Gone are the days when ransomware simply encrypted data for ransom. For several years now, cybercriminals have been transforming their business model by adding a critical step:data exfiltration prior to encryption, in order to increase their bargaining power and chances of obtaining payment. Double extortion now represents the norm in the ransomware ecosystem, transforming what was once a purely technical threat into a genuine organizational crisis involving major legal, reputational and financial stakes. This new approach is fundamentally redefining the nature of the ransomware threat and the defensive strategies needed to deal with it.
Table des matières
ToggleWhat is double extortion?
Double extortion represents a major tactical evolution in the ransomware landscape. In this attack scheme, cybercriminals no longer limit themselves to encrypting their victims’ data: they also exfiltrate a copy of the sensitive information before deploying the ransomware. This gives them double the leverage. The victim is thus faced with two simultaneous threats: paying to regain access to his encrypted data, and paying to prevent public disclosure of his confidential information.
This tactic effectively neutralizes one of the main defenses against traditional ransomware: backups. Even if an organization can restore its systems from backup copies, it remains exposed to the risk of having its sensitive data published on the dark web or sold to the highest bidder. The blackmail of disclosure then becomes as formidable, if not more so, than encryption itself.
Origins and history of double extortion
The beginnings with the Maze group
The first documented case of double extortion dates back to November 2019, when the Maze crime group targeted Allied Universal, a major US security services company. When the victim refused to pay the ransom of 300 bitcoins (around $2.3 million at the time), the attackers threatened to use information extracted from Allied Universal’s systems, as well as stolen email and domain certificates, to run a spam campaign impersonating the company.
To prove the validity of their threat, Maze ‘s operators disclosed 700 MB of stolen data, representing just 10% of what they claimed to hold, including contracts, medical records and encryption certificates. They then increased their demands by 50% over the initial request. This attack established a new paradigm in the ransomware ecosystem.
The creation of the first leaks site
The Maze group pioneered the creation of a leaks site, publicly listing the identities of uncooperative victims and regularly publishing samples of the stolen data. This digital wall of shame has become a formidable psychological pressure tool, transforming a technical attack into a public reputational crisis.
Massive adoption by the criminal ecosystem
Following the success of this approach, other criminal groups quickly adopted the double extortion tactic. REvil (also known as Sodinokibi) began publishing its victims’ data at around the same time as Maze. The DoppelPaymer, Clop, and later LockBit groups followed, creating their own leaks sites to put further pressure on their targets.
According to Arctic Wolf data, 96% of ransomware incident response cases now involve data exfiltration in addition to encryption, confirming that double extortion has become the norm rather than the exception.
Leaks sites: the digital wall of shame
Anatomy of a leaks site
Leaks sites represent a central element of the double extortion strategy. Usually hosted on the Tor network via .onion addresses, these platforms enable ransomware groups to name and publicly expose their victims. When an organization refuses to pay the ransom, the attackers list it on their site, disclose a sample of the exfiltrated data and often set up a public countdown to the full release of the information.
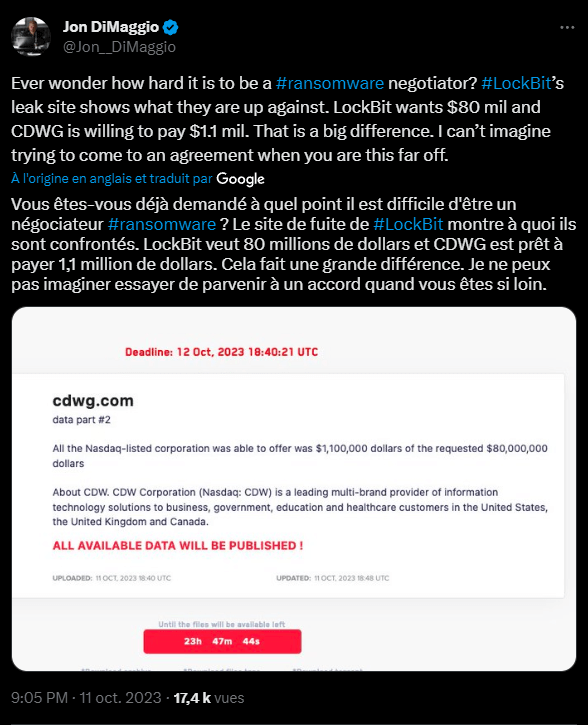
This calculated use of reputational damage is a highly effective pressure tactic, designed to force legal teams and executives to negotiate quickly. The leaks site turns a technical incident into a public relations crisis, requiring a coordinated response involving security, legal and senior management teams.
