Attackers from the Qilin group have taken their operations to a new level of sophistication by deploying a Linux variant of their ransomware directly on Windows systems. This cross-platform execution technique, combined with the exploitation of vulnerable drivers and the systematic targeting of backup infrastructures, illustrates the worrying evolution of ransomware tactics in 2025.
Table des matières
ToggleAn unabated threat in 2025
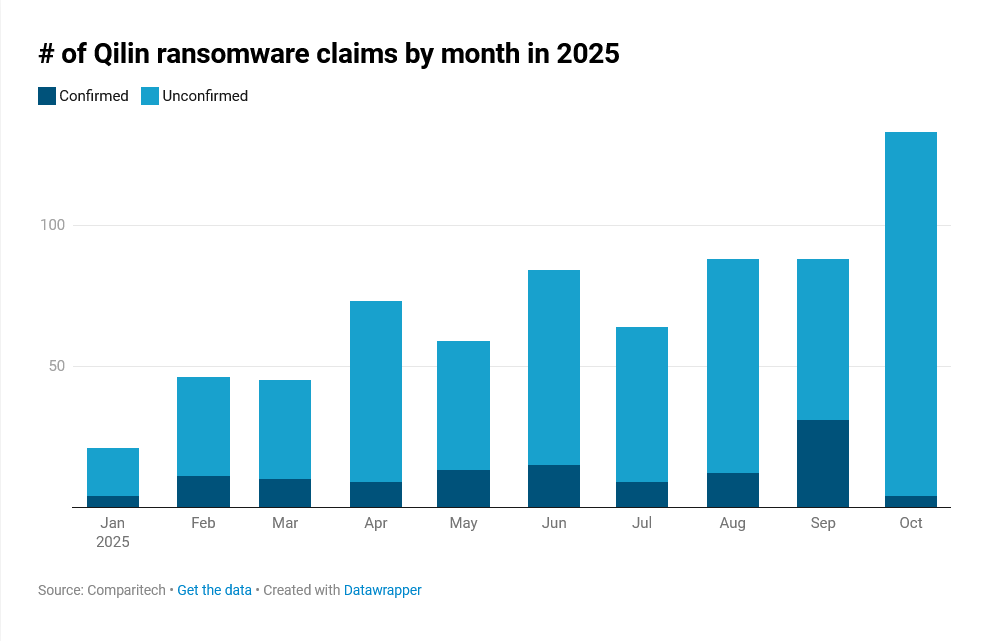
The Qilin group, also known by the aliases Agenda, Gold Feather and Water Galura, has established itself as one of the most active ransomware-as-a-service (RaaS) operations of 2025. Active since July 2022, this Russian-speaking group employs a double extortion strategy combining data encryption and the threat of publication of stolen information to increase the pressure on its victims. Since January, the operation has claimed over 40 victims per month on its leak site, with an impressive peak of 100 cases recorded in June. August and September each recorded 84 victims, confirming the group’s upward trajectory.
According to data compiled by Cisco Talos from victims listed on the Qilin leak site, the sectors most affected are manufacturing (23% of cases), professional and scientific services (18%), and wholesale trade (10%). The health, construction, retail, education and finance sectors show similar levels of impact, with an average of around 5% each.
With over 700 victims in 62 countries since the start of the year, Qilin is proving particularly formidable. Geographically, the USA, Canada, the UK, France and Germany are the most targeted territories.
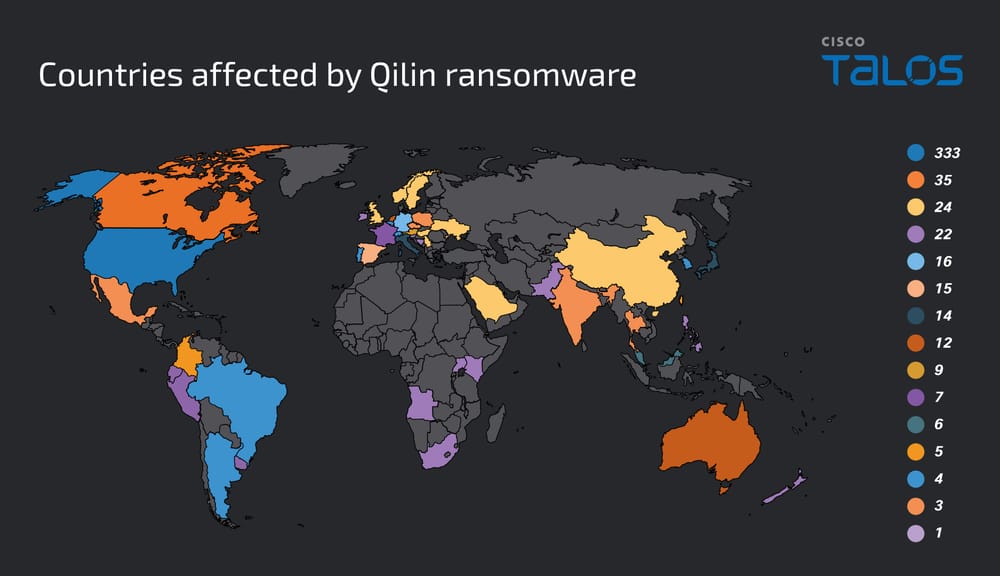
The rise of Qilin’s RaaS model
This explosive growth is partly explained by Qilin’s RaaS (ransomware-as-a-service) model. Following the demise of RansomHub in April 2025, affiliates of this group reportedly turned en masse to Qilin, causing a 280% increase in attack claims between the end of April and October. Of the 701 victims claimed in 2025, 118 were confirmed, representing 788,377 compromised records and 116 terabytes of stolen data in total (47 TB for confirmed attacks alone).
