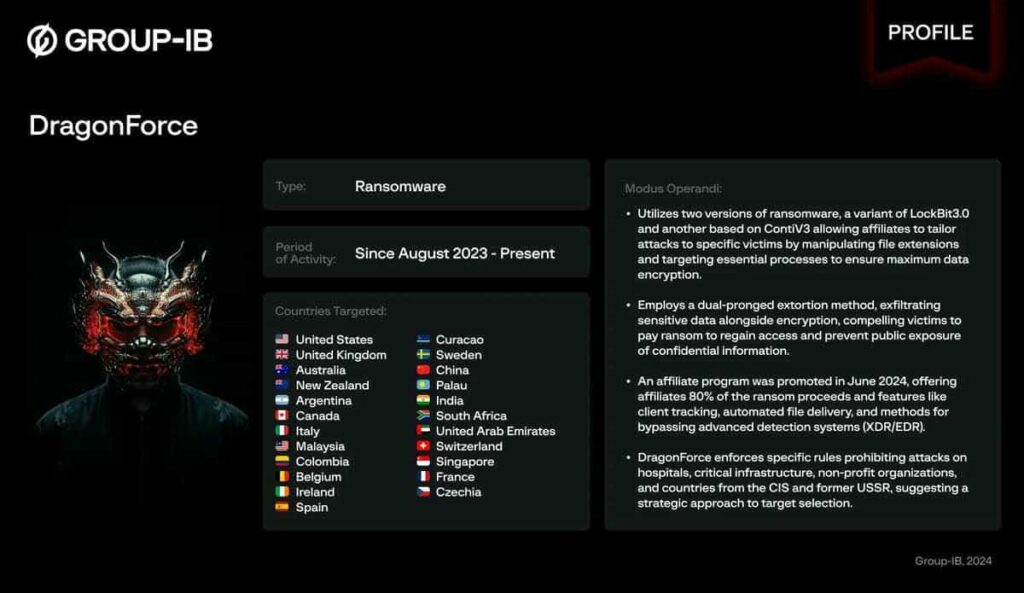
In just a few months, DragonForce has established itself as one of the most feared ransomware groups of 2025. Behind this name lies a cybercriminal cartel capable of combining the technical power of variants derived from LockBit and Conti with a novel Ransomware-as-a-Service (RaaS) model. Far from traditional structures, DragonForce offers its affiliates a complete white-label infrastructure, centralized campaign management and an aggressive expansion strategy. The result: the industrialization of ransomware, which is redefining the rules of the game and now threatens both large corporations and public institutions worldwide.
Table des matières
ToggleOrigins of DragonForce
The DragonForce group first emerged at the end of 2023 as a notable player in the ransomware ecosystem. The first documented attacks date back toAugust 2023, with initial technical variants stemming from LockBit 3.0, followed as early as 2024 by modified versions of ContiV3, illustrating a sophisticated double extortion strategy.
By mid-2024, DragonForce had launched a Ransomware-as-a-Service (RaaS) program, offering its affiliates turnkey tools – administration panels, data leakage infrastructure, technical support – in exchange for a commission of up to 20-20-30% of the ransom.
Active since 2023, the threat rapidly spread internationally. Between August 2023 and August 2024, DragonForce claimed 82 victims, notably in the manufacturing, real estate, transportation and government services sectors. Its presence is now global, with campaigns targeting the USA, Italy, Australia, the UK and beyond.
DragonForce is now seen not simply as an underground group, but as a ransomware cartel: its strength lies in its white label model, its ability to attract and structure affiliates, and its extensive presence in the organized cybercrime market .
Technical architecture: two variants to dominate the market
DragonForce operates with two main ransomware variants, a strategy that testifies to its technical sophistication and willingness to attract different types of affiliates.
Variant based on LockBit 3.0
The first variant is based on the disclosed LockBit 3.0 constructor (also known as LockBit Black). This pragmatic approach enables former LockBit affiliates to adapt quickly to the DragonForce infrastructure. The encryption algorithm uses AES for primary file encryption and RSA to secure the keys, a proven method in the ransomware ecosystem.
