September 5, 2025 marks the appearance of Yurei, a new ransomware group whose name evokes the spirits of Japanese folklore. This emergence illustrates a worrying reality of today’s cybercriminal landscape: the ease with which inexperienced actors can now deploy sophisticated campaigns based on open source malware. According to Check Point Research:“this highlights how open source malware dramatically lowers the barriers to entry for cybercriminals, enabling even less skilled actors to launch ransomware operations.”
The researchers’ analyses reveal a worrying reality: Yurei is only a slightly modified version of the Prince-Ransomware ransomware, freely available on GitHub. This discovery underlines a worrying trend in which cybercriminals are exploiting open source malware to considerably reduce the technical barriers to entry into the criminal economy.
Table des matières
TogglePrince-Ransomware: the open source arsenal behind Yurei ransomware
To fully understand the threat posed by Yurei, we need to introduce Prince-Ransomware, the open source project that serves as its technical foundation. Prince-Ransomware, developed by researcher SecDbg and published on GitHub, is a ransomware written entirely in Go that uses a mix of ChaCha20 and ECIES encryption to ensure robust file encryption. Although officially presented as a pedagogical tool, this project perfectly illustrates the democratization of offensive capabilities via open source.
Prince-Ransomware’s automated builder enables cybercriminals with limited skills to create and deploy ransomware using advanced encryption methods. As Halcyon’s experts analyze: “The barriers to entry for becoming an effective ransomware operator have all but disappeared, and with that, the volume of attacks is likely to increase”. This ease of customization has generated several variants, such as Black (Prince), Wenda and UwU, differing only in extensions and ransom notes. This proliferation is reminiscent of the evolution of other major ransomwares such as LockBit 5.0, which have also democratized their tools.
The real impact of Prince-Ransomware goes beyond the theoretical. By mid-September 2024, Proofpoint had identified a campaign in which actors were impersonating Royal Mail to distribute Prince-Ransomware in the UK and the USA. Later, in February 2025, Taipei’s Mackay Memorial Hospital was targeted by an attack using CrazyHunter, a derivative of Prince-Ransomware that encrypted over 600 devices at two sites. These incidents demonstrate the growing adoption of this tool by various criminal groups.
Yurei ransomware: emergence and double extortion strategy
First operations and documented victims
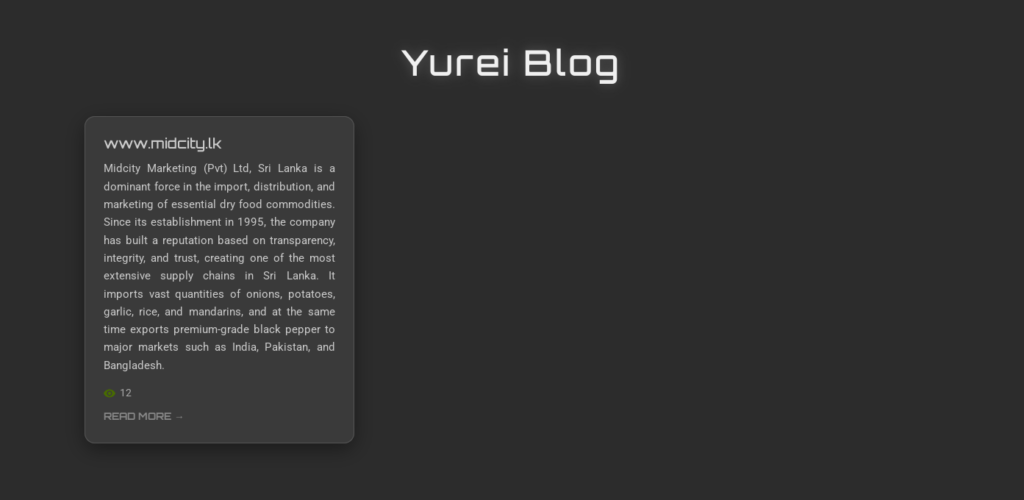
Yurei began operations by targeting a food manufacturing company in Sri Lanka as the first victim listed on its darknet blog on September 5, 2025. Within the first few days of operation, the group had listed three confirmed victims spread across Sri Lanka, India and Nigeria, demonstrating an operational presence on several continents.