Documented ransom demands demonstrate the financial scale of these operations: $10 million demanded from Malaysia Airports Holdings in March, $4 million from Cleveland Municipal Court in February, and up to $50 million demanded from British company Synnovis in 2024, setting a record for the group.
As Comparitech analyst Rebecca Moody points out: ” British company Synnovis has been asked to pay a staggering $50 million. The healthcare company refused to pay the ransom, but the attack resulted in costs of around £33 million ($44 million) and a data breach affecting 900,000 people.”
Even when victims refuse to pay, remediation costs remain considerable: the Hamilton County Sheriff’s Office spent $48,000 to restore its systems after refusing a $300,000 request, illustrating that refusing the ransom does not eliminate the financial impact of the attack.
Initial access: the gateways to the attack
To understand this meteoric expansion, it is essential to examine the initial intrusion methods that enable Qilin operators to establish their first hold on targeted infrastructures.
False CAPTCHA and social engineering
While post-compromise techniques are sophisticated, initial access frequently relies on social engineering via fake CAPTCHA pages. Researchers identified several compromised endpoints connecting to pages hosted on the Cloudflare R2 infrastructure, presenting convincing replicas of Google CAPTCHA checks.
Analysis of the obfuscated JavaScript code embedded in these pages reveals a multi-stage payload delivery system, downloading additional malware from secondary command and control servers. These pages deliver infostealers that collect authentication tokens, browser cookies and credentials stored on infected systems.
