A simple command line can infect your PC. The ClickFix attack, which exploits Internet users’ trust in familiar interfaces, has seen explosive growth since 2024. This social engineering technique now ranks second only to phishing as the most widely exploited intrusion method, turning users into unwitting actors in their own compromise.
The year 2025 marks a turning point in the evolution of cyberattacks, with the meteoric rise of ClickFix turning traditional defense strategies on their head. Unlike traditional attacks, which exploit software vulnerabilities, ClickFix uses human trust and psychology to bypass all technical protections. The principle is frighteningly effective: to induce the victim to copy and execute a malicious command himself, making him believe that it solves a legitimate problem.
Table des matières
ToggleA spectacular leap reflecting the effectiveness of the technique
The figures speak for themselves: ClickFix detections rose by 517% between the second half of 2024 and the first half of 2025, making this technique the second most common attack vector, just behind traditional phishing. This meteoric rise, documented by ESET in its bi-annual threat report, illustrates the massive adoption of this method by the cybercriminal ecosystem.
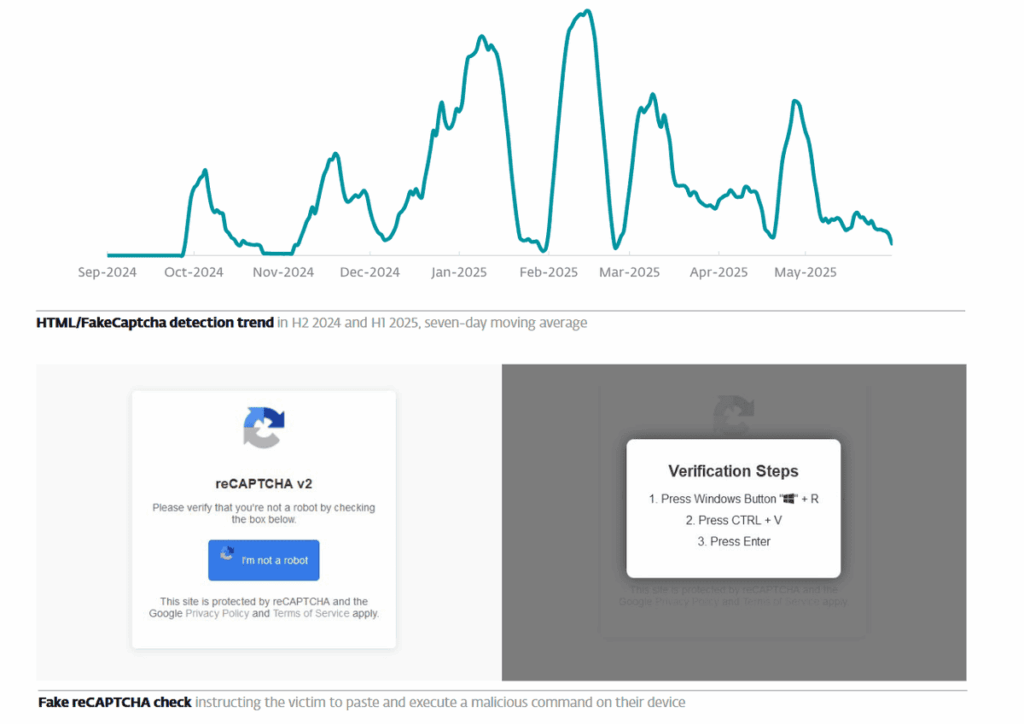
In this report Dušan Lacika, Senior Detection Engineer at ESET, explains this success: “This new social engineering technique is effective because it’s simple enough for the victim to follow the instructions, credible enough to give the impression that it could solve an invented problem, and plays on the fact that victims don’t pay much attention to the exact commands they’ve been asked to paste and execute on their device. It’s also a good example of how quickly threat actors adopt new techniques, once they’ve proven themselves.”
