First appearing in October 2025, Genesis has rapidly established itself as a formidable new player in the ransomware landscape. This emerging cybercriminal group has caught the attention of cybersecurity experts with its methodical approach, primarily targeting US organizations holding sensitive or regulated data. Specializing in data exfiltration and double extortion, Genesis represents a growing threat to businesses in all sectors.
Table des matières
ToggleA new player with assertive ambitions
Genesis’ emergence in the ransomware ecosystem is no accident. According to the CYFIRMA report of October 2025, this group surfaced with a clearly honed operational structure, claiming 12 confirmed victims in its first month of activity. This high-profile entry suggests the involvement of experienced actors, possibly from other ransomware groups or organized cybercriminal circles.
To date, the ransomware.live tracker has counted over 21 victims, mainly in the USA (19 victims), the UK (1 victim) and Malaysia (1 victim). This geographic concentration reflects a deliberate targeting strategy, focusing on developed economies where organizations hold high-value data and have substantial financial resources at their disposal.
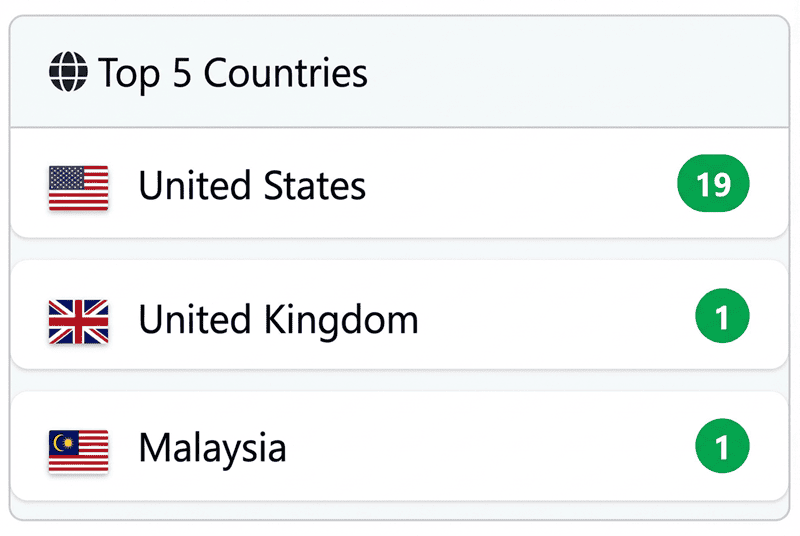
Genesis’ rapid recognition by cybersecurity analysts confirms its disruptive potential. Within the first few weeks of its activity, the group was identified by CYFIRMA as “a notable entrant with high escalation potential within the ransomware ecosystem”, underlining the strategic importance of this new threat in the analysis of contemporary cyber risks.
Targeting strategy: precision and opportunism
Unlike opportunistic ransomware operators who deploy indiscriminate mass attack campaigns, Genesis favors a strategic, selective approach. The group deliberately targets organizations managing sensitive or regulated data, thus maximizing the leverage exerted on its victims.
Economic sectors targeted
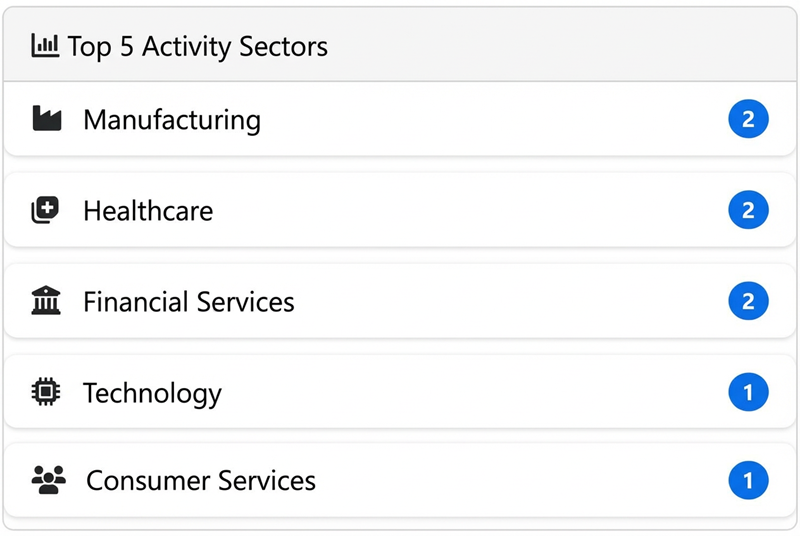
An analysis of the victims reveals a particularly well thought-out multi-sector targeting strategy:
- Legal services: law firms such as Ronemus & Vilensky (New York), Kipp & Christian (Salt Lake City), Roth & Scholl, holders of confidential customer information
- Healthcare: River City Eye Care (Portland), Claimlinx (health insurance), exposing sensitive medical records
- Finance: Austin Capital Trust, Advantage CDC (long-term loans), targeted for their critical financial data
- Manufacturing: Southern Specialty and Supply (offshore/onshore), Heimbrock Inc (refractory construction)
- Retail: Healthy Living Market & Café, exhibiting HR and financial data
- Construction: Manusos General Contracting, S.B. Conrad Inc, targeted for contractual information
Typical victim profile
Genesis mainly targets American SMEs and mid-sized organizations, a segment often characterized by limited cybersecurity resources but sufficient financial capacity to consider paying a ransom. This strategy enables the group to optimize its effort/return ratio while avoiding the massive media attention generated by attacks on large corporations.