The credentials thus harvested provide Qilin operators with the valid accounts required for initial access to the environment. This assessment is reinforced by the attackers’ ability to bypass multi-factor authentication (MFA) and move laterally using legitimate user sessions, indicating that they possessed harvested credentials rather than relying on traditional exploitation techniques.
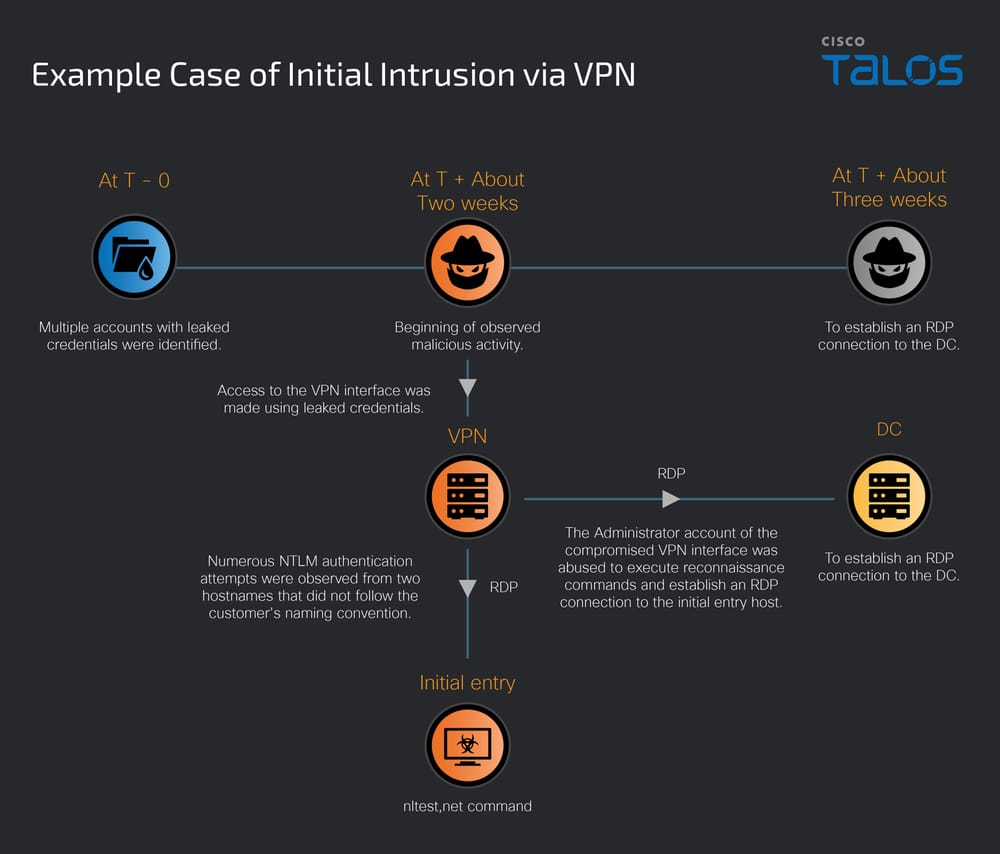
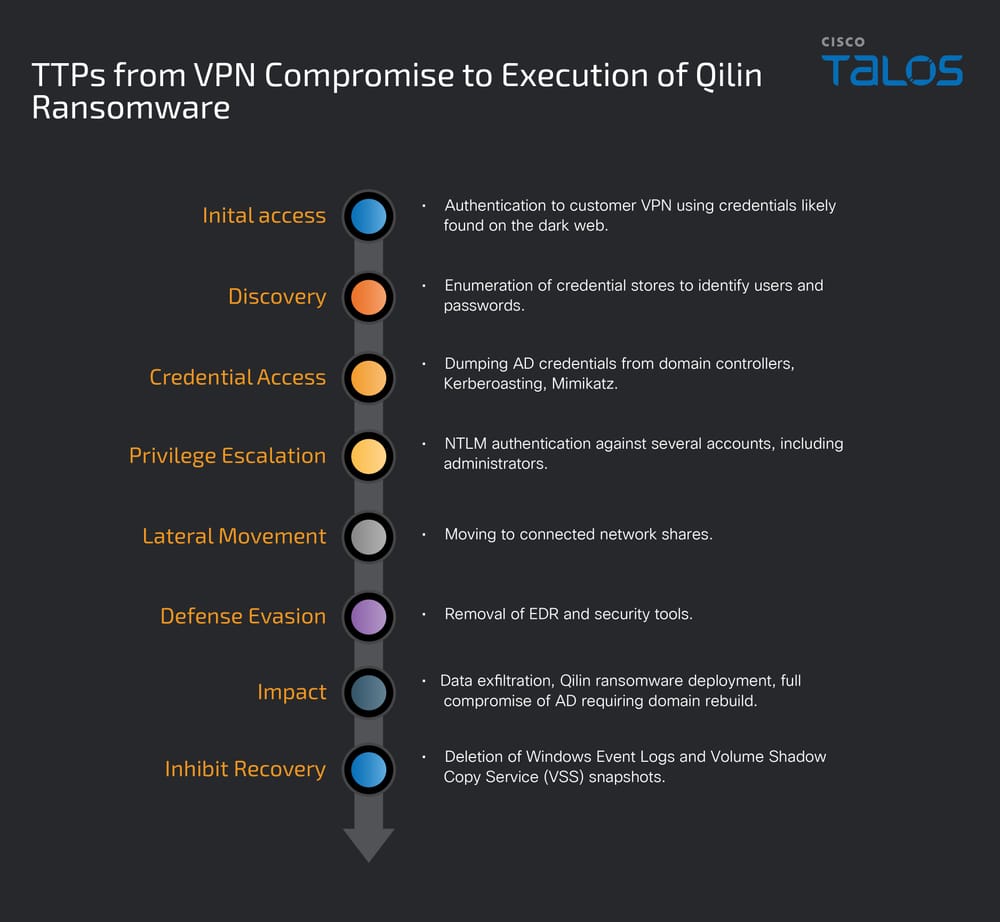
VPN access via stolen credentials from the dark web
Researchers were unable to identify with certainty a single initial intrusion vector. However, in some cases, the hypothesis of access via VPN by exploiting administrative credentials exposed on the dark web is considered with a moderate degree of confidence. The observed chronology reveals a recurring pattern: around two weeks after the credentials leak, massive NTLM authentication attempts target VPN access, culminating in a successful intrusion.
Although this activity is temporally correlated with the previously observed ID leak, there is insufficient evidence to establish a definitive causal link between the two events. An aggravating factor was nevertheless confirmed: the VPN involved had no multi-factor authentication (MFA) configured, which would have allowed an attacker with credentials unfettered access.
A complete, orchestrated attack chain
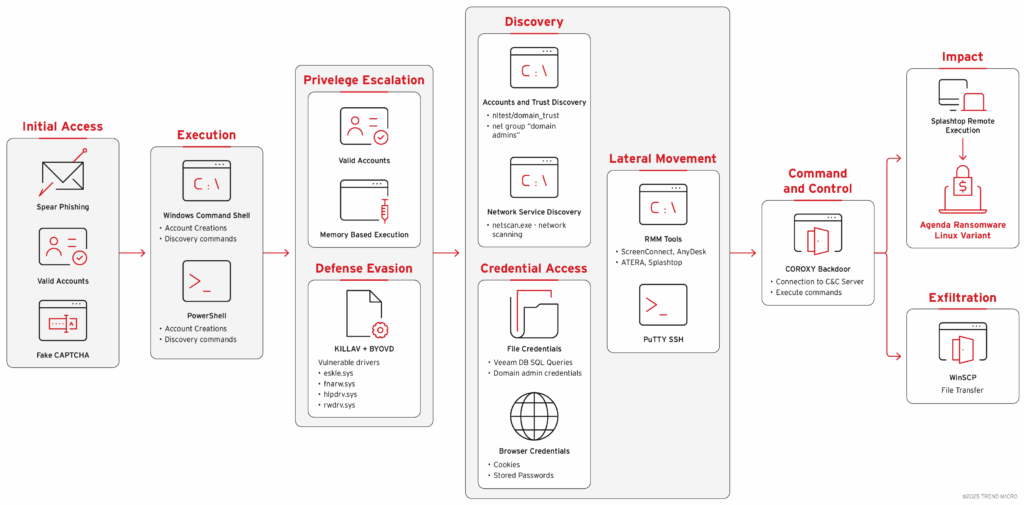
Once inside the targeted system, attackers immediately deploy a complex infrastructure designed to maintain their presence by stealth and map the compromised environment.
