The security of IT systems is a major issue for businesses, governments and even individuals. At a time when cyber-attacks have become commonplace, one of the most frequent threats is theDenial of Service (DoS ) or Distributed Denial of Service (DDoS)attack. This attack can be potentially devastating, especially for e-commerce site owners: just imagine your store being completely inaccessible and your customers going elsewhere. To fully understand what lies behind this type of attack, we’ll define the terms, explain the differences and look at the main targets.
Table des matières
ToggleWhat is a denial-of-service (DoS) attack?
DoS attacks are designed to render inaccessible, or at least temporarily disrupt, a network, online service or storage device connected to the Internet. The aim of a malicious actor is generally to saturate the capacity of a resource or bandwidth, thus preventing any legitimate activity on it. Some of the techniques used include transmitting too many requests, often under a false identity, or broadcasting messages specially designed to cause errors in the targeted servers. Among the most common DoS attacks are flood attacks, where the attacker sends a multitude of connection requests to saturate server resources.
How does a DoS attack work?
- Traffic flood: the attacker uses one computer, or sometimes several, to send a massive amount of data or requests to the target server. This saturates the server’s bandwidth, slowing down or interrupting services for legitimate users. A common technique is the SYN flood attack, which involves sending connection requests to a server without ever establishing the connection. These requests continue to flood until all open ports are saturated, preventing legitimate users from accessing the server.
- Exploitation of vulnerabilities: the attacker exploits security flaws in a system, causing errors or failures that hinder its smooth operation. Teardrop attacks, which exploit vulnerabilities in IP packet fragmentation, are an example of this method.
What is a distributed denial-of-service (DDoS) attack?
DDoS attacks are similar to DoS attacks in that they also aim to make an online network or service inaccessible. However, they differ in one crucial respect: whereas DoS attacks generally originate from a single computer, DDoS attacks are carried out by several machines simultaneously, often under the control of a single malicious actor. This approach has several advantages for the attacker:
- It generates a much higher volume of traffic, increasing the attack’s chances of success.
- Spreading the attack makes its origin difficult to identify, and adds an extra layer of anonymity for the cybercriminals involved.
- Some DDoS attacks use a network of compromised or malware-infected machines, known as a botnet, which execute the attack without the knowledge of their legitimate owners. Botnets are often used in rebound attacks, where the attacker uses intermediate machines to mask the origin of the attack.
DDoS attack techniques
There are several ways to carry out a DDoS attack:
- Amplification attack: the attacker uses intermediary machines to amplify the volume of traffic sent to the target server. The best-known technique is DNS amplification, in which DNS queries are sent to servers using the victim’s IP address as the sender. The responses, often much larger than the queries, flood the victim’s connection.
- Attack by exhaustion: the attacker seeks to consume all the resources of the target system, notably by saturating its memory, hard disks or processors, resulting in a slowdown or even a complete shutdown of the service.
- Application-level attacks: also known as “Layer 7 attacks”, these target specific applications running on a server, rather than the network itself. These attacks generally exploit very specific vulnerabilities and can be more difficult to detect and counter than other types of DDoS attack. The “ping of death”, an attack that sends malformed IP packets to crash the target system, is an example in this category.
And for anyone who wants to deepen their understanding of DoS and DDoS attacks in a visual and detailed way, we highly recommend watching this great video. You’ll find clear, concise explanations of how these complex computer attacks work and their impact.
Prime targets for DoS and DDoS attacks
Almost all online organizations and entities are now at risk of a DoS or DDoS attack. Recurring targets include:
- Online services and cloud providers, as a disruption to their service renders their customers helpless and has an immediate impact on their business.
- E-commerce sites, which can lose huge sums of money if their site is unavailable for long periods. Cybercriminals may also try to use DoS attacks to extort money from site owners in exchange for stopping the attack.
- Governments, national agencies and financial institutions also represent prime targets for malicious actors, particularly for political or ideological purposes.
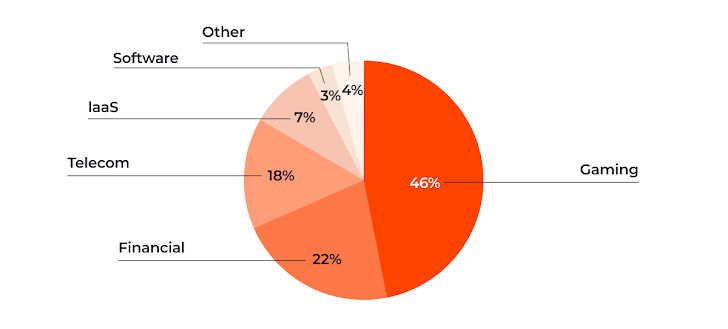
The latest Gcore Radar report sheds light on the industries specifically targeted by DDoS attacks in recent months. According to the report, the gaming industry remains the most affected, suffering almost 46% of attacks, closely followed by the financial sector with 22%. Telecoms providers, Infrastructure as a Service (IaaS) and IT software vendors are also among the prime targets, illustrating the need for these sectors to strengthen their security measures.
New trends in DDoS attacks according to Gcore
The cyberthreat landscape is constantly evolving, and Gcore’s latest semi-annual report highlights some worrying trends that merit particular attention.