Modus operandi: extortion through exposure
An approach focused on exfiltration
The distinctive feature of Genesis is its focus on data exfiltration rather than encryption. According to CYFIRMA, the group “focuses primarily on data exfiltration and public leaks rather than encryption, using exposure to exert financial and reputational pressure on its victims”.
This approach is part of the broader evolution of modern ransomware, where the threat of data disclosure is often a more effective lever than simply blocking systems. Indeed, even organizations with robust backups remain vulnerable to reputational pressure and legal obligations to notify data breaches.
Volume of data exfiltrated
The first documented attacks reveal the scale of Genesis’ operations. According to Comparitech, the group claims to have exfiltrated 2.2 terabytes of data in its first nine publicly announced attacks. Specific examples illustrate this massive extraction capacity:
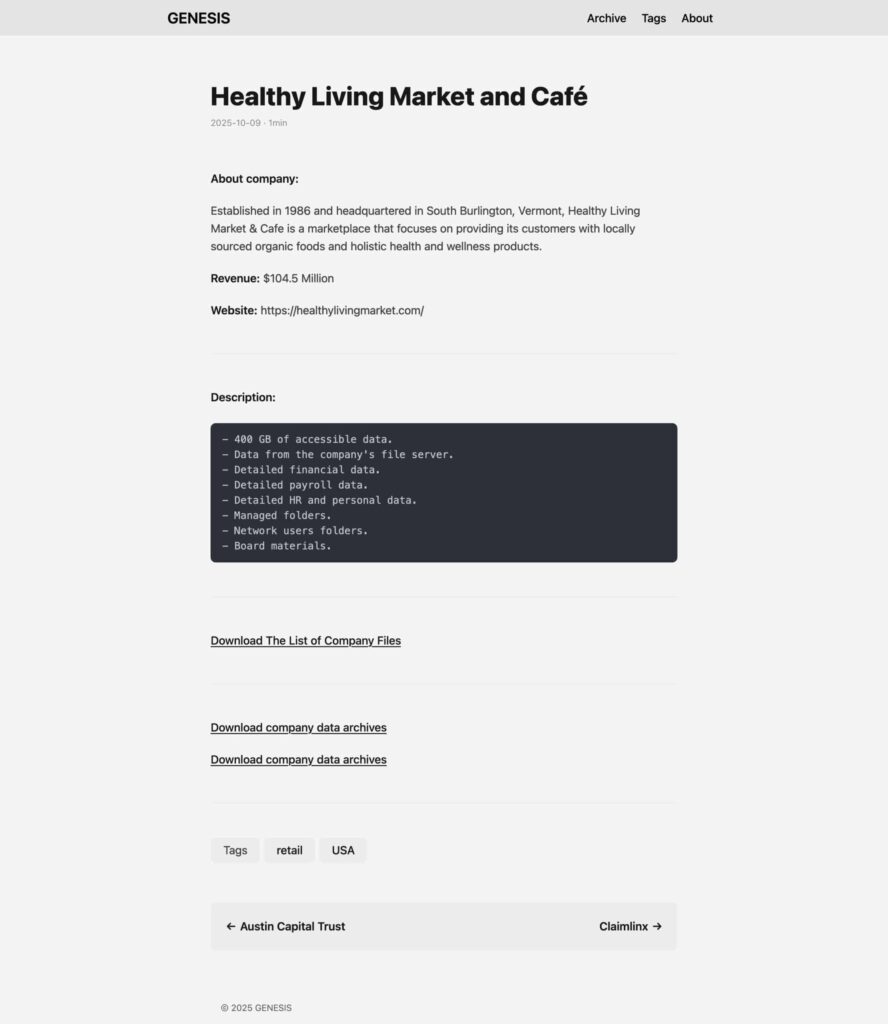
400 GB of Healthy Living Market & Café data (financial information, payroll, HR):
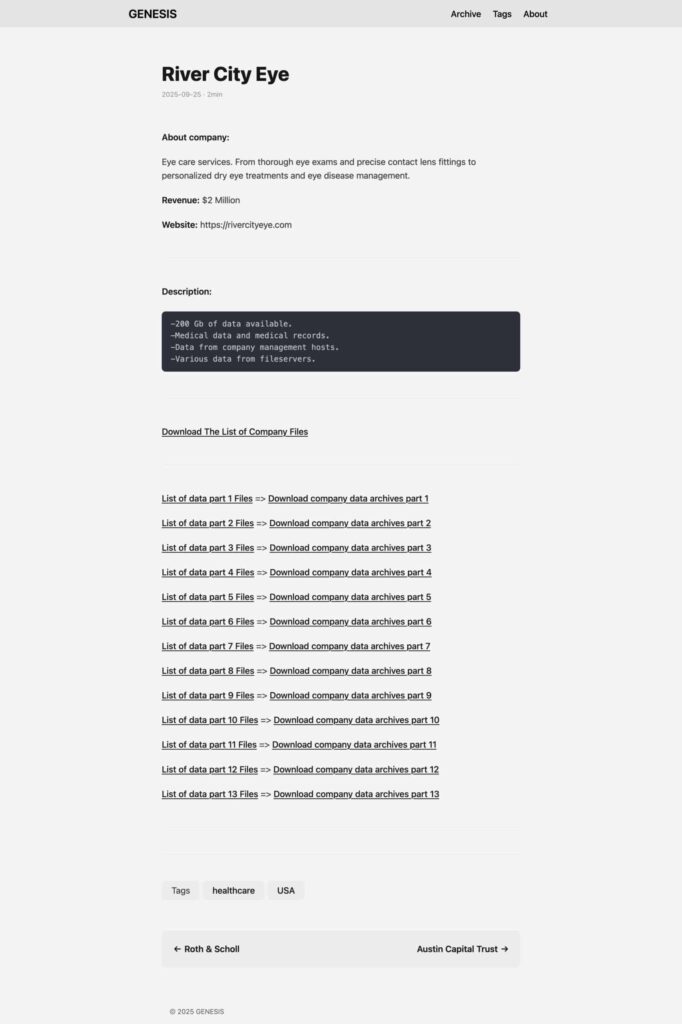
200 GB of data from River City Eye Care (medical records, social security numbers):
Extortion infrastructure
Genesis maintains an active presence on the dark web via a dedicated leak site accessible on the TOR network. This platform forms the strategic heart of their extortion operations, where the group periodically publishes information about its victims and evidence of compromise.
According to WatchGuard Technologies, Genesis employs several extortion tactics:
- Direct extortion: ransom demand in exchange for non-publication of data
- Double extortion: Combining encryption with the threat of disclosure
- Price escalation: Gradual increase in the ransom amount
Emblematic victims: revealing case studies
Examining specific Genesis victims offers valuable insight into their operational methods and the real impact of their activities.
Healthy Living Market & Café
This organic grocery chain (Road to Hana, Inc) was the victim of an attack in September 2025 that compromised financial, payroll and HR information. The company’s official notification confirms, “On or about September 22, 2025, Healthy Living was the victim of a ransomware attack in which a malicious actor gained unauthorized access to one of our local servers.”
River City Eye Care
This Portland, Oregon-based optometry clinic reported a data breach following an intrusion dated September 8, 2025. Compromised data includes names, phone numbers, dates of birth, addresses, as well as social security and driver’s license numbers for some patients. Genesis claims to have exfiltrated 200 GB of medical records.
Law firms targeted
Of note: some Genesis victims, such as law firms Roth & Scholl and Ronemus & Vilensky, have also been claimed by other ransomware groups (Play and Kraken respectively). This situation illustrates either simultaneous multiple attacks or potentially fraudulent claims in the competitive ransomware ecosystem.