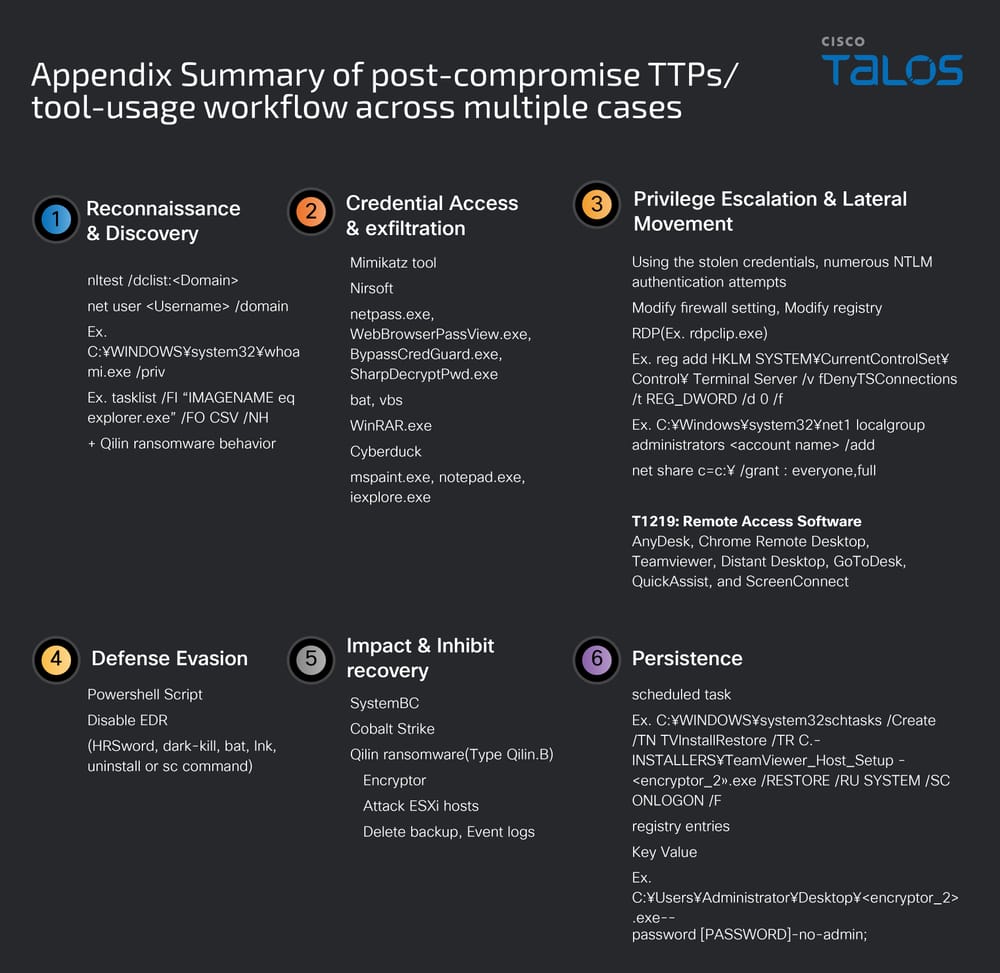
Recognition and discovery
After initial access, attackers conduct extensive reconnaissance by abusing ScreenConnect (a cloud-based solution for managing remote support operations) to execute discovery commands via temporary scripts. The nltest /domain_trusts and net group "domain admins" /domain commands enumerate domain approval relationships and identify privileged accounts, while blending in with normal administrative activity.
The NetScan utility is deployed from multiple locations (Desktop and Documents) to perform a complete network enumeration and identify potential targets for lateral movement.
Legitimate remote management tools
Attackers strategically install several RMM (Remote Monitoring and Management) tools via legitimate platforms to ensure persistent access: AnyDesk version 9.0.5 is deployed via the ATERA Networks agent, while ScreenConnect provides an additional command execution vector. This dual RMM approach offers redundant remote access capabilities that look legitimate to security monitoring systems.
Cisco Talos also observed traces of Chrome Remote Desktop, Distant Desktop, GoToDesk, QuickAssist in several incidents, illustrating the diversification of tools used.
SOCKS proxies and distributed C2 infrastructure
To maintain stealthy communications, attackers deploy multiple instances of the COROXY backdoor (SOCKS proxies) across various system directories. These proxies are systematically placed in directories associated with legitimate enterprise software:
- C:ProgramDataVeeamsocks64.dll
- C:ProgramDataVMwarelogssocks64.dll
- C:ProgramDataAdobesocks64.dll
- C:ProgramDataUSOSharedsocks64.dll
This placement strategy mixes malicious C2 traffic with normal application communications, exploiting the trust generally placed in these well-known software vendors in enterprise environments. The distributed nature of this deployment provides redundant communication channels, ensuring persistent C2 capabilities even if individual proxies are discovered and removed.
Cobalt Strike and SystemBC
Prior to the execution of the ransomware, researchers observed the deployment of Cobalt Strike loader and SystemBC backdoor to maintain persistent remote access. The Cobalt Strike loader analyzed decrypts an encrypted payload contained in the .bss section of the binary, then deploys and executes the Cobalt Strike Beacon in memory.
