Phishing is a method used by fraudsters to obtain confidential information such as passwords and bank details. This online scam usually takes the form of e-mails or messages on social networks imitating official organizations such as banks or government agencies. Phishing is also often the gateway to ransomware.
Table des matières
ToggleHow does phishing work?
The main aim of phishing is to deceive victims into believing that they are communicating with a legitimate organization. Fraudsters create fake websites, usually very similar to the official websites of the organizations concerned, in order to deceive Internet users. They then try to trick them into filling in forms containing their personal, financial or password information.
The means of communication used
Emails and text messages are the main methods used by fraudsters to reach their victims. They send personalized, well-written messages urging the recipient to log on to the fraudulent site. By clicking on a link contained in the email or SMS, the Internet user is redirected to the fake site and trapped.
Other forms of communication are also exploited by cybercriminals, such as social networks, where fake profiles are created to contact Internet users.
Persuasion techniques
A fraudulent e-mail or message can adopt a number of different strategies to entice the victim to click on the link contained in the message. The most common are :
- Urgency: The fraudster often plays on fear by claiming that access to the user’s account is blocked and that he or she needs to enter information to unblock it.
- Identity verification: The fraudster explains that a hacking attempt has been detected on the victim’s account, and asks them to confirm their identity to secure their access.
- False promotion: The fraudster offers a gift or benefit to entice the victim to visit the fraudulent site and enter their personal data.
“How to recognize a phishing e-mail? – Consomag in partnership with INC
The different types of phishing
The threat of phishing is constantly on the increase, affecting individuals, businesses and organizations alike. There are different methods used by crooks of all stripes, ranging from fraudulent emails to more sophisticated attacks such as smishing and vishing. It’s important to understand these techniques to stay vigilant and protect yourself.
- Email phishing: The most common type, where fraudsters send emails appearing to come from legitimate organizations to trick recipients into revealing personal information.
- Smishing (SMS phishing): Similar to email phishing, but fraudulent messages are sent by SMS. These messages may contain links to phishing sites or directly request sensitive information.
- Phishing on social networks: Attackers create fake profiles or hack into existing accounts to send direct messages or post content urging users to click on malicious links.
- Vishing (Voice phishing): Here, fraudsters use telephone calls to extract personal or financial information. They often pose as representatives of banks or other institutions.
- Spear phishing: These attacks are customized to target specific individuals or organizations. Fraudsters carry out in-depth research on their victims to make their attempts more convincing.
- Whaling: A form of spear phishing targeting a company’s top executives. The e-mails appear to come from reliable sources and often deal with financial or confidential business matters.
- Clone phishing: In this variant, attackers copy a legitimate email received by the victim, but replace the links or attachments with malicious versions.
By encouraging users to divulge personal information, phishing can also pave the way for the stealthy installation of Trojans on the victim’s computer, compromising security and confidentiality. Companies are also exposed to this risk, which jeopardizes their IT security and confidential data.
How to detect phishing?
When in doubt about a message or website, here are a few tips for detecting possible phishing:
- Analyze the sender: If you don’t know the sender of the message, or if it looks suspicious, it’s advisable not to click on any links in the message, and not to provide any confidential information.
- Spot spelling mistakes: Fraudulent messages and sites often contain numerous spelling and syntax errors.
- Check the URL of the site: By passing the mouse cursor over the link contained in the message, without clicking on it, it is usually possible to display the URL address to which the link points. If the URL does not correspond to the official site of the organization concerned, it’s best to refrain from clicking.
- Use common sense: If it looks too good to be true, chances are it’s a scam.
Some examples of common phishing scams
Phishing scams are diverse and can take many forms, each aimed at deceiving victims to obtain confidential information. Among the most common examples are fraudulent emails imitating trusted entities and asking recipients to verify their account information or reset their passwords. These emails often appear legitimate, with logos and formats similar to those of real bank emails.
