The Gentlemen, the new ransomware that appeared in the summer of 2025, didn’t wait long to make its presence felt, attracting all the attention of the 2025 autumn season with its sustained activity.
In a very short space of time, this criminal organization has already claimed more than 30 victims across 17 countries, shattering industry codes with its adaptability and operational professionalism.
The group stands out for its methodical approach and remarkable technical sophistication, attacking organizations’ defenses with customized tools and advanced evasion techniques.
Trend Micro was the first to provide a detailed study of The Gentlemen ransomware, back on September 9, 2025.
Table des matières
ToggleA new ransomware group with global ambitions
The Gentlemen first appeared on the cybercriminal landscape in the third quarter of 2025, but investigative evidence suggests that operations began earlier in the year.
Their first known victim is JN Aceros, a Peruvian steel company that was compromised as early as June 30, 2025.
Unlike opportunistic ransomware groups, The Gentlemen is characterized by a highly methodical approach.
As you’d expect, their name echoes the Guy Ritchie film, and they’ve adopted a polished brand identity with a professional logo and motto on their darknet leak site.

This attention to image reflectsa disciplined, detail-oriented organization.
The lack of previous history combined with a high number of victims in such a short space of time suggests either a rebranding of experienced ransomware operators, or a new, well-funded criminal team born out of the post-Conti landscape.
Attack techniques: innovation at the service of cybercrime
Exploiting legitimate, vulnerable drivers (BYOVD)
One of The Gentlemen’s most worrying innovations lies in their exploitation of the ThrottleStop.sys driver (renamed ThrottleBlood.sys).
This legitimate, signed driver, normally used to control the performance of laptop processors, contains the CVE-2025-7771 vulnerability which allows attackers to gain kernel-level privileges.
This BYOVD (Bring Your Own Vulnerable Driver) technique enables them to terminate security software processes that would normally be protected against deletion.
The All.exe tool, and its improved version Allpatch2.exe, exploit this vulnerability to neutralize antivirus and EDR solutions at kernel level.
Manipulating Group Policy Options (GPOs)
The Gentlemen once again demonstrate their impressive mastery of Active Directory environments by manipulating Group Policy Objects (GPOs) to deploy their ransomware on a domain-wide scale.
This technique enables them to distribute their malicious payload via NETLOGON sharing, guaranteeing simultaneous infection of all machines attached to the domain.
In-depth recognition and adaptation
What also sets The Gentlemen apart is their ability to adapt during the course of a campaign. After identifying the limitations of their initial tools, they carry out detailed reconnaissance of the protections in place and develop customized variants of their evasion tools. This approach reflects a shift from opportunistic attacks to highly targeted campaigns.
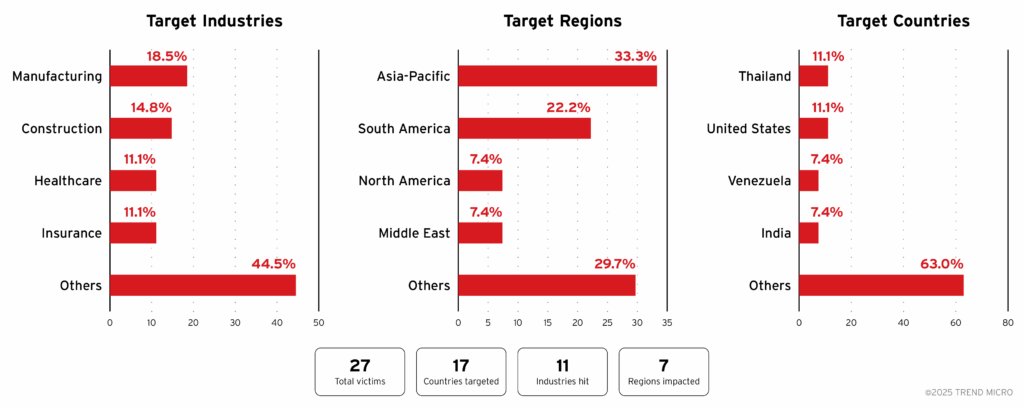
Victimology: worrying multi-sector targeting
Sectors most affected
The Gentlemen mainly targets four critical sectors:
- Manufacturing and industry: with victims including Proplastics Ltd (Zimbabwe), Grupo Halcón (Spain), and Kuwait Portland Cement Co.
- Healthcare: including Shifa Hospital (Oman) and Santa Rita Clinical Laboratory (Costa Rica)
- Construction: including Location Peintures Prestations (France)
- Financial services: such as Oriental de Seguros (Panama) and Venezuela Re
Geographical breakdown
Thailand and the United States are the most affected countries, followed by India, Mexico and Colombia. This geographical distribution suggests an opportunistic approach based on access opportunities rather than an explicit geopolitical strategy.
