First identified in February 2025, the Kraken group quickly distinguished itself in the cybercriminal ecosystem through its sophisticated technical approach. Stemming from the ashes of the HelloKitty cartel, this Russian-speaking ransomware targets Windows, Linux and VMware ESXi environments with a rare feature: it evaluates the performance of each machine before launching encryption, thus optimizing the impact of its attacks while minimizing the risk of detection.
Table des matières
ToggleA direct descendant of HelloKitty
Kraken did not emerge from nowhere. Cisco Talos researchers have established strong links between this new group and the HelloKitty operation, a ransomware program active since November 2020 and made famous by its attack on CD Projekt Red in 2021, during which the source code for Cyberpunk 2077 and The Witcher 3 was stolen. Several technical elements establish a direct link between the two operations: Kraken’s extortion portal displays an explicit reference to HelloKitty, and comparative analysis reveals that both groups’ ransom notes bear an identical file name, a marker rarely fortuitous in this ecosystem.
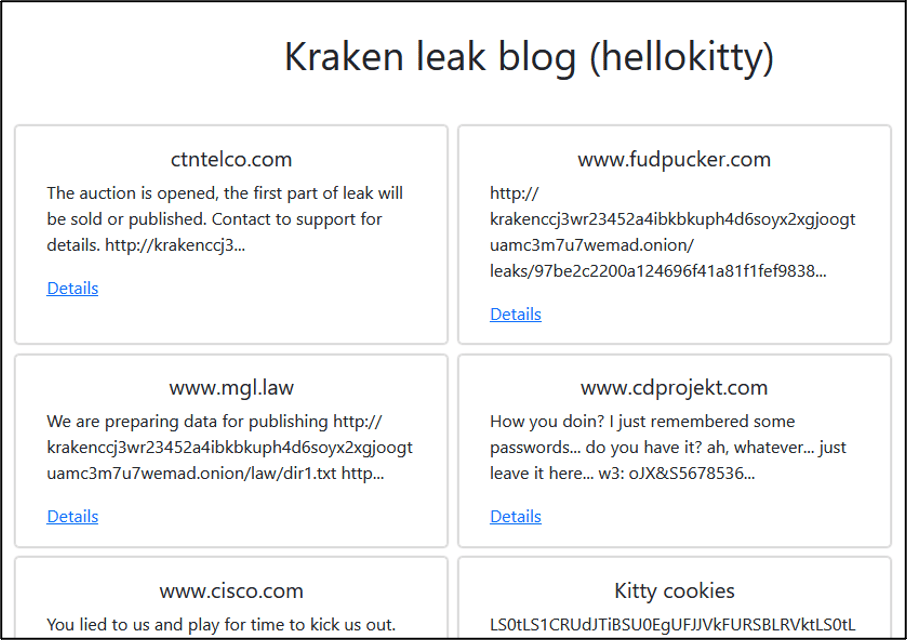
This connection follows the turbulent history of HelloKitty. In October 2023, a malicious actor using the pseudonyms kapuchin0 and Gookee had leaked the ransomware’s complete source code on a Russian-speaking forum, announcing that he wanted to develop ” something more interesting than LockBit “. The published archive contained a Microsoft Visual Studio solution for compiling the HelloKitty encryptor and decryptor, as well as the NTRUEncrypt library used for the cryptographic routines. The researcher 3xp0rt identified this person as the alleged developer of HelloKitty.
In April 2024, HelloKitty renamed itself HelloGookie, releasing decryption keys for older versions and data stolen in the attacks on CD Projekt Red and Cisco. As demonstrated by the Babuk source code leak, which spawned more than nine separate ransomware operations, the release of this type of material usually fuels new variants. The emergence of Kraken in 2025 thus represents a new evolution in this criminal lineage, confirming that well-established ransomware brands don’t really disappear, but reinvent themselves in new forms.
