Coveware’s latest 2023 quarterly report points to a striking development in the fight against ransomware: a dramatic drop in ransom payments, to a historically low level of 29%. This significant decline is not merely anecdotal, but a remarkable example of how companies are adjusting their defense strategies against cyberattacks, strengthening their resilience and increasing their awareness of the risks associated with ransomware payments.
Table des matières
ToggleSignificant drop in ransom payments
Coveware, a specialist in cyber-extortion crisis management, notes a remarkable trend: the decline in ransom payments demanded by ransomware gangs. This development, which sees the payment rate plummet to an all-time low, reflects a significant shift in organizations’ defensive strategies, and provides us with a detailed overview of current trends in ransomware attacks.
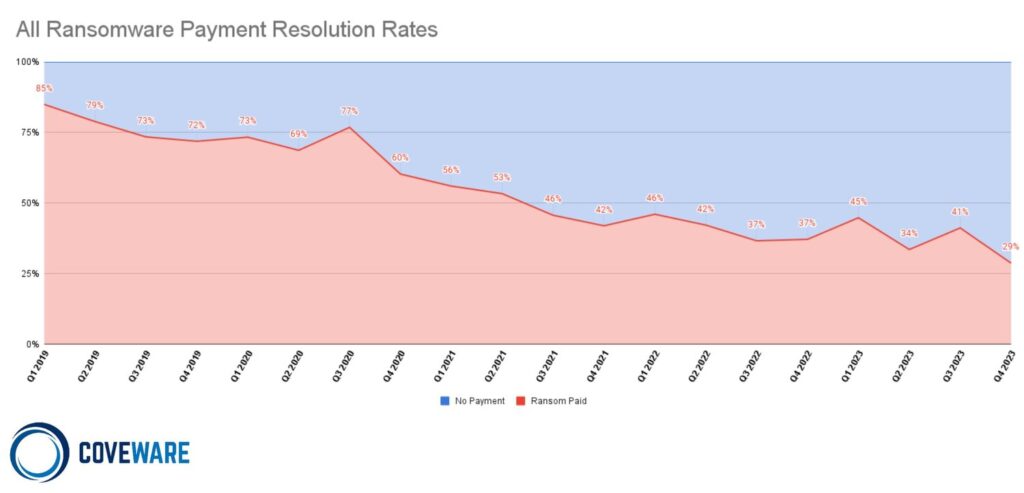
Several factors have contributed to this trend:
1. Investments in cybersecurity
The continuous improvement of cybersecurity protection measures within companies has played a leading role. Increased investment in advanced security solutions, employee training on the risks of phishing and other common attack vectors, and the development of robust incident response plans have strengthened the resilience of those involved.
2 . Increased risk awareness
At the same time, awareness of the legal and reputational implications associated with ransom payments has also played an important role. The fear of funding criminal activities and encouraging further attacks also weighed in the balance, prompting companies to seek alternatives to ransom payments.
3. The emergence of stricter regulations
The emergence of stricter regulations and guidelines encouraging the reporting of ransomware incidents to the relevant authorities has fostered a culture of transparency and cooperation. This dynamic has enabled threats to be better understood and countered, reducing the need to give in to cybercriminals’ demands.