Original” variant based on Conti v3
More sophisticated, the second variant is presented as “original” but is actually based on the leaked source code of Conti v3, enhanced with new features. This variant uses the ChaCha8 algorithm for faster encryption and incorporates advanced evasion techniques, notably the “Bring Your Own Vulnerable Driver” (BYOVD) method .
The BYOVD technique enables ransomware to exploit vulnerable but digitally signed drivers to terminate the processes of kernel-level security solutions. DragonForce uses :
- TrueSight.sys: a driver from Adlice Software (RogueKiller Antirootkit Driver v3.3)
- RentDrv.sys: developed by Hangzhou Shunwang Technology
These drivers expose IOCTL commands with privileged functionality but lack adequate access controls, enabling the termination of critical processes via ZwOpenProcess() and ZwTerminateProcess().
DragonForce targets: from global diversification to major UK retailers
Global trend in victims since 2023
Since its first attacks at the end of 2023, DragonForce has seen rapid growth in its activity. While claiming only a handful of victims in its early days, the group is now identified as one of the most active ransomware collectives of 2025.
According to a Q2 2025 report by GuidePoint Security, DragonForce has claimed over 120 victims worldwide since its inception, with a marked acceleration in June 2025 when almost 20 new victims were published on its leak site. This dynamic confirms the cartel’s growing power despite the general fragmentation of the RaaS landscape.
Diversified global targeting
Outside the UK, DragonForce has diversified its attacks by targeting different sectors internationally. In particular, the group hit healthcare with the Heart Centre in Australia, where around 5 GB of patient data was released in early 2025, and consumer services with theattack on 5àSec in France, affecting the international network of dry cleaners. DragonForce also targets industrial manufacturing, logistics and retail.
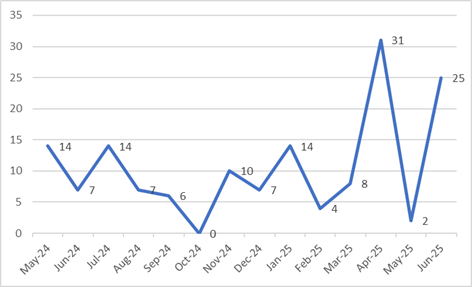
In all, according to Check Point Research, the DragonForce leak site had over 250 published victims by mid-2025, with a notable peak in activity during the spring campaigns.
These figures testify to a broader offensive strategy than that of 2024: DragonForce now targets Western media brands as well as more discreet, but equally strategic, industrial and commercial companies.
Campaign against the British retail sector
In the spring of 2025, DragonForce orchestrated a coordinated campaign against major British retailers, demonstrating its ability to carry out large-scale operations:
Marks & Spencer suffered a major attack at the end of April 2025, disrupting online ordering, payment and logistics systems. The attackers sent extortion emails directly to the CEO, threatening to divulge sensitive information. The operation, attributed to DragonForce via the Scattered Spider collective, had a massive economic impact: around £15 million in weekly losses, an estimated £300 million shortfall on 2025/26 profits, and a £750 million fall in market capitalization.
Co-op confirmed the exposure of the personal data of over 10,000 members following a compromise of its back-office systems.
Harrods, the prestigious London department store, had to restrict internet access and implement mitigation measures after an attack also attributed to DragonForce .