Microsoft Threat Intelligence observes thousands of targeted devices daily around the world, affecting organizations in all sectors. The company has had to intervene with multiple customers in various industries to counter ClickFix campaigns attempting to deploy payloads like the prolific Lumma Stealer malware.
Anatomy of an attack that exploits trust
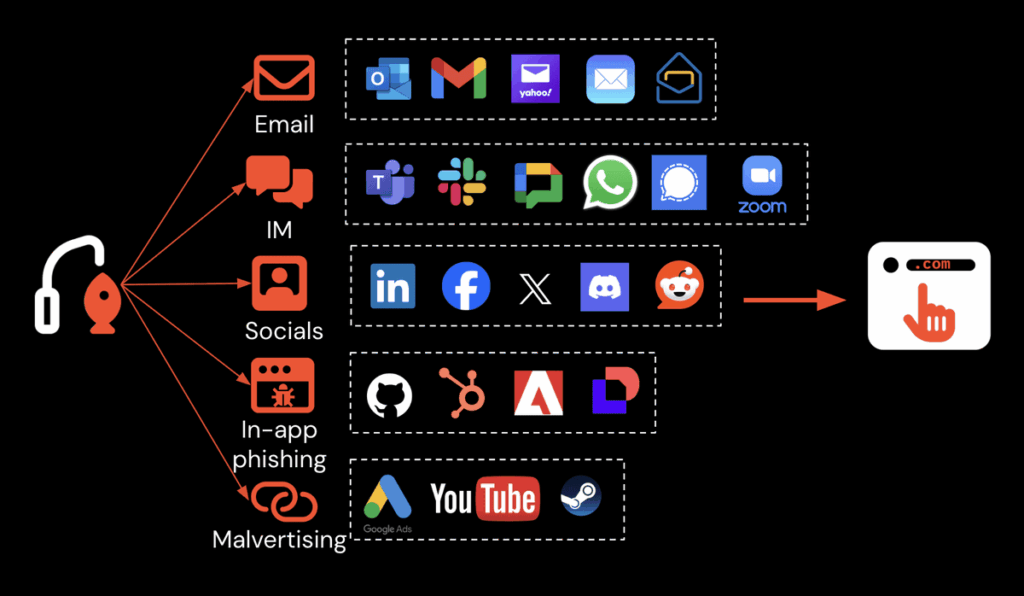
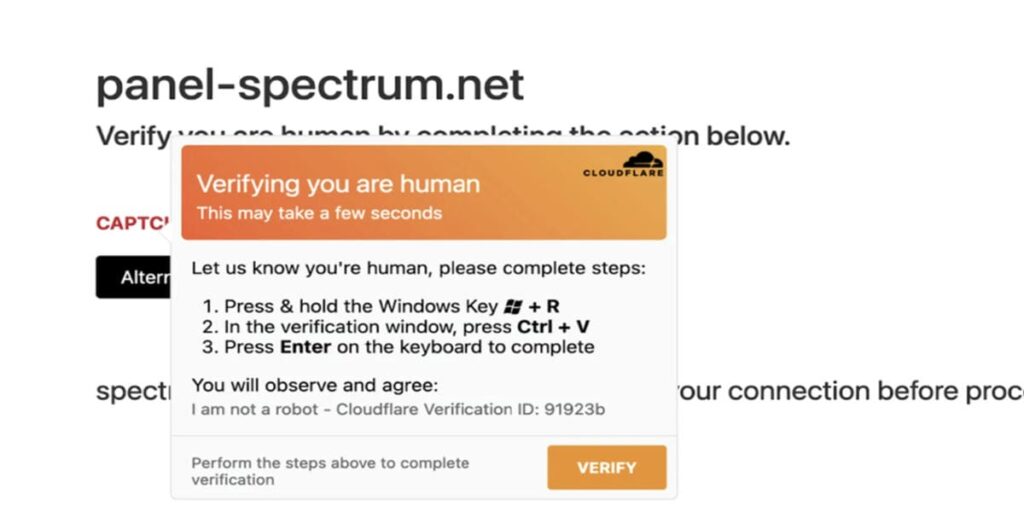
The ClickFix mechanism is based on a carefully orchestrated attack chain that transforms legitimate reflexes into infection vectors. It all starts with a visual lure: a fake system error message, a counterfeit CAPTCHA check or a security notification imitating reputable services such as Cloudflare Turnstile or Google reCAPTCHA. These deceptive interfaces are presented to users via phishing emails, compromised websites or malicious advertising.