The Beacon is configured in version 4.x with Malleable C2 to spoof HTTP headers, including “Host: ocsp.verisign(.)com” to make traffic appear to be OCSP (Online Certificate Status Protocol) or legitimate certificate distribution traffic. Communications use HTTPS on TCP port 443 to the Team Server (C2).
Elevation of privileges and lateral movement
Armed with this command and control infrastructure, the group can now elevate privileges to extend its hold on the compromised environment.
ID theft: industrialized data collection
The arsenal of credential theft deployed by Qilin’s operators reveals a methodical, automated approach. Investigators uncovered a password-protected folder containing a suite of specialized tools dedicated to ID theft: Mimikatz, several NirSoft password recovery utilities, and custom scripts orchestrating the entire process.
The attack sequence begins with a manipulation of the Windows registry to force the retention of plaintext credentials in memory. The batch file !light.bat modifies the WDigest configuration, creating the ideal conditions for subsequent extraction by Mimikatz.
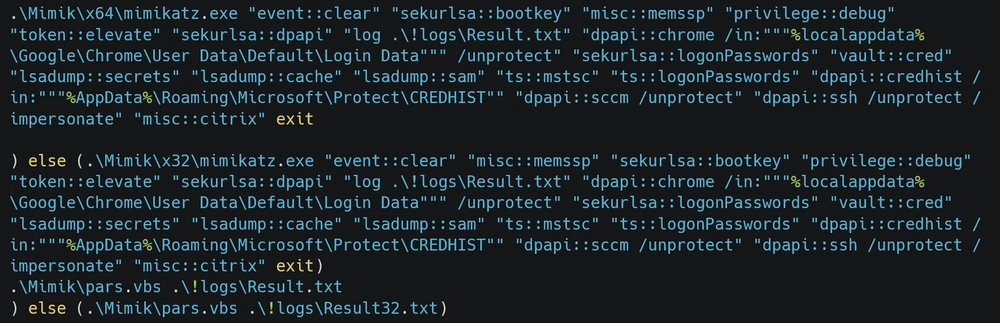
Orchestration continues with the sequential execution of netpass.exe, WebBrowserPassView.exe, BypassCredGuard.exe and SharpDecryptPwd. The latter tool systematically raids business applications: FTP clients (WinSCP, FileZilla), database management tools (Navicat), e-mail clients (Foxmail), and remote access managers (TeamViewer, RDCMan). Each application becomes a source of additional identifiers.
Mimikatz then steps in to extract credentials from active sessions, targeting privileged RDP, SSH and Citrix accesses in particular. The tool also erases Windows event logs to obscure the traces of this massive collection.
Final exfiltration takes place via a VBScript script (pars.vbs) which consolidates all stolen data into a result.txt file before transmission to an SMTP server controlled by the attackers. An intriguing detail: the script uses windows-1251 (Cyrillic) encoding, suggesting an Eastern European or Russian-speaking origin, although this may be a deliberate false flag.
BYOVD: when legitimate pilots become weapons
In addition to cross-platform execution, Qilin operators make extensive use of the BYOVD (Bring Your Own Vulnerable Driver) technique to neutralize security solutions and maintain stealth. This approach exploits legitimate but vulnerable drivers to gain privileges at Windows kernel level, enabling them to disable protective software, terminate security processes and evade detection.
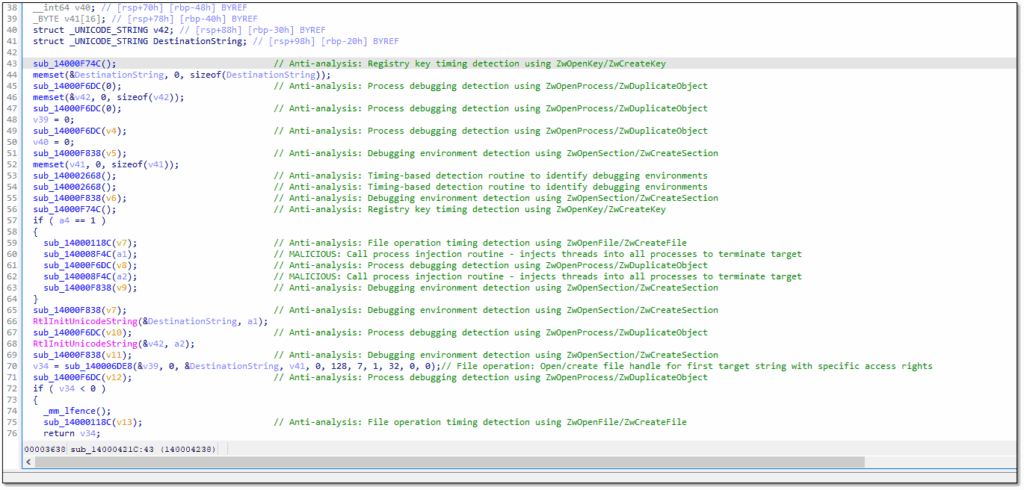
Several vulnerable drivers have been identified in this campaign: eskle.sys, whose digital signature points to a Chinese gaming company (Thumb World Beijing Network Technology), appears to be a hijacked driver originally designed to bypass anti-cheat systems. Analysis of this driver reveals sophisticated anti-virtualization detection capabilities, debugger verification and, above all, forced termination of security processes.
