The IT threat landscape has just welcomed a particularly worrisome new player. SuperBlack, a sophisticated ransomware that appeared in early 2025, is rapidly establishing itself as one of the most worrying threats to businesses and organizations worldwide. Behind this new strain of malware lies a complex story combining advanced vulnerability exploitation and potential links with notorious criminal groups.
Table des matières
ToggleA striking appearance on the cyberthreat landscape
The first signs of malicious activity attributed to SuperBlack were detected at the end of January 2025, marking the entry of a new player into the already saturated ransomware ecosystem. The Forescout Research team was among the first to identify a series of intrusions exploiting critical vulnerabilities in Fortinet firewalls(CVE flaws), culminating in the deployment of this new ransomware.
What makes SuperBlack particularly dangerous is the exceptional speed with which its operators exploit newly discovered vulnerabilities. According to the researchers, a proof-of-concept (PoC) was released on January 27, 2025, and attackers began exploiting it within the following 96 hours, leaving only a very small window for organizations to apply patches… This responsiveness demonstrates advanced technical expertise and a willingness to act quickly before organizations have time to react.
“The attacks began with the compromise of Fortigate firewall appliances and eventually led to the deployment of a new strain of ransomware that we have dubbed SuperBlack,” explain Forescout researchers in their detailed threat report.
The modus operandi: technical analysis of Fortinet vulnerability exploitation
SuperBlack is characterized by a highly structured modus operandi that begins with the exploitation of two critical vulnerabilities in Fortinet products. A detailed analysis of these exploits reveals a disturbing level of sophistication.
In-depth analysis of the exploited vulnerabilities
The two critical vulnerabilities at the heart of the SuperBlack attacks are :
- CVE-2024-55591:an authentication bypass flaw in the administration interface of FortiOS devices, enabling an attacker to obtain super_admin privileges via specially crafted WebSocket requests, paving the way for full device compromise.
- CVE-2025-24472: an elevation-of-privilege vulnerability which, when chained with the first, allows “super_admin” privileges to be obtained on FortiOS devices (versions prior to 7.0.16).
These vulnerabilities allow attackers to take complete control of exposed Fortinet firewalls, which are often a strategic entry point to corporate networks.
The exploitation method is particularly sophisticated, and takes place in several distinct phases:
Phase 1: reconnaissance and target identification
SuperBlack operators conduct massive scanning campaigns to identify vulnerable Fortinet devices exposed on the Internet. Researchers have observed automated attempts using randomly generated user names (five characters), suggesting the use of automated tools for target discovery.
- Massive scanning of the Internet for vulnerable Fortinet devices
- Use of automated tools to identify vulnerable firmware versions
- Mapping of target network to prepare lateral moves
Phase 2: Initial exploitation and establishment of persistence
Once a vulnerable target has been identified, the attacker exploits flaws CVE-2024-55591 or CVE-2025-24472 to :
- create local administrator accounts with names such as“forticloud-tech“,“fortigate-firewall” or“adnimistrator” (deliberate misspelling)
- In some cases, set up account chaining, with each account created generating other accounts, which slows down remediation by complicating their identification and revocation.
- In some cases, account chaining was implemented, with each account created generating other accounts, which slowed down remediation by complicating their identification and revocation.
- Download firewall configuration, including policies, routes, keys and VPN configurations.
- Automate resynchronization of the “forticloud-sync” account, assigning it the “super_admin” role and a known password every day, to guarantee its recreation via “system.automation-action” in the event of deletion.
