January 2025 saw a dynamic shift in ransomware activity, characterized by the resurgence of established ransomware groups, the emergence of new players and increasingly sophisticated attack methods.
Indeed, for the month of January, around 500 victims were reported worldwide, a staggering year-on-year increase compared to January 2024.
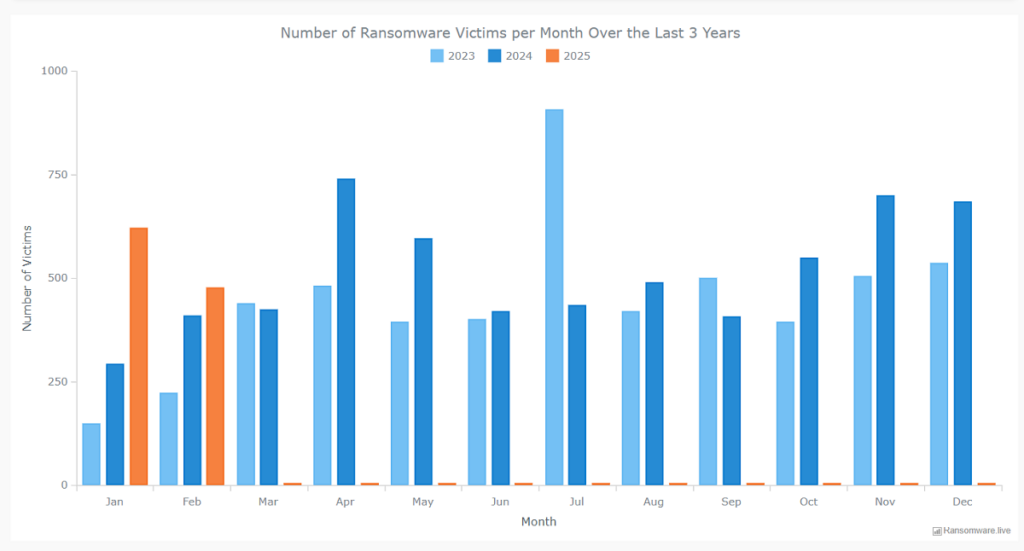
We provide an approximate value, as figures vary from one source to another, a new strategy adopted by hacker groups is to sometimes report attacks that have not taken place, and the exact chronology is often difficult to implement, from one month to the next…
Ransomware continues to exploit vulnerabilities in all business sectors and geographical areas.
Indeed, MagIT headlined its report at the start of the year with an evocative phrase: “Ransomware: an unusually violent start to the year“.
The industrial sector remains a prime target due to the high value of its data and its operational criticality, while the IT and healthcare sectors have seen alarming peaks in attacks.
This ranking analyzes the ten most active ransomware groups of the month, the evolution of their tactics and the need for companies to adopt proactive defense strategies.
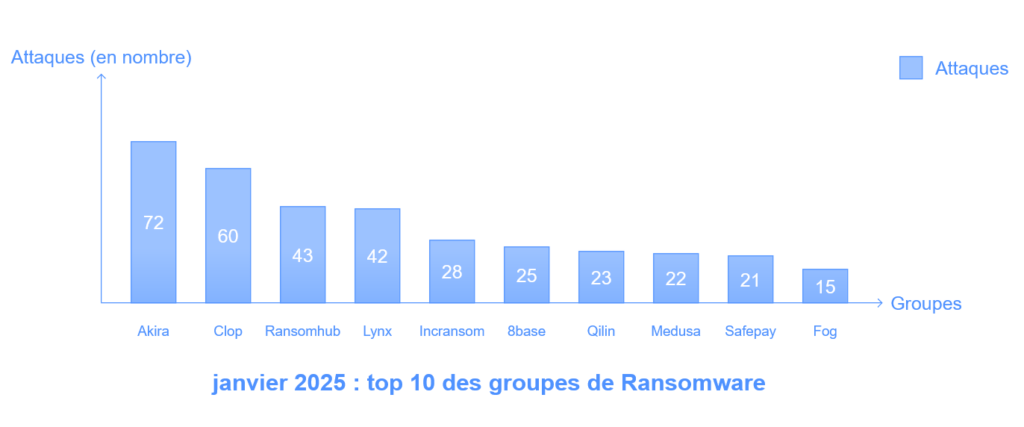
Table des matières
ToggleRanking of groups by number of ransomware attacks
Akira: 72 attacks
Akira ransomware began operations in March 2023. The operator stood out thanks to a retro aesthetic used on its Data Leak Site and in its messages.
