Table des matières
ToggleA major international alert
On November 13, 2025, an unprecedented coalition of international cybersecurity agencies issued a joint alert update on the Akira ransomware.
This update of information and advice for IT network managers, issued by the FBI, CISA (Cybersecurity and Infrastructure Security Agency), DC3 (Department of Defense Cyber Crime Center), HHS (Department of Health and Human Services), as well as Europol, the French Anti-Cybercrime Office (OFAC), German authorities and the Dutch NCSC, highlights the alarming level of risk assessed by these agencies.
The announcement comes as the Akira group continues to intensify its operations on a global scale. Its attack techniques are becoming increasingly sophisticated, and the speed of execution is a major concern for experts.
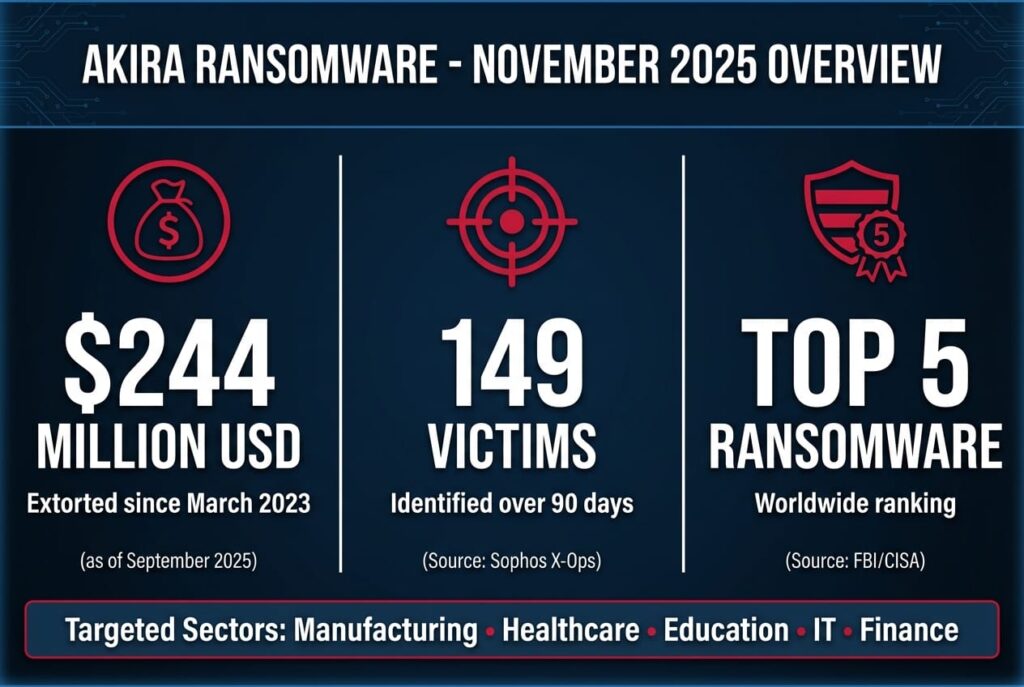
According to the latest FBI estimates from the end of September 2025, the Akira group has extorted around $244.17 million in ransomware since its first appearance in March 2023, making Akira one of the five most active ransomware groups among the 130 identified variants targeting the U.S.(Cybersecuritydive)
To nuance this picture, Coretelligent ‘s data nevertheless reveals a notable shift in the ransomware landscape: only 25% of victims now agree to pay, the lowest rate seen in three years. To counter this growing resistance, malicious actors are therefore increasingly relying on the theft of sensitive data as extortion leverage, threatening to publish the information on their leak site hosted on the Tor network.
42 days of silent intrusion: anatomy of a devastating attack
A detailed analysis published by Palo Alto Networks’Unit 42 on November 18, 2025 sheds light on the evolution of Akira’s methods. The incident concerns a global data storage and infrastructure company, victim of an attack orchestrated by Howling Scorpius, the group that distributes the Akira ransomware. What began with a simple click on what appeared to be a routine CAPTCHA check turned into 42 days of compromise that exposed critical flaws in the organization’s security posture.
