Table des matières
ToggleA surprise attack on one of the most powerful cybercrime groups
In a stunning turn of events, the LockBit ransomware group, long considered a formidable force in the world of cybercrime, has fallen victim to a major hack.
On April 29, 2025, data from its affiliated administration interface was extracted and published publicly – on its own websites. The irony is both cruel and eloquent: even those involved in digital crime are not immune to their own methods.
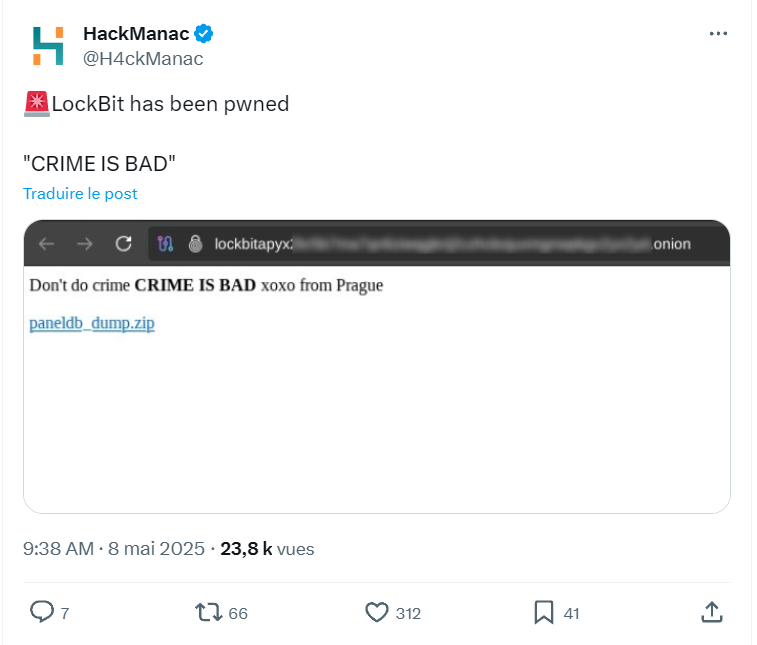
The incident has shed light on an entire section of the LockBit ecosystem, previously opaque to cybersecurity researchers.
This is not the first time the gang has suffered setbacks: in May 2024, for example, international law enforcement agencies conducted Operation Cronos , resulting in the arrest of several key members, including Dmitry Yuryevich Khoroshev, the alleged operator behind the LockBitSupp pseudonym.
But this latest leak, far more than a mere camouflet, could have far-reaching consequences both for the group’s internal organization and for our understanding of the tactics used by ransomware-as-a-service (RaaS).

An unprecedented window on the inside of a criminal empire
Data revealing opaque practices
The exposed SQL database contains edifying information: over 75 affiliated accounts, thousands of conversations with victims, 60,000 Bitcoin addresses, and even passwords stored in clear text (‘Weekendlover69, ‘MovingBricks69420’, and ‘Lockbitproud231’).
For open intelligence specialists, this treasure trove represents a rare opportunity to analyze in detail the inner workings of a structured criminal network.
Among the most striking features: a delay of up to ten days between data exfiltration and final encryption. This underlines the growing importance of detecting lateral movements and data transfers before a ransom demand is launched.
A complex but vulnerable RaaS model
LockBit is based on a franchise model: a central core develops the tools, while affiliates execute the attacks.
Of the 75 accounts identified, only 44 were active, and even fewer engaged in offensive operations at the time of the leak.
Only seven appeared to be running campaigns in real time. This hierarchical structure, although profitable, shows its limits when the security of the central core is compromised.
Furthermore, discussions between negotiators and victims revealed a worrying trend: ransom demands often hover around $20,000, or even less, with a marked preference for Monero, often offered at a 20% discount against immediate payment.
This choice reflects a growing desire for anonymity, in response to the authorities’ increasing efforts to trace cryptographic flows.
Game-changing target geography
Asia-Pacific at the heart of operations
Contrary to popular belief, it’ s not Europe or North America that mainly attracts LockBit affiliates, but the Asia-Pacific region, accounting for 35.5% of targets.
China leads the way with 51 identified victims, followed by Indonesia (49) and India (35). This regional focus suggests that threats are underestimated in these countries, where cybersecurity is sometimes less mature or less publicized.
Some affiliates, such as PiotrBond or Umarbishop47 , concentrate over 75% of their attacks in this zone, illustrating a strategic segmentation.
Conversely, South Korea seems to be under-represented in the data, without it being possible to identify the exact reason.
source : computerweekly.com
An asymmetrical targeting strategy
The data also reveal an intriguing phenomenon: the most active affiliates do not necessarily target the most lucrative victims.
Many target smaller organizations located in middle-income countries around the world. This shift in strategy may be explained by a decline in the availability of talent following the arrests associated withOperation Cronos , or by a desire to minimize geopolitical pressures by avoiding major economies.

What this reveals about the resilience of ransomware groups
A weakened but not extinct system
Despite the blows dealt by law enforcement and this embarrassing leak, LockBit is trying to maintain its presence.
In December 2024, the group teased its imminent return in February 2025. A few months later, while some claim to see the gang’s decline, others remain vigilant: the ransomware ecosystem is highly adaptable, and new groups like SuperBlack already look set to take over.
Lessons for defense
Cybersecurity experts are drawing several operational lessons from this leak:
- Prioritize patching : Dozens of critical CVEs have been exploited by LockBit in recent years, including CVE-2023-4966 (Citrix), CVE-2022-22965 (VMware), CVE-2021-44228 (Log4j). Correcting them quickly is essential.
- Protect forgotten systems : Backup solutions(such as Veeam), VMware ESXi hypervisors, NAS and administrative tools (FileZilla, WinSCP) are now among cybercriminals’ favorite targets.
- Monitor data leaks : The period between exfiltration and encryption offers a critical window of opportunity to intervene before the damage is irreversible.
Conclusion: A wake-up call for all cybersecurity players
The LockBit compromise illustrates the extent to which even the most organized criminal structures can be affected by their own cybersecurity shortcomings. It also serves as a reminder of the importance of international collaboration, forensic investigations and offensive research in countering the persistent threat of ransomware.
For businesses, this textbook case should serve as a catalyst: it’s imperative to reinforce defense postures, anticipate the entry points exploited by cybercriminals, and understand that the threat never sleeps – even when it appears to be wavering.
In the event of an incident, our ransomware data recovery service is at your disposal 24/7.
