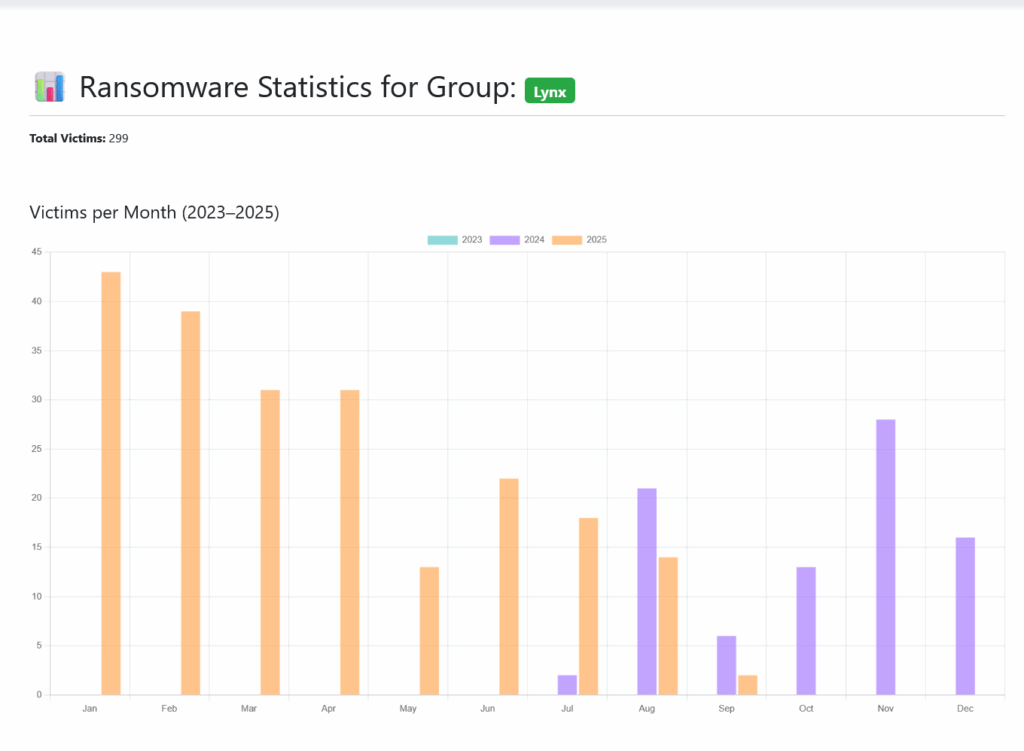
Since July 2024, Lynx ransomware has established itself as one of the most sophisticated threats in the global cybercriminal ecosystem. Born of the rebranding of the notorious INC ransomware, this group operates under a particularly successful Ransomware-as-a-Service (RaaS) model, combining advanced encryption techniques, multi-architecture infrastructure and surgical double extortion strategies. With almost 300 claimed victims and a strategic focus on MSPs (Managed Service Providers), Lynx is redefining the standards of professional ransomware.
Table des matières
ToggleFrom INC’s roots to the Lynx empire: the story of a cybercriminal mutation
The Lynx ransomware group emerged in mid-2024 and is widely regarded as a rebranding of the INC ransomware. This filiation is no accident: the two share substantial portions of their source code, indicating a strong connection between the organizations. Reports suggest that INC ransomware’s source code was for sale on dark web forums, potentially facilitating the development of Lynx as a more advanced variant.

The move towards the RaaS model represents a major strategic transformation. Unlike INC, which operated mainly as a closed group, Lynx has developed a sophisticated affiliate platform that attracts experienced slotters with an attractive 80/20 split in favor of affiliates. This approach reflects the growing professionalization of the cybercrime sector.
Since its emergence, Lynx has claimed around 300 victims, rapidly establishing its presence as a major player in the ransomware ecosystem. This rapid growth illustrates the effectiveness of its business model and the attractiveness of its platform for cybercriminals looking for a reliable infrastructure.
Technical architecture: the art of multi-platform encryption
Advanced cryptographic sophistication
Lynx ransomware employs a sophisticated combination of cryptographic algorithms, demonstrating its high technical level. The malware uses AES-128 in CTR mode combined with Curve25519 Donna for encryption, an approach that ensures both speed and robust cryptographic security.