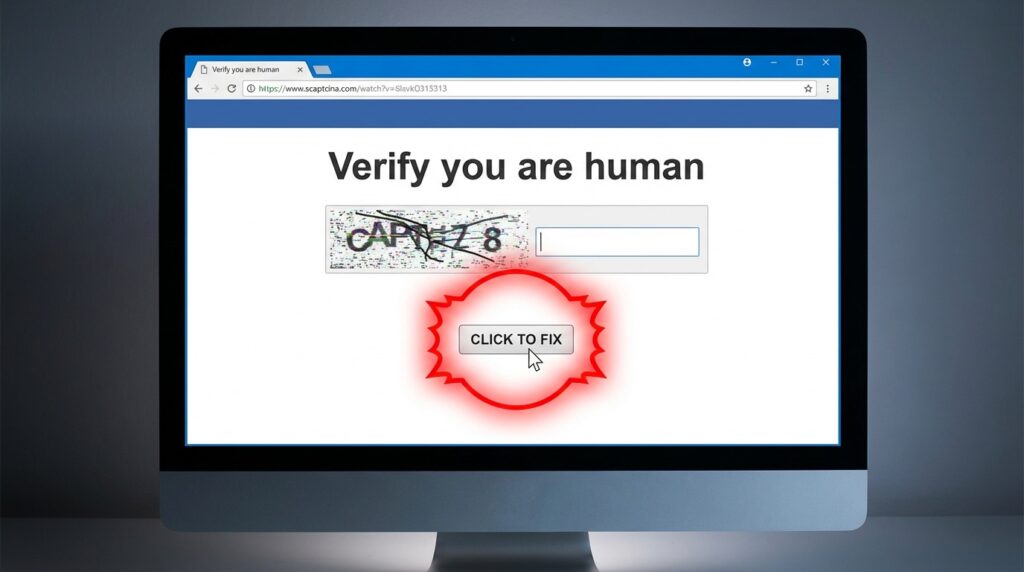
The attack began when an employee visited a compromised car dealership website. What looked like a standard anti-bot check, the familiar “click to prove you’re human”, was actually a social engineering tactic called ClickFix. This technique disguises malware delivery as a legitimate security check, fooling users into thinking they’re simply verifying their identity when they’re actually downloading a malicious payload.
When the employee interacted with the fake CAPTCHA, he unwittingly downloaded the SectopRAT malware, a .NET-based remote access Trojan that allows attackers to mask their code. This malware offers cybercriminals the ability to remotely control an infected system, monitor activity, steal data and execute commands in stealth mode. From this initial beachhead, the group established a backdoor on a server for command and control before performing reconnaissance to map the virtual infrastructure.
The attackers compromised several privileged accounts, including domain administrators, and moved laterally using the RDP (Remote Desktop Protocol), SSH (Secure Shell) and SMB (Server Message Block) protocols. Over 42 days, the malicious actors accessed domain controllers and prepared massive data archives using WinRAR on multiple file shares. They pivoted from a business unit domain to the enterprise environment and finally to cloud resources, crossing boundaries that should have contained them.
Before deploying the ransomware, they deleted the cloud provider’s storage containers that held backups and compute resources, then exfiltrated nearly 1 TB of data using FileZillaPortable. Next, they deployed the Akira ransomware on servers in three separate networks. The virtual machines shut down, operations stopped and the ransom demand arrived…
The security paradox: tools that record without alerting
The incident analyzed by Unit 42 raises a central question about the effectiveness of security solutions. The victim company had deployed two different enterprise EDR (Endpoint Detection and Response) solutions in its environment. These tools recorded malicious activity in their data logs: every suspicious connection, every lateral movement, every file prepared for exfiltration. Yet they generated very few alerts.