Initial access methods and attack techniques
DragonForce employs a diverse arsenal of initial access techniques:
Exploiting vulnerabilities
The group actively exploits several critical vulnerabilities:
- CVE-2021-44228: Log4Shell (Apache Log4j2)
- CVE-2023-46805 and CVE-2024-21887: Ivanti Connect Secure vulnerabilities
- CVE-2024-21412: Microsoft Windows SmartScreen bypass
- CVE-2024-21893: Ivanti path traversal
Sophisticated attack chain
Forensic analysis reveals a structured attack methodology:
- Initial access via phishing or vulnerability exploitation
- Deployment of Cobalt Strike for campaign management
- Installation of SystemBC as a persistence backdoor
- Elevation of privileges and escalation to SYSTEM
- Active reconnaissance with tools such as Mimikatz, ADFind and SoftPerfect Network Scanner
- Lateral movement via RDP and exploitation of legitimate RMM tools
- Data exfiltration before encryption
- Deployment of ransomware with erasure of event logs
Abuse of legitimate RMM tools
DragonForce recently exploited vulnerabilities in SimpleHelp, a remote management tool, to carry out attacks against managed service providers. This “Living off the Land” technique enables attackers to use legitimate applications generally authorized in corporate environments.
The cartel model: revolutionizing the ransomware ecosystem
In March 2025, DragonForce officially announced its transformation into a “ransomware cartel”, an evolution that goes beyond the traditional Ransomware-as-a-Service (RaaS) model. Rather than a centralized organization directly controlling operations, DragonForce now functions as a coalition of affiliates, each able to run its own campaigns while benefiting from the infrastructure, tools and support provided by the group. This hybrid model attracts new partners, increases the resilience of the criminal network and strengthens its capacity for global expansion.
White-label service and expansion
One of the DragonForce cartel’s major assets is its white-label offer. In concrete terms, affiliates can use the DragonForce infrastructure while operating under their own identity, as if they were running their own ransomware group. This approach transforms DragonForce into a true cybercrime industry, where branding and autonomy play a central role.
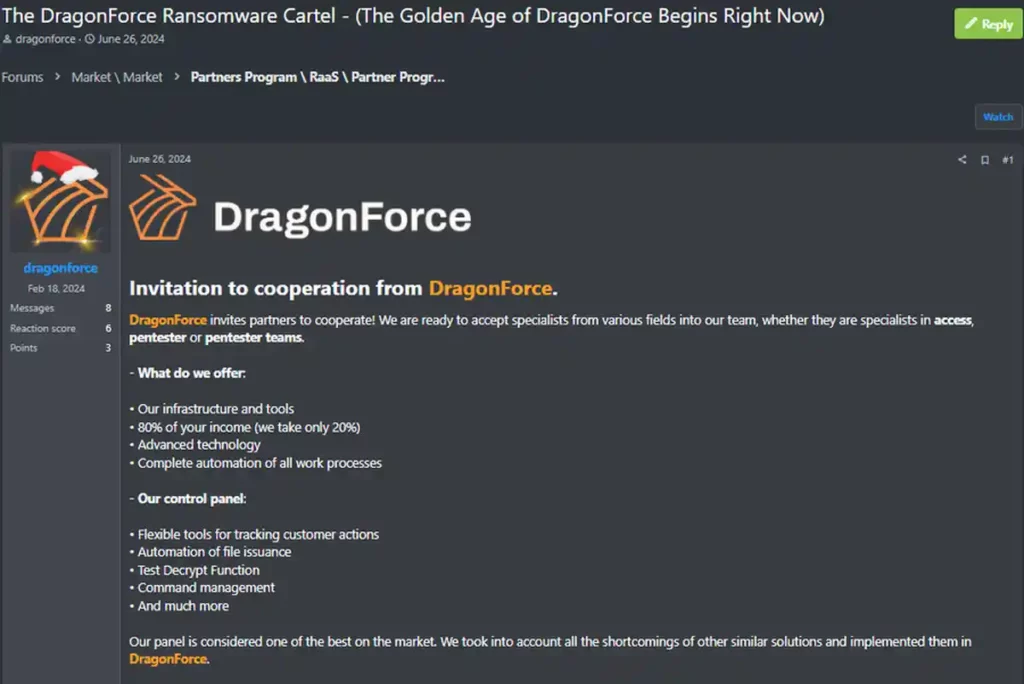
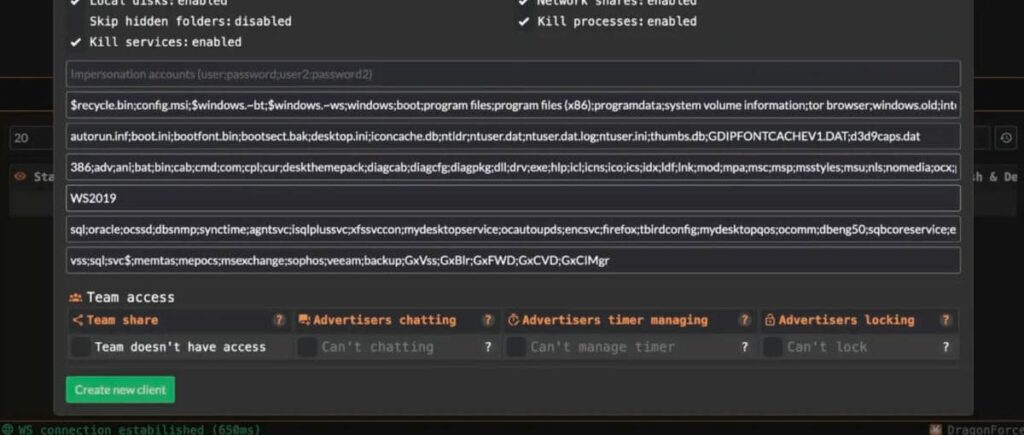
The operation is based on several pillars:
- Attractive profit-sharing: affiliates keep up to 80% of ransom money, while DragonForce takes a 20% commission. This rate is more competitive than that of older groups such as LockBit, making it easier to recruit new players(Group-IB).
- Turnkey infrastructure: leak site hosting, secure payment management, command-and-control servers and integrated trading tools.
