As you know, cybersecurity threats are constantly evolving, and new players are appearing all the time.
Today, we’re focusing on Akira, a ransomware group that has established itself as a very dangerous force, particularly at the start of this year, with no fewer than 72 attacks in January 2025 and 77 in February.
Akira is particularly active in North America, but can be found on every continent, targeting organizations of all sizes and in all sectors.
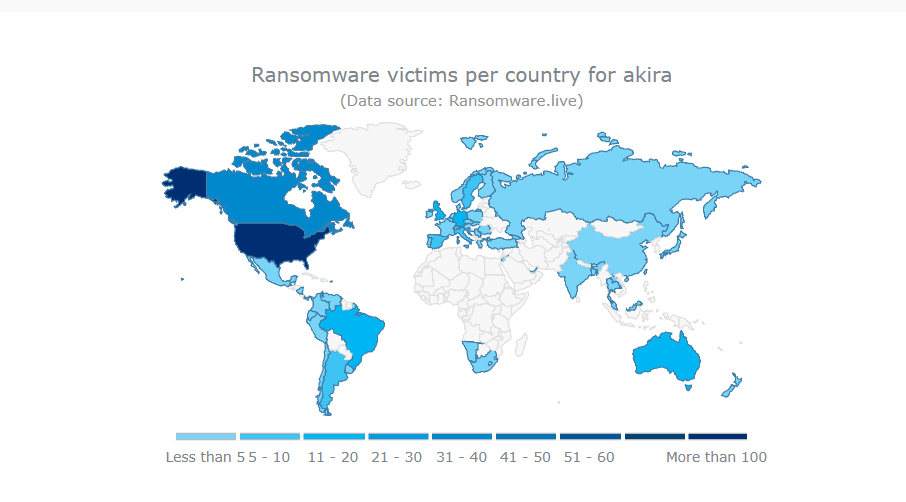
If you’re looking to protect your organization, this analysis will provide you with concrete elements to strengthen your defenses against the Akira ransomware.
Table des matières
ToggleThe Akira phenomenon in the ransomware ecosystem
Akira, which appeared in March 2023, is part of the worrying trend towards Ransomware-as-a-Service (RaaS). This model, which allows developers to make their malware available to affiliates in exchange for a share of the profits, has considerably amplified the impact of this threat.
There has been some speculation about a link with the CONTI ransomware, at a time when the latter has ceased operations.
Akira’s particularity lies in its versatility: it targets both Windows and Linux systems, with hybrid encryption combining ChaCha20 and RSA algorithms.
When Akira strikes, compromised files end up with distinctive extensions such as .akira or .powerranges. This visual signature is just the tip of a sophisticated attack process that is damaging businesses of all sizes.
Researchers believe that the name “Akira” was inspired by the 1988 cyberpunk animated film of the same name, where the main character is an uncontrollable, disruptive force. The prevailing theory is that the band uses this name to present itself in the same way.
The band has also adopted a retro, green-screen terminal aesthetic for its website and logo.

Anatomy of an Akira attack
Akira’s modus operandi reveals a well-established methodology. Initial access is usually gained by exploiting vulnerabilities in virtual private networks (VPNs), particularly those lacking multi-factor authentication. Attackers also use targeted phishing techniques and the exploitation ofremote access protocolssuch as RDP.
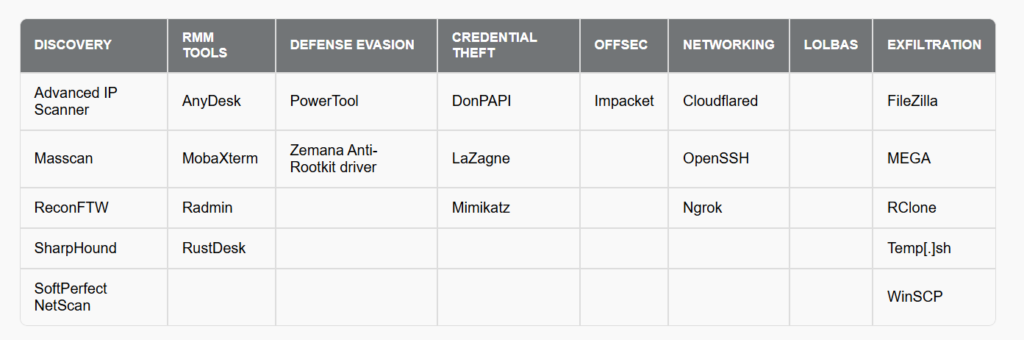
Once inside the network, Akira operators set about establishing a lasting presence. They create fictitious accounts or compromise existing administrator accounts, then use network reconnaissance tools to map the infrastructure and identify priority targets.
The next phase demonstrates the perfidy of this group: even before encryption, the attackers exfiltrate sensitive data.