Kraken ransomware infection chain and attack methodology
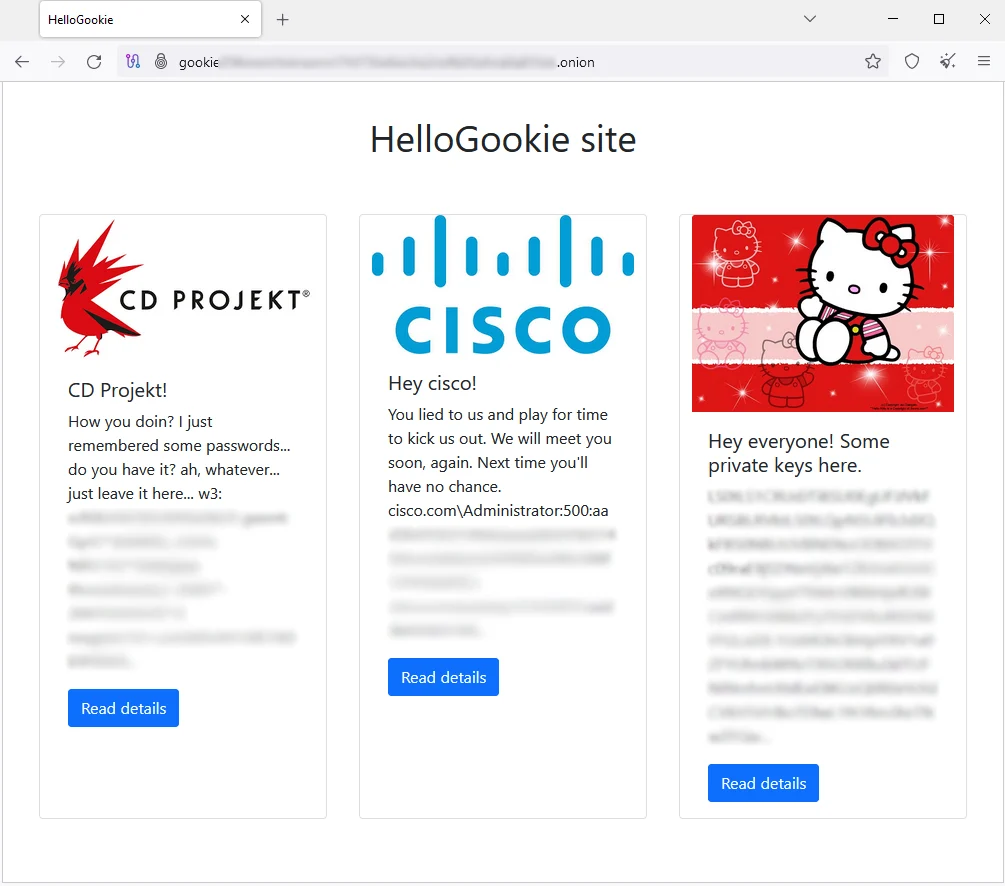
In August 2025, the Cisco Talos Incident Response team documented an intrusion characteristic of the Kraken group, revealing a methodical and sophisticated attack methodology that follows in the tradition of “big-game hunting”, these attacks specifically targeting large organizations capable of paying substantial ransoms.
Initial access is gained byexploiting vulnerabilities in the SMB (Server Message Block)protocol on poorly secured servers accessible from the Internet, to penetrate corporate networks. Once this bridgehead has been established, the attackers extract the credentials of the victim’s administrator and other privileged accounts. They then temporarily leave the environment and re-enter via a Remote Desktop Protocol (RDP) connection using the stolen credentials, a technique which lends them an appearance of legitimacy.
To maintain persistent access, Kraken operators deploy Cloudflared, Cloudflare’s tunneling tool, which they configure to create a reverse tunnel from the victim machine to their infrastructure. At the same time, they install SSHFS (SSH Filesystem), which enables them to navigate the victim’s environment and exfiltrate sensitive data via remotely mounted file systems. This combination of legitimate tools diverted from their normal use makes detection by traditional security solutions considerably more difficult.