The security team had visibility in theory, but not in practice. While the logs contained a complete record of the attack, the absence of alerts meant that this data remained hidden in plain sight until it was too late. This situation reflects a wider trend revealed in Palo Alto Networks’ Global Incident Response 2025 report: in 75% of the incidents analyzed, clear evidence of malicious activity existed in the logs but went unnoticed.
This finding underlines the importance not only of deploying security tools, but also of configuring them correctly and ensuring actionable visibility of the environment. Investing in cybersecurity is not enough: organizations must ensure that their solutions are properly configured, actively monitored and generate actionable alerts.
A new strategic threat: exploiting mergers and acquisitions (M&A)
One of the most worrying revelations of November 2025 concerns a new strategy targeted by Akira: the exploitation of vulnerabilities during mergers and acquisitions (M&A). An in-depth investigation by ReliaQuest analyzing attacks between June and October 2025 found that Akira systematically targets legacy SonicWall SSL VPN appliances during acquisitions of small and medium-sized enterprises.
In every incident analyzed, Akira operators gained a foothold in larger companies by compromising SonicWall devices inherited from small companies acquired in M&A deals. These acquiring companies were unaware that these devices existed in their new environments, leaving critical vulnerabilities exposed. This is not just the usual story of hidden technologies falling through the cracks in M&A deals. These attacks were part of a deliberate, targeted campaign against SonicWall devices, rare in large organizations but common in smaller ones.
The Akira group, also known as Gold Sahara, Howling Scorpius, Punk Spider and Storm-1567, may have links with the now-defunct Conti group. This potential parentage would partly explain the sophistication of their methods and their ability to quickly identify and exploit organizational flaws.
Three key factors in post-acquisition exploitation

ReliaQuest’s analysis identified three M&A-related factors that enabled attacks to progress: outdated privileged credentials, predictable hostnames and inconsistent endpoint protection. These factors created a perfect conjunction for Akira’s success, turning legacy environments into risks for their new owners.
In every incident analyzed between June and October 2025, Akira’s initial compromise traced back to a SonicWall SSL VPN device inherited from an acquired small or medium-sized enterprise. Once inside, the attackers immediately looked for privileged accounts, such as those from former MSP (Managed Service Provider) or administrator logins, which had been transferred during the M&A process. These logins were often unknown to the acquiring company, and remained unmonitored and unrenewed after the acquisition.
By exploiting an inherited administrator credential, Akira operators gained access to sensitive systems and navigated to a domain controller in an average of just 9 hours. In some incidents, this time was even faster, with progression in less than five hours. This rapid escalation was possible because legacy accounts remained unverified, giving attackers the persistence they needed to penetrate deeper into the network before defenders could react.
Akira operators didn’t have to work hard to identify high-value targets in legacy networks. In several investigations, they scanned networks for hosts with default or predictable names. These naming conventions, inherited from the acquired company, had not been standardized during the M&A integration, making it easy to quickly identify high-priority targets such as domain controllers and application servers. In one documented case, Akira identified a file server with a default style name and, within minutes of gaining initial access, began FTP login attempts and account enumerations, followed shortly afterwards by successful data exfiltration.
| Metric | Time |
|---|---|
| Minimum documented time between initial access and reaching the domain controller | 5 hours |
| Average time to reach domain controller | 9.3 hours |
| Average time between lateral movement and ransomware deployment | 1 hour |
| Minimum time between initial access and exfiltration | 2 hours |
| Maximum operating time without detection | 42 days |
Why SonicWall is a prime target
While it’s impossible to know Akira’s exact motivations, ReliaQuest’s investigation points to several reasons why SonicWall SSL VPN devices have become prime targets. These devices are widely deployed by small and medium-sized businesses due to their affordability and ease of use, making them a common presence in many environments and a reliable entry point for attackers.
SonicWall’s accessibility and ease of deployment often lead to rushed or inconsistent security practices, particularly with regard to credential management and patch application. In addition, SonicWall’s remote access capabilities, such as SSL VPN, are frequently exposed on the Internet and can be left misconfigured or unmonitored, creating opportunities for attackers to exploit known vulnerabilities or default settings.
