In August 2023, the Akira ransomware group reportedly compromised the IT systems of KNP Logistics, a historic British transport company founded in 1865. An intrusion made possible by a weak password that a hacker could easily guess. This seemingly insignificant detail turned into a fatal entry point.
The consequences were devastating: business paralysed, servers encrypted, operations frozen. Despite a secure infrastructure compliant with industry standards, KNP was never able to relaunch its business. The company was placed in receivership, then liquidated. In the months following the attack, a company more than a hundred years old was wiped off the British economic landscape. An industrial failure caused by simple safety negligence.
Table des matières
ToggleA century-old company crippled in a few clicks
Founded in Victorian times, KNP Logistics and its historic subsidiary Knights of Old managed over 500 trucks across the UK. The group provided logistics services for major industrial and retail customers. The attack, which took place in June 2023, brought decades of continuous business to an abrupt halt.
According to CEO Paul Abbott’s testimony in a BBC Panorama documentary broadcast on July 21, 2025, the intrusion was triggered by the exploitation of a compromised employee login. The password, insecure and easy to find, gave the hackers access to the system. Once the account had been infiltrated, the attackers extended their access laterally, gaining access to the production servers without triggering any alerts. This seemingly minor oversight proved to be the fatal tipping point that led to the collapse of the century-old company.

Data encryption took place in a matter of hours. Local backups were targeted and then erased. Deprived of its logistical and accounting information, KNP found itself unable to honor its contracts, ensure deliveries and manage its financial flows. On September 25, 2023, after three months of paralysis and rescue attempts, the group was forced to file for bankruptcy.
The social impact was considerable. Nearly 700 employees were made redundant, industrial partners were left without a logistics provider, and several customers had to reorganize their supply chains as a matter of urgency. A 158-year-old company, the flagship of the British freight transport sector, was wiped out by ransomware without even a technical flaw being exploited.
The illusion of security: when everything seems to be in place
According to information relayed by the BBC, KNP Logistics had an IT security base in line with industry standards: antivirus, firewalls, backup procedures, monitoring tools. The company had even taken out cyber insurance, which was supposed to cover it in the event of a major incident.
But none of these measures prevented the initial compromise. No system detected the fraudulent access. No alerts were triggered as the attackers moved sideways across the infrastructure. And by the time encryption began, it was already too late.
Cybersecurity experts have pointed out that the absence of multi-factor authentication (MFA) was probably a determining factor. This flaw can enable attackers to exploit a simple identification weakness to penetrate systems and move around undetected.
The KNP case shows just how destructive over-reliance on “default” security can be. Even well-equipped companies can fail to detect an elementary compromise, especially when it relies on simple, silent techniques.
The payment trap: an empty promise
As soon as the files were encrypted, a ransom was demanded. The amount – estimated at several million pounds – was supposed to unlock the data using a decryptor provided by the attackers. But in reality, there was no guarantee that this tool would work, and the company could not afford to pay such a sum. According to the BBC, KNP did not give in to the blackmail, which contributed to the permanent loss of its data.
This situation illustrates a common dilemma: even if a company considers paying to recover its data, there is no guarantee that the decryptor will work properly. As our case study on the Akira ransomware shows, decryption keys obtained from attackers are sometimes unusable: faulty, incomplete, or deliberately sabotaged.
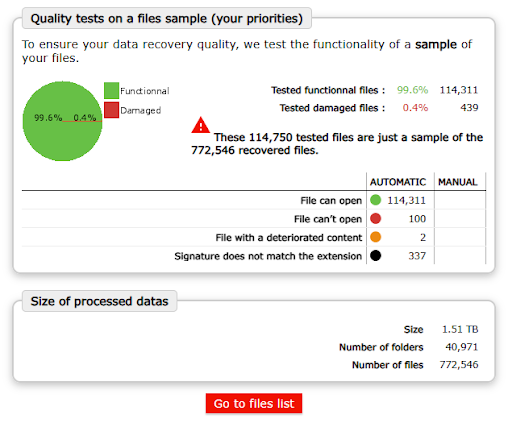
The KNP case is a reminder that the promise of a decryptor is merely a lever for psychological pressure. Faced with this situation, companies need to evaluate all available options, including independent technical expertise to identify possible recovery paths.