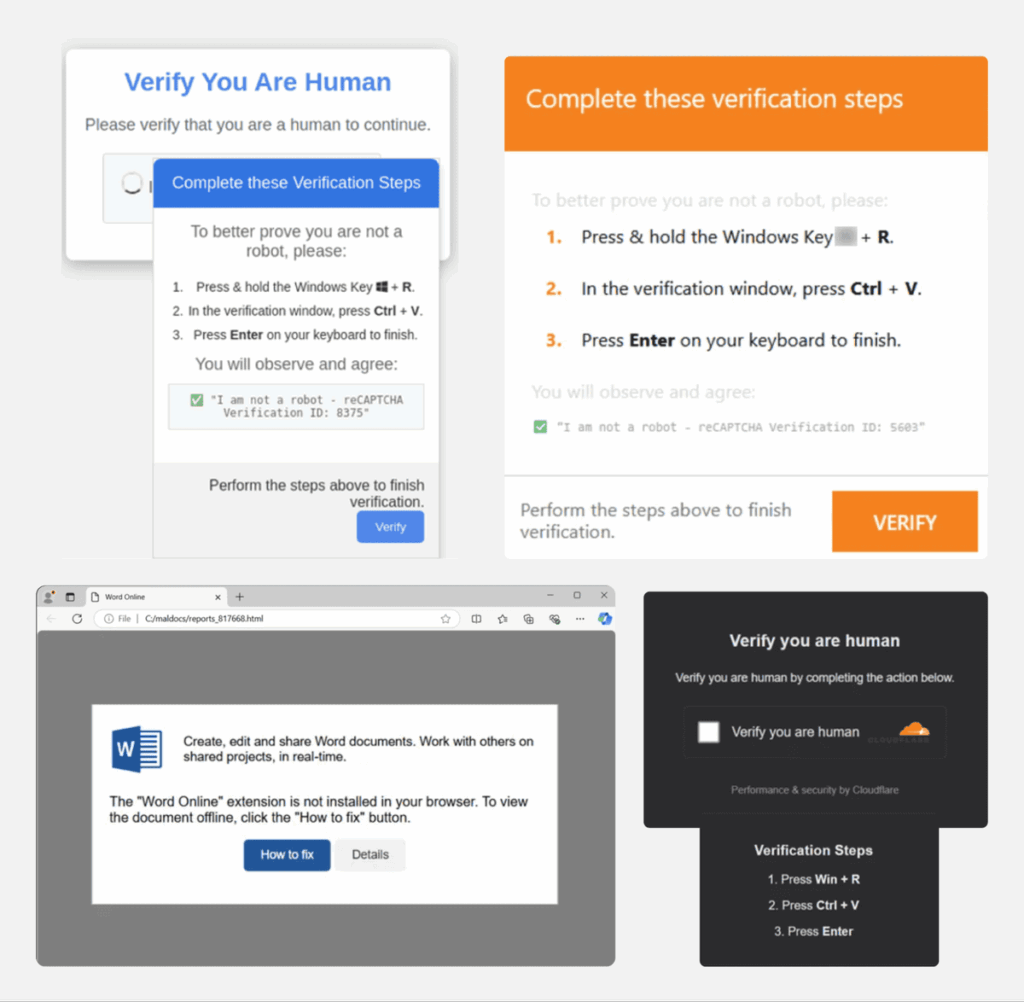
When the user clicks on the “Check” or “Solve problem” button, a JavaScript script automatically copies a malicious command to the clipboard, without the victim even realizing it. Detailed instructions then appear, guiding the user to open the Windows “Run” dialog (Win+R), Windows Terminal or PowerShell, and paste the contents of the clipboard there. Once the command has been executed, the malware downloads and installs itself on the machine.