This approach reflects the effectiveness of the group’s double extortion model, similar to the strategies employed by DragonForce and other modern groups. In addition to simply encrypting systems, Yurei simultaneously exfiltrates sensitive data to exert a double pressure: payment of a ransom for decryption and to avoid public disclosure of the stolen information. This method radically transforms the nature of the threat, rendering traditional defensive strategies based solely on backup and restore insufficient.
Psychological pressure mechanisms
The group exploits the fear of data leaks and their repercussions as the main lever of coercion on victims. This psychological strategy is particularly aimed at companies whose activities could have an impact on food security and national supply chains, like their first Sri Lankan victim.
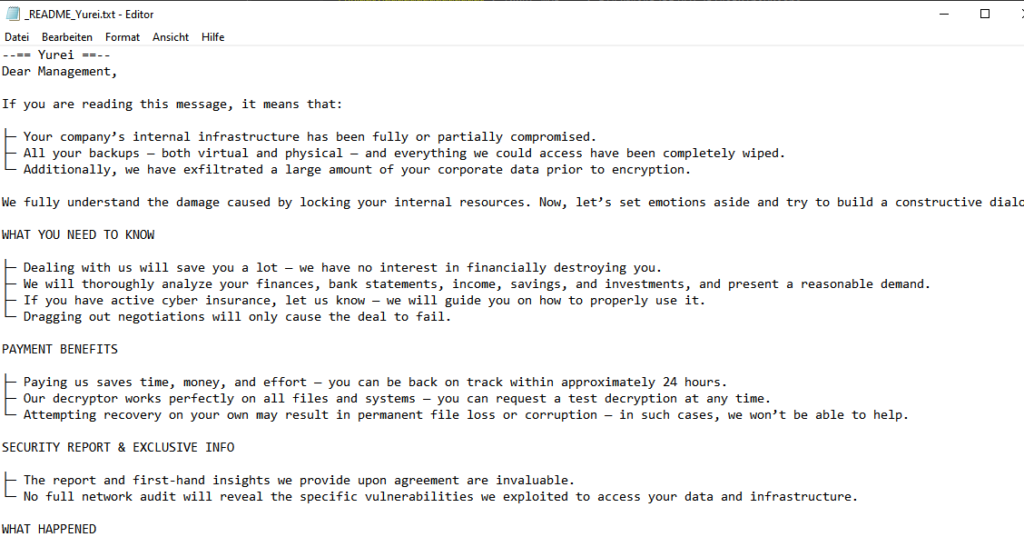
The ransomware file, deployed under the name _README_Yurei.txt, adopts both a professional and threatening tone, directly addressing the executives of targeted organizations. It even offers a “security audit” detailing the vulnerabilities exploited, similar to a penetration test.
Yurei’s technical architecture: a derivative of Prince-Ransomware
Legacy source code and minor modifications
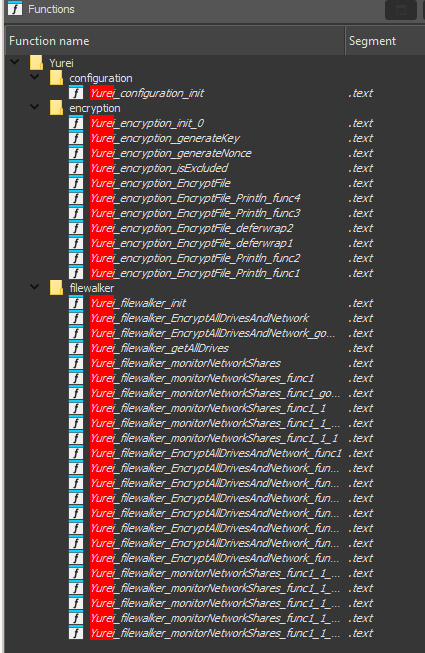
Forensic analysis of Yurei reveals massive reuse of code from Prince-Ransomware, an open source project developed in the Go language. Yurei’s developers made the critical mistake of not cleaning up the binary’s symbols, enabling researchers to clearly identify identical function and module names between the two projects. This forensic approach, similar to that used to analyze HybridPetya and its advanced UEFI techniques, enables development patterns and inherited vulnerabilities to be identified.