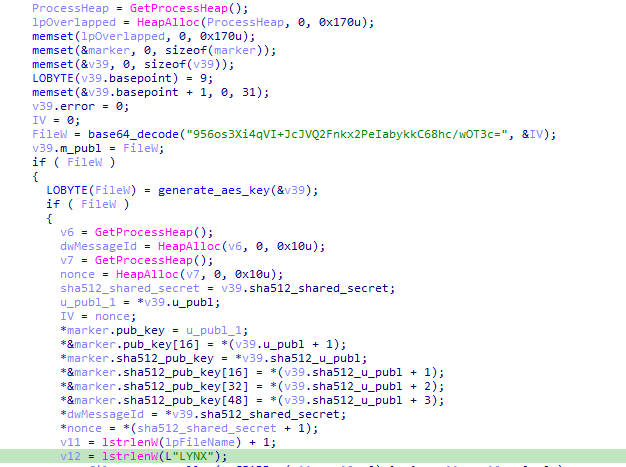
The key generation process reveals a particular sophistication. The sample decodes an ECC public key stored in Base64 format, then generates a shared secret which is hashed with SHA512 to derive the final AES key. The system also incorporates a 116-byte marker containing the ECC public key (32 bytes), the SHA512 hash of the public key (64 bytes), the “LYNX” identifier and various configuration information including the encryption block size (1MB), the encryption step and the number of ignored blocks.
A major innovation introduced in recent versions concerns variable encryption modes. Lynx now offers four distinct modes: fast (5% of the file), medium (15%), slow (25%) and entire (100%), enabling operators to adapt the speed/coverage ratio to their tactical objectives.
Revolutionary multi-architecture arsenal
One of Lynx’s most remarkable features is its comprehensive multi-architecture arsenal. Rather than targeting a single architecture, the group provides its affiliates with an “All-in-One” archive containing executables suitable for Linux x64, Linux ARM, MIPS, ESXi and many other platforms.
This strategic approach recognizes that modern corporate networks are rarely homogeneous. They may include virtualized infrastructures (ESXi), x86_64 servers running Linux or Windows, and ARM-based embedded systems. Having several ready-to-use versions greatly increases the effectiveness of ransomware, as it can be deployed on virtually any system discovered in the target network.
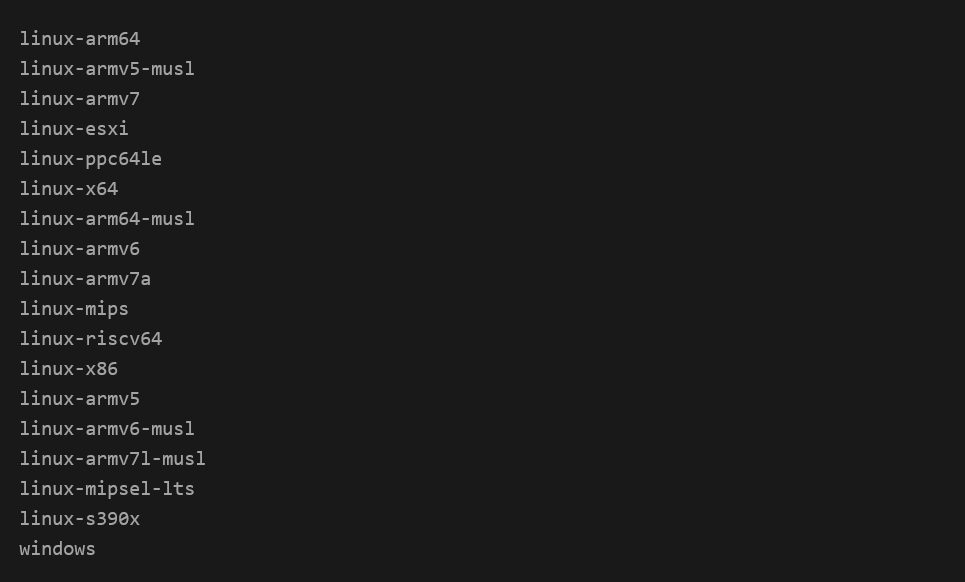
The archive includes :
- linux-arm64, linux-armv5-musl, linux-armv7: extended ARM compatibility
- linux-esxi: specific targeting of virtualization environments
- linux-mips, linux-ppc64le, linux-riscv64: support for specialized architectures
- windows: standard Windows version
The musl binaries in the archive deserve special attention. Identified by the suffix ‘-musl’, they are linked to the musl C library, making them more portable to peripheral environments and containers that may not have the standard glibc libraries installed.