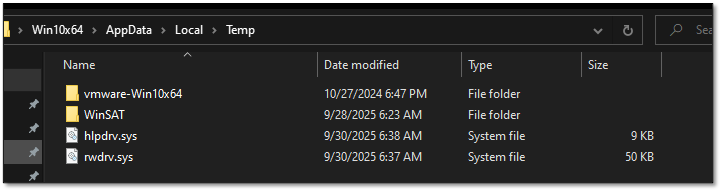
Another malicious component, msimg32.dll, functions as a dropper (also known as a syringe program or dropper virus), using the DLL sideloading technique. When executed alongside a legitimate binary such as FoxitPDFReader.exe, this library deposits two additional drivers in the temporary directory: rwdrv.sys and hlpdrv.sys, both previously documented in Akira ransomware campaigns to gain kernel-level access and neutralize traditional EDRs (endpoint detection and response).
Researchers also observed three additional executables (cg6.exe, 44a.exe, aa.exe) suspected of using a different vulnerable driver (fnarw.sys), although full analysis could not be completed in the absence of the driver. These elevated privileges obtained via BYOVD enable the attackers to attack a strategic target: the backup infrastructure.
Methodical targeting of the Veeam infrastructure
One of the most worrying features of this campaign is the systematic and specialized targeting of the Veeam backup infrastructure. The attackers have identified that these backup systems constitute a veritable vault of privileged credentials, storing access to the company’s entire critical infrastructure. This strategic understanding transforms backups into a privileged entry point for privilege elevation and lateral movement.
The extraction methodology relies on sophisticated PowerShell scripts, encoded in Base64 to evade detection, specifically developed to query Veeam’s SQL databases. Operators target three strategic tables which, combined, provide near-total access to the infrastructure:
- the Credentials table, which centralizes all login credentials ;
- the BackupRepositories table, giving access to backup storage locations;
- the WinServers table, which lists the complete inventory of backed-up Windows servers.
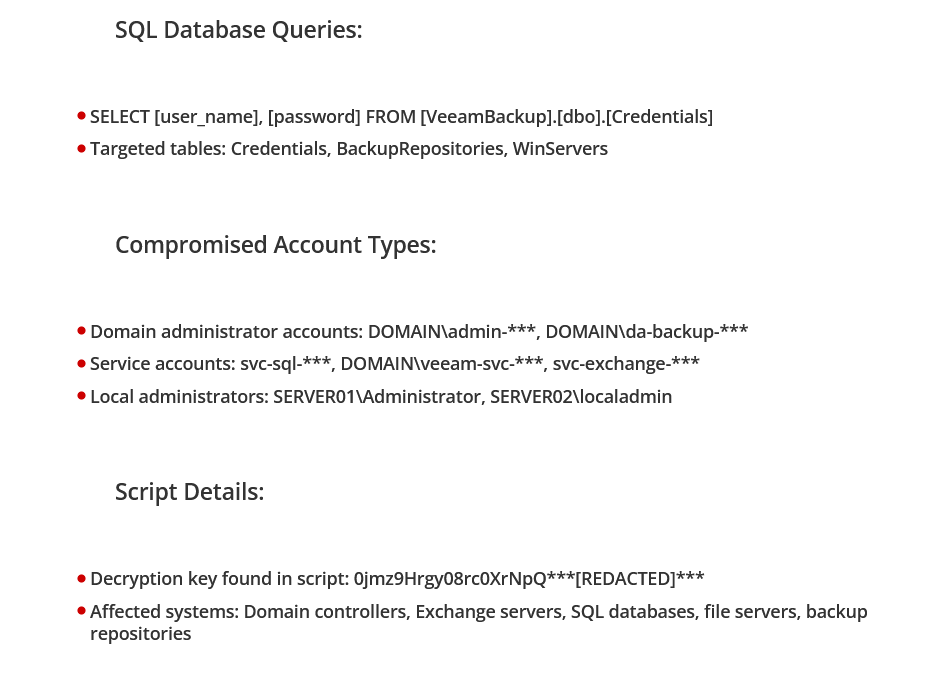
This massive extraction provides attackers with a complete set of privileged credentials: domain administrator accounts, service accounts (notably for SQL, Exchange, and the Veeam services themselves), and local administrator accounts for critical servers. Researchers observed decryption keys embedded directly in the scripts, facilitating immediate access to domain controllers, Exchange servers, SQL databases and file servers.
According to Trend Micro’s report, “attackers specifically targeted Veeam backup infrastructure using specialized credential extraction tools, systematically harvesting credentials from multiple backup databases to compromise the organization’s disaster recovery capabilities before deploying the ransomware payload.”
This approach allows attackers to compromise the organization’s disaster recovery capabilities even before the ransomware is deployed, making recovery significantly more complex and increasing the pressure to pay the ransom. Should your Veeam backups be compromised, specialized recovery solutions exist to recover your data even when files have been encrypted.
PowerShell obfuscation: three critical changes
In parallel to exploiting vulnerable drivers, attackers deploy digitally encoded obfuscated PowerShell commands to evade detection. Once decoded, these commands reveal three strategic sabotages of system defenses:
- AMSI disabling: disabling the Antimalware Scan Interface prevents Windows from inspecting running scripts and payloads, creating a blind spot in detection.
