The recent release of a decryption tool for the Babuk Tortilla ransomware is part of a proactive response to the growing challenges posed by cyber threats. This breakthrough was made possible by a police operation in Amsterdam, which led to the arrest of a threat actor and the production of a decryptor with the help of Cisco Talos cybersecurity experts. This decryptor, including all known private keys, enables victims to recover their files encrypted by various Babuk variants. This collaboration between law enforcement and cybersecurity researchers underlines the importance of intelligence and cooperation in the fight against digital threats, reflecting an adaptive and resilient approach in the face of constantly evolving cybercriminal tactics.
Table des matières
ToggleBabuk Tortilla: a fearsome and feared ransomware
The Babuk ransomware, which first appeared in 2021, quickly gained notoriety in the cybersecurity world for its targeted attacks on key sectors such as healthcare, manufacturing, logistics and utilities, including critical infrastructure. Its ability to effectively encrypt victims’ data and disrupt backup processes has been a standout feature. Babuk is distinguished in particular by its attack method, which includes the deletion of volume shadow copies, making data recovery even more difficult for victims. This specificity marked its entry into the world of cyberthreats.
Designed to be compiled on a variety of hardware and software platforms, Babuk used a ransomware generator for its configuration. Versions for Windows and ARM for Linux were the most common, but variants for ESX and an older 32-bit PE executable were also seen.
Babuk source code leaked on a forum and clones exploded
A major turning point in the Babuk story was the leak of its source code to an online forum in September 2021. This leak gave other cybercriminals access to an advanced ransomware tool and enabled them to develop their own variants, leading to an increase in cyberattacks using similar methods. Cisco Talos then analyzed the operations of ransomware groups using Babuk’s source code, including the RA group and other players. These analyses revealed that ten different groups were using Babuk source code for their operations, demonstrating the widespread impact of the source code leak on the cyberthreat ecosystem. As a result, Babuk has become an even more formidable player in the threat ecosystem, demonstrating the ability of cybercriminals to adapt and evolve rapidly to maximize the impact and profitability of their attacks.
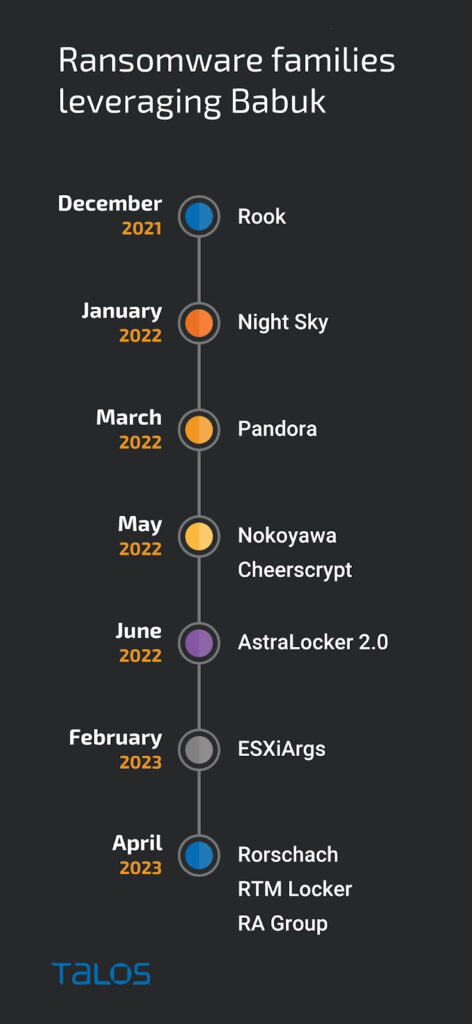
Tortilla campaign and infection technique
In October 2021, Cisco Talos discovered a campaign using the Tortilla ransomware, a variant of Babuk, targeting vulnerable Microsoft Exchange servers. The campaign exploited the ProxyShell vulnerability to deploy the ransomware in the victims’ environment. The infection technique involved an intermediate unpacking module hosted on a pastebin.com clone, pastebin.pl, which was downloaded and decoded in memory before the final payload was decrypted and executed.
Police operation and Cisco Talos collaboration
The police operation in Amsterdam marked a key moment in the fight against the Babuk Tortilla ransomware. The operation was carried out in close collaboration with Cisco Talos, a team of leading cybersecurity researchers. Their role was essential in gathering intelligence on the malware, enabling the Dutch police to locate and apprehend the key player behind the malware.
Cisco Talos not only helped identify the suspect, but also played a key role in the technical analysis of the ransomware. Their expertise made it possible to decrypt the ransomware code, recover the decryption key and share it with Avast Threat Labs engineers. The latter were responsible for developing and maintaining the decryptor for several other Babuk variants.
“Cisco Talos shared the key with its peers at Avast to include it in the Avast Babuk decryptor released in 2021,” said Vanja Svajcer in a post on the Cisco Talos blog. “The decryptor includes all known private keys, enabling many users to recover their files once encrypted by different variants of the Babuk ransomware.”
The collaboration between Cisco Talos and the Dutch police has also led to the creation of a comprehensive decryption tool, including all known private keys. This tool has been made available to the public, enabling victims to recover their files encrypted by different variants of Babuk. This step marks a significant advance in the availability of effective tools to counter the devastating effects of Babuk, offering a glimmer of hope to victims of this fearsome ransomware.
This episode in the fight against ransomware demonstrates the importance of cooperation between law enforcement and cybersecurity experts to effectively counter digital threats. The operation also highlighted the need for a proactive, collaborative approach to dealing with increasingly sophisticated cyber attacks. It underlined the importance of cybersecurity intelligence and international cooperation in the fight against cybercriminals.
How and where to download the Babuk Tortilla decryptor
To access the Babuk Tortilla decryptor, victims must follow a specific technical process, detailed by Cisco Talos experts. This decryptor, developed from Babuk’s source code and its generator, is designed to neutralize the ransomware’s sophisticated encryption mechanism. Vanja Svajcer from Cisco Talos explained that the ransomware uses a unique public/private key pair to encrypt victims’ data. The public key, embedded in the ransomware payload, encrypts the symmetric key of each file. This symmetrical key is then added to the end of each encrypted file, enabling the decryptor to recognize and decrypt the affected files.
Victims of the Babuk Tortilla ransomware can download the decryption tool free of charge. This decryptor is available on the NoMoreRansom decryptors page and on the Avast Babuk decryptor download page. These platforms offer a reliable and secure solution for recovering encrypted files without having to pay a ransom.
Users can access these platforms to download the single decryptor containing all Babuk keys known to date, and do not have to choose between competing decryptors for individual variants. The generic Avast Babuk decryptor was already being used as the de facto standard Babuk decryptor by many affected users, so it made perfect sense for it to be updated with the keys that Talos recovered from the Tortilla decryptor.
It is important to note that the Babuk decryptor is a sophisticated tool, designed to run on multiple hardware and software platforms. Users should carefully follow the instructions provided to ensure effective recovery of their data.
The Babuk Tortilla story and the effective response to this threat underline the crucial importance of collaboration between law enforcement and cybersecurity experts. The police operation in Amsterdam and the work of Cisco Talos not only neutralized a significant threat, but also provided valuable tools and knowledge to prevent future attacks. This victory against Babuk Tortilla demonstrates that, despite the constant evolution of cyber threats, coordinated and innovative responses can provide concrete and effective solutions.