Professional RaaS model: an enterprise-grade criminal infrastructure
Revolutionary membership panel
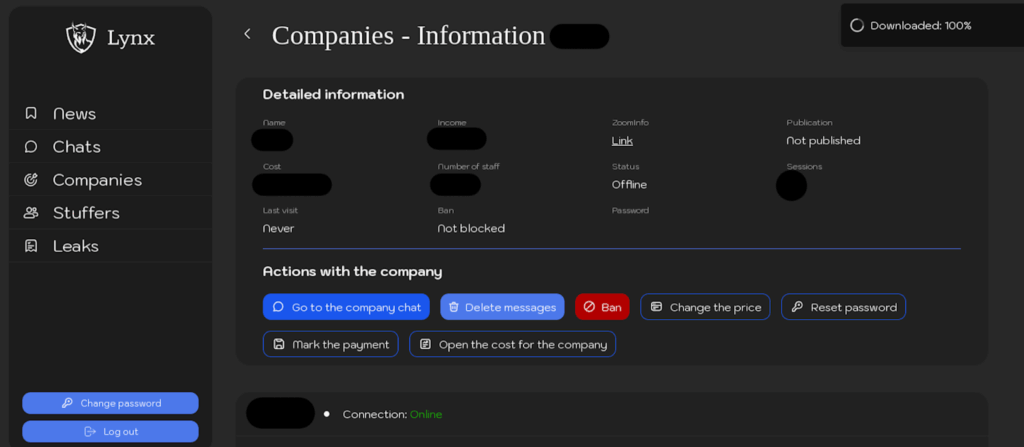
The heart of the Lynx model lies in its sophisticated administration panel, which illustrates the level of professionalization achieved by the cybercriminal group. Designed as a true campaign management interface, it enables affiliates to control every stage of their operations through five main sections: News, Companies, Chats, Stuffers and Leaks.
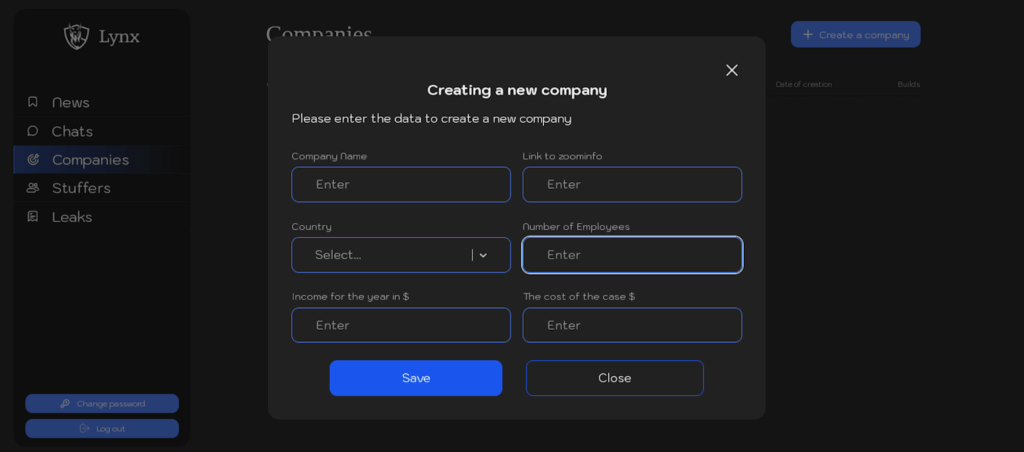
The “Companies” section offers a comprehensive interface for victim management. Affiliates can configure detailed information on each target: company name, link to ZoomInfo, country, number of employees, annual revenues in dollars and estimated cost of the case. This methodical approach reflects a targeting strategy based on business intelligence.
The “Leaks” section enables affiliates to create and schedule publications about attacked companies that have not paid the ransom. Features include scheduling of publications, customization of the attacked company’s logo, selection from the list of companies, specification of a publication time, choice of a category and addition of detailed descriptions of the leaks.
