Far from being simple infection vectors, Trojans play a key role in orchestrating elaborate attacks. Although Trojans are traditionally seen as infection vectors, this is a particularly simplistic view. In reality, the Trojan horse is often the prelude to a much more elaborate attack, serving as a springboard for the deployment of additional payloads, the latter being separate pieces of malware discreetly introduced into target systems. These payloads can lead to espionage, theft of sensitive data, or total control of the infected infrastructure.
Table des matières
ToggleUnderstanding Trojans
Definition and origin
The term “Trojan horse” derives from the ancient Greek stratagem used during the Trojan War, when the Greeks offered the Trojans a large wooden horse with soldiers hidden inside. This story perfectly illustrates the method of attack of modern Trojans: malware masquerading as harmless to infiltrate enemy defenses. Like their mythological namesake, digital Trojans disguise their malicious nature to penetrate computer systems and deploy their harmful payload.
Infection methods and social engineering
Cybercriminals frequently use social engineering to propagate Trojans, exploiting users’ trust or curiosity. Such malware can be disguised as seemingly legitimate email attachments(phishing), enticing free downloads or even necessary software updates. Once the user has been duped into executing the file, the Trojan activates its malicious code, performing actions ranging from spying to the extraction of sensitive data, as well as installing other malware.
Among the tools used to disseminate Trojans are binders and droppers, essential for the initial infection phase. Binders merge malicious files with legitimate ones, while droppers discreetly install the malware on the target system, without requiring additional user interaction. These techniques facilitate the malware’s entry into the system, paving the way for more elaborate malicious actions. Once the initial infection has been established, injectors and downloaders take over to deploy additional payloads, as we shall see later.
Types of Trojans and their objectives
Trojans fall into several categories, each designed with specific malicious objectives in mind. This versatile malware can cause considerable damage, from stealing confidential information to taking complete control of a system. Here’s a classification of the types of Trojans most commonly used by cybercriminals:
- Backdoor Trojan: enables the attacker to remotely access and control the infected computer, often used to integrate a network into a botnet or to install other malware.
- Banking Trojan: specially designed to steal users’ financial information, such as bank login details and credit card numbers.
- DDoS (Distributed Denial of Service) Trojan: uses the infected computer to take part in a distributed denial of service attack, overloading target servers with excessive requests.
- Downloader Trojan: downloads and installs new malware on the infected system, often without the user’s consent or knowledge.
- Trojan Exploit: contains data or code that exploits a specific vulnerability in software or operating systems.
- Spy Trojan: collects information from the infected computer, such as keystrokes, browsing history and user files, and sends it to the attacker.
- Instant messaging Trojan: steals credentials and personal data through instant messaging applications.
- Ransomware Trojan: blocks access to files or the system until the user pays a ransom to the attacker.
- Rootkit Trojan: designed to hide certain objects or activities in your system, making the malware or malicious activity undetectable by normal security software.
Each type of Trojan represents a unique threat and requires a specific approach to detection and elimination. Understanding these different categories is essential to developing effective defense strategies against Trojan attacks. Attacks orchestrated by Trojans can often be classified as Advanced Persistent Threats (APTs), which refer to targeted cyber espionage campaigns or cyber attacks, conducted over the long term and aimed at remaining undetected in order to extract maximum information or cause significant impact on the target system.

Secondary payloads, the real heart of the attack
Trojans are distinguished by their ability to deploy not just one, but often several malicious payloads within a target system. These loads, designed to perform a range of specific malicious actions, can include installing spyware, hijacking system resources for cryptocurrency mining, or deploying ransomware.
To fully understand the impact and sophistication of these attacks, it’s essential to distinguish between payloads and secondary payloads.
Payloads: the starting point
The payload acts as the initial mechanism by which the malware achieves its malicious objective, whether that be stealing data, installing spyware, or encrypting files for ransom. It is often concealed within a seemingly legitimate program, or delivered via an infected document that exploits a specific vulnerability in the target software. This payload represents the first level of attack upon successful infiltration of the system. Once the Trojan has managed to enter the system undetected, it can then download and execute the secondary payload.
Secondary payloads: the evolution of the attack
Secondary payloads take over after the initial infection, enabling cybercriminals to introduce additional malware, escalate their privileges, or further compromise the system in a discreet and targeted manner. This modular approach allows attackers to update or replace payloads without redeploying the Trojan, offering greater flexibility, evasiveness and durability against cybersecurity defenses. Deployment techniques such as encryption and polymorphism, as well as the exploitation of zero-day vulnerabilities, enable payloads to remain active and operational, even if the original infection vector is detected. It’s a method that makes these payloads particularly dangerous, as they can be adapted to suit the target environment or updated in response to the security measures put in place to counter them.
This two-stage attack strategy offers several tactical advantages:
- Flexibility: attackers can adapt their strategy to suit the target environment, choosing specific secondary payloads to maximize the impact of the attack.
- Evasion: by separating the initial infection from the execution of malicious activities, secondary payloads help bypass the detection and analysis mechanisms of security software.
- Durability: even if the initial payload is detected and removed, secondary payloads can remain active, allowing the attack to continue operating under the radar.