Unprecedented proliferation
The proliferation of leaks sites is expanding significantly. According to Allan Liska, Threat Intelligence Analyst at Recorded Future, in 2024, over 56 new leaks sites were identified, more than double the number identified the previous Recorded Future year. The number of victims posted on these platforms has increased considerably: in the first half of 2025, over 3,700 victims were listed, representing a 67% increase on the same period the previous year.
Evolving publication tactics
Different ransomware groups employ a variety of strategies on their leaks sites. Some publish data incrementally, others make full disclosures. Re-extortion tactics have also been observed: a malicious actor posing as a rebranding of the Babuk group attempted to re-extort over 60 victims using data from previous extortion campaigns already solved.
Triple extortion and beyond
Definition of triple extortion
Triple extortion adds an extra layer of pressure to double extortion tactics. Attackers can employ a variety of additional methods to induce their victims to pay:
- contact and potentially blackmail individuals whose data has been exfiltrated during the attack ;
- launch distributed denial-of-service (DDoS) attacks against the victim’s infrastructure;
- target the business partners, customers or suppliers of the organization initially compromised;
- contact the media directly to amplify public pressure.
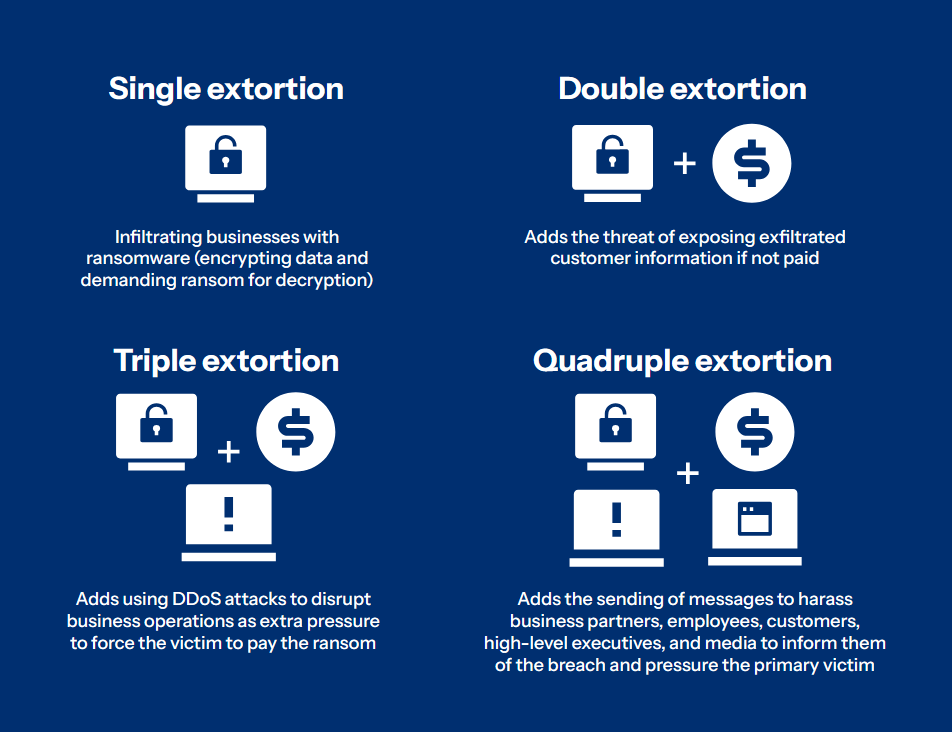
Quadruple extortion
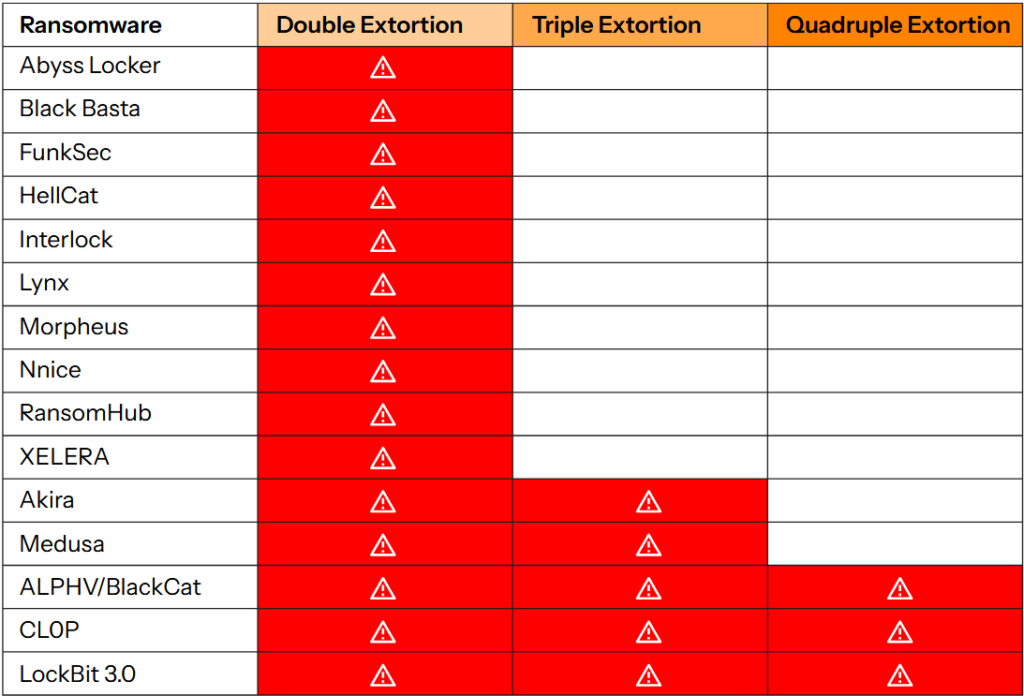
