses.

This prolonged downtime can have devastating consequences, particularly for SMEs and VSEs, which do not have the same resources as large corporations to cope with such interruptions. The total cost of an attack is not limited to the ransom potentially demanded by cybercriminals. It also includes lost productivity, the cost of data recovery, reputational damage, and sometimes regulatory fines in the event of personal data being compromised. For SMEs and VSEs, these impacts can be devastating, even threatening the survival of the business. Hence the importance of preparedness and incident response planning to minimize the impact of attacks and accelerate recovery.
Lessons and prospects
The second quarter of 2024 typifies the resilience of ransomware groups, such as Lockbit, and their ability to target French businesses, particularly smaller ones. The fact that the latter represent the majority of targets shows that cybercriminals are exploiting a systemic flaw in the cybersecurity of SMEs, ETIs and TPEs. Raising awareness, facilitating access to protective technologies, and intensifying cooperation between the public and private sectors are all levers that need to be activated to stem this threat.
France must continue to invest in cybersecurity infrastructures and encourage prevention and training initiatives. Businesses of all sizes need to put in place incident response plans to limit the impact of attacks, reduce recovery times and minimize losses.
Fortunately, at SOS Ransomware, we offer solutions to recover your data without giving in to ransomware. Our specialists are equipped to decrypt files and restore access to your critical information. By intervening quickly, we help businesses reduce downtime and avoid financial loss. Call on our expertise to overcome these difficult situations with complete security.