Using these persistent connections, attackers move laterally to all accessible machines on the network, steal valuable data and prepare the ground for the deployment of ransomware binaries. The encryptor is then propagated via RDP using compromised privileged accounts, enabling coordinated execution of the ransomware on all targeted systems.
Benchmarking: a rare technical innovation in the ransomware ecosystem
Kraken’s most distinctive feature is its ability to benchmark system performance before initiating encryption. This feature, rarely seen in modern ransomware, enables the attack to be optimized according to the hardware capabilities of each victim machine.
In concrete terms, the ransomware performs a preliminary test to measure the speed at which the machine can encrypt data. Based on this result, it automatically adapts its strategy: full encryption if the machine is powerful enough, or partial block encryption if resources are limited. In both cases, the files become unusable for the victim.
Technical operation of Kraken’s benchmark
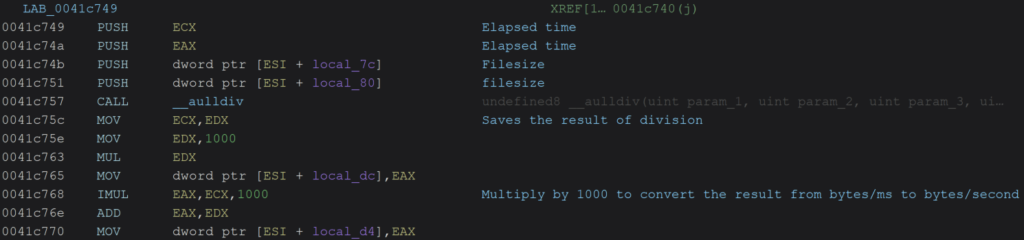
The benchmarking process is based on a precise sequence. The attacker can activate this functionality via the command line options -tests, -tempfile and -tempsize. The ransomware then creates a temporary file at the specified path, fills it with random data in 1 MB blocks until it reaches the defined size, then records the starting time via the clock_gettime function before proceeding with the test encryption.
Once the operation is complete, it calculates the elapsed time and the encryption speed in MB/s according to the formula: Speed = ((total bytes / elapsed time) * 1000) / 1048576. This calculates a throughput (e.g. in MB/s) that reflects the machine’s actual encryption capacity (CPU, disk, I/O). The test file is then deleted using the unlink() function.
On Linux and ESXi systems, the logic remains the same: a performance test is run before the actual encryption, taking multithreading into account to assess the extent to which the machine can be called upon without causing instability. This step is rare in today’s ransomware families, which is what makes Kraken so special.
Full or partial encryption: an automated decision
Depending on the benchmark results, the ransomware automatically opts for full or partial block encryption. If the machine is judged to be sufficiently powerful, Kraken proceeds to full encryption of each file, making recovery extremely difficult. If the measured throughput proves insufficient, the ransomware falls back on partial encryption, affecting only a portion of each file – a faster but equally effective approach to rendering data unusable.
This adaptation enables the attack to be completed within a reasonable timeframe, even on heavy infrastructures such as large file servers or ESXi hypervisors hosting numerous virtual machines, and thus increases the attack’s chances of success.
Tactical benefits for attackers
This preliminary assessment has several strategic objectives. By adapting the encryption mode to the machine’s actual capabilities, Kraken avoids system overload, which could trigger security alerts or visibly degrade performance, thus attracting the attention of administrators. In this way, the group can dramatically increase the damage in the shortest possible time, while maintaining a discreet profile until the final revelation of the attack.
This benchmark helps Kraken strike a balance between maximum impact and operational discretion: enough activity to paralyze the company, but not so much as to cause crashes or abnormal load spikes that would immediately alert detection systems. By dynamically adapting encryption parameters to each machine, operators also gain predictability over the duration of the attack, and can better coordinate their actions with the other phases of the intrusion (exfiltration, service shutdown, lateral propagation).
Neutralize recovery mechanisms
Before triggering the actual encryption, Kraken meticulously prepares the ground by deleting shadow copies, emptying the recycle garbage can via the Windows SHEmptyRecycleBinA function, and disabling backup services. These preventive actions are designed to eliminate any possibility of data recovery without ransom payment.