Social engineering: an underestimated intrusion lever
Contrary to popular belief, ransomware groups don’t always need sophisticated scripts or unpatched vulnerabilities to compromise a system. In the case of KNP Logistics, it was the reuse of a password – already compromised in a previous leak – that enabled the attackers to break into the network. The password, retrieved from a database circulating on dark web forums, was still active on an internal user account.
Once logged in, the cybercriminals used social engineering techniques to bypass internal controls: privilege escalation through breach of trust, unverified internal reset requests, observation of user routines. These actions, often invisible to traditional detection devices, rely on human automatisms rather than software vulnerabilities.
Cybercriminals are never short of imagination when it comes to achieving their goals. The Interlock group, for example, recently broke new ground with the FileFix method, which consists in duping users with carefully designed fake files embedded in familiar environments. This technique perfectly illustrates the rise of attacks that target predictable human behavior rather than technical flaws.
Exploiting human vulnerabilities is no longer the exception: it is becoming the norm.
The revealing example of Clorox: when social engineering targets the helpdesk
A recent case illustrates this potential vulnerability between humans and organizational processes. Clorox took its IT service provider Cognizant to court, accusing it of enabling a major cyberattack in August 2023 that caused $380 million in damage.
According to Clorox’s allegations in the court documents made public, a cybercriminal simply contacted Cognizant’s IT helpdesk by telephone, posing as a Clorox employee. And the helpdesk agent would have reset the passwords and multifactor authentications (MFAs) of the requested account without applying any identity verification procedure.
This case shows how the security chain, however robust it may be technically, can be compromised by its weakest link: the human being and the processes that frame his or her actions. Experts now recommend rethinking the architecture of security systems so that they automatically enforce identity verification protocols. This systemic approach, rather than relying solely on employee training, makes social engineering attacks considerably more difficult to pull off.
React quickly: every hour counts
When a ransomware attack is detected, time becomes a critical factor. Every minute of inaction can exacerbate the damage, making data recovery more complex, if not impossible.
Immediate steps to take:
- Isolate affected systems: disconnect compromised machines from the network to prevent malware propagation.
- Preserve evidence: avoid any action that could alter system logs or encrypted files, which are essential for post-incident analysis.
- Contact data recovery experts: call on specialists who can intervene quickly to assess the situation and propose recovery solutions without giving in to the demands of cybercriminals.
Effective coordination with the authorities and various service providers is also an undeniable asset for assessing the extent of the attack and implementing appropriate remediation measures.
Rethinking security: beyond the password
Traditional authentication methods based solely on passwords are showing their limitations in the face of today’s threats. The Zero Trust model has emerged as an appropriate response, based on the principle of “never trust, always verify”. It involves systematic verification of every access attempt, regardless of the origin of the request.
In addition, the 3-2-1 backup strategy remains a solid foundation: three copies of data, on two different types of media, one of which is kept off-site. To reinforce this approach, the 3-2-1-1-0 rule adds an immutable or isolated copy (air gap) and requires error-free verified backups. This method offers enhanced resilience against ransomware.
To enhance security, companies should consider the following measures:
- Implement multi-factor authentication (MFA): add an extra layer of security by requiring multiple forms of verification.
- Staff awareness: train employees in good cybersecurity practices to reduce the risks associated with social engineering.
- Regular data backup: adopt the 3-2-1 backup strategy, which involves keeping three copies of data on two different media, including one off-site.
- Restoration tests: regularly check the ability to restore data from backups.
- Draw up an incident response plan: clearly define the procedures to be followed in the event of an attack, including the internal and external contacts to be mobilized.
By combining strong authentication, ongoing staff awareness and robust backup strategies, companies can significantly reduce their exposure to cyber threats.
What the KNP case teaches us
The KNP Logistics case acts as a wake-up call. A robust company with a long history did not survive an attack made possible by a compromised password. No infrastructure, however well-equipped, is invulnerable when the flaw lies in human usage.
This type of incident is more than just a temporary loss of operations. It directly threatens business continuity, reputation, jobs and commercial relations. If the attack has occurred, it is still possible to take action, provided you know where to turn.
Our role is precisely to intervene after the attack, when all seems lost. In collaboration with IT teams, we analyze encrypted systems to determine the technical options for recovery.
Faced with a ransomware attack?
Our teams can help you recover your data and limit the impact on your business. Contact us today.
