Since the end of 2023, KillSec has been gradually establishing itself in the global cybercrime ecosystem, perfectly illustrating the modern transformation of hacktivist groups towards financially motivated operations. Born under the banner of the Anonymous collective, this group rapidly evolved into a sophisticated Ransomware-as-a-Service (RaaS) model, primarily targeting the healthcare sector despite its official declarations. With an accessible affiliate program, KillSec represents a new generation of hybrid threats combining political ideology and cybercriminal profit.
Table des matières
ToggleFrom hacktivist roots to criminal ecosystem: the evolution of KillSec
KillSec’s story begins in autumn 2023 with the appearance of its first Telegram message, immediately revealing its ambitions beyond mere hacktivism. In this initial announcement, the group openly recruited individuals with specific skills in “network penetration”, “web penetration” and “malware creation”, clearly signaling an orientation towards offensive cybercriminal operations rather than traditional activism.
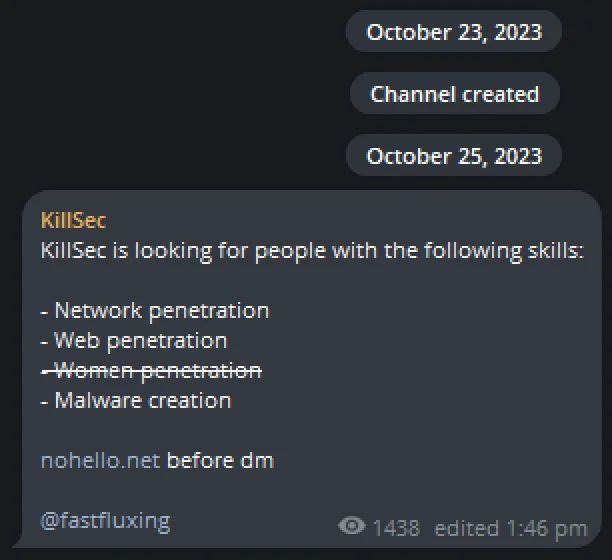
This prediction came true in June 2024, around a year after the creation of the Telegram channel, when the group officially introduced its new RaaS service. This transition perfectly illustrates the phenomenon described by the experts at ReliaQuest: “Today, many hacktivist groups are moving away from website defacement and document disclosure to more lucrative tactics such as ransomware.” in short, modern hacktivism is evolving from protest to profit, transforming digital protest tools into lucrative criminal infrastructures.
Based on the topics, languages and ideas discussed in the group’s communications, analysts locate KillSec in the Eastern Europe-Russia region. This likely geographic location aligns with trends seen in other Russian-speaking ransomware groups, although KillSec stands out for its international targeting strategy and bilingual English-Russian communication. This rapid evolution reflects the accelerated professionalization characteristic of new hybrid cybercriminal threats. This professionalization has led to the development of a diversified criminal architecture.

Criminal architecture: KillSec services and illegal offerings
KillSec now operates in three distinct areas, revealing the breadth of its criminal activities and its strategy of revenue diversification. This multi-service approach positions the group as a true “cybercriminal service provider” rather than a mere ransomware operator, demonstrating a worrying organizational maturity for a relatively new group.
Malicious “penetration test” service
KillSec markets its “pentest” services as a means of gaining unauthorized access to systems or data. Unlike legitimate penetration testing aimed at identifying and correcting security vulnerabilities, KillSec’s service is promoted as a method enabling customers toaccomplish an illegal intrusion into specific networks or steal sensitive information. This backdoor approach to legitimate cybersecurity practices illustrates the sophistication of their criminal business model and their ability to exploit professional terminology to commit illicit activities.
Hijacked OSINT (Open Source Intelligence) service
KillSec’s OSINT service targets individuals or organizations seeking to uncover detailed and often private information. Although OSINT is a legitimate practice used in cybersecurity and investigation, KillSec is hijacking it for malicious purposes. This service can attract customers interested in doxxing (disclosure of personal data), industrial espionage or targeted attacks, making it a significant threat to the privacy and security of targeted individuals and organizations.
Ransomware-as-a-Service (RaaS) affiliate program
However, it was with the launch of its affiliate program that KillSec really took the plunge into large-scale organized crime. In June 2024, KillSec officially launched its RaaS affiliate program, offering a platform for cybercriminals to deploy ransomware attacks in exchange for a share of the profits from successful extortion campaigns. Although the group’s publications often featured extortion rather than ransomware use per se, this RaaS (Ransomware-as-a-Service) initiative enables less technically skilled individuals to carry out ransomware attacks, thus broadening their reach. This democratization of cybercrime, as seen recently with the hijacking of the HexStrike AI tool, represents a particularly worrying development in the threat landscape.