Multi-platform technical architecture
Kraken is distinguished by its cross-platform architecture, with separate encryption engines optimized for Windows, Linux and VMware ESXi, enabling it to target all modern enterprise environments, from traditional servers to virtualized infrastructures.
Kraken Windows Encryptor
The Windows version is a 32-bit executable written in C++, probably protected by a Golang-based packer. To guarantee its effectiveness on 64-bit systems, the ransomware disables WoW64 file system redirection via the Wow64EnableWow64FsRedirection function with the False argument. This manipulation allows the 32-bit binary to directly access the C:WindowsSystem32 folder instead of being redirected to SysWoW64, an essential step for disabling backup services and encrypting system files on 64-bit machines. The ransomware then elevates its privileges by modifying its process token to obtain SeDebugPrivilege, giving it access to files locked by other processes.
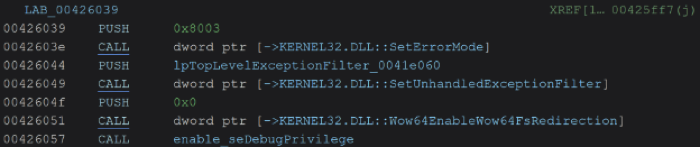
The Windows Encryptor integrates four highly specialized parallel encryption modules:
- SQL Database Module: targets Microsoft SQL servers by consulting the Windows registry to identify MSSQLSERVER and SQLEXPRESS instances, then retrieves database file paths via the SQLDataRoot value before encrypting them.
- Network Share module: scans network shares accessible via Windows WNet APIs, targeting RESOURCETYPE_DISK and RESOURCETYPE_ANY resources, while systematically ignoring ADMIN$ and IPC$ system shares.
- Local Drive module: lists all available drives via GetLogicalDrives, then filters removable, fixed and remote volumes with GetDriveTypeW, excluding CD-ROMs.
- Hyper-V module: discovers Hyper-V virtual machines via PowerShell commands, retrieves their virtual hard disk paths, forces shutdown of running VMs, then encrypts VHD/VHDX files.
The ransomware deploys several sophisticated anti-analysis techniques: obfuscation of control flow via multiple conditional loops, suppression of Windows error dialogs (SetErrorMode 0x8003), and sleep-based execution delays to evade sandboxes. The malware also deletes restore points (vssadmin delete shadows) and empties the recycle garbage can via the SHEmptyRecycleBinA API.
The Linux/ESXi encryptor
The Linux/ESXi version is a 64-bit ELF executable developed in C++ and compiled with crosstool-NG version 1.26.0. It incorporates a platform detection module capable of identifying ESXi systems (via esxcli system version get) and Synology NAS (via cat /etc/defaults/VERSION).
On ESXi environments, the ransomware inventories and forcibly shuts down active virtual machines to unlock their disk files prior to encryption. The Linux variant implements the same benchmarking mechanism as the Windows version and performs multi-threaded encryption in either solid or step mode, depending on the attacker’s parameters.
The ELF variant can be run in daemon mode via the fork_as_daemon() function, operating unobtrusively in the background. After encryption, an automatic cleanup process kicks in: the ransomware generates a bash script(bye_bye.sh) that deletes log files, the shell history, the ransomware binary and the script itself, ensuring complete self-deletion of the malware and minimizing forensic traces.
Common features
Encrypted files are given the .zpsc extension, and a ransom note entitled readme_you_ws_hacked.txt is deposited in affected directories. The ransomware uses a combination of RSA-4096 for asymmetric key encryption and ChaCha20 for symmetric file encryption, offering robust cryptographic protection. To enable victims to communicate with attackers and negotiate payment, Kraken intentionally excludes executable files (.exe) and libraries (.dll), as well as Program Files, Program Files (x86) and ProgramData folders from the encryption process.