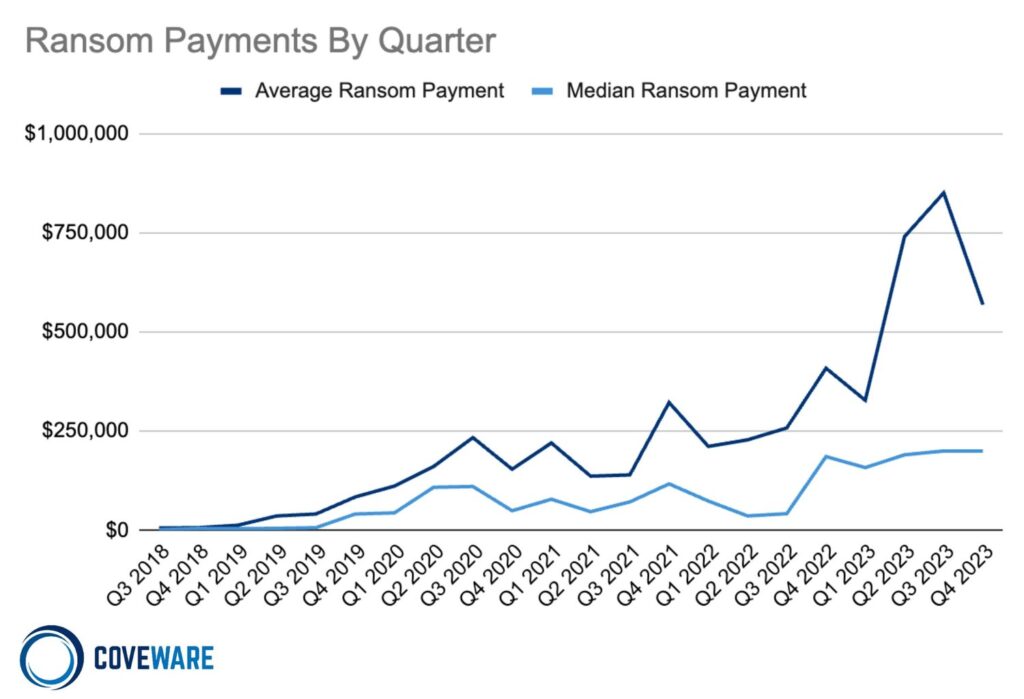
Debate on banning ransom payments
The Coveware report addresses a recurring topic of discussion in the cybersecurity field: the effectiveness and implications of a legal ban on ransom payments. This proposal aims to reduce the financial incentives for cybercriminals by eliminating their main source of revenue. On the other hand, Coveware highlights several critical points in this debate.
1. Arguments in favor of a ban
The idea behind a ban is to discourage attacks by making payments illegal, with the hope that this will reduce the profitability of ransomware operations. Supporters believe it could be an important step towards cybercriminals abandoning plans to target organizations in jurisdictions where payments are banned. However, early experiments with bans, such as those seen in several US states, have shown mixed results, with little evidence of a significant reduction in malicious attacks despite the regulations in place, as Coveware has found.
2. The potential consequences of a total ban on ransom payments
A total ban on ransomware payments could have unintended consequences for the cybersecurity landscape. One major concern is the creation of a black market for ransomware payment services, making transactions even more opaque and difficult to trace. Coveware highlights a potential ethical dilemma for businesses facing ransomware attacks, as some victims could be forced to choose between paying the ransom and irreversibly losing vital data. Cybercriminals are aware that their targets will attempt to circumvent the rules if necessary, and are even prepared to assist them in doing so in order to get the ransom paid. It’s also common for gangs not to bother checking whether a victim is in a state where payments are banned.
A ban of this kind could possibly compromise cooperation between victims and law enforcement authorities. The prospect of severe penalties for breaking the law could deter companies from reporting ransomware incidents, creating a climate of opacity and mistrust. This raises questions about the effectiveness of strict legislative measures to combat ransomware, while maintaining an adequate level of collaboration and transparency between the players involved.
In fact, the FBI had publicly stated on this subject:“If we now ban ransom payments, American companies risk being confronted with another form of extortion, namely blackmail to pay a ransom and refusal to communicate it to the authorities.”
3. Assessing ransomware bans
Guidelines issued by the US Treasury in 2021 and the New York Department of Financial Services (NYDFS) in 2023 have encouraged the adoption of vigilance and transparency practices, and prompted relevant entities to develop more sophisticated protection strategies. However, despite these advances, a total ban on ransom payments could prove ineffective in practice. It risks shifting the flow of money to a black market, without guaranteeing a real increase in security spending on the part of companies. The latter, often influenced by short-term considerations, could be tempted to circumvent the ban, compromising its effectiveness in the fight against ransomware.
4. Coveware’s opinion
Coveware advocates a strategic approach to the fight against ransomware. Rather than opting for a total ban on ransomware payments, Coveware proposesencouraging good practice through incentives, while reinforcing existing regulatory measures. This could include financial incentives and support for companies adopting robust cybersecurity measures, as well as tougher penalties for those failing to meet standards of reporting and collaboration with the authorities.