- Advanced customization: creation of customized ransomware samples, choice of encryption type (full, partial, header), modification of ransom notes and configuration of targeted file extensions.
- Technical support and ongoing updates: DragonForce maintains its tools for bypassing security defenses, thanks in particular to BYOVD techniques and the regular integration of new exploited vulnerabilities.
This model attracts affiliates with a wide range of profiles: former LockBit or Conti operators, emerging groups looking for reliable infrastructure, or cybercriminals looking to professionalize quickly. By establishing itself as an open criminal platform, DragonForce strengthens its appeal and increases its market share in the ransomware ecosystem.
Advanced affiliate panel
At the heart of the DragonForce model is an administration panel that illustrates the level of professionalization achieved by the cartel. Designed as a true campaign management interface, it gives affiliates control over every stage of their operations:
- Hierarchical team management: possibility of creating sub-accounts with differentiated access levels, reflecting a quasi-corporate organization.
- Automated publication of stolen data: schedule the progressive online publication of exfiltrated information to maximize pressure on victims.
- Real-time monitoring: visualization of active infections, status of negotiations and payments in progress.
This level of sophistication brings DragonForce closer to the operation of a criminal SaaS platform, where each affiliate has its own dashboard and integrated tools to manage its business. This professionalism testifies to the industrialization of ransomware, where technology, organization and communication are designed to maximize both the efficiency and attractiveness of the cartel.
Cartel warfare and elimination of competition
The rise of DragonForce has led to increased rivalry with other ransomware groups. The move to a cartel model, attractive to many affiliates, puts the group in head-to-head competition with rival collectives who are also seeking to recruit and retain partners.
Attacks on RansomHub
In April 2025, the sudden disappearance of RansomHub left the field open for DragonForce to occupy. The cartel immediately claimed that RansomHub was “joining” its ranks, a communication tailored to attract affiliates in transit.
The conflict then materialized with cross-attacks on infrastructures. The RansomHub leak site was compromised and briefly displayed the message “RansomHub R.I.P 03/03/2025”, symbolically marking the end of the group. In retaliation,RansomHub spokesperson“koley” defaced the DragonForce site, accusing the cartel of collaborating with Russian law enforcement and being infiltrated by “traitors”, forcing DragonForce to temporarily suspend recruitment of new affiliates before the leaks site came back online.