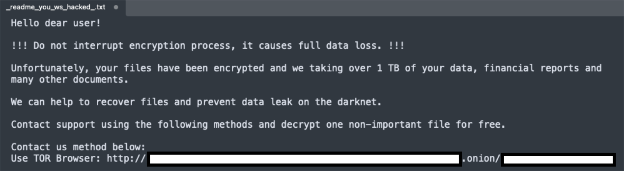
The Last Haven Board: ambitions beyond ransomware
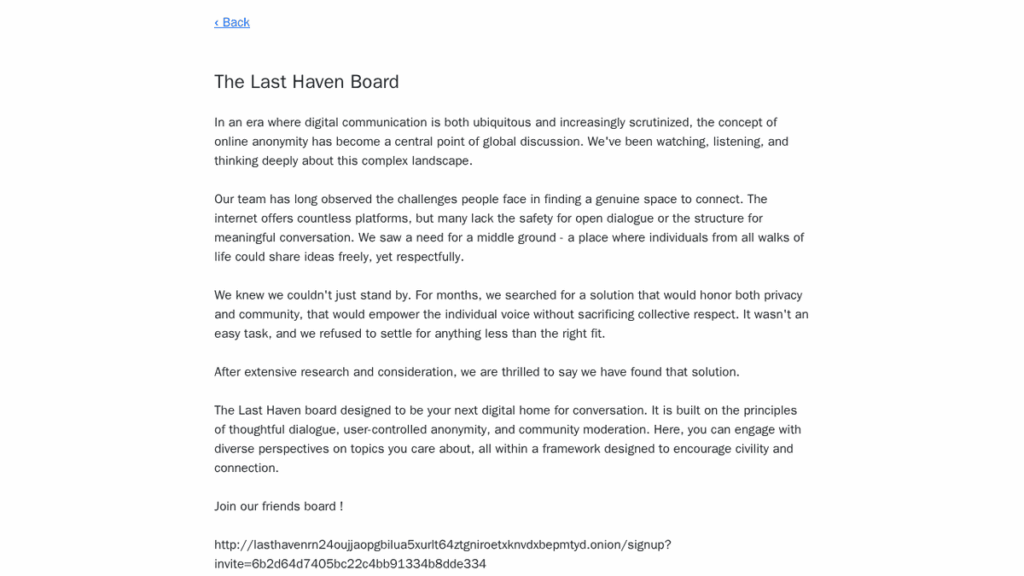
In September 2025, Kraken took things a step further by unveiling “The Last Haven Board”, an underground discussion platform presented as a secure communication space for players in the cybercriminal underground. This initiative testifies to ambitions that go beyond simple ransomware operations: Kraken is seeking to build a structured ecosystem capable of supporting and federating other malicious actors.
The announcement of official support from HelloKitty operators and WeaCorp, a collective specialized in exploit trading, lends further credence to the hypothesis of direct continuity between the two organizations. Kraken thus seems intent on transforming its HelloKitty legacy into a veritable service platform for the cybercriminal ecosystem.
Victim profile
The Kraken group employs the double extortion technique now standard in the ransomware ecosystem: after exfiltrating sensitive data, the attackers encrypt the victim’s environment and threaten to publish the stolen information on their leak website if the ransom is not paid. In one case documented by Cisco Talos, the ransom demand amounted to around $1 million in Bitcoin, with a promise to decrypt the environment and guarantee non-disclosure of the data after successful payment.
The group appears to be adopting an opportunistic approach with no concentration on specific business sectors. The victims referenced on Kraken’s leak site come mainly from the USA, which accounts for the majority of cases, followed by Canada, the UK, Denmark, Panama and Kuwait. Ransomware.live data also shows victims in Spain, Poland and Italy, with a predominance of the technology, business services and telecommunications sectors.
It’s worth noting that when Kraken first emerged in February 2025, the group claimed attacks against Cisco and CD Projekt Red on its leaked site. Cisco clarified, however, that this data originated from a 2022 compromise and was simply republished, suggesting that the group was seeking to establish credibility by appropriating old HelloKitty exploits.