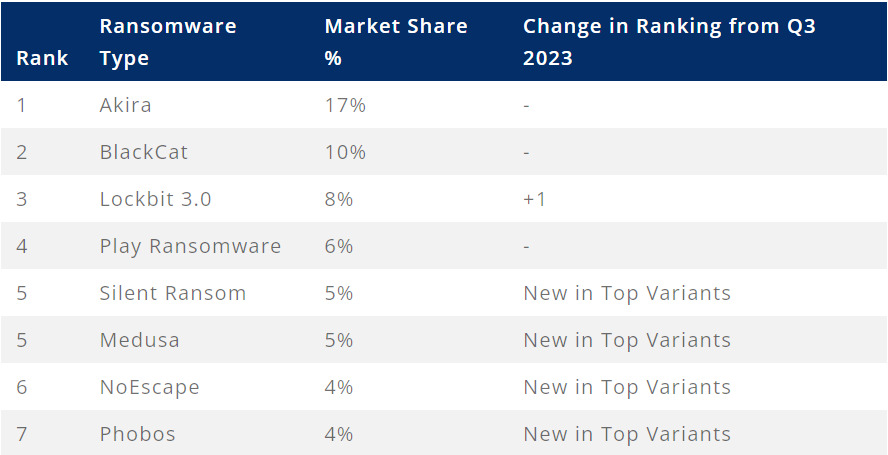
The most common ransomware variants in the fourth quarter of 2023
Several variants particularly marked the ransomware landscape with their increased activity at the end of 2023. Among them, Akira stands out with 17% of incidents recorded, illustrating its ability to bypass traditional security measures and carry out effective targeted attacks.
BlackCat, with a 10% market share, also maintained a significant presence, although its activity declined sharply in December following the intervention and seizure of its infrastructure by law enforcement agencies. This action demonstrates the potential impact of efforts to combat cyberthreats when effectively coordinated.
Lockbit 3.0 increases its market share to 8%. Notorious for its aggressive approach and high ransom demands, it is primarily aimed at large-scale targets, as demonstrated by the recent attack on aerospace giant Boeing.
The fourth quarter saw the arrival of newcomers Silent Ransom and Medusa, each with a 5% share, as well as NoEscape and Phobos with 4%. The arrival of these new variants testifies to the growing diversity of the ransomware landscape, and reminds us of the importance of unfailing vigilance and preparation in the face of evolving cyberthreats.
Most common attack vectors and tactics
The report highlights the diversity of attack vectors and tactics used by hackers to infiltrate corporate networks. The trends observed show a classic matrix of actors, with a notable distinction between those targeting small businesses and those targeting medium-sized to large enterprises.
For small businesses, brute-force RDP (Remote Desktop Protocol) attacks remain a preferred entry vector, often exploiting inadequate security configurations. This attack method reminds us of the vital importance of securing remote access with robust password policies and the activation of multi-factor authentication.