This double extortion approach enables them to exert additional pressure on victims, threatening to disclose the information if the ransom is not paid. For exfiltration, they rely on tools such as WinSCP, FileZilla and Rclone.
The process concludes with an atypical ransom demand. Unlike other groups, Akira does not display a detailed initial note, but instead directs victims to a site on the Tor network where payments are required in Bitcoin.
Akira’s growing impact in recent news
The year 2025 confirmed Akira’s rise to prominence. In January, security reports identified it as the most active ransomware globally.
This dominance was sadly illustrated in November 2024, when the group disclosed the data of over 30 victims in a single day – an unprecedented event that testifies to the scale of their operations.
The US healthcare sector suffered particularly from Akira’s attacks, to the extent that the Health Sector Cybersecurity Coordination Center (HC3) had to issue a formal warning in February 2024.
More recently, in February 2025, an Australian engineering company was added to the list of victims, demonstrating the international reach of this threat.
Another highlight was Akira’s exploitation of critical vulnerabilities in Veeam Backup & Replication systems in October 2024. This event underlines the crucial importance of rapid security patching, as attackers systematically exploit known vulnerabilities before organizations have time to protect themselves.
Effective protection strategies against Akira
To counter this threat, a multi-layered defensive approach is required. Multifactor authentication is an essential first line of defense, particularly for VPN access, webmail services and high-privilege accounts. This simple measure can neutralize many initial access attempts.
Vulnerability management and the rapid application of security patches also play a decisive role. Organizations need to put in place a rigorous process to identify and remediate vulnerabilities, prioritizing those actively exploited by groups like Akira.
Network segmentation represents a valuable complementary defensive strategy. By limiting communications between different parts of the network, organizations can contain the lateral spread of ransomware and significantly reduce the potential impact of an intrusion.
Proactive network monitoring, combined with endpoint detection and response (EDR) solutions, canidentify suspicious behavior before it becomes a full-blown compromise. This early detection often makes the difference between a minor incident and a major catastrophe.
Filtering network traffic, in particular by blocking access from unapproved sources to critical internal services, completes this protection scheme. This measure considerably limits the exploitable attack surface.
A robust backup strategy remains the last bastion against data loss. Backups must be regular, encrypted and, above all, kept offline to prevent them being compromised in the event of an attack. Their restoration must be periodically tested to guarantee their reliability in real-life situations.
Finally, employee awareness remains a fundamental element of any cybersecurity strategy. Employees who are aware of the risks and of attack techniques such as phishing are better equipped to identify and report intrusion attempts.

Preparedness and resilience to deal with the threat
The growing sophistication of Akira and similar ransomware makes absolute protection illusory. That’s why organizations also need to prepare for the eventuality of a compromise.
A clearly defined, regularly updated and tested incident response plan can significantly reduce the reaction time and impact of an attack. This plan must identify responsibilities, establish communication channels and foresee the stages of containment, eradication and recovery.
Resources available on institutional sites such as stopransomware.gov offer valuable information for understanding current threats and adopting best practices.
Recently, security researcher Yohanes Nugroho developed a decryptor for the Linux version of the Akira ransomware. This tool uses the processing power of the GPU to recover the decryption key and unlock files free of charge.
In the event of an incident, SOS Ransomware offers 24-hour emergency assistance.
The final word
The Akira ransomware illustrates the continuing evolution of cyberthreats facing organizations today. Its sophisticated methodology, combining network compromise, data exfiltration and destructive encryption, makes it a formidable adversary.
Being on the front line, organizations cannot afford to do nothing. A defense-in-depth strategy, combining technical measures, organizational processes and human awareness, represents the best approach to reducing risk.
Constant vigilance, rigorous application of good security practices and incident preparedness are the cornerstones of a security posture adapted to this type of ransomware attack.
Fighting groups like Akira requires sustained effort and continuous adaptation to changes in their tactics. It’s an everyday challenge that IT managers, security teams and business leaders must collectively rise to.
Article source :
StopRansomware: Akira Ransomware on the US Cyber Defense Agency website
New Akira ransomware decryptor cracks encryptions keys using GPUs
Ransomfeed: monthly statistics
FAQ
How does Akira initially access victims’ systems?
– Known vulnerabilities in Cisco VPNs, often in the absence of multi-factor authentication (MFA).
– Internet-exposed services, such as Remote Desktop Protocol (RDP).
– Spear-phishing (via malicious attachments or links).
– The use of compromised valid credentials.
What techniques does Akira use once it has accessed a network?
– Creating new domain accounts to ensure persistence.
– Extracting credentials from the LSASS (Local Security Authority Subsystem Service) memory using techniques like Kerberoasting or tools like Mimikatz and LaZagne.
– Using network discovery tools like SoftPerfect and Advanced IP Scanner to map the victim’s network.
– Deleting volume shadow copies on Windows systems to prevent data restoration.