Chronology of documented attacks
The following table lists the main known Genesis victims:
| Victim | Sector | Date discovered | Country |
|---|---|---|---|
| Healthy Living Market & Café | Commerce/Food | 21/10/2025 | USA |
| River City Eye Care | Health | 21/10/2025 | USA |
| Ronemus & Vilensky | Legal | 21/10/2025 | USA |
| Claimlinx | Health insurance | 21/10/2025 | USA |
| Austin Capital Trust | Finance | 21/10/2025 | USA |
| Roth & Scholl | Legal | 21/10/2025 | USA |
| Southern Specialty and Supply | Industry | 21/10/2025 | USA |
| Kipp & Christian | Legal | 28/10/2025 | USA |
| Advantage CDC | Finance | 28/10/2025 | USA |
| Manusos General Contracting | Construction | 11/11/2025 | USA |
| S.B. Conrad, Inc | Construction | 11/11/2025 | USA |
| Lows Orkney | Legal/accounting services | 11/11/2025 | UK |
Context: a changing ransomware ecosystem
The emergence of Genesis takes place against a backdrop of a global upsurge in ransomware attacks. According to the CYFIRMA report for October 2025, the number of victims reached 738 that month, compared with 545 in September, an increase of 35%. This marks a significant upturn after a period of relative stability in mid-2025.
The CheckPoint Research report confirms this trend, noting an average of 1,938 cyberattacks per week per organization in October 2025, a 5% increase on October 2024. This escalation is fuelled by the growing sophistication of ransomware operations and the expansion of risks associated with the adoption of generative AI.
The appearance of Genesis also coincides with the emergence of other new groups such as Black Shrantac and Coinbase Cartel, illustrating the continued fragmentation of the ransomware ecosystem following law enforcement actions against major players such as LockBit and ALPHV/BlackCat.
Defensive strategies: towards adaptive resilience
Data protection and exfiltration prevention
Faced with a group like Genesis, whose strategy is based on exfiltration, preventing data leakage becomes paramount:
- Deployment of DLP (Data Loss Prevention) solutions: Monitoring and blocking unauthorized data transfers
- Advanced network segmentation: isolation of sensitive data to limit lateral propagation
- Encryption of data at rest: Protection of sensitive files against exploitable exfiltration
- Outbound traffic monitoring: Detection of unusually large data transfers
Access management and authentication
- Multi-factor authentication (MFA): mandatory for all accounts, especially privileged ones
- Least privilege principle: Strict limitation of permissions to actual operational needs
- Account monitoring: Detection of abnormal behavior and suspicious access
Incident preparation and response
- Incident response plan : Procedures documented and tested regularly
- Offline backups: Copies disconnected from the network and tested for recovery
- Continuous monitoring: Monitoring of leak sites and the dark web to detect compromises
- Employee training: Awareness of phishing and social engineering techniques
Future prospects
The evolution of Genesis over the coming months will be decisive in assessing its place in the threat ecosystem. Several factors suggest significant growth potential:
- Organized structure: Operational efficiency in the first month suggests an experienced team.
- Strategic focus: Focus on high-value sectors with regulatory obligations
- Proven business model: Double extortion approach maximizes chances of payment
- Favorable context: Global increase in ransomware attacks creates a favorable environment
The cybersecurity community will be keeping a particularly close eye on the evolution of Genesis’ tactics, techniques and procedures (TTPs), as well as any indications of links with other established cybercriminal groups.
Conclusion: vigilance against an emerging threat
Genesis represents the epitome of the challenges posed by the new generation of cybercriminal groups: rapid emergence, structured organization and a sophisticated extortion strategy focused on the exfiltration of sensitive data.
With over 12 confirmed victims in just a few weeks of activity and 2.2 terabytes of data claimed as exfiltrated, the group poses a real and growing threat to global organizations, particularly those operating in the USA in sectors handling sensitive or regulated data.
The best defense remains a multi-layered preventive approach combining protection against data exfiltration, rigorous access management, network segmentation, ongoing user training and a regularly tested business continuity plan. This approach must include a dimension of continuous monitoring of the evolution of this emerging threat.
In the event of an incident, the involvement of experts specialized in ransomware data recovery optimizes the chances of recovery, while minimizing the operational and financial impact. SOS Ransomware supports victim organizations in crisis management and system restoration.
Main article sources
- CYFIRMA: Tracking Ransomware: October 2025
- Comparitech : New ransomware gang Genesis claims 9 data breaches
- WatchGuard Technologies: Genesis Ransomware Tracker
- Ransomware.live : Genesis Group Profile
- CheckPoint Research : Global Cyber Attacks Surge in October 2025
- DeXpose : Genesis Ransomware Attack Reports
