Threats to businesses are constantly evolving to adapt to new technologies and defense mechanisms. Among these threats, ransomware is one of the most feared, involving malicious software that blocks access to a user’s files or system, demanding a ransom to unlock them. Today, a new business model is emerging among cybercriminals: Ransomware-as-a-Service (RaaS). What is RaaS, and what are its implications for businesses and individuals?
Table des matières
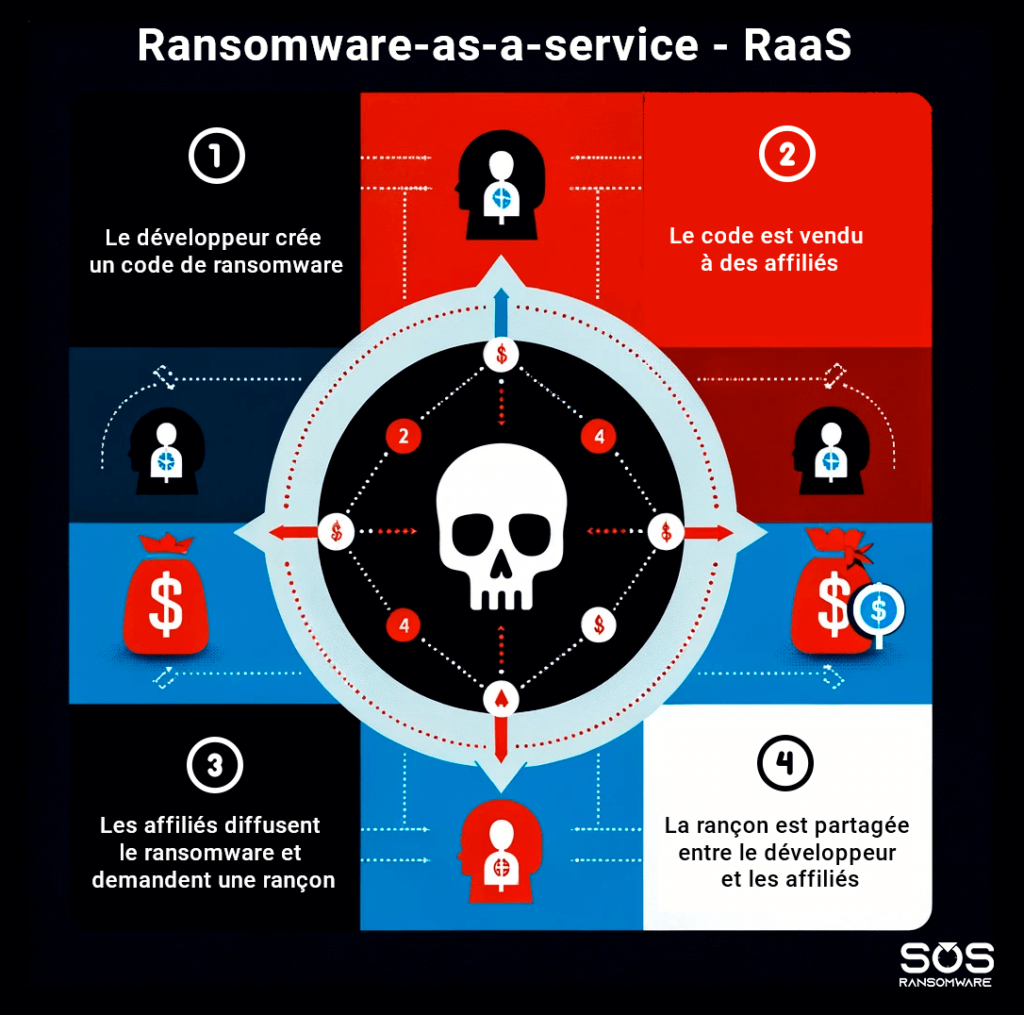
ToggleHow does Ransomware-as-a-Service work?
RaaS is based on a business model similar to Software-as-a-Service (SaaS), where a provider makes application software available to its customers via the Internet. In this case, the service offered is none other than easily accessible and customizable ransomware.