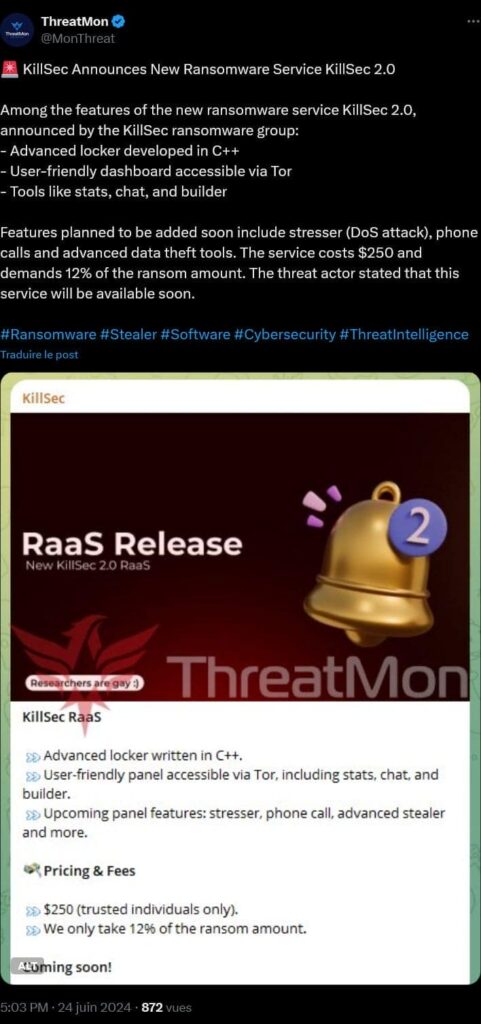
RaaS technical model: sophistication and accessibility
The technical architecture developed by KillSec for its RaaS program reveals a particularly thoughtful approach to the design of its criminal offering. In June 2024, the group showcased an “advanced locker” developed in C++ and a control panel accessible via Tor. This interface provides affiliates with real-time statistics, a chat function and a build tool to easily customize and deploy their own ransomware campaigns without in-depth technical expertise.
KillSec’s business model sets a $250 entry fee for its RaaS program, with a 12% commission on ransomware collected. This percentage, lower than many RaaS competitors, could be a competitive advantage designed to attract new affiliates with attractive ****profit-sharing conditions. However, access remains limited to “trusted individuals” according to the group’s unspecified criteria, suggesting a selection of affiliates.
KillSec announced the development of additional functionalities: a tool apparently dedicated to **** DDoS attacks (distributed denial of service attacks), **** a phone call function for social engineering or victim harassment, and an advanced stealer for the extraction of sensitive information.
Targeting strategy and operational impact: a multi-faceted global threat
Analysis of the 242 victims documented by ransomware.live reveals a methodical and geographically diverse targeting strategy, testifying to a constantly evolving operational capability since autumn 2023.
Geographical analysis: the USA and India in the firing line
The current geographical distribution of KillSec victims reveals a concentration on India and the USA, which largely dominate the catalog of compromised organizations. The UK, Brazil and Belgium round out the top 5 most-targeted countries, but lag far behind these two leaders in terms of number of victims.
Sector breakdown: from sensitive infrastructures to mission-critical services
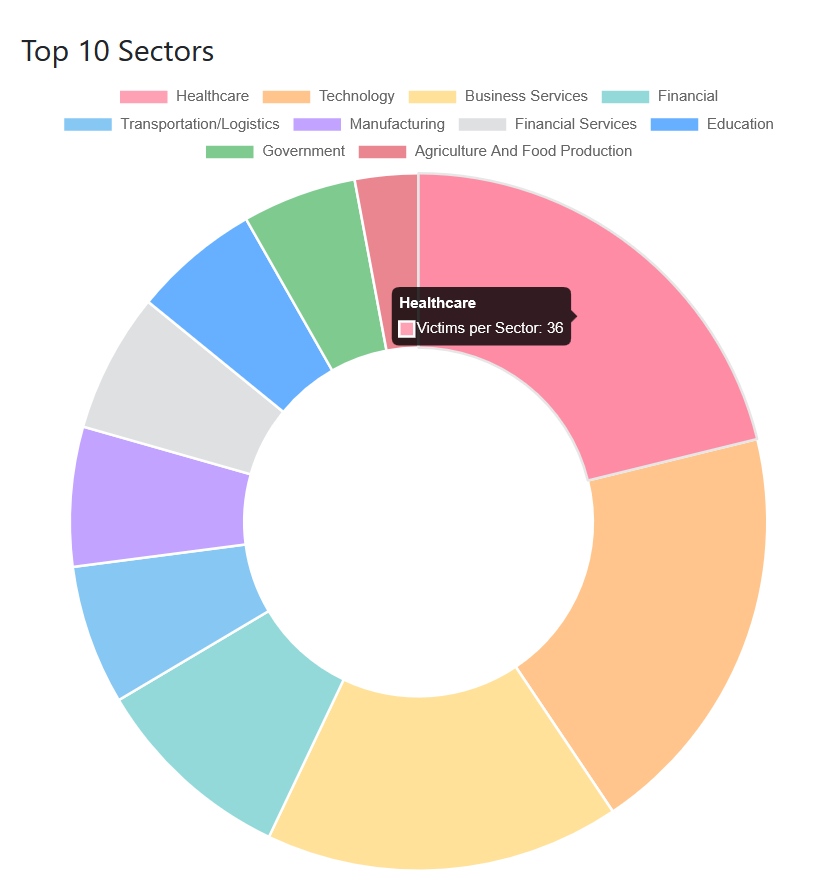
Sectoral analysis of victims reveals a marked focus on critical sectors. Healthcare is the main target, accounting for 14.9% of attacks, closely followed by technology at 13.6% and business services at 11.6%. This concentration on critical sectors reveals a major contradiction with the official rules of the KillSec affiliate program.