CYFIRMA adds:“Analysis of the Yurei ransomware reveals a significant degree of possible reuse of source code from the Prince-Ransomware open-source project. The link is established by symbol retention, corresponding cryptographic schemes, structural similarities in file management, and inherited behavioral quirks“. The filewalker, encryption and configuration modules present in Yurei correspond exactly to the Prince-Ransomware source files available on GitHub. This perfect match confirms that the malicious actors simply downloaded, slightly modified and redeployed the existing code without any substantial development.
Specific technical enhancements
Despite the common base, Yurei features a number of notable changes compared to Prince-Ransomware that improve its operational efficiency:
- Parallelized encryption: unlike the single-task approach of the original code, Yurei uses Go goroutines to encrypt multiple drives simultaneously, considerably speeding up the encryption process.
- Continuous monitoring of network drives: the malware activates a permanent monitoring routine that automatically detects newly connected network drives and adds them to the encryption queue.
- Extended propagation capabilities: Yurei implements lateral movement mechanisms via SMB shares (network file shares), removable media and ID-based remote execution (PsExec style).
ChaCha20 + ECIES encryption mechanism
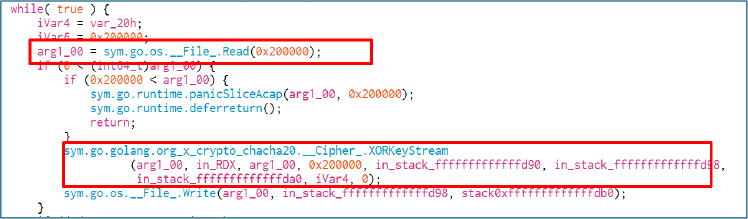
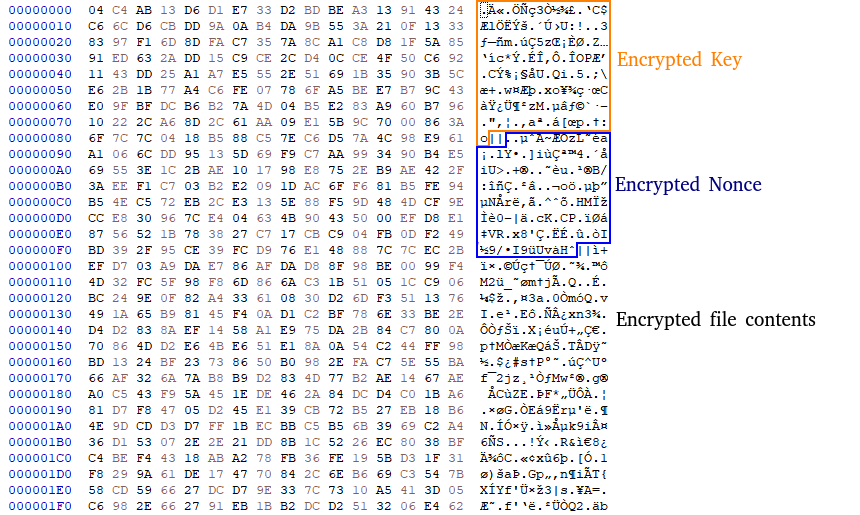
Yurei uses the ChaCha20 algorithm for file encryption, generating a unique key and nonce for each file. These elements are then encrypted with ECIES (Elliptic Curve Integrated Encryption Scheme) using the attacker’s public key.
The structure of encrypted files follows a standardized format: (ENCRYPTED_KEY + NONCE) || CIPHERTEXT, with elements separated by the characters || (0x7c7c). This architecture guarantees optimal decryption while making recovery without operator cooperation technically impossible.