Some groups go even further with quadruple extortion, adding an extra dimension to their tactics. The attack on Change Healthcare in February 2024 is a prominent example: after an initial BlackCat/ALPHV attack compromised the healthcare information of almost 193 million people – the largest healthcare data breach ever recorded in the USA – the RansomHub group attempted a second extortion in April 2024 despite paying a ransom of $22 million. In what amounts to an exit scam, BlackCat’s operators disappeared with the funds in March 2024 without honoring their promise to return the data or share the ransom with their affiliates, leaving the field clear for RansomHub to exploit the stolen data once again. The total financial impact of this incident is estimated at over $2.4 billion.
Evolution of ransomware extortion tactics
| Extortion tactics | Traditional ransomware | Double extortion | Triple extortion | Quadruple extortion |
|---|---|---|---|---|
| Data encryption | ✅ Encrypts files on the victim’s system | ✅ Encrypts files on victim’s system | ✅ Encrypts files on victim’s system | ✅ Encrypts files on victim’s system |
| Exfiltration and leak threat | ❌ | ✅ Exfiltrates data and threatens to publish it if the ransom is not paid | ✅ Exfiltrates data and threatens to publish it if ransom is not paid | ✅ Exfiltrates data and threatens to publish it if the ransom is not paid |
| DDoS attack | ❌ | ❌ | ✅ Threatens to disrupt operations with DDoS attacks | ✅ Threat to disrupt operations through DDoS attacks |
| Customer/partner contact | ❌ | ❌ | ❌ | ✅ Threat to contact customers, suppliers and partners to disclose the breach |
Increasing impact: Each additional level of extortion significantly increases the pressure on victims and reduces the effectiveness of traditional protective measures such as backups.