A partnership model between developers and distributors
The development and distribution of ransomware are two complex activities, often carried out by players specialized in each of these fields. Ransomware developers create and maintain the source code and infrastructure needed to infect targeted systems, while distributors take care of spreading this malware through phishing campaigns, exploit kits or other infection methods.
In the RaaS model, developers offer a platform where distributors can customize ransomware as they see fit, choosing for example the ransom amount demanded or the payment method. Profits are then shared between the two parties, according to pre-negotiated percentages.
Revenue models are broadly similar to those of traditional businesses. They can sell their services on a fixed-price, subscription basis, or opt for profit-sharing, the latter being less regular but potentially more lucrative.
4 types of Ransomware-as-a-Service revenue model
- Monthly subscription: users pay a fixed amount each month, and earn a small percentage of each successful ransom.
- Affiliate programs: a percentage of profits, between 20 and 30% in most cases, is paid to RaaS developers to improve the service and increase profits.
- Single license fee: payment of a single fee for access, with no profit sharing, offering perpetual access to affiliates.
- Pure profit-sharing: distribution of profits between affiliates and operators according to pre-defined percentages when the license is purchased.
As you can see, the business model is a classic one, apart from its illegal purpose. In 2020, over 60% of all ransomware attacks were linked to Ransomware-as-a-Service (RaaS) models, a fast-growing and highly competitive sector. This trend makes RaaS increasingly attractive to cybercriminals, partly because of the many poorly secured infrastructures. The year 2020 saw an almost 500% increase in the total number of ransomware attacks, with two-thirds attributed to RaaS offerings. A trend that continues to grow. Revenues generated by ransomware attacks reached around $20 billion in 2020. Lockbit still accounts for the lion’s share of the Ransomware-as-a-Service (RaaS) economy, as we saw again recently.
Attractive ease of access and flexibility
The main attraction of RaaS lies in its accessibility and ease of use. No special programming or cybersecurity skills are required to create and launch a ransomware campaign. What’s more, the customization offered enables cybercriminals to adapt their products to the new defenses put in place by companies or authorities.
Ransomware-as-a-Service (RaaS) developers offer malware in the form of “kits”, which are sold or rented to those wishing to carry out cyberattacks. These kits are available on the dark web, where they are marketed in a similar way to products from legitimate companies, with advertising, special offers, and even customer support. Prices range from a few dozen dollars to several thousand, representing a relatively small investment compared to the potential ransoms attackers may demand.
Risks and consequences for victims
With the emergence of RaaS, ransomware attacks are multiplying worldwide, affecting both large organizations and private individuals. The direct consequences of such an infection are manifold:
Financial loss due to ransom
The first consequence is obviously the ransom demanded to unlock the files. This can amount to several thousand euros, or even more for organizations. While this payment can sometimes restore access to data, it is not guaranteed and may encourage cybercriminals to reoffend.
Damage to IT systems
Ransomware can also cause material damage, particularly when it attacks servers or industrial equipment that must be replaced in the event of failure. The costs involved are considerable, especially if the victim has no effective backup system.
Consequences for reputation and productivity
A ransomware attack can seriously damage a company’s reputation, especially if its customers or partners are also affected. In addition, the loss of access to files often leads to a drop in productivity, or even a complete halt to certain activities until the situation is resolved.
Preventive measures against RaaS
To counter ransomware attacks, several preventive measures can be put in place:
User awareness and training
Educating users is essential to avoid falling into the traps of cybercriminals. Regular training and the adoption of good security practices (using strong passwords, not clicking on suspicious links, etc.) help reduce the risk of infection.
Keeping systems up to date
Ransomware often exploits security holes in software, so it’s essential to keep your systems and applications up to date. Regular updates minimize the risk of exploiting known vulnerabilities.
Regular backups
In the event of a ransomware infection, an effective solution to limit data loss is to have regular backups on external media or remote servers. This measure makes it possible to restore the infected system without having to give in to ransom demands.
Ransomware-as-a-Service’s ease of use and massive spread represent an additional threat to businesses and individuals, who need to adapt their cybersecurity strategies accordingly. Raising awareness of good security practices and implementing preventive measures such as updates and backups are all ways of combating this new form of crime.