Attractive, competitive business model
Beyond the attractive financial breakdown already mentioned, theGroup-IB researchers’ study revealed that Lynx’s business ecosystem reveals a remarkable elaboration. The group has structured a comprehensive service offering that goes far beyond simple access to an encryption tool, transforming its model into a true criminal infrastructure platform. Lynx also offers its affiliates a tempting allocation, with a more attractive rate than older groups such as LockBit, making it easier to recruit new, experienced players.
The recruitment process reveals a professional approach. On the underground RAMP forum, user “silencer” posted a detailed advert on August 8, 2024, targeting experienced pentesting teams. The offer includes a complete infrastructure: builder with private keys not stored in the panel, independent blog post creation capability, full publication management and guest access for “traffickers”.
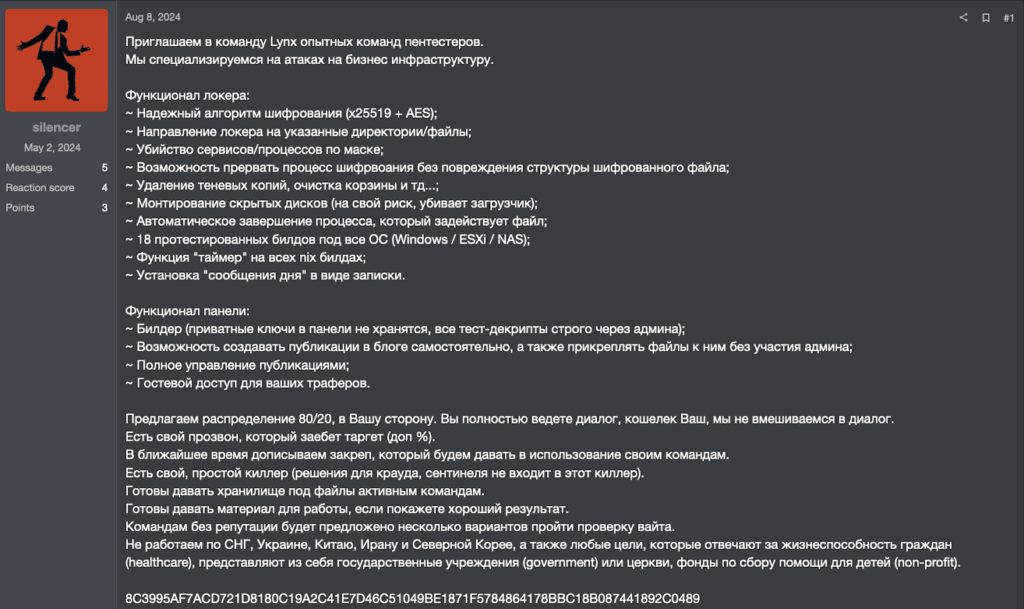
Additional services include a call service to harass targets, a persistent tool currently being finalized, a “simple killer” (not covering CrowdStrike or Sentinel when the post is published), and the provision of storage for active teams. This full-service approach transforms Lynx into a true criminal SaaS platform.
Themirrored infrastructure revealed comprises 29 .onion domains divided between administration panels (7 mirrors), leak blogs (7 mirrors), guest panels (7 mirrors) and corporate mirrors (8 mirrors), guaranteeing exceptional operational resilience.
Modern targeting strategy: MSP and sector diversification
Focus MSP, the preferred target
According to Acronis analysis in August 2025, managed service providers (MSPs) represent prime targets for cybercriminals, as they provide access to a network of other customers, amplifying the potential bounty. This targeting strategy is not specific to Lynx, but the group has particularly perfected it, as has Akira, which is proving very active in 2025.
An analysis of access techniques reveals different approaches for each group. WhileAkira mainly uses stolen or purchased administrator credentials, Lynx favors phishing e-mails to spread its malware to victims. Once access has been gained, the cybercriminals systematically disable security software. If this fails, they initiate remote exfiltration, followed by encryption using legitimate tools that are often whitelisted and beyond the reach of traditional surveillance.
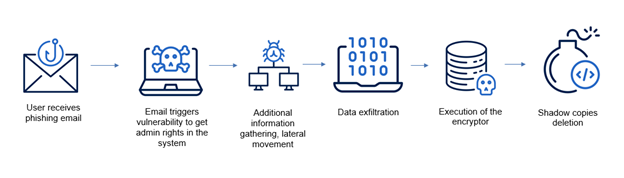
The sophistication of this approach lies in the use of legitimate tools diverted from their original function, a strategy which significantly complicates detection as these tools are naturally present in corporate environments.