By deploying secondary payloads, Trojans reveal their true nature: not simple infection vectors, but sophisticated tools for cyberespionage, sabotage and information theft. This ability to orchestrate complex attacks and evolve in response to cybersecurity defenses makes secondary payloads the real heart of modern cyberattacks. Once the initial infection has been established, injectors and downloaders take over to deploy additional payloads, as we shall see later.
A striking example: Emotet and ransomware attacks
A striking example of the use of Trojans as vectors for ransomware attacks is the case ofEmotet. Initially known as a banking Trojan, Emotet has evolved into a major threat, capable of serving as a platform for the deployment of a variety of malware, including fearsome ransomwares such as Ryuk and Conti. By first infecting a system, Emotet creates a security breach that then enables the introduction of ransomware, which encrypts the victim’s data and demands a ransom for its decryption. This strategy illustrates the complexity of modern attacks, where one piece of malware can pave the way for even more devastating consequences, underlining the crucial importance of a robust and reactive IT defense. For a detailed analysis of the Emotet attack, the Varonis article offers an in-depth look.
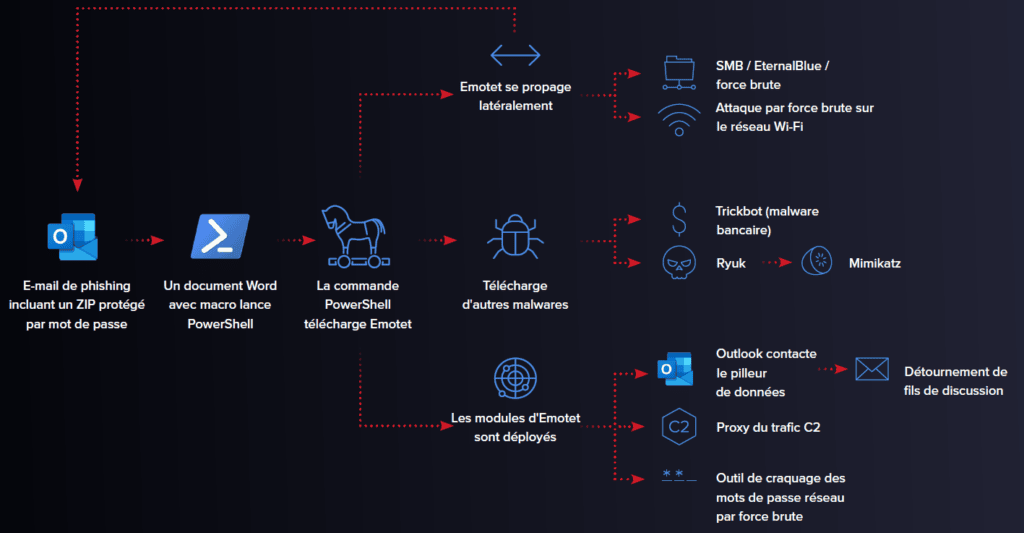
Injectors and downloaders, automated deployment tools
Mechanisms for deploying additional payloads come into play after the initial infection, and fall into two main categories: embedding and downloading.
- Injectors: these tools are designed to embed the malicious payload directly within the target system, often transforming it into an executable form to facilitate execution. Injectors can also employ advanced evasion techniques, such as polymorphism or encryption, to mask the payload and evade traditional antimalware solutions.
- Downloaders: in contrast, downloaders retrieve the secondary payload from an external source, usually via the Internet. This method has the advantage of minimizing the initial size of the malicious file and reducing the chances of generating suspicious network traffic that could alert security systems. Nevertheless, it exposes the payload to an increased risk of detection during the download process by network defenses.
These automated deployment tools play a fundamental role in the effectiveness and stealth of cyberattacks, enabling malware to adapt and react to ever-changing security environments.
Avoiding detection: a cat-and-mouse game
To remain undetected, cybercriminals are constantly innovating, turning IT security into a cat-and-mouse game. Injectors, which operate without generating any significant network traffic, effectively evade firewalls. Conversely, downloaders, despite their discretion in terms of size, run the risk of being detected by security systems as they download payloads. This dynamic forces cybersecurity professionals to constantly refine their detection methods.
The evolution of attacks and the flexibility of malware
The advent of malware-as-a-service, notably popularized by ransomware, has revolutionized the creation and distribution of custom malware. Attackers no longer need to be programming experts to carry out large-scale attacks. This has led to increased specialization and division of labor in the development of cyberattacks, making malware more flexible and difficult to detect. Common infection vectors, such as Microsoft Office documents andPDFs, are frequently exploited to disseminate injectors and downloaders, complicating the task of security solutions, which must adapt to detect these increasingly sophisticated threats.
A constantly evolving threat that’s far more sophisticated than it seems
Trojans, with their additional payloads, embody an increasingly complex and evolving component of modern cyberattacks. A thorough understanding of how they work, from infection tactics to evasion of defenses, is essential to developing robust defense strategies. In the face of continuous innovation by cybercriminals, cybersecurity must be proactive, requiring constant vigilance and adaptation on the part of experts and users alike. Staying informed and reactive to new methods of attack is essential to preserving the security of our digital environment.
For the latest malware trends, check out Checkpoint’s December 2023 report on the most prevalent malware activity here.
