The cybercriminal landscape of 2025 is undergoing a major evolution with the striking emergence of Safepay.
Safepay is a ransomware group that has established itself as one of the most notable threats of 2025, even taking the lead in the number of attacks in May 2025.
In just a few months, this criminal organization has managed to climb to the top of the global rankings, dethroning historical players such as Qilin and LockBit.
Table des matières
ToggleSafepay’s meteoric rise
First identified in November 2024, Safepay quickly established its dominance in the ransomware ecosystem. According to the latest data from Ransomfeed, the group took the top spot in the ransomware rankings in May 2025, claiming no fewer than 72 victims in that month alone.
This progression is all the more remarkable given that Safepay claims not to operate on the traditional Ransomware-as-a-Service (RaaS) model. Unlike other groups that delegate their operations to affiliates, Safepay maintains a centralized, in-house structure, enabling it to adopt consistent tactics, techniques and procedures (TTPs) and more precise targeting.
A formidable operational model
Double extortion at the heart of SafePay’s strategy
Safepay employs a particularly effective double extortion strategy…
Indeed, the group not only encrypts its victims’ data, but also exfiltrates sensitive information prior to encryption. This approach puts maximum pressure on victims, who risk not only the loss of their data, but also its public disclosure.
Cyble ‘s analysis reports that Safepay has already claimed 198 victims since its appearance in autumn 2024, peaking at 43 victims in March 2025 before reaching its record of 58 victims in May, according to its own data, which differs slightly from Ransomfeed’s.
Aggressive intimidation tactics
Safepay stands out in particular for the aggressiveness of its negotiation methods. According to DCSO‘s research, the group does not hesitate to contact its victims directly by telephone to increase psychological pressure.
This direct approach is accompanied by the operation of a .onion “site of shame”, where the stolen data of victims who refuse to pay is published.

SafePay’s specific geographic targeting
Germany, particularly targeted
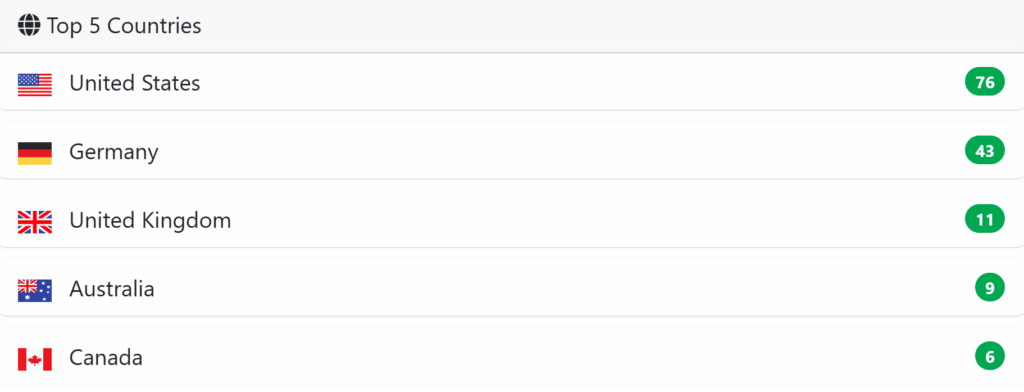
One of the most striking features of Safepay is its geographic targeting. In contrast to the usual ransomware trends, which focus mainly on the USA, Safepay shows a marked preference forGermany, which accounts for almost 18% of its victims – a percentage well above the average for other ransomware groups.
This concentration on the German market suggests a deliberate strategy, possibly linked to the country’s economic prosperity and the value of German companies’ data. The United States nevertheless remains a preferred target, confirming the group’s bilateral approach.
Preferred sectors
Safepay demonstrates a remarkable ability to adapt by targeting a wide range of industries, with a notable preference for :
- Manufacturing (22)
- Professional services (19)
- Education (17)
- Tech companies (14)
- Medical (13)
Conversely, the group seems to avoid certain sectors such as finance, IT and public administration, suggesting a considered targeting strategy based on risk analysis and potential returns.