Critical legacy vulnerabilities and defensive opportunities
Volume Shadow Copies deletion failure
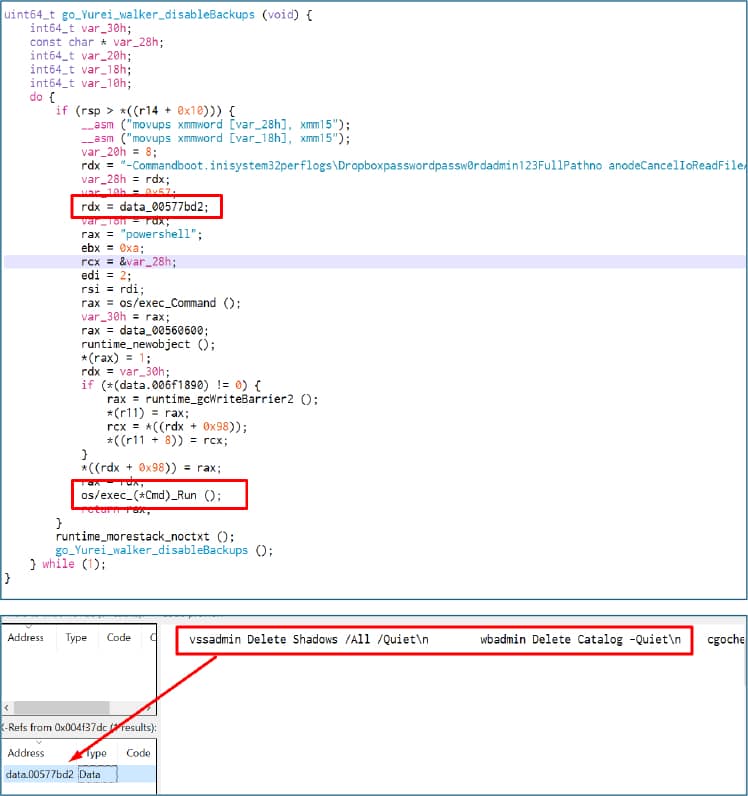
One of Yurei’s most significant vulnerabilities lies in its inability to delete Windows Volume Shadow Copies (VSS). This functionality, usually targeted and destroyed by advanced ransomware, allows files to be restored to previous snapshots without negotiation with the attackers.
This major technical flaw, directly inherited from Prince-Ransomware, reveals the relatively limited skill level of Yurei operators. Researchers at Check Point Research point out: “By reusing the Prince-Ransomware code base, the group was able to launch its operations quickly, but also inherited its shortcomings, notably the failure to delete Volume Shadow Copies”. Organizations that have enabled the VSS service can potentially recover their encrypted files by restoring previous system snapshots.
However, this recovery option only protects against the encryption aspect of the attack, and in no way prevents the extortion associated with data exfiltration. Enabling VSS is a highly recommended protection measure against threats such as Yurei, but does not dispense with a comprehensive strategy including proactive CVE vulnerability management and protection against exfiltration.
Revealing configuration errors
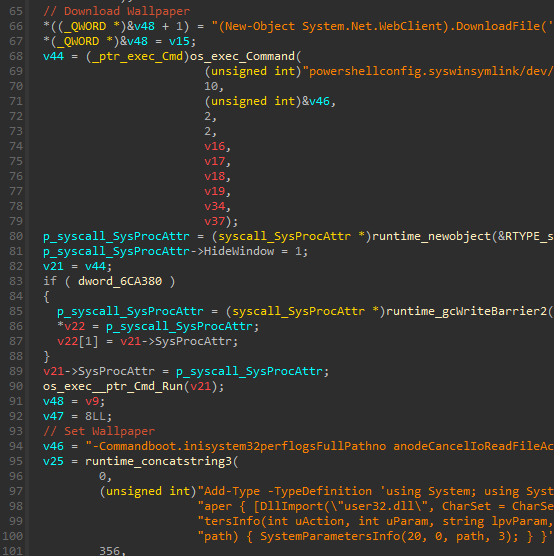
Code analysis reveals other significant technical flaws. PowerShell commands inherited from Prince-Ransomware are supposed to download and set a custom wallpaper, but Yurei’s developers have provided no functional URL for the download.
This omission causes the PowerShell command to fail, generating a uniform black wallpaper instead of a visual ransomware message. This error, combined with the retention of debugging symbols in the binary, confirms that the actors likely used the Prince-Ransomware generator without understanding or modifying its core functionality.
Yurei ransomware propagation and persistence techniques
Payload deployment and lateral movement
Yurei uses sophisticated propagation methods that exceed the capabilities of the original Prince-Ransomware code. The malware deposits executables in temporary directories and uses PowerShell scripts to facilitate network propagation.