These weaknesses are exploited by attackers as a launching pad for ransomware. SonicWall devices are frequently deployed with default passwords, legacy privileged accounts or outdated settings. If these are overlooked during integration, they become an easy access route for attackers. Many organizations add SonicWall appliances to their network without regular patching or security reviews, leaving known vulnerabilities open to exploitation. In the rush of M&A activity, devices can sometimes be left out of inventories or monitoring processes, allowing attackers to use these devices as hidden entry points to move from acquired companies to larger organizations undetected.
Mass exploitation of CVE-2024-40766
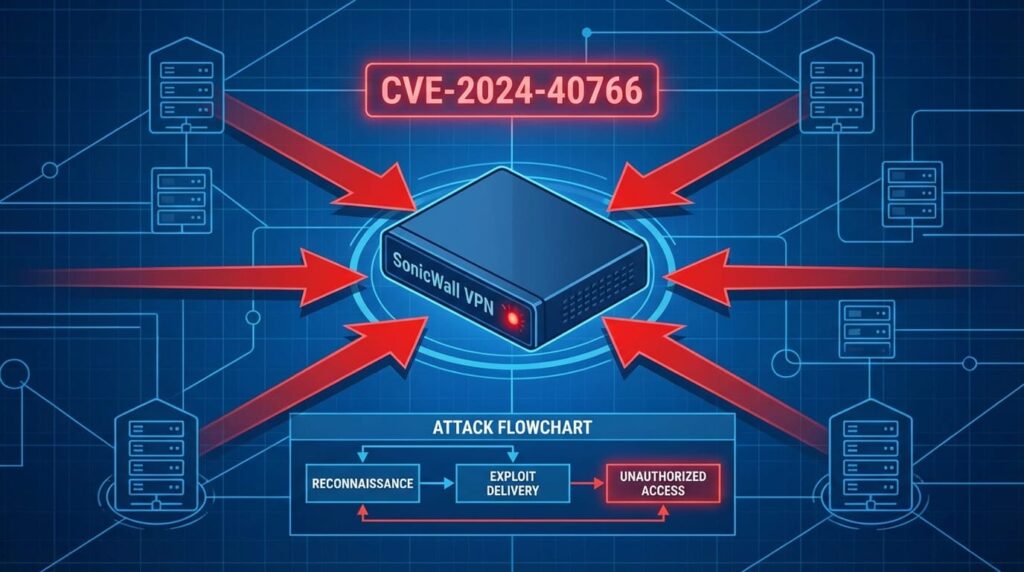
More globally, from July 2025 onwards, cybersecurity researchers observed a significant upsurge in Akira attacks exploiting the CVE-2024-40766 vulnerability affecting SonicWall SSL VPN firewalls. This inappropriate access control flaw allows attackers to steal VPN login credentials, bypass multi-factor authentication (MFA) when not properly configured, and gain initial access to corporate networks.
In particular,Arctic Wolf has reported a marked increase in Akira activity targeting SonicWall SSL VPN accounts since late July 2025, a campaign that remains active to this day. Sophos analysis indicates that 149 victims have been linked to Akira attacks in the last 90 days, with a predominance in the manufacturing, legal and professional services, and construction and engineering sectors.
In October 2025 alone, the group compromised over 70 victims by exploiting publicly accessible devices such as SonicWall SSL VPNs.
Expanding technical capabilities: Nutanix VMs now targeted
One of the most significant technical revelations of November 2025 concerns the expansion of Akira’s capabilities beyond VMware ESXi and Hyper-V. CISA’s bulletin on this ransomware has just been updated to include a key piece of information: in June 2025, the group’s players succeeded for the first time in encrypting Nutanix AHV virtual disk files. This development demonstrates the group’s ability to adapt quickly and its willingness to target an ever wider range of virtualization systems.