Extensive global victimology
According to the latest available data, Lynx has claimed around 300 victims since its emergence, marking rapid and sustained growth. This expansion testifies to the effectiveness of its operating model and the attractiveness of its platform for cybercriminal affiliates.
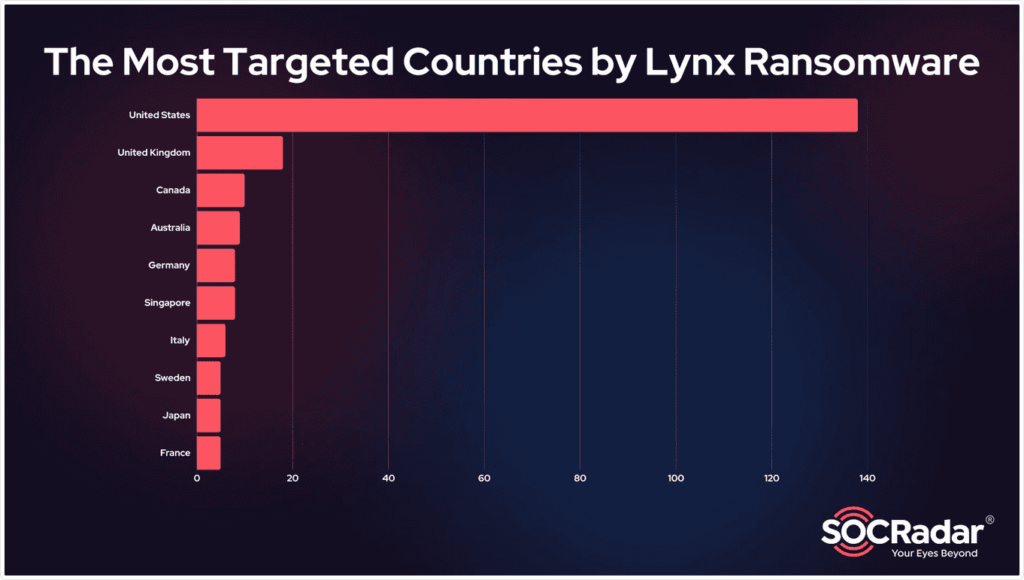
The geographical breakdown reveals a strategic concentration: the USA accounts for the majority of victims, followed by the UK, Canada, Australia and Germany. This selection reflects a strategic understanding of developed economic markets, where companies manage large volumes of sensitive data and generally have the financial resources to respond to ransomware demands.
From a sectoral point of view, manufacturing stands out as the most targeted sector, followed by professional services, technology and transportation. Energy, agriculture and tourism are also among the sectors affected, demonstrating a diversified opportunistic approach that exploits sector-specific vulnerabilities.
Emblematic cases include theattack on Electrica Group in December, one of Eastern Europe’s leading energy companies, and Hunter Taubman Fischer & Li LLC in January, a US law firm specializing in corporate and securities law. These incidents illustrate Lynx’s ability to target critical organizations with significant economic and social impacts.
Tactics, techniques and procedures: surgical sophistication
Advanced, methodical infection chain
Lynx deploys diversified access techniques, with phishing emails as the main vector. Once initial access has been gained, Lynx deploys a structured attack methodology that demonstrates considerable technical expertise. The reconnaissance phase uses tools such as CreateToolhelp32Snapshot with the TH32CS_SNAPPROCESS flag to create a snapshot of all running processes.
Specific persistence techniques include creating malicious Windows services, inserting scheduled tasks and modifying autorun registry keys. The malware also establishes persistent network connections to command and control servers, enabling continuous control even after systems have been rebooted.
The termination process reveals a surgical approach. The malware compares each process name to a predefined list using a case-insensitive search function.