Lateral movement mechanisms include the use of PSCredential, CIM sessions, and PsExec-like remote execution to spread the infection across corporate networks. The malware copies its payloads to write-accessible SMB shares under misleading names such as System32_Backup.exe.
As for removable media, Yurei automatically replicates itself on USB drives under the name WindowsUpdate.exe, exploiting users’ familiarity with legitimate system processes.
Advanced anti-forensic techniques
Despite its open source origins, Yurei implements elaborate anti-forensic routines via its selfDestruct function, which sequentially calls secureDelete, cleanTraces and wipeMemory to erase its traces after post-execution.
The secureDelete process performs three overwrite passes with random data, renames the executable twice under randomly generated names, then permanently deletes the file and cleans up system metadata.
Memory cleanup routines include deleting the console history, forcibly triggering the Go garbage collector (Go’s automatic memory release system), and overwriting 1 MB of random memory data to prevent artifacts from being recovered by forensic tools.
Geographical attribution and clues to the origin of Yurei ransomware
Elements of technical attribution
Analysis of the samples submitted to VirusTotal reveals geographical clues converging on a Moroccan origin. All Yurei samples were initially submitted from Moroccan IP addresses, with one sample lacking a ticket ID, suggesting a test build potentially downloaded by the developers themselves.
Examination of the HTML code of the .onion negotiation page reveals comments in Arabic, reinforcing the hypothesis of a geographical origin in the Maghreb or the Middle East. These linguistic elements are significant markers of technical attribution.
Recovered path artifacts show references to D:\\\\\\\\satanlockv2\\\\\\\\*, suggesting possible links with the SatanLockV2 ransomware. The latter, also based on Prince-Ransomware, had initially been submitted from Morocco, reinforcing the geographical hypothesis. This attribution, estimated with a low level of confidence, is based primarily on the convergence of several technical clues rather than on definitive evidence.
Limited operational sophistication
The possible use of VirusTotal to test the ransomware detection rate suggests that operators lack experience in operational security operations (OPSEC). This practice, indicative of entry-level players, contrasts with established ransomware groups with private testing infrastructures.
Consequences of Yurei for the cybercriminal threat ecosystem
Democratization of cybercrime through open source
The emergence of Yurei illustrates a worrying trend in the cybercrime ecosystem, with open source malware significantly lowering the barriers to entry. This democratization allows less skilled actors to access advanced offensive capabilities without substantial investment in development.
This trend accelerates the proliferation of ransomware variants, while complicating attribution for security teams. Other emerging groups such as INC Ransom and Lynx ransomware also illustrate this rapid evolution of the ecosystem. Groups can now launch operations quickly by inheriting not only the technical capabilities of other developers, but also their vulnerabilities and flaws.
The reuse of malicious code paradoxically generates opportunities for cybersecurity analysts, who can develop detection signatures covering several families derived from the same source code. Nevertheless, as the initial success of Yurei demonstrates, even unsophisticated operations can achieve significant results.
Impact on defensive strategies
The move towards data theft-based extortion models is fundamentally transforming defensive requirements. Traditional backup and restore strategies, while essential against encryption, are becoming insufficient in the face of the data publication threat.
Organizations must now integrate protection against exfiltration into their security architectures, including monitoring outgoing traffic, classifying sensitive data, and preparing for data publication scenarios.
Yurei’s rapid spread (three victims in just a few days) underlines the importance of early detection and rapid response. Security teams need to monitor indicators of compromise associated with this emerging threat, and prepare response procedures specifically tailored to double extortion scenarios.
Defensive recommendations against Yurei ransomware
Technical protection measures
Enabling the Volume Shadow Copy Service (VSS) is a critical protection measure against Yurei and similar ransomware with this vulnerability. Organizations should set up regular snapshots and periodically test restoration procedures.
Behavioral detection becomes crucial to identify Yurei activity, including suspicious PowerShell commands, SMB propagation attempts, and parallel encryption patterns. SOC teams need to monitor the creation of files with the .Yurei extension and new files named WindowsUpdate.exe or System32_Backup.exe.