Technical analysis of the Safepay ransomware
Architecture and operation
NCC Group ‘s experts have carried out an in-depth analysis of the Safepay ransomware, based on a real attack and revealing the complexity and speed of the attack:
Attack chronology
The incident took place over a period of 2 days, demonstrating the attackers’ speed of execution:
- T+0: Initial access via a poorly configured firewall
- T+7 hours: Deployment of malicious batch files and network reconnaissance
- T+1 day: Compromised credentials and file access
- T+2 days: Deployment of ransomware
Initial attack vector
The critical flaw
The attack was made possible by a misconfiguration of the Fortigate firewall, allowing local and LDAP accounts to authenticate over the VPN bypassing multi-factor authentication (MFA). This misconfiguration, combined with weak passwords, opened the door to attackers.
Escalation of privileges
The attackers quickly escalated their privileges by compromising a domain administrator account, using a device named “vultr-guest” – a known indicator of Vultr VPS infrastructures used by cybercriminals.
The ransomware’s technical arsenal
Sophisticated encryption
SafePay uses the ChaCha20 algorithm with an x25519 key exchange mechanism:
- Each file is encrypted with a unique key
- Partial encryption: only 10% of data blocks (parameter -enc=1)
- 65 bytes of unencrypted metadata added at the end of each file
Persistence tools
- ScreenConnect: Hijacked legitimate remote access tool
- QDoor: Sophisticated backdoor with C2 communication to 88.119.167[.]239
- Anti-recovery techniques: Delete VSS snapshots, disable Windows automatic repair
Targeted extensions
The ransomware only encrypts files with specific extensions (over 60 types), including executables, libraries, documents and multimedia files.
Evasion techniques
Language verification
The ransomware performs a system language check and terminates immediately if it detects :
- Russian, Ukrainian, Belarusian
- Azeri (Cyrillic), Armenian, Georgian, Kazakh
Obfuscation
- UPX packaging modified to hide content
- Process injection via process hollowing technique
- Unencrypted C2 communication with specific header: C4 C3 C2 C1
Impact and consequences
The SafePay attack caused :
- Encryption of hypervisors, rendering virtual machines unusable
- Modification of all administrator passwords
- Deployment of ransom notes (readme_safepay.txt) on numerous hosts
- .safepay extension added to encrypted files
Security lessons
This analysis reveals several crucial points for organizational security:
- Rigorous configuration: a simple configuration error can compromise the entire infrastructure
- Strong passwords: weak passwords remain a major attack vector
- Universal MFA: multi-factor authentication must cover all accounts, without exception
- Network monitoring: early detection of suspicious activity is essential
- Secure backup: VSS snapshots are not enough in the face of modern ransomware
The SafePay case demonstrates that even emerging ransomware groups can cause considerable damage by exploiting basic vulnerabilities. The technical sophistication of the malware contrasts with the simplicity of the initial attack vector, underlining the importance of a holistic security approach.
Technical comparisons
Comparative analysis conducted by DCSO reveals architectural similarities with LockBit3 (LockBit Black), including:
- Use of Overlapped I/O
- Similar state machine for encryption
- comparable import resolution structure
However, researchers believe that Safepay was developed independently, probably inspired by existing ransomwares rather than derived directly from their source code.
Outlook for the future
Observed trends
Safepay’s rapid evolution suggests several worrying trends:
- Increasing professionalization: the group has demonstrated a remarkable capacity for adaptation and innovation.
- Specialized geographic focus: the company’s emphasis on Germany could inspire other groups.
- Abandonment of the RaaS model: the centralized structure could become an alternative model
Future challenges
Experts anticipate several challenges:
- Technical evolution: potential development of hypervisor encryption capabilities
- Geographic expansion: possible extension of targeting to other European countries
- Sophistication of attacks: continuous improvement of intrusion and persistence techniques.
Conclusion
Safepay represents a significant evolution in the ransomware landscape of 2025. Its meteoric rise, aggressive methods and specific geographic targeting make it a major threat to businesses, particularly in Germany and the USA.
The group’s technical sophistication, combined with its centralized structure and direct intimidation tactics, is setting new standards in the cybercriminal ecosystem. To counter this emerging threat, it is imperative that organizations strengthen their defenses, adopt a proactive security approach and maintain a constant watch on the evolutions of this particularly dangerous group.
The emergence of Safepay confirms the need for greater international collaboration in the fight against ransomware, and underlines the importance of sustained investment in cybersecurity to counter this new generation of threats.
The main sources of the article :