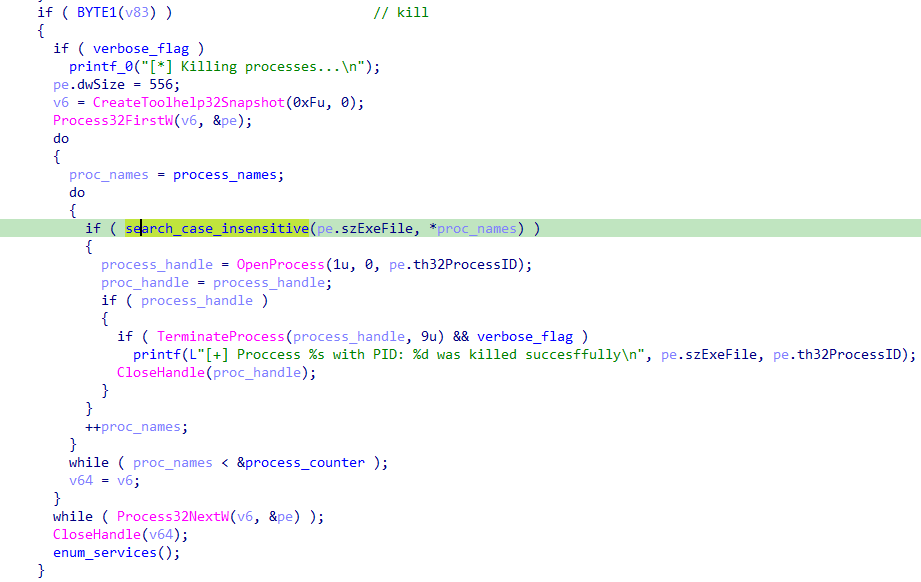
Targeted processes systematically include :
- sql
- veeam
- backup
- exchange
- java
- notepad
This strategic selection aims to disable recovery mechanisms and backup tools that could enable victims to restore their data without paying the ransom. The specific targeting of solutions such as Veeam testifies to the group’s determination to neutralize the most common enterprise backup solutions.
Evasion and persistence techniques
Lynx uses the Restart Manager API to terminate processes that maintain locks on files to be encrypted. This technical approach bypasses traditional protections that prevent the modification of files in use.
Shadow copy deletion uses a technique via DeviceIoControl with parameter ’53C028h’ (IOCTL_VOLSNAP_SET_MAX_DIFF_AREA_SIZE). By setting a maximum size of 1 byte, this operation forces the deletion of all existing snapshots, significantly hampering standard recovery capabilities.
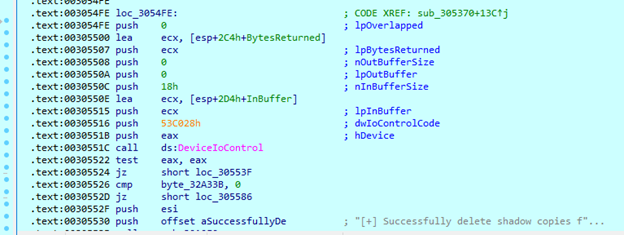
Multi-threading optimization reflects a quest for performance. The malware creates a number of threads equal to the number of processors multiplied by four, using the Windows I/O Completion Port mechanism to efficiently manage asynchronous I/O operations.
Double extortion infrastructure: the pressure ecosystem
Sophisticated and resilient escape sites
Lynx maintains a particularly elaborate leakage infrastructure that forms the core of its extortion strategy. The main site accessible via clearnet (lynxblog[.]net) serves as a public showcase, while a network of numerous .onion domains ensures operational resilience.
This distributed architecture reflects a thorough understanding of operational risks. If a domain is blocked or seized, the infrastructure can quickly switch to alternative mirrors, keeping pressure on victims and business continuity.
A dedicated page for each victim, detailing the stolen documents, the revenues of the targeted organization and the date of publication of the data, is created in the Lynx administration panel.
Sophisticated psychological pressure mechanisms
Lynx can automatically send the ransom note to available printers, adding an unexpected element to its attack strategy. The function lists all printers connected to the system and sends them the ransom note to print.
The ransomware also modifies the desktop background by creating a temporary image file named “background-image.jpg” in the temp folder. This file contains the ransom note as an image and is set as the desktop background.
The affiliate panel can be used to schedule the publication of stolen data, as well as to communicate with victims via a chat window accessible via normal browsers.
Recommendations for protection against Lynx ransomware
Reinforced backup strategies
The protection of backup systems is the critical issue in the face of Lynx. According toNextron Systems’ technical analysis, the group is targeting backup, exchange and veeam processes in particular.
Implement disconnected backups: the 3-2-1 rule must be supplemented by physically isolated offline copies. As Lynx is able to browse network shares, only air-gapped backups offer absolute protection.