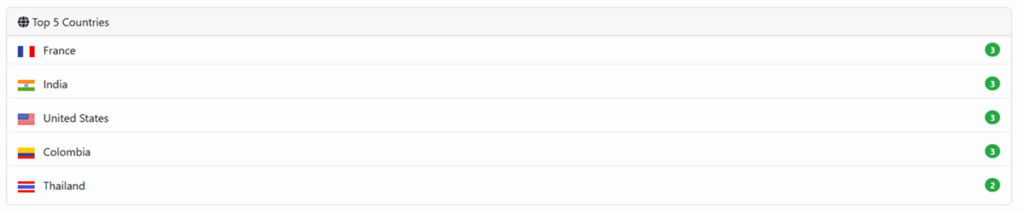
Including new victims from France and India
In September 2025, three new victims were added to the group’s list, including two French companies:
- Location Peintures Prestations (LPP): a French company founded in 1991, initially specializing in anti-corrosion paint and now a key supplier of safety and formwork equipment to major French construction groups.
- Saelen/Heizomat: expert supplier of green space maintenance machinery and renewable energy solutions via its Heizomat France division, focused on the biomass energy sector.
- Surtel Technologies Pvt: Indian IT services company operating worldwide, offering management consulting and outsourcing solutions.
Technical analysis of the ransomware
Characteristics of the malware
The Gentlemen ransomware has several distinctive technical features:
- Encrypted file extension: .7mtzhh
- Ransom note: README-GENTLEMEN.txt containing a victim ID and contact information
- Mandatory execution parameter: an 8-byte password required for activation, serving as an anti-analysis measure
- Self-deletion: a final cleanup batch script that deletes traces after encryption
Attack preparation process
Prior to encryption, the ransomware executes a methodical preparation sequence:
Shutdown of critical services: the malware systematically terminates services related to backups, databases and security, including specific services such as Veeam, SAP, Oracle, MySQL, and various security solutions.
Removal of defenses: disabling Windows Defender via PowerShell, adding global exclusions, and deleting support files.
Impeding recovery: deleting shadow copies, emptying Windows event logs, and deleting RDP log files.
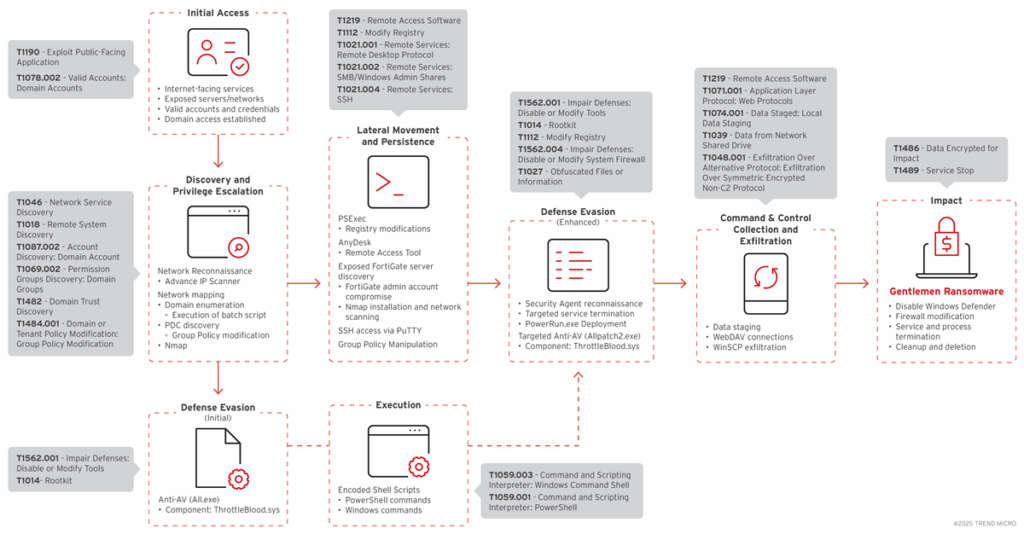
Modus operandi: from intrusion to extortion
Initial access
The Gentlemen usually gains initial access by exploiting exposed Internet services or using compromised accounts. In at least one documented case, they exploited a FortiGate server with open administrative access, using the compromised administrator account to perform internal Nmap scans.
Recognition and discovery
Once access was gained, the group immediately deployed reconnaissance tools:
- Advanced IP Scanner for initial network mapping
- Nmap for detailed service discovery
- Customized batch scripts for Active Directory account enumeration
A batch script named 1.bat enumerates over 60 domain user accounts, querying both standard administrative groups and virtualization-related groups.
Lateral movement and persistence
PsExec is the preferred tool for lateral movement, accompanied by critical registry modifications to weaken authentication:
- Modification of NTLM parameters to facilitate operation
- Enabling RDP with reduced security parameters
- Installation of AnyDesk as a persistent, encrypted C2 channel
Data exfiltration
Exfiltration takes place mainly via WinSCP, using encrypted SFTP connections to avoid detection by network monitoring solutions. Data is first organized in the C:ProgramDatadata directory before being exfiltrated.