Recent examples of multi-extortion
The Qilin group is a prime example of the trend towards increasingly aggressive tactics. In 2024, its attack on Synnovis, a UK NHS pathology service provider, led to a record ransom demand of $50 million. When the company refused to pay, the group published the stolen data of around 900,000 people on the dark web. The financial impact for Synnovis is estimated at £33 million, demonstrating that refusing to pay does not eliminate the economic consequences. With over 700 victims recorded in 2025 across 62 countries, Qilin has established itself as one of the most active RaaS operations.
Play, identified by CISA as one of the most active ransomware groups, employs a double extortion model combined with direct phone calls to victims to encourage them to pay and threaten to divulge their information.
This new era of ransomware is also characterized by collaborations between specialized groups. Scattered Spider, part of the Scattered LAPSUS$ Hunters alliance, excels in initial access via advanced social engineering (vishing, SIM swapping, helpdesk manipulation). The group has historically acted as an affiliate of several major RaaS programs, including ALPHV/BlackCat, Qilin, RansomHub and DragonForce. The latter, which positions itself as a “ransomware cartel” offering a white-label model to its affiliates, attempted to reclaim RansomHub’s affiliates after the group’s demise in April 2025. This role specialization – where some groups manage the initial intrusion while others provide the encryption and extortion infrastructure – maximizes the efficiency of criminal operations.
Extortion without encryption: the new trend
A paradigm shift
A substantial evolution has been confirmed in recent years: some criminal groups are now abandoning encryption in favor of extortion based solely on data theft. According to Sophos’s State of Ransomware 2025 report, the encryption rate has fallen to its lowest level in six years, from 70% in 2024 to 50% in 2025. At the same time, the proportion of extortion attacks without encryption has doubled, from 3% in 2024 to 6% in 2025.
This approach offers several advantages for attackers. Developing ransomware capable of bypassing modern security solutions requires time and advanced technical skills. By focusing solely on exfiltration, criminal groups can operate more quickly and opportunistically. What’s more, 97% of organizations whose data has been encrypted are now able to recover it, making encryption less effective as a pressure lever.
Nevertheless, double extortion remains a major tactic: 28% of organizations that have suffered data encryption have also been victims of data theft, representing 14% of all ransomware victims. This development is accompanied by differentiated targeting: small organizations (100-250 employees) are particularly vulnerable to extortion attacks without encryption (13% of them), compared with just 3% of large companies.

Groups practicing extortion without encryption
Several groups have adopted this exclusive or partial approach. World Leaks, formed from the dissolution of Hunters International in November 2024, has been practicing pure extortion without encryption since January 2025. RansomHub has also been observed employing this tactic occasionally, as have emerging groups such as Weyhro. The Cl0p group , specialized in the industrial exploitation of zero-day vulnerabilities affecting massively deployed enterprise platforms, systematically favors exfiltration over encryption. After MOVEit Transfer in 2023 (more than 2,700 organizations affected), its sixth major campaign targets Oracle E-Business Suite, with around a hundred victims already confirmed.
Anatomy of a double extortion attack
Attackers gain access to the victim’s network using a variety of methods:
- phishing remains one of the most common vectors, with emails designed to trick the user into clicking on a malicious link or downloading an infected file. A particularly worrying development is the rise of the ClickFix technique, which encourages victims to execute malicious commands themselves. Some ransomware groups, notably Interlock, now use FileFix, an even more sophisticated variant that exploits Windows File Explorer and bypasses system protections;
- exploiting unpatched vulnerabilities in systems exposed on the Internet;
- the use of compromised credentials, sometimes obtained through previous data leaks or brute force attacks;
- exploitation of insecure remote access services, such as Remote Desktop Protocol (RDP) or VPN.