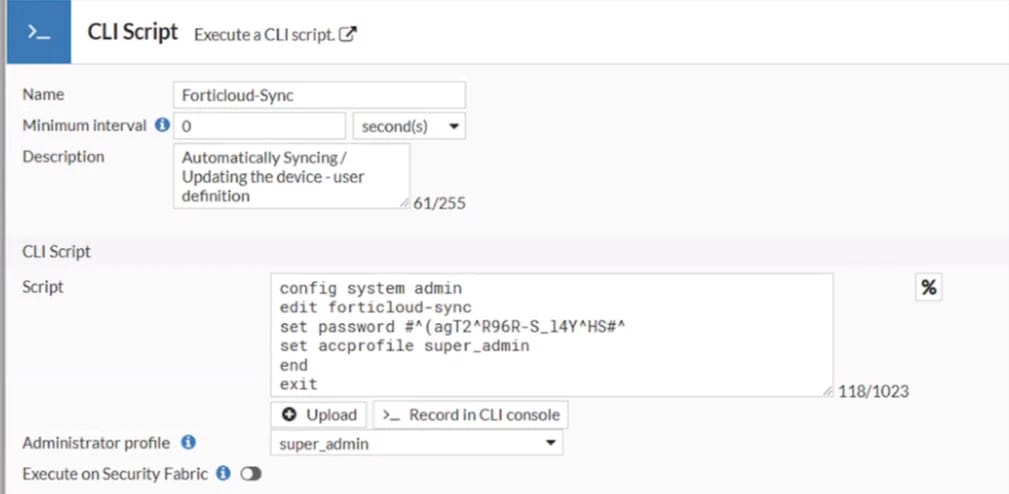
In addition to automating persistence via recreated administrator accounts, the attacker configured local VPN accounts whose names mimicked those of existing users, suffixed with a number. Added to the VPN group, these accounts enabled access to be maintained discreetly.
Phase 3: Internal recognition and elevation of privileges
Once the first accesses had been obtained by exploiting Fortinet vulnerabilities, the attackers turned their efforts to exploring the internal network and increasing their privileges.
- Use firewall administration interfaces to map the target network environment, identifying critical assets such as domain controllers and critical servers.
- Add accounts to existing groups, facilitating access to more systems and more sensitive data.
- Exploit insecure configurations or implementation errors to elevate privileges to the domain level.
This phase demonstrates a keen understanding of corporate network environments and an ability to exploit organizational as well as technical vulnerabilities.
Phase 4: Lateral movement and deployment of ransomware
In the final phase, SuperBlack operators extend their control across the network before performing the final encryption.
- Using legitimate protocols such as WMI (Windows Management Instrumentation) and SSH to move laterally without triggering alerts.
- Disabling or bypassing security tools such as anti-virus, EDR solutions and backup processes, to ensure effective encryption.
- Exfiltration of sensitive data to external servers, before launching the ransomware, thus preparing a double extortion – threatening to disclose the data if the ransom is not paid.
- Targeted, orchestrateddeployment of the SuperBlack ransomware, often via Windows scheduled tasks, enabling rapid, synchronized distribution on critical systems.
What sets SuperBlack apart is its targeted deployment strategy – instead of encrypting the entire network, attackers often prioritize file servers containing sensitive data, thereby increasing impact while minimizing the risk of detection.
SuperBlack and LockBit: a proven technical connection
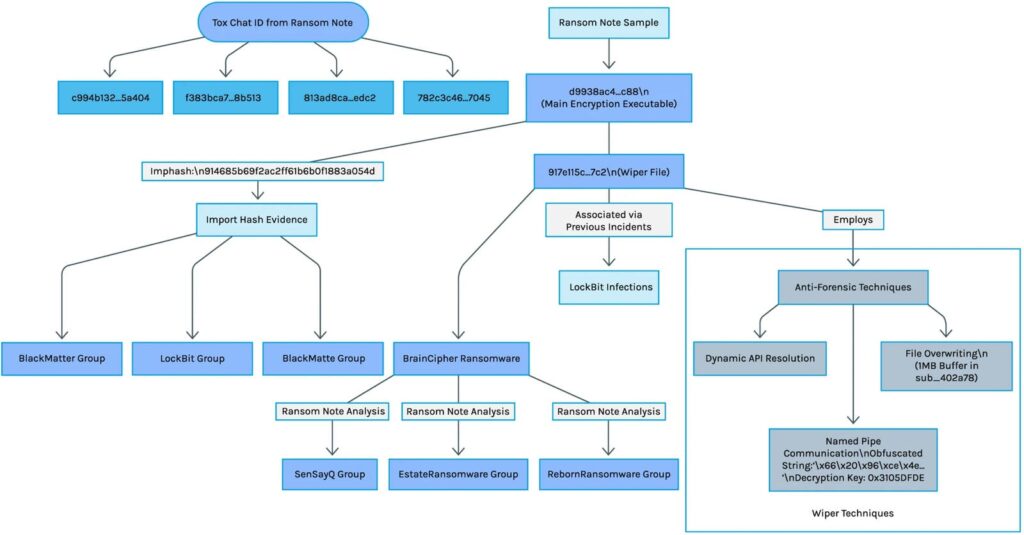
Analysis of SuperBlack’s source code reveals undeniable technical links with the infamous LockBit 3.0 ransomware, whose main operations were disrupted by law enforcement in February 2024. This connection goes far beyond mere superficial similarities.