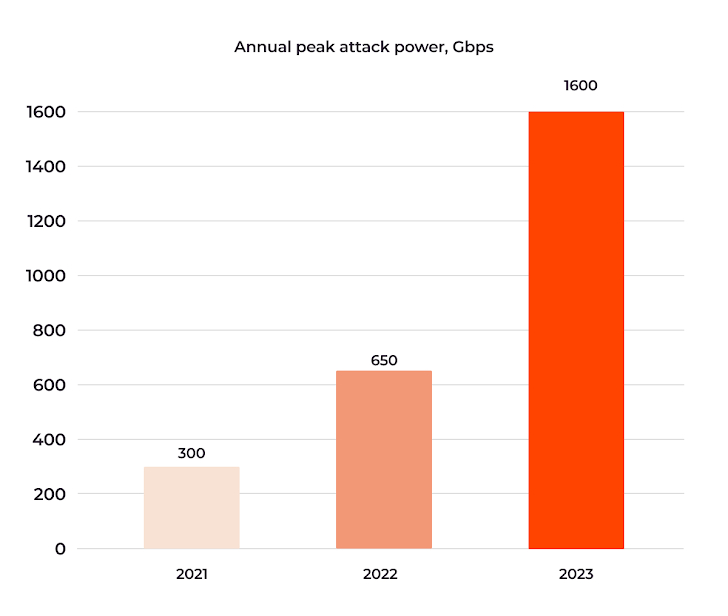
Attack power: all-time highs
The report reveals an annual increase of over 100% in the maximum volume of DDoS attacks, peaking at 1.6 Tbit/s in the second half of 2023. This escalation means that we are entering an era where attacks are now measured in terabits, posing an unprecedented challenge for cybersecurity.
Variability in attack duration
Attack duration varies widely, from a few minutes to nine hours. This variability makes short attacks particularly insidious, as they are harder to detect and mitigate, while prolonged attacks can cause significant damage through their persistence.
Overview of attack methods
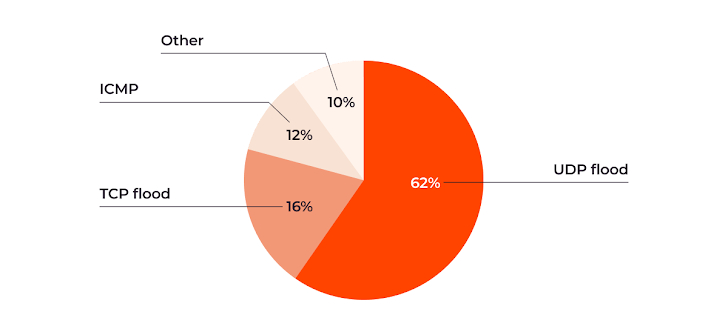
UDP floods dominate the landscape, accounting for 62% of observed attacks. TCP Flood and ICMP attacks also remain widespread, underlining the diversity of threats facing organizations.
The unusual arsenal of cyberattacks: from toothbrushes to babyphones
What if objects as mundane as connected toothbrushes, babyphones and surveillance cameras could be transformed into tools for DDoS attacks? Yes, you read that right: toothbrushes, among other everyday gadgets, become vectors for cyberthreats. While the apparent absurdity of this scenario might make you smile, it hides a far more serious reality that has already been observed since 2016. These devices, so innocent yet so integral to our digital daily lives, can be hijacked to paralyze corporate websites, demonstrating the vulnerability of our connected environment. This exploitation of the Internet of Things (IoT ) highlights the sometimes staggering ingenuity of cybercriminals, and underlines theurgent need to secure every connected device, even those that seem the most innocuous.
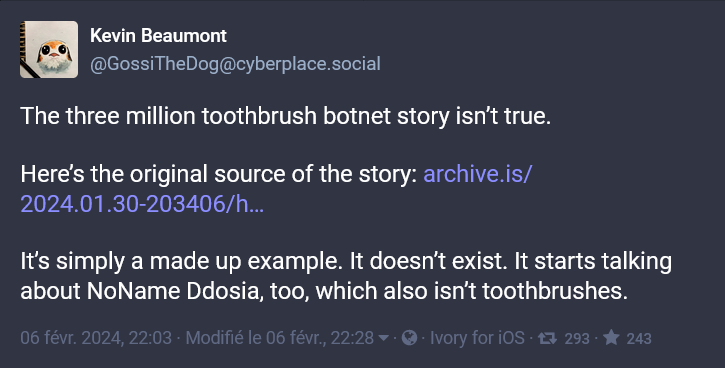
Update 07.02.2024:
According to cybersecurity expert Kevin Beaumont, the anecdote about the botnet of three million connected toothbrushes is the result of a misinterpretation. He points out that the example, although widely reported on the Internet, does not correspond to a proven reality, but rather to a hypothetical illustration of the risks associated with IoT. For more details, see the Forbes article and Kevin Beaumont’s original post on Mastodon.
Although the majority of DoS or DDoS attacks do not cause data loss or demand ransom payments, they do result in the targeted company spending time, money and various resources to restore its strategic operations. Faced with these threats, it is essential for all online services and IT managers to take all necessary measures to secure their systems and prevent or reduce the potential impact of these attacks.