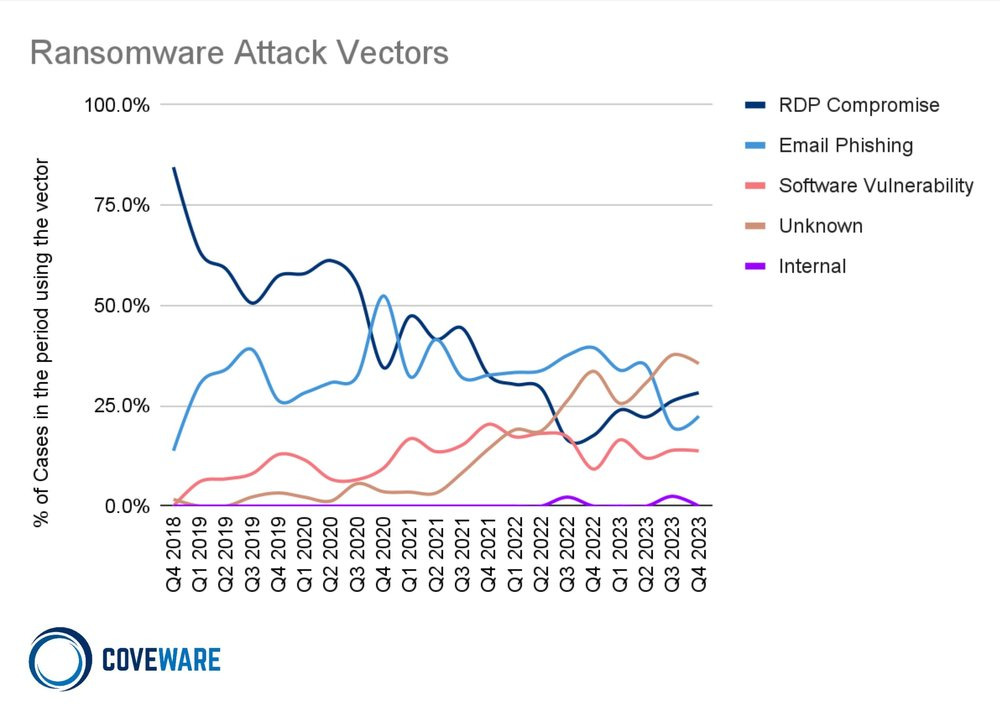
Attackers targeting medium and large enterprises have tended to rely on the exploitation of known vulnerabilities (CVE) and increasingly sophisticated social engineering techniques, including SIM swap attacks on executives to appropriate MFA authentication codes sent by SMS. The Cisco ASA vulnerability (CVE-2023-20269) has been particularly exploited by Akira, mainly affecting software services companies and managed service providers.
Significant differences can therefore be seen in the strategies implemented: while RDP/VPN attacks are generally linked to small businesses and mainly focused on encryption, social engineering attacks are more likely to target large companies in an attempt to exfiltrate data.
Sector impact and size of companies affected
Coveware’s Q4 2023 report highlights the varied impact of ransomware attacks on different sectors and company sizes. A key observation here is the drop in the median size of affected organizations, which fell to 231 employees, indicating a 32% decrease on the previous quarter. This trend suggests that, despite high-profile incidents attracting media attention, ransomware remains primarily a problem for small and medium-sized businesses.
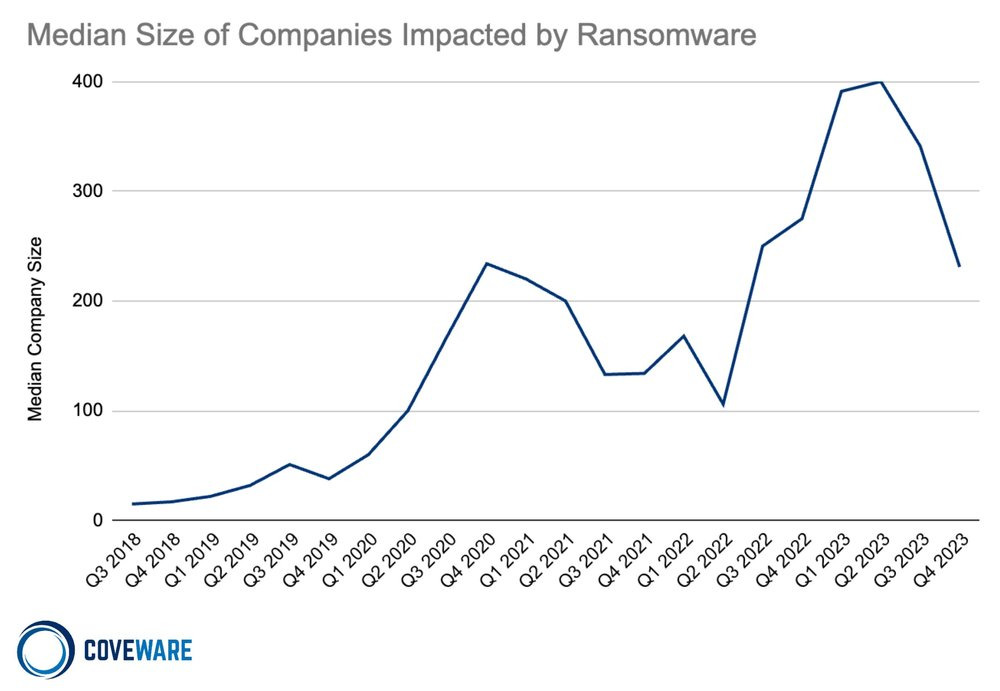
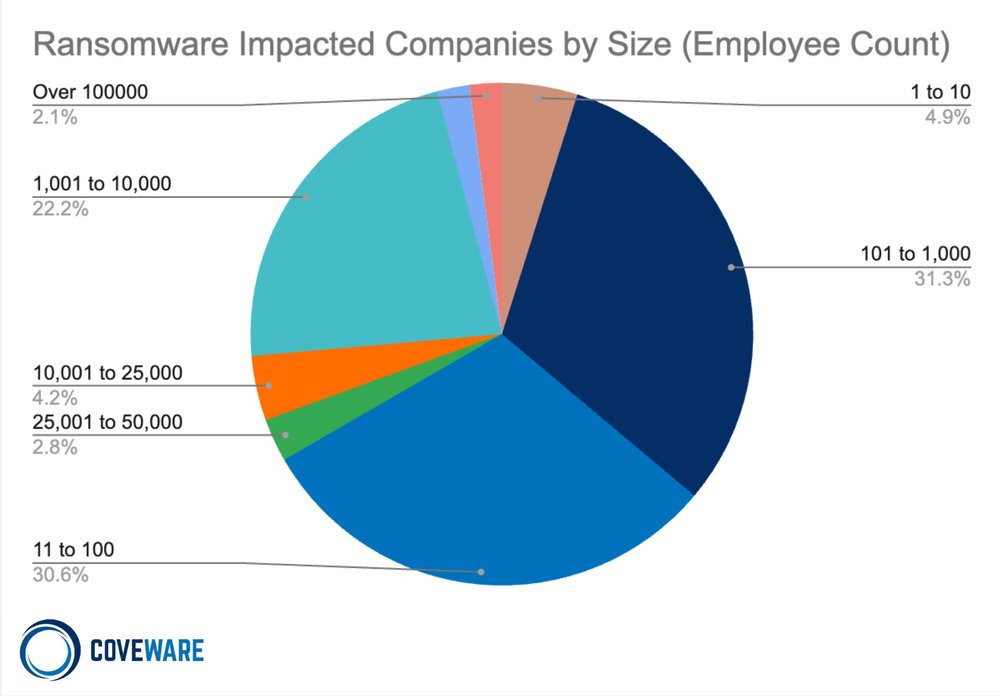
The most affected sectors remain constant, with professional services, healthcare, consumer services and the public sector topping the list. This consistency reflects the ubiquitous nature of ransomware, which does not discriminate according to industry type. However, the increased prevalence in certain sectors can be attributed to general characteristics that make these industries easier targets, such as a lack of cybersecurity resources or obsolete IT systems.
Trend data published by Coveware highlights that the risk of being targeted by a particular ransomware group depends primarily on the size of the company and its reported revenues, rather than on the industry sector. Some cybercriminal groups specifically target companies that exceed a certain size or turnover threshold, in order to derive more profit from attacking potentially more lucrative victims.
As we enter 2024, Coveware’s latest 2023 Quarterly Report offers us an informed and in-depth perspective on the current state of the ransomware threat. The historic decline in ransomware payments, while a positive indicator of growing business resilience, does not mark the end of the fight against these cyberthreats. On the contrary, it highlights the importance of continued vigilance, meticulous preparation and seamless collaboration between the private and public sectors.
Concerted efforts to strengthen cybersecurity defenses, determined action by law enforcement and a commitment to international cooperation are all pillars on which our collective fight against ransomware rests. Coveware reminds us that, despite the challenges and ever-changing threat landscape, perseverance, security innovation and global solidarity are our best weapons for protecting our digital future.
By learning from the data and analysis provided by Coveware, companies of all sizes can fine-tune their cybersecurity strategies to not only withstand ransomware attacks, but also contribute to a safer digital environment for all. The road is long, but with every step forward, we strengthen our collective ability to overcome threats and secure our digital space against malicious actors.