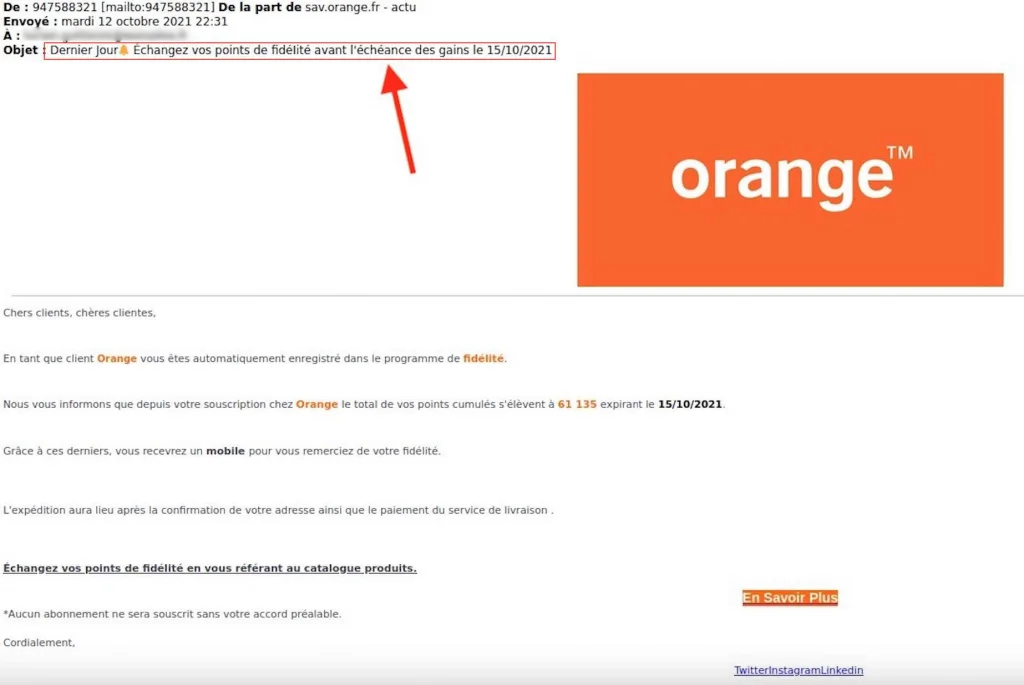
Other common examples include emails pretending to be from tax authorities or Internet service providers, which use urgency, fear or a tempting offer to spur rapid action. These emails can include links to fraudulent websites that look remarkably similar to official sites. It’s crucial to remain vigilant and check the authenticity of sources before responding to such solicitations.
Don’t confuse phishing with fishing
It’s important to distinguish between “phishing” and “fishing”, two terms which, although phonetically similar, refer to distinct realities. Phishing combines the concepts of “fishing” and “phreaking”. The term refers to a cybercriminal practice aimed at impersonating trusted organizations in order to obtain sensitive information such as login credentials or banking data, often via fraudulent e-mails, messages or websites.
- Phishing is an online fraud technique in which cybercriminals impersonate trusted entities through emails, messages or websites. Their aim is to obtain sensitive information such as login credentials and financial data, which can lead to security compromises and identity theft.
- Fishing is not directly related to cybercrime. The term is often used as a spelling error or to make a pun on the analogy between “fishing” and “phishing”.
How can I protect myself against phishing?
It’s essential to adopt a few best practices to combat phishing:
- Keep your software up to date: Keeping your operating system, browser and antivirus software up to date reduces the risk of security breaches.
- Don’t provide sensitive information by e-mail: Official bodies never send requests for confidential information by e-mail.
- Install antivirus software and spam filters: These tools can help identify and block phishing e-mails and related malware.
- Use a password manager: This prevents you from entering your login details on a fake site, as password managers only issue passwords for real registered sites.
- Acquire a culture of cybersecurity: Regular training and information on new phishing methods and online security best practices is crucial.
- Maintain constant vigilance: Even if protection techniques and tools are evolving, vigilance remains your best ally. Always be skeptical of requests for sensitive information, even if they appear to come from reliable sources.
In case of doubt, or if you think you’ve been the victim of phishing, it’s important to contact the relevant organization (bank, administration…) as soon as possible to take the necessary steps to prevent fraudulent use of your personal and financial information.