According to Arctic Wolf, almost 60% of observed ransomware attacks exploit external remote access to gain initial access, often via compromised credentials enabling entry into the environment via an insecure VPN or RDP.
Phase 2: Lateral movement and elevation of privileges
Once initial access has been gained, attackers move laterally across the network to identify and access as many valuable resources as possible. This phase usually includes elevation of privileges to gain administrator rights over the entire infrastructure. Attackers use legitimate tools present on the systems (the “living-off-the-land” technique) to avoid detection.
Phase 3: Data reconnaissance and exfiltration
Attackers scan the network to identify high-value data: personally identifiable information (PII), financial data, intellectual property, trade secrets, health data and so on. This data is then exfiltrated to external servers controlled by the criminals, often using tools such as Rclone or transferring it to cloud services.
Phase 4: Encryption and ransom demand
The ransomware payload is deployed to encrypt critical systems. A ransom note is then presented, indicating the amount demanded and threatening to divulge the stolen data in the event of non-payment. Operations have become faster, with negotiations often starting just hours after data exfiltration.

The consequences of double extortion
Regulatory and legal impact
A double extortion attack involving the exfiltration of personal data triggers strict notification obligations in many jurisdictions. The extent of these obligations varies by region:
In Europe (RGPD): the loss of control over personal data means that the individuals concerned have lost the protections and rights guaranteed to them. Payment of ransom is not considered an appropriate remedy by regulatory authorities. Organizations face fines of up to 20 million euros or 4% of annual worldwide sales.
In the USA (HIPAA): for the healthcare sector, a ransomware attack is presumed to constitute a data breach requiring notification, unless the entity can demonstrate a low probability of compromise of protected health information (PHI). Notifications must be made within 60 days, with an obligation to inform affected individuals, HHS (Department of Health and Human Services) and the media if more than 500 people are affected. Fines can reach $50,000 per violation, with an annual maximum of $1.5 million per category of violation.
In California (CCPA/CPRA): companies must notify affected California residents and the State Attorney General if more than 500 residents are affected. Penalties can reach $7,500 per intentional violation. Victims can also exercise a private right of action to claim damages.
Cybercriminals consciously exploit this regulatory pressure in their negotiation tactics, knowing that potential fines can exceed the amount of ransom demanded.
Reputational damage
Publishing stolen data on a leaks site can cause irreparable damage to an organization’s reputation. The exposure of confidential information, be it customer data, trade secrets or sensitive internal communications, erodes the trust of stakeholders and can have a lasting impact on brand image.
Operational and financial consequences
The attack on CDK Global in June 2024 illustrates the scale of possible operational disruption: this automotive dealership software provider saw its incident affect over 10,000 dealerships in North America, resulting in collective losses estimated at $1 billion. The attack on Starbucks via its supplier Blue Yonder disrupted the planning and payroll systems of 11,000 stores.
No guarantee of data recovery or deletion
Paying a ransom offers no guarantee of data recovery or deletion by the attackers. Recent data speaks for itself: in 2024, although 84% of victims paid a ransom, only 47% recovered their uncorrupted data. Even more worryingly, according to the Cybereason study “Ransomware: The True Cost to Business 2024”, 78% of organizations attacked in 2023 fell victim to a new attack in 2024, 63% of which faced higher ransom demands in the second attack, of which 36% were targeted by the same criminal group.

Legislative developments: towards a ban on payments
The UK took a decisive step in July 2025 by confirming a ban on ransom payments for the public sector and operators of critical national infrastructure. This measure, supported by 72% of respondents to the public consultation, will apply to the NHS, local authorities, schools and companies operating in critical sectors such as energy, transport and telecommunications.
The UK legislation also includes:
- a payment prevention regime requiring private organizations to notify the authorities prior to any payment ;
- a requirement to report any ransomware incident within 72 hours, followed by a full report within 28 days.