The group uses several extortion methods and runs a .onion website, where it displays victims and all stolen data when they don’t comply with its ransom demands. Victims must then contact the attacker via this TOR portal by entering a unique identifier indicated in the ransom note to begin negotiations.
This group has a reputation for demanding exorbitant ransom sums, up to several hundred million dollars.
Akira, like Fog, is actively exploiting the CVE-2024-40711 flaw, which endangers Veeam Backup & Replication (VBR) servers.
Cl0p: 60 attacks
The CL0P ransomware appeared in early 2019 and is linked to the TA505 threat group.
Active until at least January 2022, it made a name for itself with high-profile attacks targeting major corporations.
Its malicious payloads, often digitally signed, incorporate various mechanisms to evade analysis. Some versions of CL0P are designed not to run on Russian-language systems.
Like Maze and NetWalker, the authors of CL0P have been publishing their victims’ stolen data on a Data Leak Site since early 2020.
In 2024, CL0P massively exploited vulnerabilities in Cleo’s product range (LexiCom, VLTrader, Cleo Harmony), affecting around ten victims in a supply chain-style attack, resulting in significant data leaks on their dedicated site.

Ransomhub: 43 attacks
RansomHub ‘s activities were first observed in February 2024.
Since then, the group has largely leveraged its ability to attract operators from other troubled extortion operations, such as during the collapse of ALPHV, which saw several affiliates join RansomHub to monetize their stolen data.
RansomHub is linked to the re-extortion of ransomware victims, including large organizations and notably from the healthcare sector. RansomHub’s main leaders openly recruit affiliates from other groups via various communication channels, such as DLS sites, forums and Telegram.
Lynx: 42 attacks
The Lynx ransomware represents a new and highly sophisticated cyber threat. It has been active since mid-2024.
The result of a requalification and enhancement of the earlier INC ransomware, Lynx is built on INC’s source code, establishing a direct filiation between the two.
Operating in Ransomware-as-a-Service (RaaS) mode, it combines a dual extortion strategy with advanced encryption, depriving victims not only of access to their systems, but also exposing them to the disclosure of their stolen data if the ransom is not paid. The group primarily targets Windows environments, adding the .lynx extension to encrypted files and systematically deleting clone copies to hinder recovery.
The danger lies in its customizability, enabling affiliates to precisely parameterize the files and directories to be encrypted via command-line arguments.
Inc. ransom: 28 attacks
Inc. ransomware appeared in July 2023 as an extortion operation. Its operators position themselves as a genuine service to their victims, who can pay the ransom to “preserve their reputation”.
Indeed, the attackers threaten to reveal their methods, which they claim would make the victim’s environment “more secure”. Inc. is a multiple extortion operation characterized by the theft of sensitive data and the threat to broadcast it online if demands are not met.
Operators target a wide range of industries without discrimination, including healthcare, education and government entities.
8base: 25 attacks
The 8base operation’s showcase site was confiscated as part of an international investigation involving the Paris Prefecture’s cybercrime squad.
Recognized since the spring of 2022, 8base has claimed more than 450 victims – including the Belgian commune of Heron, attacked at the end of January – as well as around 30 in France.
Last autumn, the company caused a stir when it claimed responsibility for an attack on Volkswagen, which confirmed that it had been informed of an incident that had not compromised its IT infrastructure.

Agenda (Quilin): 23 attacks
Discovered in July 2022, Agenda – also known as Qilin – is written in Golang and offers several encryption modes, fully configurable by the operator. Its actors practice double extortion, demanding payment both for the decryptor and to prevent disclosure of the stolen data. This ransomware mainly attacks large corporations and high-value targets, with a particular focus on the healthcare and education sectors in Africa and Asia.
Agenda infects its victims via phishing and spear phishing campaigns, and exploits exposed applications and interfaces, such as Citrix or the remote desktop protocol. The ransomware offers advanced customization options, such as modifying encrypted file extensions or selecting processes and services to be interrupted. It supports several encryption modes – “skip-step”, “percent” and “fast” – which the operator can choose via the integrated help screen.