At the start of the attack chain for this incident appears to have been the exploitation of flaw CVE-2024-40766, a failed access control vulnerability in SonicWall firewalls. This expansion towards Nutanix is particularly worrying given Gartner’s recent predictions that by 2028, 35% of VMware workloads will have migrated to another platform, with Nutanix suggested as a first-choice alternative not so much for price as for functional capabilities.
The updated bulletin also reveals a sophisticated technique for bypassing virtual disk protection. In one documented incident, VMDK protection was bypassed by temporarily shutting down the domain controller’s virtual machine. The VMDK files were then copied and attached to a new VM, extracting the NTDS.dit file and the SYSTEM hive, ultimately compromising a domain administrator account. This method illustrates the growing ingenuity of Akira affiliates in their ability to bypass protection mechanisms.
Diversified initial access vectors
The November 2025 update reveals that the Akira group now exploits a wide range of vulnerabilities to gain access to networks. The initial version of the April 2024 bulletin mainly referred to initial access via MFA-free VPNs, mainly from Cisco. According to the new version of the bulletin, to which OFAC contributed, the initial access arsenal has diversified considerably.
| CVE | Affected product | Description |
|---|---|---|
| CVE-2020-3259 | Cisco ASA/FTD | Exposure of sensitive information – allows in-memory content to be retrieved without authentication |
| CVE-2023-20269 | Cisco ASA/FTD | Authentication bypass – paves the way for brute-force attacks or setting up unauthorized SSL VPN sessions |
| CVE-2020-3580 | Cisco ASA/FTD | Cross-Site Scripting (XSS) without authentication on web interface |
| CVE-2023-28252 | Windows CLFS | Flaw in Windows logging service used for privilege elevation |
| CVE-2024-37085 | VMware ESXi | Active Directory authentication bypass |
| CVE-2023-27532 | Veeam Backup | Lack of authentication for critical function – allows encrypted authentication to be exfiltrated from config database |
| CVE-2024-40711 | Veeam Backup | Untrusted data deserialization allowing RCE |
| CVE-2024-40766 | SonicWall | Inappropriate access control in SSL VPN firewalls |
Arsenal of attack tools and techniques
The November 2025 update documents Akira’s use of a wide range of tools covering the entire attack cycle. For remote access and persistence, affiliates use AnyDesk, LogMeIn, RustDesk and MobaXterm, enabling them to establish persistence and blend in with legitimate administration activity. The initial version of the bulletin already reported the use of a legitimate tool, Zemana AntiMalware, to stop antivirus-related processes.
For recognition, Akira affiliates rely on AdFind, Advanced IP Scanner, SoftPerfect NetScan and BloodHound with Invoke-BloodHound. The update also adds the use of nltest /dclist: and nltest /DOMAIN_TRUSTS to map the Active Directory environment. ID theft relies on classic tools such as Mimikatz and LaZagne, as well as LSASS dumping via comsvcs.dll in PowerShell and SharpDomainSpray for password spraying.
Data exfiltration is achieved using FileZilla, WinSCP, RClone and Mega cloud storage, while data is compressed with 7-zip or WinRAR prior to transfer. For tunneling and command and control, attackers use Ngrok, Cloudflare Tunnel, SystemBC, Cobalt Strike and Impacket. In some cases, as little as 2 hours elapsed between initial access and exfiltration, leaving little time for security teams to react.
Double extortion and encryption scheme
Akira systematically uses a double extortion strategy that combines massive data exfiltration – up to 1 TB in documented cases – with system encryption. Data is compressed with WinRAR or 7-zip before exfiltration, then the attackers threaten to publish the stolen data on their Tor leak site. Additional pressure is applied via direct phone calls to the victims.
The encryption scheme used by Akira is hybrid, combining a ChaCha20 cipher and a public RSA key system. The combination enables full or partial encryption, customized according to file type and size. To complicate recovery and forensic analysis, PowerShell commands are used to delete VSS (Volume Shadow Copy) copies. Encrypted files are given the extension .akira, .powerranges, .akiranew or .aki, depending on the variant used, and ransom notes named akira_readme.txt or fn.txt appear in the root and user directories.