Affiliation contradictions: theoretical prohibitions vs. real targeting
KillSec’s affiliate program rules explicitly prohibit partners from attacking critical infrastructure. This policy stands in stark contrast to operational reality. However, according to ransomware.live data, the healthcare sector represents one of their main targets, with 36 documented victims – the most attacked category in their victim catalog. This discordance highlights a glaring gap between the rules they promote to affiliates and the actions they are willing to endorse or execute themselves.
2025 campaigns: escalating attacks on the healthcare sector
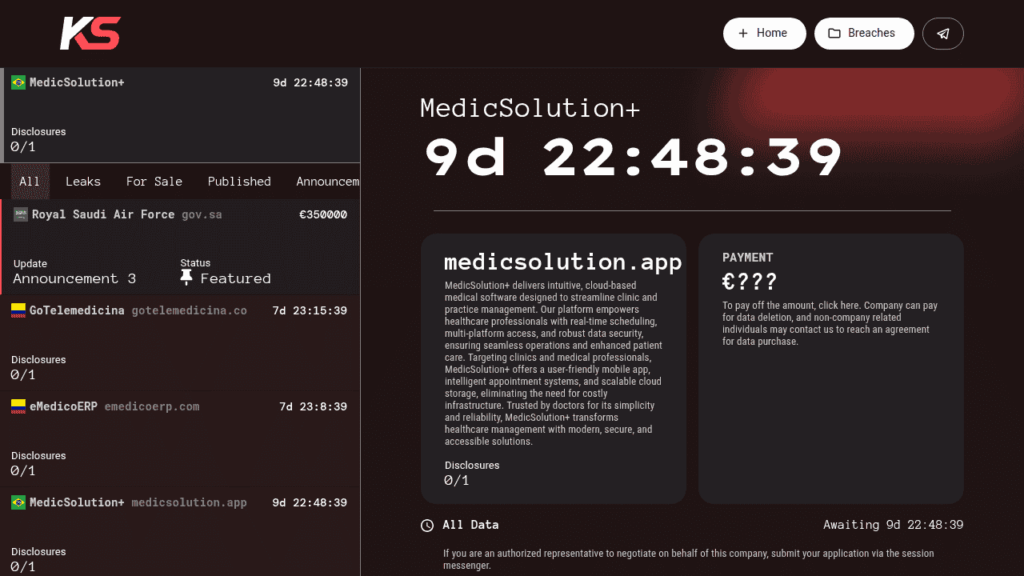
The year 2025 marked a significant intensification of KillSec’s operations against the healthcare sector, culminating in several major attacks. Theattack on MedicSolution on September 8, 2025 is a perfect illustration of the group’s tactical shift towards supply chain attacks. This offensive against the Brazilian healthcare software provider compromised over 34 GB of data containing 94,818 files, including lab results, X-rays, non-anonymized patient images and minors’ records.
The MedicSolution attack reveals a particularly worrying multiplier strategy. By compromising a single service provider, KillSec potentially exposed data from multiple client healthcare facilities, including Vita Exame, Clinica Especo Vida, Centro Diagnostico Toledo, Labclinic and Laboratório Alvaro. This “supply chain attack” approach demonstrates growing operational sophistication and a keen understanding of the sector’s structural vulnerabilities.