Forescout Research has identified several converging pieces of evidence for this connection:
- Source code based on the leaked LockBit 3.0 builder: SuperBlack uses a payload structure and encryption methods identical to LockBit, but with all brand elements removed
- Ransom note structure: maintains LockBit’s HTML structure, although brand elements have been removed
- Shared Tox ID: the SuperBlack ransom note includes a TOX chat ID directly linked to LockBit operations, suggesting that the operator is either a former LockBit affiliate or a member of the central team managing the negotiations
- Common operational methods: persistence techniques and deletion of LockBit-identical Windows shadow copies
- Overlapping IP addresses: the infrastructures used show significant overlap with previous LockBit operations
- Common wiper module: WipeBlack, SuperBlack’s wiping component, has also been used by BrainCipher, EstateRansomware and SenSayQ, all linked to the LockBit ecosystem.
This technical filiation suggests that SuperBlack is a variant developed from the LockBit 3.0 builder, leaked in September 2022. Although SuperBlack appears to operate independently, this reuse of LockBit code immediately confers a high level of sophistication on the attackers, explaining their ability to exploit newly discovered Fortinet vulnerabilities so quickly.
The LockBit 3.0 builder and its criminal legacy
In September 2022, a disgruntled developer working for LockBit leaked the “LockBit 3.0 builder” (nicknamed “Black”), a tool for creating customized instances of the ransomware. This leak made sophisticated, proven code available to many malicious actors, explaining the emergence of variants such as SuperBlack.
The LockBit 3.0 builder includes several technical components:
- A graphical configurator for customizing ransomware parameters (targets, exclusions, encryption methods)
- An integrated RSA cryptographic key pair generator
- A compiler for creating customized executables
- Obfuscation tools to bypass security defenses.
“On September 21, 2022, the LockBit 3.0 ransomware builder dubbed ‘Black’ was leaked online by a developer working for the LockBit group. The leak was the result of a dispute between the developer and LockBit management”, states RH-ISAC in its technical analysis.
This leak has had a major impact on the ransomware ecosystem, enabling new criminal groups to rapidly deploy sophisticated variants without developing their own encryption code. SuperBlack perfectly illustrates this trend, demonstrating how leaked criminal tools continue to fuel new threats years after their initial disclosure.
Technical sources :
- RH-ISAC – LockBit 3.0 Builder Code Leak Technical Analysis
- Security Affairs – LockBit 3.0 leaked code usage analysis
- Kaspersky SecureList – LockBit Ransomware Builder Analysis
Indicators of compromise (IOCs) and technical signatures
Forensic analysis of the SuperBlack attacks carried out by Forescout has identified several characteristic indicators of compromise (IOCs), essential for detection and prevention.