Variant evolution
Akira has demonstrated a capacity for constant evolution since its first appearance. The first version of the ransomware was written in C++ and used the .akira extension. Its second incarnation, spotted in the summer of 2023 under the name Megazord, was written in Rust and used the .powerranges extension, but seems to have been abandoned since 2024.
The current variant, Akira_v2, is an enhanced Rust version offering advanced functionality. It features granular control over CPU core usage and protection via Build ID to hinder dynamic analysis. It also offers targeted deployment options on virtual machines only via the –vmonly parameter, as well as the ability to stop running VMs with the –stopvm parameter. This ability to specifically target virtualized environments partly explains the group’s effectiveness against modern enterprise infrastructures.
Real-life attacks in November 2025
Victim tracking data reveal particularly intense activity by the Akira group during November 2025, with dozens of claimed victims in a variety of sectors.
On November 11, 2025, the group claimed responsibility for an attack on Rhodes Young Black & Duncan, an accounting firm in Duluth, Minnesota. The attackers threaten to publish corporate documents including clients’ personal documents such as scanned passports, driver’s licenses and social security numbers, as well as sensitive medical information, complete HR records, financial documents and contracts, and some files related to military projects. This attack illustrates the diversity of exfiltrated data and the major reputational risk for consulting firms handling sensitive client information.
On November 28, 2025, American Public Television, a historic distributor of public television programs that introduced iconic figures such as Julia Child and Fred Rogers, was targeted by Akira. The group claimed to have exfiltrated 22 GB of data, including personal information on employees and customers, numerous projects and agreements, as well as confidential legal files. The attack also simultaneously affected several other organizations: Morton LTC Home (pharmaceutical solutions), Reed Pope (law firm), Benchmark Connector Corporation (aerospace and military connectors), and Radtke Contractors (construction company).
On the same day, Panini Kabob Grill, a Mediterranean restaurant chain, had 60 GB of sensitive corporate documents compromised, including employee personal information, financial documents and operational data. Design Team Sign Company, a manufacturer of personalized graphic signage, suffered the exfiltration of 108 GB of corporate documents.
| Victim | Sector | Data exfiltrated |
|---|---|---|
| Rhodes Young Black & Duncan | Accounting firm | Personal customer documents, medical information, HR files |
| American Public Television | Media | 22 GB – employee data, projects, legal files |
| Panini Kabob Grill | Catering | 60 GB – financial and operational documents |
| Design Team Sign Company | Manufacturing | 108 GB – corporate documents |
| Lone Rock Timber | Forestry | 25 GB |
| Parrish Tire | Distribution | Not specified |
| Zoetis | Veterinary pharmaceuticals | Not specified |
| Crucible Industries | Metallurgy | Not specified |
| Hitech | Motorsports | Not specified |
Most targeted sectors
Authorities identify the manufacturing sector as the one most targeted by the Akira Group. Educational institutions as well as the health and public health sector, including hospitals and care organizations, are also among the priority targets. Information technology, financial services, food and agriculture, as well as construction and engineering, have all seen strong growth recently. Legal and professional services round off the list of high-risk sectors. Although Akira primarily targets small and medium-sized enterprises, the group has also compromised larger organizations in these various sectors.
Mitigation recommendations
In the face of this growing threat, the authorities recommend a series of priority actions that organizations should implement immediately.
Immediate measures
Fixing known exploited vulnerabilities is the top priority, particularly CVE-2024-40766 for SonicWall, CVE-2024-40711 and CVE-2023-27532 for Veeam, as well as all the Cisco CVEs listed above. Phishing-resistant multi-factor authentication must be enabled and enforced on all VPN services, administration accounts and remote access services such as RDP and SSH. Organizations should maintain regular backups by keeping offline copies, regularly testing restore processes and protecting backup servers from unauthorized access.