- TLS Validation disabled: by removing TLS certificate verification, communications to malicious C2 (Infrastructure Command and Control) servers become undetectable by solutions that rely on certificate inspection.
- Restricted Admin enabled: this change forces RDP authentication to use NT hashes rather than passwords. These hashes, stored in memory, can be reused by attackers to move sideways without ever knowing the real passwords (pass-the-hash technique).
Preparing for encryption
Recovery inhibition
Prior to encryption, the ransomware methodically removes all recovery capabilities: it changes the startup type of the Volume Shadow Copy Service (VSS) to Manual, deletes all shadow copies (volume snapshots) maintained by VSS with vssadmin.exe Delete Shadows /all /quiet, then stops the service and completely disables VSS.
The ransomware also executes PowerShell commands to completely clear all Windows event logs by enumerating all system logs with Get-WinEvent -ListLog * and calling the .NET method EventLogSession.GlobalSession.ClearLog() to clean them up entirely, thus eliminating potential forensic traces.
For virtualized environments, a hard-coded PowerShell script establishes a connection to the vCenter server, enumerates all datacenters and clusters, disables HA and DRS in cluster configurations, changes the root password of all ESXi hosts, enables SSH access, and downloads and executes an arbitrary binary in the “/tmp” directory of all identified hosts.
Data theft with Cyberduck
For data exfiltration, attackers use the open source tool Cyberduck, which enables file transfers to cloud servers. Researchers report that in recent trends, Cyberduck has been widely employed in cases involving the Qilin ransomware.
The screenshot of the Cyberduck history file, below, “indicates that a Backblaze host was specified as the destination and that a custom setting for split/multipart downloads was enabled in order to transfer large files.” By abusing legitimate cloud services for exfiltration, the attacker can camouflage his activities within trusted domains and legitimate web traffic.
Artifact logs also revealed the use of notepad.exe and mspaint.exe to inspect files containing highly sensitive information prior to exfiltration.
Qilin ransomware deployment: the cross-platform Linux variant
A novel execution technique: Linux on Windows
The major tactical innovation observed by Trend Micro researchers lies in the deployment of a Linux ransomware binary on Windows hosts via legitimate remote management tools. This cross-platform approach effectively bypasses traditional Windows-centric defenses, including conventional EDR (Endpoint Detection and Response) solutions.
The deployment process is divided into two distinct steps: First, WinSCP is used to securely transfer the Linux ransomware binary (named mmh_linux_x86-64) to the target Windows system. Then, the Splashtop Remote management service (SRManager.exe) directly executes this Linux binary on the Windows infrastructure, a particularly devious method since most detection systems are not configured to monitor or block the execution of Linux binaries via legitimate remote management tools on Windows platforms.
Trend Micro researchers point out that “this attack challenges traditional Windows-centric security controls. The deployment of Linux ransomware on Windows systems demonstrates how malicious actors adapt to bypass endpoint detection systems that are not configured to detect or prevent the execution of Linux binaries via remote management channels. “
This cross-platform capability enables attackers to simultaneously impact Windows and Linux systems within the same environment using a single payload, greatly simplifying their operation while optimizing the extent of damage.
The Linux variant: architecture and capabilities
Analysis of the Linux ransomware binary reveals an advanced cross-platform payload with extensive configuration capabilities. The ransomware requires password authentication to run, and displays detailed configuration output listing blacklisted processes, blocked file extensions and excluded paths.
Like other ransomware, it avoids targeting essential system directories. Trend Micro experts point out that“the configuration shows extensive targeting of VMware ESXi paths (/vmfs/, /dev/, /lib64/) while excluding critical system directories, demonstrating hypervisor-focused deployment strategies.”
Older variants implemented operating system detection for FreeBSD, VMkernel (ESXi) and standard Linux distributions, enabling platform-specific encryption behavior. The updated samples have incorporated Nutanix AHV detection, broadening targeting to include hyperconverged infrastructure platforms. This evolution demonstrates the adaptation of malicious actors to modern enterprise virtualization environments beyond traditional VMware deployments.
Comparison of logging routines reveals incremental improvements in error handling, with more recent variants implementing improved logging of file operations and fallback mechanisms for failed log file creation.
Tailor-made configuration for every victim
Analysis of the ransomware reveals a high level of customization. The configuration file contains precise lists defining what will be spared (critical system files, Windows directories) and what will be explicitly targeted (backup extensions .vbk, .vmdk, virtual machines).
Particularly revealing, the configuration includes a white_symlink_subdirs list containing only “ClusterStorage”, the directory used by Windows Server Failover Cluster (Cluster Shared Volumes or CSV). CSVs typically host files that are highly critical to organizations, such as Hyper-V virtual machines (VHDX) and databases. By explicitly targeting ClusterStorage subdirectories, the ransomware demonstrates its intention to increase impact by directly targeting virtualization and cluster infrastructure. According to Cisco Talos: “files in ClusterStorage subdirectories are explicitly listed as targets to be encrypted. The fact that white_symlink_dirs is empty is probably intended to avoid following symbolic links that could cause infinite loops or double encryption.”