Signatures on compromised Fortinet devices
Suspicious administrator accounts:
- Presence of previously described malicious accounts with their automated persistence mechanisms
- Detection of suspicious automation rules maintaining fraudulent access
- Identification of compromised VPN accounts integrated into existing groups
Configuration changes :
- Unauthorized downloading of firewall configuration (policies, routes, VPN keys)
- Automation rules added via
system.automation-actionto maintain persistence - Modifications to existing VPN groups
Ransomware signatures
Malicious files identified :
- Hash SHA-256:
d9938ac4346d03a07f8ce8b57436e75ba5e936372b9bfd0386f18f6d56902c88(main executable) - WipeBlack” wiper module with hash import:
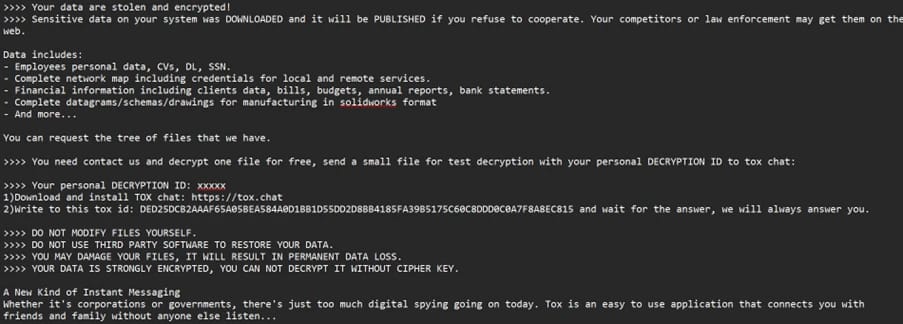
914685b69f2ac2ff61b6b0f1883a054d - Ransom note retaining LockBit HTML structure with Tox ID:
DED25DCB2AAAF65A05BEA584A0D1BB1D55DD2D8BB4185FA39B5175C60C8DDD0C0A7F8A8EC815
Operating techniques observed
Initial phase:
- Exploitation of CVE-2024-55591 and CVE-2025-24472 on FortiOS devices
- Authentication attempts with random user names (5 characters)
- Automated scanning to identify vulnerable devices
Persistence and lateral movement:
- Exploitation of legitimate protocols previously detailed for discrete movements
- Systematic disabling of security tools and backup solutions
- Orchestration of data exfiltration prior to encryption deployment
“The attacks start with the compromise of FortiGate firewall appliances and ultimately lead to the deployment of SuperBlack,“ states the Forescout report. The organization provides a comprehensive list of indicators of compromise (IoC) at the end of the report to enable security teams to detect these threats.
Important note: Forescout provides an exhaustive list of technical IOCs in its original report for incident response teams.
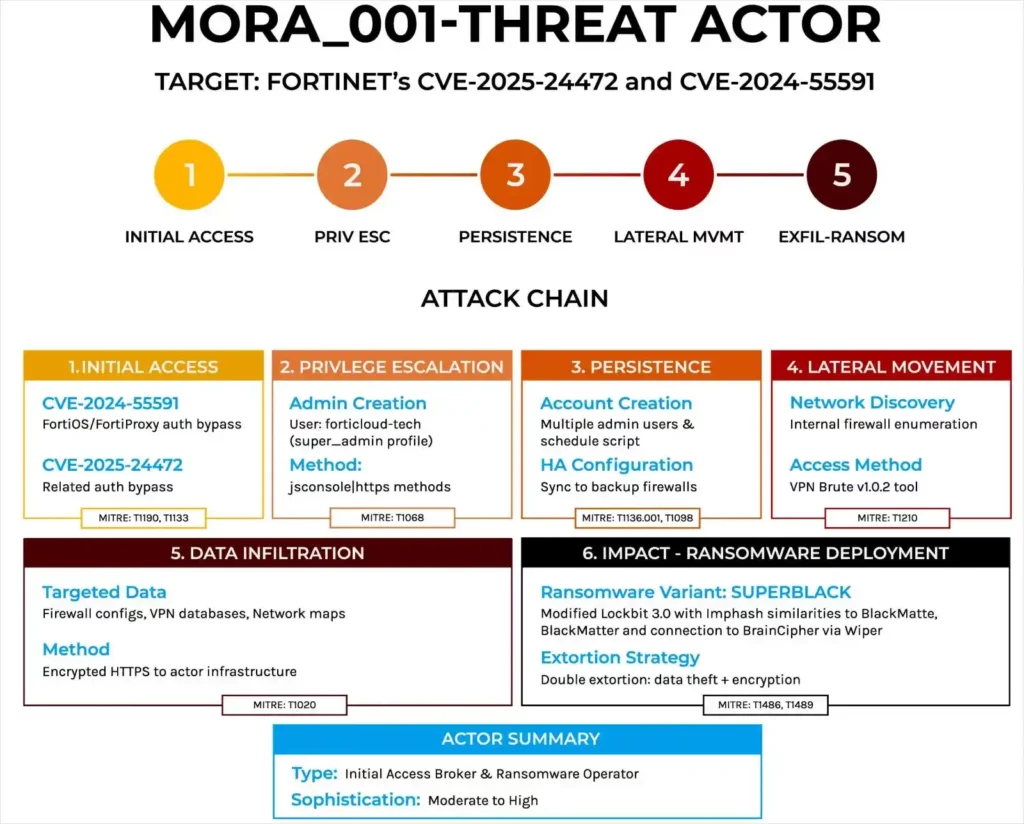
The Mora_001 group: between novelty and LockBit heritage
Forescout Research tracks this new player under the name “Mora_001”, following their naming convention based on the mythology of different regions. In this case, they use Slavic mythology, as the actor uses artifacts in the Russian language. Forescout Research
Analysis reveals that Mora_001 has a distinct operational signature that blends elements of opportunistic attacks with proven links to the LockBit ecosystem. This relationship with LockBit’s wider operations underlines the growing complexity of the modern ransomware landscape, where specialized teams collaborate to exploit complementary capabilities.