Specific measures for mergers & acquisitions
Organizations engaged in M&A transactions should conduct an immediate inventory of legacy assets by deploying automated discovery tools, identifying all remote access devices such as VPNs and RDPs, and mapping legacy SonicWall appliances. Strict post-acquisition credential hygiene is a must, with mandatory rotation of all passwords, auditing of legacy privileged accounts, revocation of obsolete MSP and administrator accounts, and renewal of the KRBTGT account for Kerberos.
Standardization of security controls is essential, with unified EDR deployment on all legacy systems, standardization of naming conventions to avoid predictable hostnames, and activation of anti-tampering protection on all endpoints. ReliaQuest also recommends the use of automated discovery tools to inventory every device in the merged environment, helping to quickly identify blind spots and misconfigured systems after an acquisition.
Hardening measures
Network segmentation must isolate critical infrastructures, restrict administrative access to dedicated management VLANs and limit lateral movement. Endpoint hardening involves eliminating end-of-life systems, keeping patch levels up-to-date and disabling unnecessary services.
In terms of monitoring and detection, organizations need to deploy robust cloud surveillance, monitor unusual VPN connections, monitor privileged account activity and implement effective alert rules. It’s crucial not just to collect logs, but to ensure that they generate actionable alerts, as the 42-day incident painfully demonstrated.
Raising user awareness of social engineering techniques such as ClickFix and fake CAPTCHA, of the risks of phishing and establishing procedures for reporting suspicious activity complete these recommendations. The incident involving the fake CAPTCHA on the car dealer’s website is a perfect illustration of how a seemingly innocuous action can be the entry point to a major compromise.
Outlook and conclusion
The November 2025 revelations concerning the Akira group confirm that this threat continues to evolve and intensify. With $244 million extorted, exfiltration times of less than 2 hours, systematic exploitation of mergers and acquisitions, and expansion to new platforms such as Nutanix AHV, Akira represents a major danger to organizations of all sizes.
ReliaQuest predicts that the ransomware risk for organizations engaged in M&A is likely to grow as malicious actors refine what works. The result will be larger, faster attacks, with more groups likely to copy Akira’s proven playbook for automating the exploitation of neglected, low-cost technologies. This level of efficiency and reward is likely to inspire other ransomware groups to adopt similar strategies, intensifying the competition and increasing the overall impact of these campaigns.
The paradox revealed by the Unit 42 incident – security tools that record but don’t alert – underlines that investing in cybersecurity isn’t enough. Organizations need to ensure that their solutions are properly configured, actively monitored and generate actionable alerts. Forty-two days is a long time. When attackers have that much time to operate undetected, they’ll find your most valuable assets, compromise privileged accounts and position themselves for maximum impact.
Faced with an adversary capable of operating for 42 days undetected, stealing 1 TB of data before encryption, and compromising legacy systems in a matter of hours, prevention, rapid detection and incident preparedness become absolute imperatives. Authorities’ recommendations must be applied immediately, in particular the patching of known vulnerabilities, the deployment of phishing-resistant multi-factor authentication, and the rigorous auditing of legacy environments during acquisitions.
References and sources
CISA Advisory AA24-109A – Updated November 13, 2025
Unit 42 Palo Alto Networks – Anatomy of an Akira Ransomware Attack: When a Fake CAPTCHA Led to 42 Days of Compromise
ReliaQuest – Threat Spotlight: Akira Ransomware’s SonicWall Campaign Creates Enterprise M&A Risk
Silicon.fr – Akira: the evolution of ransomware that encrypts even Nutanix VMs
HIPAA Journal – Akira alert November 2025
Cybersecurity Dive – Critical sector attacks
Coretelligent – Report November 2025
DExpose.io – Real-time victim tracking
Ransomware.live – Akira victim database
Indicators of Compromise (IoCs) and detection signatures are available in the full CISA advisory and the reports of the various security solution vendors.