Test your restores regularly: an untested backup is just an illusion of security. Schedule quarterly restore exercises on isolated environments to validate the integrity and functionality of your backups.
Secure privileged access: use dedicated accounts for backup operations, with mandatory multi-factor authentication and regular login rotation. Implementing a Zero Trust architecture reinforces this approach by applying the principle of continuous verification for all access, even internal.
Early detection and monitoring
Monitor specific indicators: Lynx generates distinctive behavioral signatures: massive process terminations, shadow copy deletion via DeviceIoControl, and communications to .onion domains.
Deploy network monitoring: abnormal outbound communications, particularly to newly registered domains or suspicious address ranges, are early indicators of infection.
Reinforce email detection: as phishing is Lynx’s main access vector, implement advanced filtering solutions with behavioral analysis and dynamic sandboxing.
Infrastructure hardening
Segment your network: limit lateral propagation by micro-segmenting critical environments. Isolate virtualization servers and storage systems in particular.
Apply priority patches: maintain a rigorous patch management program, with prioritization based on exposure to identified attack vectors.
Train your teams: organize regular simulation exercises including Lynx-specific techniques (double extortion, multi-architecture encryption).
In the event of an attack: data recovery
Reality on the ground
Official decryption is never guaranteed, even if a ransom is paid. Our experience in the field regularly demonstrates the shortcomings of the tools provided by cybercriminals, particularly in the case of process interruptions or complex system configurations.
How we recover and restore data encrypted by ransomware
Computer systems are made up of multiple complex layers, making them vulnerable to rapid and sophisticated attacks by cybercriminals.
We use proprietary software to implement four data recovery techniques: decryption, recovery of deleted data, reverse engineering of encryption algorithms and repair of damaged files.
If they’ve broken into your system, we’ll find the flaw in their actions.
For security reasons, we voluntarily limit the disclosure of detailed information about our specific tools.
Our intervention process
Immediate technical assessment: our experts analyze the attack footprint, identify the Lynx variant and assess the possibilities for recovery without ransom payment.
Secure cloning: we systematically clone affected media to preserve evidence and prevent further damage during recovery attempts.
Development of customized solutions: when standard decryptors fail, our engineers develop tailor-made tools adapted to the specificities of each attack, as demonstrated in our intervention on Akira ransomware.
Conclusion
Lynx ransomware perfectly illustrates theadvanced technical evolution of modern cybercriminal threats. Its professional RaaS model, multi-platform architecture and surgical double extortion techniques are repositioning criminal industry standards towards enterprise-level industrialization.
This technological and organizational transformation is accompanied by remarkable operational resilience, materialized by an infrastructure of 29 mirror sites and an ecosystem of experienced affiliates. Faced with this growing complexity, traditional defensive approaches are showing their limits.
Specialized technical expertise is becoming decisive in the fight against these advanced threats. As our fieldwork shows, data recovery often requires innovative solutions that go beyond conventional tools, including those provided by the cybercriminals themselves.
The organizations that survive this new generation of ransomware will be those that have invested in resilience rather than mere protection, developing the capacity for continuous adaptation and innovation.
Is your business paralyzed by ransomware?
SOS Ransomware is at your side 24/7/365 to recover your encrypted data. With over 100,000 successful recoveries and recognized expertise in all types of ransomware, our specialists intervene quickly on your affected systems.
Our emergency services:
- Data recovery from servers, virtual machines, databases and backups
- Specialized Veeam expertise and complex RAID systems
- Remote or on-siteintervention to suit your needs
- Free evaluation to prove our expertise
Don’t pay ransom without consulting our experts. Our success rate of over 80% and our tailor-made solutions can recover your data even if official decryptors fail.
Main article sources :
- SOCRadar: Dark Web Profile: Lynx Ransomware
- Acronis TRU: MSPs a top target for Akira and Lynx ransomware
- Group-IB: Cat’s out of the bag: Lynx Ransomware
- Fortinet: Ransomware Roundup – Lynx
- Picus Security: Lynx Ransomware
- Nextron Systems: In-Depth Analysis of Lynx Ransomware
- Palo Alto Unit 42 : Lynx Ransomware: A Rebranding of INC Ransomware
- Bleeping Computer : INC ransomware source code selling on hacking forums for $300,000
- Darktrace : New Threat on the Prowl: Investigating Lynx Ransomware
- Ransomware live : Lynx