Network segmentation limits the impact of Yurei’s lateral propagation. Organizations should restrict SMB access to known subnets, disable anonymous access to shares, and monitor for unusual SMB write activity. In the event of compromise despite these preventive measures, it is then crucial to have an effective data recovery plan and tested incident response procedures in place.
Organizational strategies
For a robust defense, organizations need to adopt complementary organizational strategies:
- Adopting a connected security architecture integrating endpoint, network and identity protection is becoming essential, particularly in hybrid and multi-cloud environments.
- Organizations need to deploy large-scale anti-phishing measures, including user awareness programs, email analysis and behavioral analytics capable of detecting AI-generated lures.
- The deployment of honeypots and threat hunting enables early discovery of affiliate activity and lateral movements in the attack chain. Backups should be segmented and recovery processes regularly tested.
Indicators of compromise (IoC)
To facilitate operational monitoring, here are the key IoCs recommended by CYFIRMA to be integrated into detection systems:
- Trading .onion domain:
fewcriet5rhoy66k6c4cyvb2pqrblxtx4mekj3s5l4jjt4t4kn4vheyd[.]onion - Known file hashes:
- YureiRansomware.exe (SHA256: 4f88d3977a24fb160fc3ba69821287a197ae9b04493d705dc2fe939442ba6461)
- Associated PowerShell script (SHA256: 1263280c916464c2aa755a81b0f947e769c8a735a74a172157257fca340e1cf4)
- Behavioral artifacts: files with
.Yureiextension, copies namedWindowsUpdate.exe(USB) andSystem32_Backup.exe(SMB) - YARA rules: integrate signatures covering Yurei and indicators inherited from Prince-Ransomware for extended coverage
Expected evolution and continuous monitoring
Development trajectory
Although Yurei currently has significant technical flaws, its adoption of the double extortion model and early operational successes suggest potential for evolution. Operators could patch vulnerabilities inherited from Prince-Ransomware in future versions.
Improved anti-forensic techniques and the correction of the Volume Shadow Copies deletion error would significantly transform the dangerousness of this threat. The future integration of emerging technologies, such as theAI seen in HexStrike or the automated capabilities of Promptlock, could significantly transform Yurei’s capabilities. Security teams should monitor the evolution of this family to detect such improvements.
Monitoring indicators
Organizations should monitor .onion domains associated with Yurei and detect communications to the identified trading domain. Monitoring known file hashes and specific behavior patterns enables early detection.
The integration of YARA rules covering Yurei signatures and Prince-Ransomware legacy indicators offers extensive coverage against this family and its future variants.
Conclusion
Yurei perfectly embodies the challenges posed by the increasing accessibility of cybercriminal tools via open source malware. This group, despite its obvious technical limitations, proves that even unsophisticated operations can achieve significant success in today’s ecosystem.
Yurei’s exploitation of Prince-Ransomware illustrates how publicly available source code can accelerate the proliferation of threats while lowering the threshold of entry for novice cybercriminals. This evolution is fundamentally transforming the nature of attribution and defense in cybersecurity.
For cybersecurity equioes, Yurei paradoxically offers opportunities thanks to its technical vulnerabilities, notably the failure to remove Volume Shadow Copies. However, the double extortion model adopted by the group is a reminder that traditional recovery strategies are no longer sufficient in the face of modern threats.
The emergence and rapid growth of Yurei is a wake-up call for the security community: continued vigilance, adaptation of defensive strategies and preparation for double extortion scenarios become absolute imperatives in the face of this new generation of accessible and replicable threats.
Main article sources :
- Check Point Research: Yurei & The Ghost of Open Source Ransomware
- CYFIRMA: Yurei Ransomware: The Digital Ghost
- Industrial Cyber: Yurei ransomware exploits open-source tools, raising double extortion risks
- GBHackers : Yurei Ransomware Uses PowerShell to Deploy ChaCha20 File Encryption
- Halcyon AI: Open-Source Builder for Prince Ransomware Discovered Available on GitHub
- Foresiet: Understanding Prince Ransomware: A Comprehensive Overview
- Proofpoint: Royal Mail Lures Deliver Open Source Prince Ransomware
- WithSecure Labs: CrazyHunter: The Rising Threat of Open-Source Ransomware