Defacement of competing sites
At the same time, DragonForce carried out targeted attacks on the leak sites of rival groups such as BlackLock and Mamona, affixing its own logo. At BlackLock, these defacements leaked internal communication logs and exposed configuration files, destabilizing these players while strengthening DragonForce’s position in the hierarchy of ransomware groups.
Economic impact and ransom trends
Analysis of ransom demands reveals a sophisticated pricing approach based on in-depth victim research. DragonForce uses tools such as ZoomInfo to assess the revenues of target organizations and adjust its demands accordingly.
The amounts observed vary considerably:
- Minimum: several hundred thousand dollars
- Estimated maximum: $7 million during a negotiation in 2024
This dynamic pricing approach testifies to the group’s growing professionalism and understanding of the economic realities of its victims.
Challenges for data recovery
Faced with DragonForce ransomware, victim organizations have several options, each presenting specific challenges:
Technical analysis of variants
The encryption techniques employed make recovery complex without decryption keys:
- The LockBit variant uses AES with RSA for key protection
- The Conti variant uses ChaCha8 for optimized performance
- Three encryption modes are available: full, partial and header-only.
Recovery approaches
Data recovery experts like SOS Ransomware develop specialized methods:
- Analysis of vulnerabilities in encryption implementation
- Recovery of data deleted before encryption
- Reverse engineering of encryption algorithms
- Repair of partially damagedfiles
These proprietary techniques often make it possible toavoid paying the ransom while recovering critical data.
Protection measures and recommendations
In the face of DragonForce’s growing sophistication, organizations need to adopt a multi-layered security approach:
Technical prevention
- Rigorous patch management, particularly for vulnerabilities exploited by the group
- Network segmentation to limit lateral propagation
- Behavioral monitoring to detect BYOVD techniques
- Protection of RMM tools and reinforced authentication
Organizational preparedness
- Regularly testedoffline backups
- Business continuity plans including ransomware scenarios
- Staff training in advanced phishing techniques
- Incident procedures with established emergency contacts
Outlook for the future
DragonForce represents the natural evolution of ransomware towards more flexible, decentralized models. Several trends are emerging:
Innovation in business models
- White-label services enabling complete customization
- Decentralized ecosystem reducing the risk of dismantling
- Economic warfare between cartels to attract the best affiliates
Increasing technical sophistication
- Integration of AI to automate attacks
- Advanced evasion techniques against modern security solutions
- Advanced payloadcustomization per victim
Conclusion
DragonForce embodies the new generation of ransomware threats: technically sophisticated, organizationally agile and strategically aggressive. Its transformation from a possible hacktivist group into a cybercriminal cartel illustrates the fluidity of the cyberthreat landscape and the adaptability of malicious actors.
For organizations, this evolution calls for a fundamental review of cybersecurity strategies. Defense can no longer be content with reactive approaches; it must anticipate criminal innovations and constantly adapt.
In the face of such adversaries, specialized expertise becomes crucial. Whether for prevention, detection or post-incident recovery, only a professional approach combining technological intelligence, behavioral analysis and advanced recovery capabilities can offer effective protection against this constantly evolving threat.
SOS Ransomware remains mobilized 24/7 to support organizations affected by these new threats. Our technical expertise and field experience enable us to offer tailored recovery solutions, even against the most sophisticated variants such as those deployed by DragonForce.
Main article sources :
- Group-IB: DragonForce Ransomware Group
- Bitdefender : DragonForce: The Ransomware Cartel Guarding Its Burrow
- Bridewell: Who are Dragonforce Ransomware Group?
- Barracuda Networks Blog: DragonForce Ransomware Cartel vs. Everybody
- SentinelOne: DragonForce Ransomware Gang | From Hacktivists to High Street Extortionists
- Specops Software: DragonForce: Inside the Ransomware-as-a-Service group
- Sophos: DragonForce targets rivals in a play for dominance