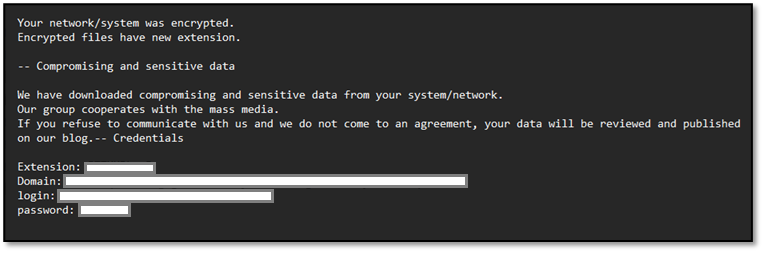
Even more worrying, hard-coded domain IDs, usernames and passwords in the configuration specific to the victim’s environment were discovered. According to the researchers: “This indicates that attackers have pre-loaded credentials into the ransomware to facilitate privilege escalation and related activities.”
Qilin execution methods and propagation
Attackers sometimes deploy an encryption program, but cases have also been observed where two programs are deployed simultaneously. In these configurations, the first (encryptor_1.exe) is distributed across the environment using PsExec, copied to remote machines, raised to run with administrative privileges before being launched with the –spread and –spread-process options.
The second encryptor (encryptor_2.exe) runs from a single system and targets multiple network shares, maximizing impact with a centralized approach.
To widen the scope of file access, the ransomware enables symbolic link evaluations with the commands fsutil behavior set SymlinkEvaluation R2R:1 (Remote to Remote, allowing a symbolic link on server A to reference files on server B) and R2L:1 (Remote to Local, allowing a shared symbolic link to point to local files on the host).
Post-encryption persistence
After executing the ransomware, the attackers maintain their persistence via task scheduling and registry modification. A scheduled task named “TVInstallRestore” is created, configured to run on connection with the /SC ONLOGON argument. To disguise itself as a legitimate tool, the ransomware file is renamed “TeamViewer_Host_Setup <encryptor_2>.exe”, exploiting TeamViewer which had been installed as an RMM (Remote Monitoring and Management) tool prior to the compromise.
At the same time, an entry was added to the HKLM\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Run registry key, ensuring the automatic launch of the ransomware at every system start-up.
This dual mechanism – scheduled task and registry modification – ensures that the ransomware is reactivated even after a cleanup attempt, whether during a full reboot or a simple user reconnection.
Defensive recommendations
Faced with this tactical evolution, Trend Micro and Check Point researchers recommend that security teams adopt an urgent, multi-layered approach:
- secure remote access and RMM tools: limit RMM platforms to authorized management hosts and enforce multi-factor authentication. Monitor abnormal activities such as out-of-hours connections or lateral movement between unexpected endpoints;
- harden the backup infrastructure: segment backup networks, apply the principle of least privilege, regularly rotate administrator credentials, and monitor suspicious use of administrative tools such as PowerShell or SQL queries interacting with backup credentials;
- detect BYOVD and cross-platform threats: monitor unsigned or unexpected driver loads, DLL sideloading, and the execution of Linux binaries on Windows via remote tools. Extend detection rules to cover non-system-native payloads;
- extend visibility to hybrid environments: ensure that EDR solutions and SOC playbooks include Windows and Linux telemetry, and actively monitor internal lateral movement to detect the early stages of hybrid ransomware attacks;
- drastically shorten patch cycles: when uptime is measured in hours, patching can no longer be a multi-week process. Automated patch validation and deployment pipelines are becoming essential.
A paradigm shift in the ransomware threat
The Qilin campaign marks a break with the ransomware tactics seen to date. The window between the disclosure of a vulnerability and its mass exploitation is shrinking drastically, transforming the cybersecurity ecosystem into a permanent race against time where defensive teams have less and less time to react.
The deployment of Linux ransomware on Windows systems demonstrates how malicious actors adapt to bypass endpoint detection systems not configured to detect or prevent the execution of Linux binaries via remote management channels. This attack challenges traditional Windows-centric security controls.
The combination of BYOVD techniques,social engineering via bogus CAPTCHAs, and strategic targeting of the backup infrastructure demonstrates a methodical approach aimed at ensuring the successful deployment of ransomware while eliminating recovery options. The use of legitimate tools and cross-platform execution methods makes detection significantly more difficult.
As Trend Micro experts conclude, ” this Qilin (Agenda) attack shows how ransomware operators are increasingly using legitimate IT tools and hybrid environments to discreetly bypass conventional security. Defenses need to control operational blind spots and reinforce visibility and control over critical assets. “
Organizations urgently need to reassess their security posture to account for these unconventional attack vectors, and implement improved monitoring of remote management tools and access to backup systems. Defenses must now be more vigilant than ever, reinforcing visibility and control over critical assets.
Sources
- Trend Micro Research: Agenda Ransomware Deploys Linux Variant on Windows Systems Through Remote Management Tools and BYOVD Techniques
- Cisco Talos Intelligence: Uncovering Qilin attack methods exposed through multiple cases
- Comparitech: Qilin ransomware: stats on attacks, ransoms & data breaches
- The Hacker News: Qilin Ransomware Combines Linux Payload With BYOVD Exploit in Hybrid Attack
- Security Affairs: Linux variant of Qilin Ransomware targets Windows via remote management tools and BYOVD