September 2025 proved particularly destructive with a series of coordinated attacks against healthcare institutions in Latin America. In addition to MedicSolution in Brazil, the group simultaneously hit Archer Health in the USA, Suiza Lab in Peru, GoTelemedicina in Colombia and eMedicoERP in Colombia.
Modus operandi and adaptability
Investigations into recent attacks reveal that KillSec favors theexploitation of faulty configurations rather than sophisticated intrusion techniques. Resecurity’s analysis of the MedicSolution attack highlighted the exploitation of misconfigured AWS S3 buckets, enabling massive data exfiltration without the need for advanced technical capabilities. This pragmatic approach illustrates that the technical sophistication of the C++ locker coexists with an opportunistic strategy that prioritizes operational efficiency over demonstrating technical prowess.
This “low-hanging fruit” approach (targeting easily exploitable vulnerabilities) reflects a strategy of operational efficiency maximizing return on investment. Rather than developing complex exploits, the group focuses on identifying and exploiting configuration vulnerabilities that are easily accessible but overlooked by victims.
The group’s infrastructural resilience is demonstrated by its ability to maintain operations despite disruptions. After the loss of their primary Telegram channel in November 2024, KillSec immediately switched to backup channels and maintained regular publication of their claims via their Tor-accessible website, demonstrating mature operational planning incorporating business continuity mechanisms.
Tactics, techniques and procedures (TTPs)
Analysis of KillSec’s tactics, techniques and procedures reveals a methodical approach combining in-depth reconnaissance, sophisticated initial access, and systematic data exfiltration. According to the MITRE ATT&CK analysis, the most likely TTPs for KillSec include :
- Acquire Access (T1650): acquisition of initial access by various methods
- Valid Accounts (T1078): use of compromised valid accounts
- Web Service (T1102): exploitation of legitimate web services
- Remote Services (T1021): exploit remote services
- Command and Scripting Interpreter (T1059): use of command and script interpreters
- Data from Information Repositories (T1213): extract data from information repositories
- Data from Local System (T1005): local system data collection
This list of TTPs indicates a methodical approach that favors stealth and persistence, characteristic of experienced groups despite KillSec’s relative youth.
Recommendations for protection against KillSec
Specialized defense strategies
In the face of the KillSec threat and similar groups, organizations need to adopt a multi-layered defense approach that is particularly well-suited to this group’s techniques. Experts recommend implementing defense-in-depth strategies, establishing a multi-layered security approach incorporating firewalls, intrusion detection systems, endpoint protection and data backups to ensure that if one defense is compromised by a ransomware attack, others will block it.
Targeted preventive measures
PowerShell restriction: use Group Policy Objects (GPOs) to restrict PowerShell access to necessary users only, preventing ransomware actors from using it to write malicious scripts.
Decoy strategies: implement deception technology by deploying honeypots and honeytokens to mimic valuable assets. This will distract ransomware attackers and alert security teams early in the attack cycle.
Enhanced monitoring of indicators of compromise: recent attacks reveal variable detection times ranging from a few hours to several days. Organizations need to implement 24/7 monitoring with automated alerts on known KillSec IoCs.
Disconnected backups: in the face ofsustained activity in 2025, it is critical to maintain regularly tested offline backups stored in isolated environments.
Network segmentation: given the priority targeting of critical infrastructures, microsegmentation of sensitive networks can limit lateral propagation in the event of an initial compromise.
Conclusion
KillSec now represents a mature and persistent cybercriminal threat, perfectly illustrating the transformation of hacktivist groups into sophisticated and lucrative criminal operations. With its accessible RaaS model, its problematic focus on the healthcare sector despite claims to the contrary, and its adaptability in the face of disruptive measures, the group represents a significant and evolving threat.
Thehybridization of ideological and financial motivations observed at KillSec probably foreshadows the future of the cybercriminal landscape, where the traditional boundaries between hacktivism, cybercrime and potentially state operations continue to blur. Organizations, particularly in the healthcare and critical infrastructure sectors, need to adapt their defensive strategies to cope with this new generation of hybrid threats, which exploit the contradictions between public discourse and actual practice.
Ongoing monitoring of KillSec’s evolution remains essential, as the group continues to refine its techniques, expand its network of affiliates and potentially broaden its destructive impact across the global digital ecosystem. Understanding its TTPs, motivations and business model is crucial to developing effective countermeasures against this emerging threat and similar groups that may follow its trajectory of criminal professionalization.
Main article sources :
- Ransomware.live: KillSec Group Statistics
- SOCRadar: Dark Web Profile: KillSec
- ReliaQuest: 5 Critical Threat Actors You Need to Know About –
- Blackwired: Hacktivist Groups Transition to Ransomware-as-a-Service Operations
