The sophistication of Deadglyph malware and its ability to evade detection make it a particularly formidable threat.
Once installed, it can collect sensitive data from the compromised system and give cybercriminals extensive control over the infected computer.
It was used in a cyberespionage attack against a government agency in the Middle East. The malware is attributed to the Stealth Falcon APT hacking group (also known as Project Raven or FruityArmor), a group backed by the state of the United Arab Emirates (UAE). This group has been known to target activists, journalists and dissidents for almost a decade.
At the LABScon conference dedicated to cybersecurity, ESET expert Filip Jurčacko revealed his findings on a recent modular malware and how it infects Windows systems. While ESET doesn’t have exact details on how the infection starts, it’s likely that a malicious executable file, such as an installer, is involved. Nevertheless, thanks to the key elements of the infection chain recovered, ESET has been able to decipher how the malware works and its evasion techniques.
Companies must remain vigilant and implement preventive measures to protect themselves against this growing threat. These measures include
- Regular updating of operating systems and software to correct vulnerabilities.
- Using effective antivirus solutions to detect and block threats such as Deadglyph.
- Raising employee awareness of the social engineering techniques often exploited by malicious actors to spread their malware.
Table des matières
ToggleThe Deadglyph load chain
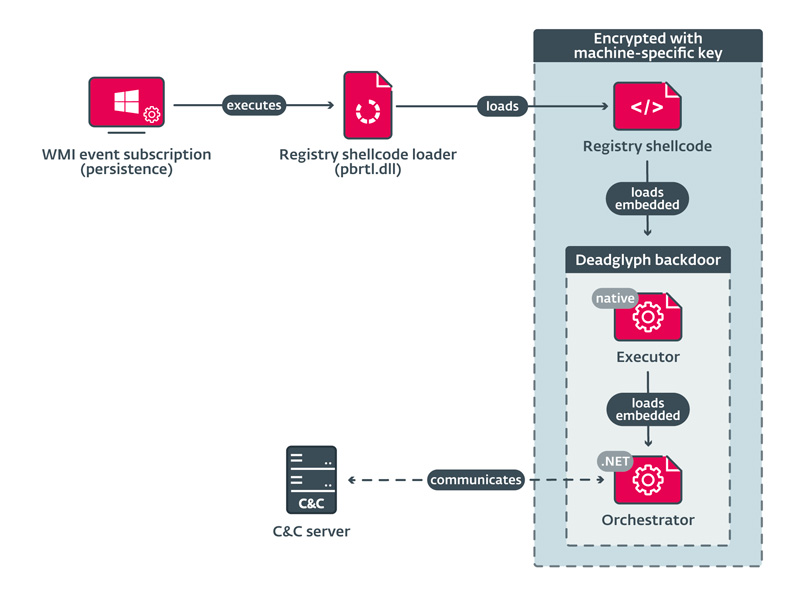
The Deadglyph load chain, an emerging threat in cyberspace, uses sophisticated techniques to infect Windows systems. It starts with a registry shellcode loader that extracts code from the Windows registry to load the Executor component. This then loads the Orchestrator component.
One of the deception techniques used is the homoglyphic attack found in the VERSIONINFO resource. Malicious actors use distinct Greek and Cyrillic Unicode characters to mimic Microsoft information and thus appear as a legitimate Windows file.
The modular nature of Deadglyph malware
What makes Deadglyph particularly dangerous is its modular nature. It downloads new modules from the C2 (command and control) server containing different shellcodes to be executed by the Executor component. These modules have access to Windows APIs and custom Executor APIs, the latter offering 39 functions that enable file operations, executable loading, Token Impersonation access, encryption and hashing.
The information collector
The Information Collector uses WMI (Windows Management Instrumentation) queries to gather a variety of information about the compromised system. This includes details of the operating system, network adapters, installed software, drives, services, drivers, processes, users, environment variables and security software.
The process creator
One of the key steps is the use of the Process Builder, a tool that allows specific commands to be executed in the form of new processes. The results of these commands are then delivered to the Orchestrator component. This method enables malicious actors to effectively control the infected system, discreetly initiating various actions on it.
Evasion methods employed by Deadglyph malware
In addition to its ingenious modular design, Deadglyph malware also employs advanced techniques to conceal itself within the compromised system and evade detection. It mainly employs a homoglyphic attack, a spoofing technique involving the use of visually similar Unicode characters (usually belonging to different writing systems) to fool the user or security mechanisms.
By imitating Microsoft information through these characters, the malware manages to pass for a legitimate Windows file. In order to operate undetected, the malware also encrypts its sensitive data and communication with the C2 server. This makes it difficult for security researchers to analyze the malware’s behavior and detect its presence.
In a nutshell
The Deadglyph malware is an impressive example of the complexity and rapid evolution of contemporary computer threats. It perfectly illustrates the challenges of cybersecurity for individuals and businesses alike.