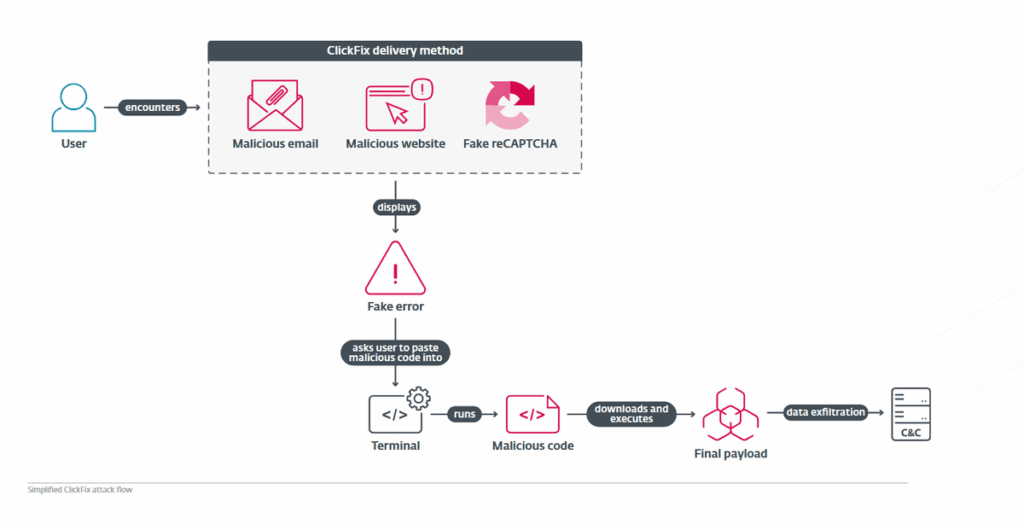
What makes ClickFix so pernicious is that it is the user himself who executes the malicious code, bypassing many automated protections.
Three reasons why ClickFix is so effective
Users are unprepared for this type of attack
For more than a decade, cyber security awareness has focused on teaching simple defensive behaviors: don’t click on suspicious links, avoid downloading dubious files, don’t enter your credentials on unknown sites. But no one has taught users to be wary of opening a terminal to execute a command, especially when this action is presented as the solution to a technical problem.
Suspicion is further reduced by the fact that the malicious action of copying to the clipboard takes place in the background via JavaScript in 99% of cases. The user is unaware that anything untoward has just happened. What’s more, modern ClickFix sites are becoming increasingly sophisticated and legitimate in appearance, sometimes even incorporating instructional videos showing the user exactly how to proceed.
ClickFix is not detected during the delivery phase
Pages using ClickFix, like modern phishing sites, employ an arsenal of evasion techniques that make them invisible to security tools: camouflage and domain rotation to avoid blacklists, bot protection to prevent automated analysis, massive content obfuscation to thwart detection signatures.

By using delivery vectors other than email – notably SEO poisoning (placing fraudulent websites in the top search engine results) and malicious advertising via Google Search – attackers bypass an entire layer of detection. By creating new domains or compromising legitimate sites, they create “watering hole” scenarios (booby-trapping a legitimate website) to intercept users browsing the Internet.
Malvertising”, a word derived from the contraction of “malicious” and “advertising” designating a false advertisement used as a gateway to infection, adds a further layer of targeting. Google ads can be configured to target searches from specific geographic areas, tailored to particular email domains or device types. If you know your target’s location, you can set up the ad campaign accordingly.
Finally, because the code is copied inside the browser’s sandbox (an isolated environment designed to protect the system from potentially dangerous web content), conventional security tools can neither observe nor flag this action as potentially dangerous. The last – and only – opportunity for organizations to stop ClickFix therefore lies at the endpoint (the end-user’s computer or device), after the user has attempted to execute the malicious code.