Medusa: 22 attacks
Medusa is a ransomware-as-a-service (RaaS) platform that first appeared in June 2021 and quickly became popular among cybercriminals. Unlike many ransomware groups that operate solely on the dark web, Medusa has opted for a dual-platform approach by maintaining an active presence on the surface web, enabling it to reach a wider audience and attract more affiliates.
Since 2023, Medusa has steadily increased the number of its victims. It’s important to note that Medusa is distinct from MedusaLocker, another RaaS variant active since 2019.
Medusa’s operations are global in scope, targeting a wide range of industries, including healthcare, education, manufacturing and retail, with a particular focus on organizations in the USA, Europe and Africa.

Safepay: 21 attacks
The SafePay ransomware group is an emerging cybercriminal entity that attracted attention in 2024 for its sophisticated and rapid attacks. First identified by analysts in October 2024, SafePay stands out for its ability to deploy ransomware in less than 24 hours after initial access, well below the industry average of several days.
The group uses advanced techniques, including modifications to domain controller registries to encrypt systems, and relies on a code base derived from the LockBit ransomware (leaked in 2022), suggesting a potential connection with experienced operators.
SafePay also practices double extortion, stealing data before encrypting it and threatening to publish it if the ransom is not paid, a common tactic among modern groups.
Probably operating from Eastern Europe, as suggested by a “kill switch” that interrupts attacks on systems using Cyrillic characters, SafePay has already claimed numerous victims worldwide, including in Australia, the UK and the USA.
Notable targets include Snow Brand Australia, Microlise in the UK and the Starkville School District in the USA, with data thefts of up to 1.2 terabytes in some cases.
Despite its novelty, the group shows a methodical organization, using valid credentials to access networks via VPNs and disabling defenses such as Windows Defender before striking. Its rapid rise and aggressiveness underline the growing threat of ransomware in today’s cybersecurity landscape.
Fog: 15 attacks
The Fog ransomware is a cybercriminal threat that emerged in May 2024, initially targeting the education and entertainment sectors in the USA, before spreading to industries such as finance. It exploits compromised VPN credentials, often via vulnerabilities such as CVE-2024-40766 in SonicWall devices, to penetrate networks.
Once inside, Fog deploys its ransomware quickly – sometimes in less than two hours – using techniques like pass-the-hash to escalate its privileges, while stealing data for double extortion.
Probably based in Eastern Europe, Fog disables defenses such as Windows Defender before encrypting files, adding .FOG or .FLOCKED extensions. Its attacks, which include the use of legitimate tools such as AnyDesk, have targeted a variety of organizations, with Bitcoin ransoms ranging from thousands to millions of dollars. Again, the group publishes the stolen data on its darknet site if victims refuse to pay.
FunkSec the ransomware that makes massive use of AI
A new type of threat at the start of this year is the FunkSec ransomware, which appeared at the end of 2024.
This unprecedented threat is shaking up the world of cybersecurity due to its intensive use of artificial intelligence to design its malicious tools.
According to the experts at Check Point Research, this group has already claimed 85 victims by December 2024, mainly in the USA, India and Brazil, exploiting a ransomware-in-tant-que-service (RaaS) model.
Its distinctive feature lies in its ability to rapidly generate malware using AI, notably via the Miniapps platform to create malicious chatbots, making it both accessible and frighteningly effective.
FunkSec also stands out for its low-cost double extortion strategy, with ransoms sometimes limited to $10,000, coupled with the resale of stolen data at low prices on the dark web.
Although its code is still technically basic, the comments in perfect English betray an AI assistance, worrying experts with its evolutionary potential. Oscillating between hacktivism and cybercrime, FunkSec illustrates a new era of threats where AI democratizes and accelerates attacks, making specialists tremble in the face of this meteoric rise in power.
Other cybercrime highlights for January 2025
In France and Switzerland, numerous institutions were targeted by massive DDoS attacks from the pro-Russian group NoName057(16), opposed to support for Ukraine and the World Economic Forum (WEF). In France, local authorities saw their websites paralyzed in late 2024 and early 2025, while in Switzerland, communes and banks were affected in January 2025 during the WEF (Wold Economic Forum).
These attacks, claimed on Telegram, aim to disrupt digital infrastructures in response to the pro-Western stances of both countries. Although they do not steal data, they highlight the growing threat of this hacktivist group, which has been active since 2022, using tools such as DDosia to mobilize its supporters.
Statistical sources for the article:
Ransomfeed.it