This approach aims to hit cybercriminals’ business model by making public sector targets less attractive. The UK thus becomes the first Western country to impose a legal ban on ransomware payments for the public sector and critical infrastructure, potentially paving the way for similar measures in other jurisdictions.
A worldwide downward trend in payments
Despite the increase in the volume of attacks, ransom payments fell by 35% in 2024, to around $813 million compared with $1.25 billion in 2023. The rate of refusal to pay has increased significantly: 63% of victims now refuse to pay, compared with 41% the previous year. This trend reflects organizations’ improved restoration capabilities and a growing awareness that payment does not guarantee a successful outcome.
Protecting against double extortion
Defending against double extortion attacks requires a multi-layered approach combining prevention, detection and response capabilities.
Access management and authentication
The majority of ransomware attacks exploit compromised remote access to penetrate networks. Implementing phishing-resistant multi-factor authentication (MFA) on all remote access services (VPN, RDP) is a fundamental protection. The attack on Change Healthcare was made possible by exploiting a Citrix portal without multi-factor authentication.
Vulnerability management
The exploitation of unpatched vulnerabilities represents a major intrusion vector. Vulnerabilities such as those affecting Cleo (CVE-2024-50623) or Atlassian Confluence servers (CVE-2023-22527) have been massively exploited for double extortion attacks. An effective vulnerability management program, prioritizing the rapid correction of critical vulnerabilities, is essential.
Detecting data exfiltration
Data exfiltration usually precedes ransomware deployment and forms the very basis of double extortion. Organizations need to invest in network monitoring, data loss prevention (DLP) and anomaly detection solutions to identify unusual transfers. In particular, monitoring should detect the installation of suspicious applications such as Rclone, frequently used to exfiltrate data.
Continuous monitoring and response
A 24/7 monitoring, detection and response capability is essential to identify suspicious behavior and rapidly contain threats. In 2024, 56% of organizations under attack did not detect the compromise for 3 to 12 months, illustrating the lack of visibility that enables attackers to exfiltrate data over long periods.
Backups and continuity planning
Although exfiltration can still occur, having regular, tested backups in place helps organizations resume operations in the event of an attack. Only 54% of victims who suffered encryption in 2025 were able to restore their data via backups, the lowest rate in six years, underlining the importance of regularly testing restoration procedures.
Network segmentation
Network segmentation limits the ability of attackers to move laterally once initial access has been gained. This approach, central to Zero Trust architectures, reduces the attack surface and contains propagation in the event of initial compromise, thus limiting the volume of potentially exfiltrable data.
Preparing for crisis management
Regular tabletop exercises enable teams to practice responding to double extortion attacks in a controlled environment. These exercises clarify roles and responsibilities and identify gaps in the response strategy. Management involvement is essential to integrate cybersecurity into the organizational culture.
Conclusion
Double extortion represents a major and lasting evolution in the ransomware threat. By combining data encryption with theft and the threat of disclosure, cybercriminals have neutralized traditional defenses based solely on backups. This reality is forcing organizations to rethink their approach to cybersecurity, incorporating exfiltration prevention as a priority alongside encryption protection.
Faced with attackers who continue to innovate, moving from double to triple extortion, or even extortion without encryption, organizational resilience becomes an imperative. Regulatory developments, notably the UK’s ban on ransomware payments, signal a growing awareness on the part of public authorities, and could transform the ransomware economy for good. The combination of early detection, rapid response, data loss prevention and close collaboration between IT, legal and management teams is the bedrock of an effective defense against this ever-evolving threat.
Sources :
- Akamai: Ransomware Report 2025
- Sophos: The State of Ransomware 2025
- Tech Target: What is double extortion ransomware?
- Arctic Wolf: The Dangers of Double and Triple Extortion in Ransomware Attacks
- Unit 42: What is Multi-Extortion Ransomware?
- Chainalysis Team: 5% Year-over-Year Decrease in Ransomware Payments, Less than Half of Recorded Incidents Resulted in Victim Payments
- Bleeping Computer: Ban on ransomware ransom payments in the United Kingdom