EDR is the last line of defense, and it’s not infallible
There are several stages in the attack that can and should be intercepted by EDR (Endpoint Detection and Response) solutions, but the level of detection and real-time blocking depends on the context. As there is no downloading of files from the web, and the act of executing code on the machine is initiated by the user, there is no context linking the action to another application to make it suspect.
Malicious commands themselves can be obfuscated or broken down into several steps to avoid detection by heuristic rules. EDR telemetry can record the execution of a PowerShell process, but without a known malicious signature or clear policy violation, it may not report it immediately. The final phase when the attack should be intercepted by any respectable EDR is the moment of malware execution. But evading detection is a cat-and-mouse game, and attackers are constantly looking for ways to modify their malware to evade or disable detection tools.
Cybercriminal groups and distributed payloads
ClickFix is regularly used by the Interlock ransomware group and other prolific threat actors, including state-sponsored APTs. Several public data breaches have been linked to ClickFix-style TTPs, such as Kettering Health, DaVita, the city of St. Paul in Minnesota and the Texas Tech University Health Science Centers.
Interlock’s adoption of the FileFix technique, an evolution of ClickFix exploiting the Windows File Explorer rather than the Run dialog box, illustrates the constant adaptability of cybercriminals. This variant moves the attack to an even more familiar and reassuring environment for users.
Microsoft observes that ClickFix campaigns deliver an impressive variety of malware:
- infostealers such as Lumma Stealer, which appears to be the most prolific ClickFix payload according to Microsoft’s observations and investigations;
- remote access tools (RATs) such as Xworm, AsyncRAT, NetSupport and SectopRAT, enabling attackers to carry out manual activities such as reconnaissance, lateral movement and persistence;
- loaders such as Latrodectus and MintsLoader, capable of delivering additional malware and payloads;
- rootkits, such as a modified version of the open source r77, enabling attackers to employ several sophisticated persistence and defense evasion tactics.
Proofpoint has observed ClickFix campaigns leading to malware including AsyncRAT, Danabot, DarkGate, Lumma Stealer, NetSupport and many others.
Beyond Windows: ClickFix now targets macOS
In June 2025, a ClickFix campaign targeting macOS users to deliver Atomic macOS Stealer (AMOS) was reported. This new campaign marks an evolution in the threat landscape, as ClickFix was previously mainly observed in Windows attacks.
The campaign, dating back to late May 2025 according to Microsoft’s analysis, redirects targeted users to fraudulent sites generated by ClickFix impersonating Spectrum, a US company providing cable TV, Internet access and unified communications services. Interestingly, the page displays instructions for Windows devices even to macOS users, but copies a different command tailored to the detected operating system in the background.
ClickFix industrialization: kits and services for sale
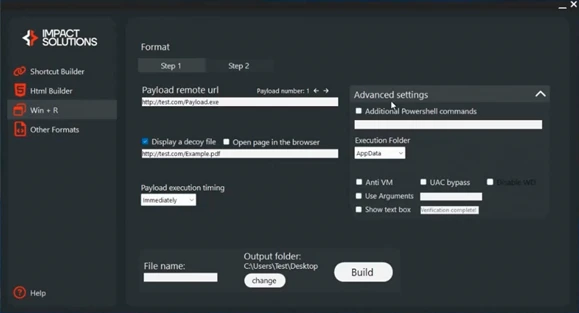
The criminal ecosystem quickly organized itself around ClickFix. Microsoft Threat Intelligence has observed several actors selling ClickFix builders (also known as “Win + R”) on popular hacker forums since late 2024. Some players bundle ClickFix builders into their existing kits, which already generate various files such as LNK, JavaScript and SVG.
These kits offer the creation of landing pages with a variety of available decoys including Cloudflare, as well as the construction of malicious commands that users will paste into the Windows Run dialog. These kits claim to guarantee antivirus and web protection bypassing (some even promise to bypass Microsoft Defender SmartScreen), as well as payload persistence. The cost of subscribing to such a service can range from US$200 to US$1,500 per month. Vendors also offer one-off solutions (e.g. only source code, landing page or command line) priced between $200 and $500.
Defense strategies against ClickFix
In the face of this growing threat, organizations need to adopt a defense-in-depth approach combining technical measures and human awareness.
Priority technical measures
Microsoft recommends several essential configurations:
- activate network and webprotection in Microsoft Defender for Endpoint to guard against malicious sites and Internet threats;
- use PowerShell script block logging to detect and analyze obfuscated or encoded commands, providing visibility into the execution of malicious scripts that might otherwise escape traditional logging;
- configure PowerShell execution policies such as AllSigned or RemoteSigned to reduce the risk of malicious execution by ensuring that only signed and trusted scripts are executed;
- disable the Run dialog box (Win + R) and remove the Run option from the Start menu via Group Policy if these features are not required;
- create an App Control policy prohibiting the launch of native Windows binaries from Run.
Awareness as an essential bulwark
Organizations can reduce the impact of this technique by training users and employees to recognize social engineering attacks, and ensuring that they are aware of what they are copying and pasting.
To mark Cybersecurity Month (October 2025), Cisco Talos has published a practical guide for the general public, setting out the steps to be taken in four distinct scenarios: simply clicking on a suspicious link, entering credentials, transmitting banking information, or downloading a malicious file.
General recommendations to prevent these situations include
- always check links before clicking: hover over the link to make sure it leads to an official site; if in doubt, type in the URL manually;
- activate multi-factor authentication for all accounts when available;
- keep software and antivirus up-to-date;
- report all phishing attempts to the e-mail provider and IT/security team.
Innovative detection solutions
Faced with the rapid evolution of ClickFix, some security vendors are exploring new browser-based detection approaches to intercept these attacks before they reach the endpoint. These solutions aim to detect malicious clipboard manipulations directly in the browser environment, regardless of delivery channel or attack page structure.
This defense-in-depth approach creates an additional layer of protection upstream of traditional EDR solutions, which remain the last line of defense once the user has attempted to execute the malicious code. However, the real effectiveness of these new detection mechanisms in a variety of production environments remains to be assessed over the long term.
Organizations need to consider that defense against ClickFix requires a multi-layered strategy combining technical protections (EDR, web filtering, behavioral detection) and user awareness, rather than relying on a single solution.
A paradigm shift in cybersecurity
The emergence of ClickFix marks a pivotal moment in the history of cybersecurity, revealing the structural limits of traditional defense architectures in the face of advanced social engineering attacks. This technique demonstrates that an attack chain that is perfectly legal from a systems point of view can nonetheless completely compromise an organization, simply by exploiting the trust and conditioned reflexes of users.
ClicFix illustrates an inescapable reality: technical solutions alone are no longer enough. Signature-based detection fails in the face of attacks that involve no malicious files downloaded prior to execution. Email filters are bypassed by alternative delivery vectors. EDRs intervene too late, after the user has already initiated execution.
Faced with this threat, CERN has issued a simple but essential recommendation: “Stop, think, don’t click”. A piece of advice that sums up the critical importance of human vigilance as the first line of defense against modern social engineering attacks.
Sources:
- Microsoft Security Blog: Think before you Click(Fix): Analyzing the ClickFix social engineering technique
- ESET: ESET Threat Report H1 2025
- The Hacker News: Analysing ClickFix: 3 reasons why security controls are failing to stop it
- Ars Technica : ClickFix may be the biggest security threat your family has never heard of
- Cisco Talos: What to do when you click on a suspicious link
- Proofpoint: Security Brief: ClickFix Social Engineering Technique Floods Threat Landscape
- Push Security: The most advanced ClickFix yet?
- CERN: Computer Security: “ClickFix”, a nasty copy & paste