Forescout researchers identify three key factors that distinguish Mora_001 as an independent player while acknowledging its links to established operations:
Consistent post-exploitation patterns observed in all incidents studied, including the creation of identical usernames across multiple victim networks, overlapping IP addresses used for initial access and command-and-control operations, and rapid ransomware deployment within 48 hours when conditions are favorable.
Ransomware customization: the actor exploited the leaked LockBit builder, modifying the structure of the ransom note by removing the LockBit branding, while employing its own exfiltration tool.
Relationship to LockBit: the ransom note includes the same TOX ID used by LockBit ,suggesting that Mora_001 is either a current affiliate with unique operational methods, or an associated group sharing communication channels.
This consistent operational signature allows researchers to confidently attribute future intrusions to this entity, regardless of its exact relationship with LockBit.
Global impact and targeted victims
Forescout’s analysis reveals that the most exposed FortiGate devices are in the USA (7,677 devices), India (5,536 ) and Brazil (3,201), representing the priority targets for Mora_001. Confirming the methodical approach already observed, the group favors a systematic double extortion where exfiltration systematically precedes encryption, aligning itself with recent trends among ransomware operators who favor data theft over pure disruption.
The infrastructure used by Mora_001 also reveals the use of a sophisticated tool dubbed “VPN Brute v1.0.2” discovered on IP address 185.147.124[.]34. This tool, containing Russian-language content, is designed to brute force several perimeter devices, including RDWeb, PulseSecure, OWA, GlobalProtect, Fortinet, Cisco, BIG-IP and Citrix.
More recent versions (v1.1.0) introduce advanced features such as the ability to “continue searching after successful discovery” and “scan honeypots” to avoid detection. Researchers identified 15 additional IP addresses running these versions of VPN Brute, testifying to the scale of the infrastructure deployed.
The worrying future of ransomware in 2025
The emergence of SuperBlack perfectly illustrates the growing professionalization of the criminal ecosystem. The intrusions studied by Forescout highlight the growing trend of exploiting perimeter security appliances for initial access, with a rapid transition between vulnerability disclosure and active exploitation that considerably reduces the window for applying critical patches.
To counter these threats, Forescout recommends a defense-in-depth approach comprising :
- Immediate application of patches for CVE-2024-55591 and CVE-2025-24472
- Restricting externalmanagement access to firewalls
- Regular auditing of administrator accounts and removal of unauthorized users
- Review of automation parameters to detect unauthorized tasks
- Enable full logging, including CLI audit logs, HTTP/S traffic and NPS audit.
The report highlights a critical flaw in many investigations: the absence of full logging. This gap significantly hampers detection, investigation and proactive threat hunting.
The SuperBlack story demonstrates that, despite law enforcement’s efforts to dismantle large groups like LockBit, new players are rapidly emerging, often more agile and difficult to track down. In a landscape where the time between the discovery of a flaw and active exploitation is counted in hours rather than days, every unpatched vulnerability represents an open door for increasingly sophisticated attackers.
The resilience of the criminal ecosystem, illustrated by the transformation of LockBit into variants like SuperBlack, is a reminder that vigilance and preparation are no longer optional but essential to the digital survival of organizations.
Source:
