Since August 2023, INC Ransom has established itself as a major cybercriminal player in the international IT security arena. Specializing in double extortion, this group has developed a particularly formidable modus operandi, combining theft of sensitive data and encryption of systems to maximize the pressure exerted on its victims.
Table des matières
ToggleA major player with many faces
INC Ransom’s reputation in the world of cybercrime is no accident. Their meteoric rise is based on a remarkable ability to adapt and surgically precise targeted attacks. The figures speak for themselves: according to Trend Micro data, the group orchestrated at least 325 attack attempts between October 2023 and August 2024.
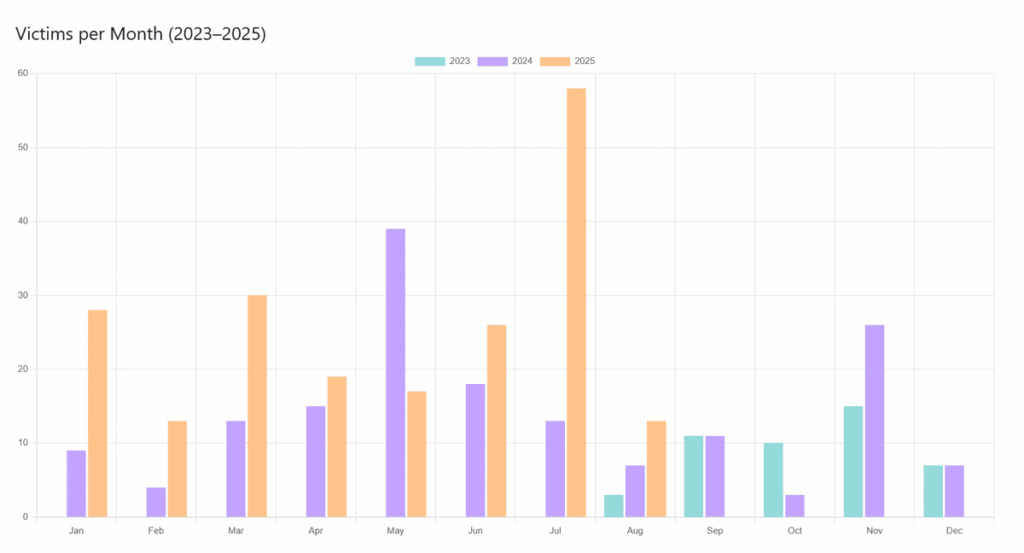
This frenzy of activity reveals a remarkable operational consistency, with the group maintaining a steady attack pace since its emergence. There was a spectacular intensification in 2025, with a peak in activity in July, when almost 60 victims were recorded in a single month. This regularity in the production of attacks testifies to a robust infrastructure and a perfectly honed criminal organization, capable of adapting to cycles of vulnerability and periods of reduced vigilance on the part of target organizations.
The recognition of INC Ransom as an emerging threat by Secureworks as early as August 2023 confirms the relevance of this new cybercriminal force. This early identification by IT security specialists illustrates the strategic importance that this group now represents in the analysis of contemporary cyber risks, marking its definitive entry into the closed circle of leading threats.
Targeting strategy: precision and profitability
Unlike opportunistic ransomware operators who deploy indiscriminate mass attack campaigns, INC Ransom favors a methodical, selective approach. The group deliberately targets entities with substantial financial resources and managing significant volumes of sensitive data.
This targeted strategy enables them to maximize their profits while optimizing their efforts, an approach that testifies to their increasing professionalization in the modern cybercrime landscape. Rather than spreading their efforts over multiple low-value targets, they concentrate their resources on victims selected according to precise economic and strategic criteria.
Intrusion arsenal: diversity and sophistication
Multiple, adaptive access vectors
INC Ransom’s sophistication is evident right from the initial phases of their operations, where the group demonstrates mastery of multiple intrusion vectors. Exploiting vulnerabilities is their preferred method, with particular attention paid to the CVE-2023-3519 flaw affecting Citrix NetScaler.
This critical vulnerability, documented by Trend Micro, was massively exploited by the group, illustrating their ability to quickly identify and exploit emerging security flaws in corporate infrastructures. This reactivity to zero-day vulnerabilities testifies to an active technological watch and considerable technical expertise.
Alongside this technical approach, INC Ransom does not hesitate to use social engineering techniques. Their particularly elaborate spear-phishing campaigns aim to compromise user credentials by exploiting human rather than technical vulnerabilities. These personalized attacks reveal a thorough reconnaissance phase of the targeted organizations, enabling the group to create decoys of remarkable credibility.
The group also reveals its economic dimension by resorting to the purchase of valid identifiers from so-called “Initial Access Brokers”, an essential link in the cybercrime underground economy. This pragmatic approach illustrates the professionalization of the sector, where initial access to an infrastructure can be purchased rather than developed, allowing specialized groups to concentrate on their core skills in encryption and extortion.
Attack methodology: a tried-and-tested infection chain
Once initial access has been gained, INC Ransom deploys a well-honed, multi-stage attack methodology, demonstrating considerable technical expertise and an in-depth understanding of modern corporate environments.
The reconnaissance phase is the crucial first step in this infection chain. The group uses specialized tools such as NetScan and Advanced IP Scanner to meticulously map their victims’ network architecture, identifying critical systems, points of vulnerability and potential propagation paths.
Lateral movement represents the next step in this methodical progression. INC Ransom deploys a panoply of tools to propagate through the compromised infrastructure: PSExec for remote command execution, AnyDesk for remote access, and TightVNC for system control. This diversity of tools reveals a sophisticated redundancy strategy, where several persistence and propagation mechanisms are implemented simultaneously.
Privilege escalation demonstrates particularly advanced technical expertise. The group uses specialized tools such as lsassy.py, a sophisticated Python tool for extracting identifiers from the memory of Windows systems. Even more remarkably, Trend Micro has documented INC Ransom’s use of new tools developed specifically to extract credentials from Veeam Backup and Replication managers , revealing a constant adaptation to modern backup technologies.
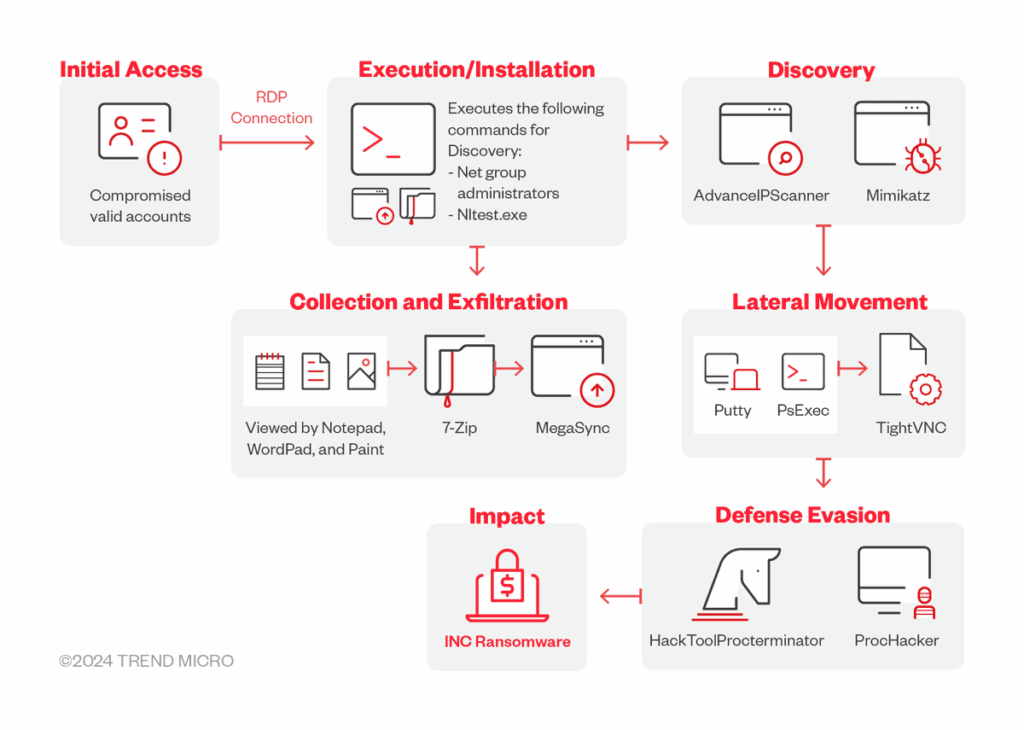
Evasion techniques: the art of invisibility
INC Ransom’s sophistication is also evident in their mastery of evasion techniques, essential for maintaining their presence in compromised systems while avoiding detection by modern security solutions.
The group excels in the use oflegitimate tools diverted from their original function, an approach known as “Living off the Land”. This strategy involves exploiting native system tools such as PowerShell, WMIC and cmd.exe, which are naturally present in Windows environments and whose use does not immediately arouse the suspicions of surveillance systems.
Disguising malicious tools is another facet of their evasion expertise. For example, the group systematically renames PSExec, a legitimate Microsoft tool, as “winupd” to imitate a genuine Windows update. This attention to detail in concealment reveals a deep understanding of normal system processes.
Removing evidence is a crucial aspect of their post-intrusion methodology. INC Ransom systematically uses wevtutil, a legitimate Windows utility, to erase security logs and thus eliminate traces of their activity. This methodical cleaning approach significantly complicates the investigative work of incident response teams.
Particularly revealing of their adaptation to specific threats, the group deploys tools such as HackTool.ProcTerminator specifically designed to terminate processes related to security solutions, including those from TrendMicro. This targeted approach demonstrates an active watch on protection solutions on the market.
Threat geography: strategic targeting
Geographic concentration and strategic implications
Analysis of the geographic distribution of INC Ransom’s victims reveals significant strategic patterns that shed light on the group’s motivations. The United States dominates the statistics, accounting for 57.9% of victims according to SOC Radar, a proportion that reflects the particular attractiveness of this market for cybercriminals.
This geographical concentration can be explained by several converging factors: the relative wealth of American companies, their critical dependence on digital technologies, and paradoxically, their presumed financial capacity to pay substantial ransoms.
Europe is the Group’s second preferred theater of operations, with a notable presence in the UK, France, Germany and the Netherlands. This selection reveals a strategic understanding of developed economic markets, where companies manage large volumes of sensitive data and generally have the financial resources to respond to ransomware demands.
Economic sectors: targeted vulnerabilities
The sectoral analysis of victims reveals a particularly well-thought-out targeting strategy that exploits the specific vulnerabilities of certain business sectors. According to SOC Radar, professional services, manufacturing and construction are the most frequently targeted sectors.
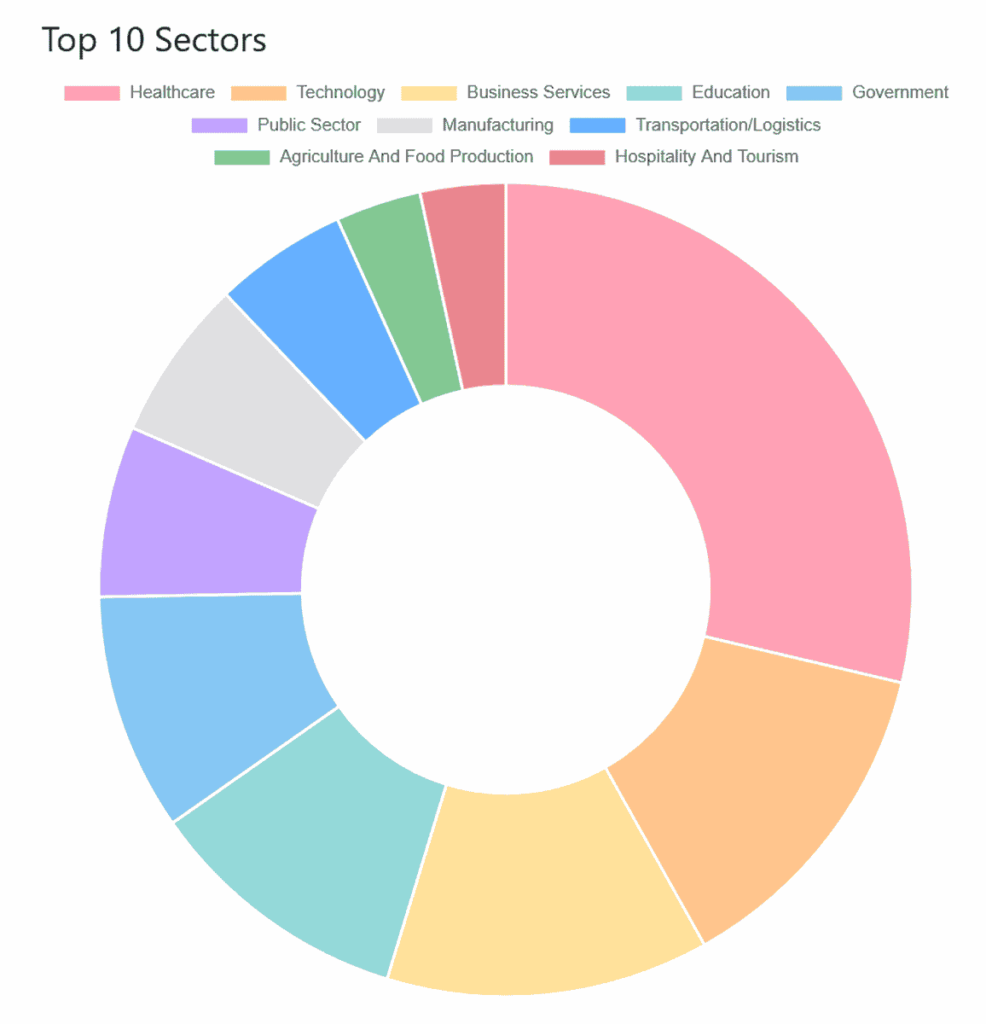
Professional services are particularly attractive due to their critical dependence on customer data and their confidentiality obligations. Law firms, consultants and financial services companies manage huge volumes of sensitive information, the public disclosure of which could have catastrophic consequences.
The manufacturing sector attracts attention for different but complementary reasons. These companies are often dependent on critical industrial infrastructures, the disruption of which can lead to considerable financial losses and unacceptable production delays.
Trend Micro also identifies healthcare and education among the sectors of focus, both of which present specific vulnerabilities that can be particularly exploited. The healthcare sector combines the management of highly sensitive personal data with critical operational imperatives.
Emblematic victims: revealing case studies
Examining specific INC Ransom victims offers valuable insight into their operational methods and the real impact of their activities.
The case ofAFPA, the French vocational training organization, is a perfect illustration of the group’s ability to target public or para-public institutions. INC Ransom claims to have stolen 5 terabytes of sensitive data from this organization, a considerable quantity that testifies to the duration and scale of their presence in compromised systems.
The attack on NHS Dumfries & Galloway in Scotland represents a particularly worrying case that illustrates the potential impact on essential public services. Confirmed in March 2024, this attack resulted in the compromise of patient data and the threatened release of 3 terabytes of sensitive medical information.
The case of Yamaha Motor Philippines offers a different perspective, demonstrating their ability to target subsidiaries of multinational companies. The attack confirmed on October 25 focused on a specific server managing employee data, revealing a surgical approach capable of targeting particular components of the infrastructure.
More recent attacks on the Radford Public Schools in Virginia and La Biennale di Venezia testify to the group’s operational continuity in 2025, affecting both public education and prestigious cultural institutions.
Extortion infrastructure: criminal sophistication
Technical architecture of double extortion
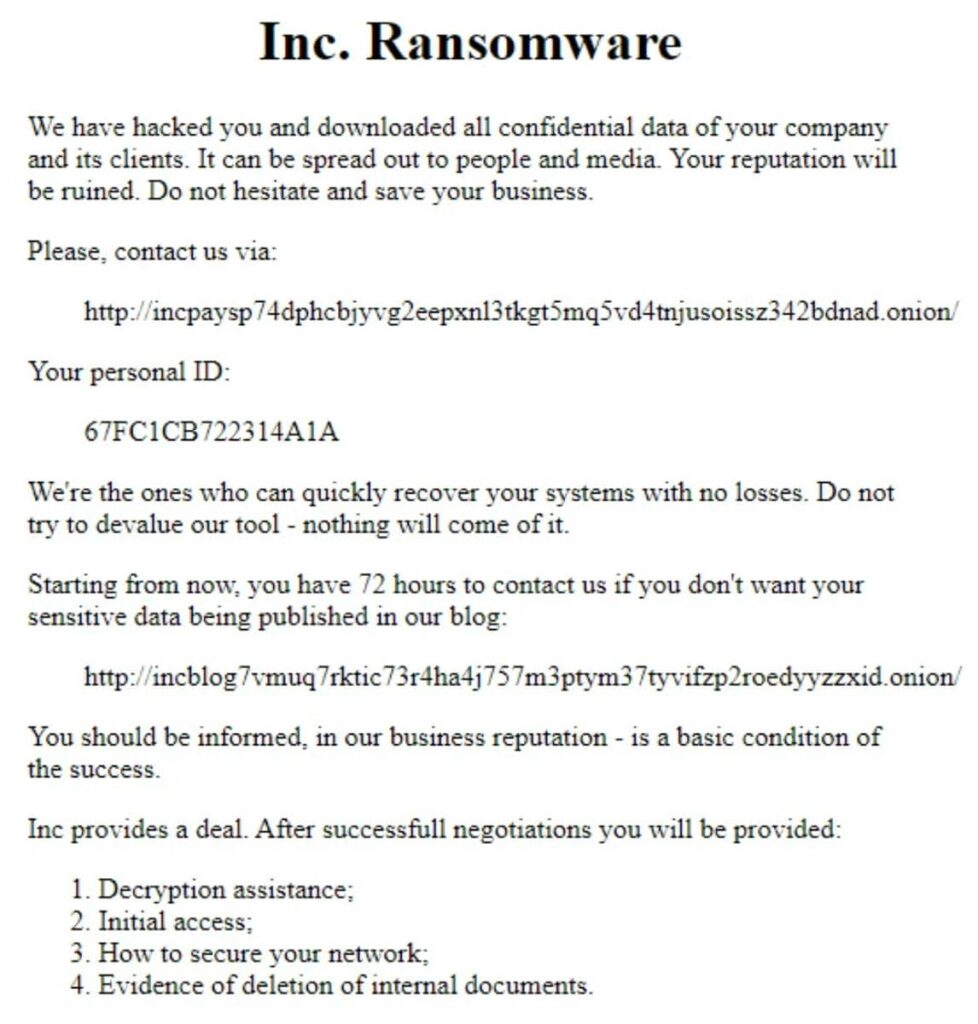
INC Ransom’s sophistication extends to theelaborate infrastructure they have developed to maximize the effectiveness of their extortion strategies. This digital infrastructure is much more than just a website: it represents the strategic core of their extortion operations. The group maintains an active presence on the dark web through a TOR platform where it periodically publishes information on its successful cyberattacks, turning each compromise into an additional pressure tool.
The architecture of this platform reveals a deep understanding of the psychology of extortion. By making public information about their victims and evidence of compromise, INC Ransom creates social and reputational pressure that effectively complements the technical pressure exerted by encrypting systems, thus increasing their chances of obtaining payment of the ransoms demanded.
Psychological pressure mechanisms
Beyond the digital infrastructure, INC Ransom deploys particularly sophisticated psychological pressure mechanisms. The automatic printing of ransom notes on all printers in the compromised network is an effective tactic that transforms every printing device into a communication vector for the threat.
Systematically changing the wallpaper of all compromised workstations with a compromise message is another facet of this communication saturation strategy. By making the compromise visible on every screen in the organization, INC Ransom ensures that the impact of their attack cannot be minimized or concealed.
The threat of publication of sensitive data represents the most sophisticated leverage in the group’s arsenal. INC Ransom specifically targets the types of information whose public disclosure would have the most devastating impact: passports and identity documents, confidentiality agreements revealing sensitive strategic information, and internal financial documents.
Technical evolution: constant adaptation
Multi-platform development
INC Ransom’s technical evolution bears witness to its growing sophistication and remarkable adaptability. Trend Micro’s detailed analysis reveals further gradual development, illustrating the group’s rapid maturation.
The first Windows version, released in July 2023, already laid the technical foundations of their approach. The introduction of a Linux version in December 2023 marks a significant milestone, revealing their understanding of the importance of Unix environments in modern enterprise infrastructures.
The most recent Windows version, detected in March 2024, incorporates significantly enhanced features that reflect the group’s continuous learning. This rapid evolution, with major updates every four to six months, bears witness to an organized development process.
Advanced operational granularity
Technical sophistication is particularly evident in the granularity of the configuration options developed for their ransomware. Analysis of the command line arguments supported reveals a remarkable level of operational sophistication.
The selective encryption functionality, accessible via the “–file” argument, enables the group to specifically target critical files rather than blindly encrypt the entire system. This surgical approach can be particularly effective in specific contexts.
The “–mode” option introduced in recent versions illustrates this quest for operational optimization. The three modes available – fast, medium and slow – enable the group to tailor their approach to specific time constraints and tactical objectives.
| Argument | Function |
|---|---|
| –debug | Displays debug logs in the terminal |
| –file | Encrypts a specific file |
| –dir | Encrypts a directory |
| –sup | Stops the use of processes |
| –ens | Encrypts network shares |
| –lhd | Encrypts hidden and recovery volumes |
| –mode | Choice of encryption mode (fast/medium/slow) |
| –hide | Hides the console window |
| –safe-mode | Terminates processes/services by mask |
| –help | Displays available arguments |
| –kill | Starts the victim machine in safe mode |
| –daemon | Turns the sample into a daemon process (Linux) |
| –motd | Modifies message of the day (Linux) |
| –skip | Prevents VM termination (Linux) |
Defensive strategies: towards adaptive resilience
Holistic security architecture
Combating sophisticated adversaries such as INC Ransom requires a security approach that transcends traditional technical measures to embrace a holistic vision of organizational resilience.
Rigorous management of privileged accounts is the foundation of this defensive approach, as these accounts represent the priority targets of advanced ransomware groups. Strictly limiting service account permissions requires a granular analysis of actual operational needs.
Multi-factor authentication, now mandatory for all administrator accounts, is only one element of a broader authentication strategy. This approach must incorporate adaptive authentication mechanisms that take account of context, geolocation and behavioral patterns.
Securing the network requires a segmentation approach that goes far beyond mere technical isolation. Effective network segmentation must reflect the organization’s actual data flows, creating graduated zones of trust that naturally limit lateral propagation.
Backup strategies and continuity
Designing attack-resistant backup strategies requires an approach that recognizes the evolved nature of contemporary threats. Regular offline backups disconnected from the network are only the bare minimum.
Regular testing of restoration procedures is a critical aspect that is often overlooked. These tests should not be limited to technical verification of data recovery, but should simulate realistic attack scenarios, including partial compromise of backup systems.
Operational continuity in the face of an attack also requires the development of degraded operating procedures that enable the organization to maintain its critical functions even in the event of widespread compromise of its digital infrastructure.
Advanced detection and adaptive response
Effective detection of INC Ransom activities requires an in-depth understanding of their specific techniques. According to Trend Micro’s recommendations, monitoring should focus on the abnormal use of legitimate tools such as PowerShell and WMIC.
Detecting suspicious RDP connections and lateral movements requires real-time traffic analysis capabilities that can correlate seemingly independent events to identify sophisticated attack patterns.
Identifyingunusual archiving of large amounts of data is a particular challenge in environments where handling large volumes of information is a normal activity. Detection systems need to incorporate a contextual understanding of organizational data flows.
Geopolitical implications and future prospects
Geopolitical contextualization
INC Ransom’s activity takes place in a complex geopolitical context, where cyberattacks transcend national borders and challenge traditional concepts of sovereignty and jurisdiction. The geographical concentration of their attacks on developed economies raises important questions about the systemic vulnerabilities of highly digitized societies.
Analysis of geographic patterns also reveals asymmetries in global cyber defense capabilities and regulatory arbitrage opportunities exploited by cybercriminal groups. The group’s ability to operate with impunity across multiple jurisdictions illustrates the limits of current international cooperation mechanisms.
Emerging trends
Observation of INC Ransom’s evolution between 2023 and 2025 reveals several trends characteristic of the contemporary threat ecosystem. The increasing professionalization of their operations, with the development of bespoke tools and the adoption of modern software development practices, testifies to the rapid maturation of the cybercriminal sector.
The increasingly precise targeting of critical sectors such as healthcare and education reveals a strategic shift towards exploiting societal rather than purely technical vulnerabilities. This approach reflects a sophisticated understanding of the social and economic impact of cyber attacks.
The group’s rapid adaptation to the security measures deployed illustrates the fundamentally reactive nature of many cybersecurity approaches, and the need to develop proactive strategies capable of anticipating evolving threats.
Conclusion: in the face of a constantly evolving threat
INC Ransom represents the epitome of the challenges posed by the new generation of cybercriminal groups: technical sophistication documented by MITRE ATT&CK across 25 distinct techniques, remarkable adaptability and a strategic understanding of modern organizational vulnerabilities.
With 325 confirmed attack attempts since October 2023 and over 165 victims published on their leak site, the group poses a persistent and evolving threat to global organizations. In-depth analysis of their methods reveals that combating such adversaries requires a fundamental transformation of the traditional approach to cybersecurity.
Security can no longer be conceived as a set of static technical measures, but must evolve towards a model of adaptive resilience capable of anticipating, detecting and responding to constantly evolving threats. This adaptive resilience must integrate several complementary dimensions: technical sophistication to match the complexity of attacks, organizational agility to adapt rapidly to new threats, and cross-sector collaboration to share knowledge in the face of adversaries who transcend borders.
The best defense remains a multi-layered preventive approach that combines rigorous systems updating, ongoing user training, dynamic network segmentation and a regularly tested business continuity plan. This approach must now incorporate a dimension of continuous learning and proactive adaptation that recognizes the fundamentally evolving nature of contemporary threats.
In the event of an incident, the involvement of specialized experts optimizes the chances of recovery, while minimizing the operational and financial impact. This reactive response must be part of a broader organizational resilience strategy that prepares the organization to face future challenges rather than just current threats.
The growing sophistication of INC Ransom and its demonstrated ability to adapt to defensive measures underline the crucial importance of continuous security intelligence and proactive preparation in the face of this constantly evolving threat. The future of organizational cybersecurity will depend on the ability of defenders to maintain the pace of innovation and adaptation required to deal with increasingly sophisticated and determined adversaries.
Main article sources:
- Trend Micro: Ransomware Spotlight: INC
- SOCRadae: Dark Web Profile: INC Ransom
- Secureworks: GOLD IONIC Deploys INC Ransomware
- SentinelOne : Inc. Ransom
- Ransomware live: Incransom
- MITRE ATT&CK : INC Ransom