Protection recommendations
In the face of Kraken’s sophistication, organizations need to adopt a multi-layered defensive approach that addresses each stage of the documented attack chain.
1. Reduce the exposed attack surface
The first priority is to reduce the exposed attack surface. As Kraken’s initial access is systematically via the exploitation of SMB vulnerabilities on servers exposed to the Internet, it is imperative to eliminate any direct exposure of this protocol on the external perimeter. RDP services must also be strictly limited to authenticated and authorized connections, ideally protected by a VPN gateway or Zero Trust access solution. Rigorous application of security patches on all systems, particularly those exposed, is a fundamental prerequisite.
2. Protect privileged identities and accesses
Protecting identities and access is the second critical area. As theft of privileged credentials is a central element of the Kraken methodology, the deployment of multi-factor authentication on all administrative interfaces is essential. A robust password policy combined with active monitoring of abnormal RDP activity and unexpected connections will detect re-entry attempts via compromised credentials. Strict network segmentation will also limit the possibility of lateral movement in the event of initial compromise.
3. Detect hijacked persistence tools
Detecting the persistence tools used by Kraken deserves special attention. Security teams should actively monitor for unexpected Cloudflared and SSHFS connections in their environment, as these legitimate tools are hijacked by attackers to maintain access and exfiltrate data. The creation of temporary files followed by encryption operations and then rapid deletion can also signal benchmarking in progress, potentially offering a window of detection before actual encryption is deployed.
4. Ensuring backup resilience
Finally, backup resilience remains the last bastion against ransomware attacks. Backup systems must be isolated from the production network to withstand the systematic deletion of shadow copies and the deactivation of backup services that Kraken performs prior to encryption. Regular restoration tests will guarantee the effectiveness of this ultimate line of defense.
To accompany the implementation of these defensive measures, Cisco Talos has published detailed indicators of compromise associated with Kraken, including detection signatures for leading security solutions. These technical elements are available in their complete study.
Conclusion
Kraken illustrates a worrying trend in the ransomware ecosystem: the resilience of criminal groups who, despite source code leaks and takedown operations, manage to reinvent themselves in new, often more sophisticated forms. The direct filiation with HelloKitty demonstrates that established ransomware brands don’t really disappear, but evolve, capitalizing on accumulated expertise and connections forged in the cybercriminal underground.
Kraken’s adaptive benchmarking capability represents a significant evolution in ransomware sophistication. By dynamically calibrating the encryption process to the capabilities of each system, the group maximizes impact while minimizing the risk of early detection. This “intelligent” approach could inspire other malicious actors and become widespread in the months to come.
The creation of the Last Haven Board forum, with the open support of HelloKitty and WeaCorp, bears witness to a desire to structure a sustainable criminal ecosystem. Kraken is no longer content to be a simple ransomware operation, but aspires to become a service platform for the cybercriminal community, a model reminiscent of the evolution of other major groups such as LockBit or ALPHV/BlackCat towards Ransomware-as-a-Service structures.
For organizations, the message is clear: traditional defenses are no longer sufficient in the face of adversaries who combine exploitation of known vulnerabilities, hijacking of legitimate tools and algorithmic optimization of their attacks. A proactive defensive posture, combining the securing of exposed services, identity protection, behavioral detection and truly isolated backups, is now the minimum required to deal with this new generation of threats.
Are you a victim of ransomware? Contact our 24/7 support team. We provide an exclusive technical response to ransomware incidents, to help you recover your data and get back to business quickly.
Sources :
- Cisco Talos: Unleashing the Kraken ransomware group
- BleepingComputer: Kraken ransomware benchmarks systems for optimal encryption choice
- BleepingComputer: HelloKitty ransomware behind CD Projekt Red cyberattack, data theft
- Infosecurity Magazine: Kraken Uses Benchmarking to Enhance Ransomware Attacks
- CYJAX: Kraken onto the extortion scene
- Ransomware.live: Kraken