Negotiations and business model
Contact method
The Gentlemen stand out for their OPSEC (operational security) approach to communication. They provide a public TOX ID (F8E24C7F5B12CD69C44C73F438F65E9BF560ADF35EBBDF92CF9A9B84079F8F04060FF98D098E) for encrypted negotiations, avoiding centralized chat portals that could be intercepted or shut down (source: Ransomnews).
Double extortion strategy
The group operates on a double extortion model: after encryption, victims are threatened with publication of the stolen data on their darknet leak site. This strategy considerably increases the pressure on victims, particularly those in regulated sectors.
Technical indicators and detection
Indicators of compromise (IOCs)
Organizations can monitor the following indicators:
Malicious Hashes:
- c12c4d58541cc4f75ae19b65295a52c559570054 (ransomware payload)
- c0979ec20b87084317d1bfa50405f7149c3b5c5f (All.exe – AV killer)
- df249727c12741ca176d5f1ccba3ce188a546d28 (Allpatch2.exe – enhanced AV killer)
- e00293ce0eb534874efd615ae590cf6aa3858ba4 (PowerRun.exe)
File artifacts:
- ThrottleBlood.sys (vulnerable driver exploited)
- README-GENTLEMEN.txt (ransom note)
- .7mtzhh extension on encrypted files
MITRE ATT&CK techniques
The Gentlemen exploits a wide range of techniques documented in the MITRE ATT&CK framework, including :
- T1190: Exploiting public applications (FortiGate servers)
- T1562.001: Defense tampering (disabling security tools)
- T1014: Rootkit (vulnerable driver exploitation)
- T1484.001: Domain policy modification (GPO manipulation)
- T1486: Data encryption for impact
Protective measures and recommendations
Essential access controls
To counter the exploitation by The Gentlemen of infrastructures exposed on the Internet, the adoption of Zero Trust principles is of the utmost importance:
- Elimination of direct RDP exposure on the Internet
- Application of multi-factor authentication on all administrative interfaces
- Network segmentation between IT management tools and production systems
- Virtual patching for known vulnerabilities in perimeter devices
Endpoint hardening
Protection against documented process termination techniques is also a priority:
- Enabling tampering protection with exploit protection
- Password protection of agent uninstallation
- Enabling agent self-defense protection
- Predictive machine learning in pre-execution and runtime modes
Monitoring and detection
Organizations need to implement targeted monitoring:
- Restricting access to domain controller shares and alerting on unauthorized NETLOGON modifications
- Automatic isolation of devices showing indicators of driver-based attacks
- Monitoring of shutdown commands targeting security processes
- Application control to restrict unauthorized remote access tools
Impact on the ransomware landscape
An evolution towards tailored attacks
The Gentlemen represents a significant evolution from universal methods to highly customized attacks. The ability to study and adapt to deployed security software raises the bar for incident detection, prevention and response.
Threat to critical infrastructures
The group’s impact on critical infrastructures and use of double extortion techniques underline the significant risk this threat actor poses to organizations. Their attacks on essential services such as healthcare highlight their disregard for public safety.
Global context for ransomware in 2025
This emergence takes place against a worrying backdrop: Check Point observed a 126% increase in ransomware attacks in the first quarter of 2025 compared to the previous year, with an average of 275 incidents per day affecting organizations.
Law enforcement actions and international response
To date, no arrests or seizures of public infrastructure have been reported concerning The Gentlemen. Their Tor leak site remains online, and the use of encrypted communications (TOX) makes traceability considerably more difficult.
International agencies such as Interpol and Europol are likely to be gathering intelligence, but no coordinated public action has yet been announced against this group specifically.
Conclusion: a new era of criminal sophistication
The Gentlemen epitomize the evolution of ransomware towards unprecedented technical and operational sophistication. Their methodical approach, combined with their ability to adapt in real time and their mastery of corporate environments, makes them one of the most dangerous groups observed in 2025.
This rise in power illustrates the growing trend among ransomware operators to abandon one-size-fits-all methods in favor of highly personalized attacks. For organizations, this means that traditional defenses are no longer enough: a proactive approach must now be adopted, including hunting down group-specific threats, continuously strengthening protections, and constantly refining incident response strategies.
Organizations still need to review their security posture, focusing particularly on monitoring anomalous administrative activity, preventing the exploitation of legitimate tools for lateral movement, and early detection of attempts to evade defenses. The era of basic ransomware attacks is over; we’re entering a new phase where only constant vigilance and continuous adaptation can effectively protect our organizations.
Are you a victim of ransomware? Contact our 24/7 support. We provide an exclusive technical response to ransomware incidents, to help you recover your data and get back to business quickly.
